Microsoft today released updates to fix more than 60 security holes in Windows computers and supported software, including two “zero-day” vulnerabilities in Windows that are already being exploited in active attacks. There are also important security patches available for macOS and Adobe users, and for the Chrome Web browser, which just patched its own zero-day flaw.

First, the zero-days. CVE-2024-30051 is an “elevation of privilege” bug in a core Windows library. Satnam Narang at Tenable said this flaw is being used as part of post-compromise activity to elevate privileges as a local attacker.
“CVE-2024-30051 is used to gain initial access into a target environment and requires the use of social engineering tactics via email, social media or instant messaging to convince a target to open a specially crafted document file,” Narang said. “Once exploited, the attacker can bypass OLE mitigations in Microsoft 365 and Microsoft Office, which are security features designed to protect end users from malicious files.”
Kaspersky Lab, one of two companies credited with reporting exploitation of CVE-2024-30051 to Microsoft, has published a fascinating writeup on how they discovered the exploit in a file shared with Virustotal.com.
Kaspersky said it has since seen the exploit used together with QakBot and other malware. Emerging in 2007 as a banking trojan, QakBot (a.k.a. Qbot and Pinkslipbot) has morphed into an advanced malware strain now used by multiple cybercriminal groups to prepare newly compromised networks for ransomware infestations.
CVE-2024-30040 is a security feature bypass in MSHTML, a component that is deeply tied to the default Web browser on Windows systems. Microsoft’s advisory on this flaw is fairly sparse, but Kevin Breen from Immersive Labs said this vulnerability also affects Office 365 and Microsoft Office applications.
“Very little information is provided and the short description is painfully obtuse,” Breen said of Microsoft’s advisory on CVE-2024-30040.
The only vulnerability fixed this month that earned Microsoft’s most-dire “critical” rating is CVE-2024-30044, a flaw in Sharepoint that Microsoft said is likely to be exploited. Tenable’s Narang notes that exploitation of this bug requires an attacker to be authenticated to a vulnerable SharePoint Server with Site Owner permissions (or higher) first and to take additional steps in order to exploit this flaw, which makes this flaw less likely to be widely exploited as most attackers follow the path of least resistance.
Five days ago, Google released a security update for Chrome that fixes a zero-day in the popular browser. Chrome usually auto-downloads any available updates, but it still may require a complete restart of the browser to install them. If you use Chrome and see a “Relaunch to update” message in the upper right corner of the browser, it’s time to restart.
Apple has just shipped macOS Sonoma 14.5 update, which includes nearly two dozen security patches. To ensure your Mac is up-to-date, go to System Settings, General tab, then Software Update and follow any prompts.
Finally, Adobe has critical security patches available for a range of products, including Acrobat, Reader, Illustrator, Adobe Substance 3D Painter, Adobe Aero, Adobe Animate and Adobe Framemaker.
Regardless of whether you use a Mac or Windows system (or something else), it’s always a good idea to backup your data and or system before applying any security updates. For a closer look at the individual fixes released by Microsoft today, check out the complete list over at the SANS Internet Storm Center. Anyone in charge of maintaining Windows systems in an enterprise environment should keep an eye on askwoody.com, which usually has the scoop on any wonky Windows patches.
Update, May 15, 8:28 a.m.: Corrected misattribution of CVE-2024-30051.
Millions of U.S. government employees and contractors have been issued a secure smart ID card that enables physical access to buildings and controlled spaces, and provides access to government computer networks and systems at the cardholder’s appropriate security level. But many government employees aren’t issued an approved card reader device that lets them use these cards at home or remotely, and so turn to low-cost readers they find online. What could go wrong? Here’s one example.

A sample Common Access Card (CAC). Image: Cac.mil.
KrebsOnSecurity recently heard from a reader — we’ll call him “Mark” because he wasn’t authorized to speak to the press — who works in IT for a major government defense contractor and was issued a Personal Identity Verification (PIV) government smart card designed for civilian employees. Not having a smart card reader at home and lacking any obvious guidance from his co-workers on how to get one, Mark opted to purchase a $15 reader from Amazon that said it was made to handle U.S. government smart cards.
The USB-based device Mark settled on is the first result that currently comes up one when searches on Amazon.com for “PIV card reader.” The card reader Mark bought was sold by a company called Saicoo, whose sponsored Amazon listing advertises a “DOD Military USB Common Access Card (CAC) Reader” and has more than 11,700 mostly positive ratings.
The Common Access Card (CAC) is the standard identification for active duty uniformed service personnel, selected reserve, DoD civilian employees, and eligible contractor personnel. It is the principal card used to enable physical access to buildings and controlled spaces, and provides access to DoD computer networks and systems.
Mark said when he received the reader and plugged it into his Windows 10 PC, the operating system complained that the device’s hardware drivers weren’t functioning properly. Windows suggested consulting the vendor’s website for newer drivers.
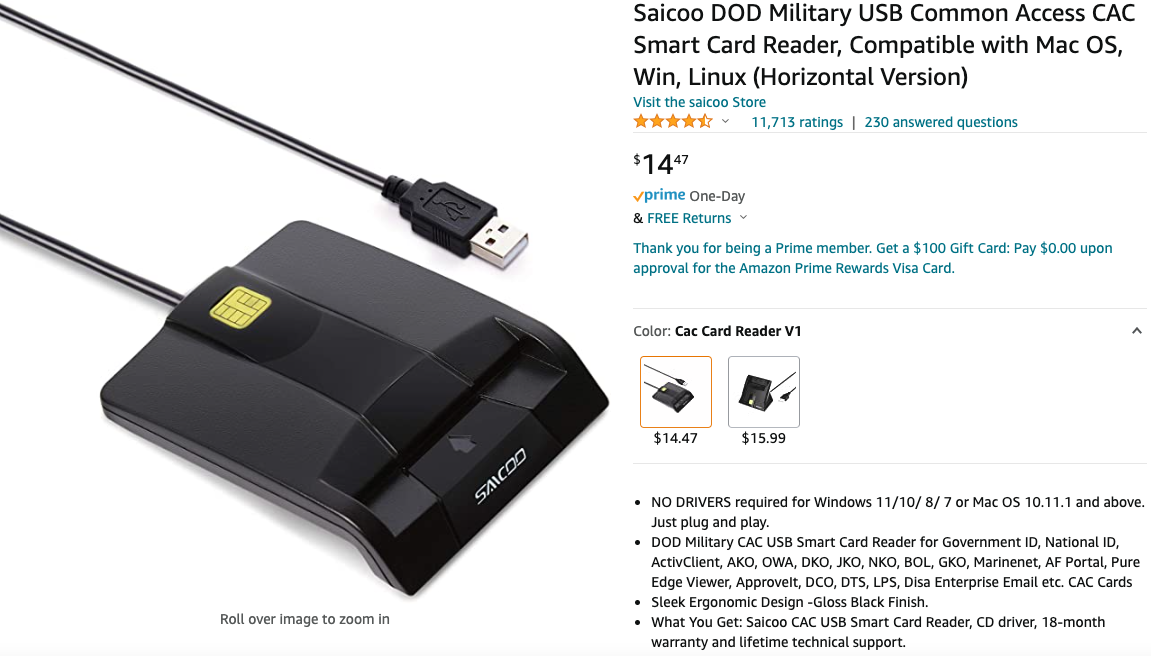
The Saicoo smart card reader that Mark purchased. Image: Amazon.com
So Mark went to the website mentioned on Saicoo’s packaging and found a ZIP file containing drivers for Linux, Mac OS and Windows:
Image: Saicoo
Out of an abundance of caution, Mark submitted Saicoo’s drivers file to Virustotal.com, which simultaneously scans any shared files with more than five dozen antivirus and security products. Virustotal reported that some 43 different security tools detected the Saicoo drivers as malicious. The consensus seems to be that the ZIP file currently harbors a malware threat known as Ramnit, a fairly common but dangerous trojan horse that spreads by appending itself to other files.
Ramnit is a well-known and older threat — first surfacing more than a decade ago — but it has evolved over the years and is still employed in more sophisticated data exfiltration attacks. Amazon said in a written statement that it was investigating the reports.
“Seems like a potentially significant national security risk, considering that many end users might have elevated clearance levels who are using PIV cards for secure access,” Mark said.
Mark said he contacted Saicoo about their website serving up malware, and received a response saying the company’s newest hardware did not require any additional drivers. He said Saicoo did not address his concern that the driver package on its website was bundled with malware.
In response to KrebsOnSecurity’s request for comment, Saicoo sent a somewhat less reassuring reply.
“From the details you offered, issue may probably caused by your computer security defense system as it seems not recognized our rarely used driver & detected it as malicious or a virus,” Saicoo’s support team wrote in an email.
“Actually, it’s not carrying any virus as you can trust us, if you have our reader on hand, please just ignore it and continue the installation steps,” the message continued. “When driver installed, this message will vanish out of sight. Don’t worry.”
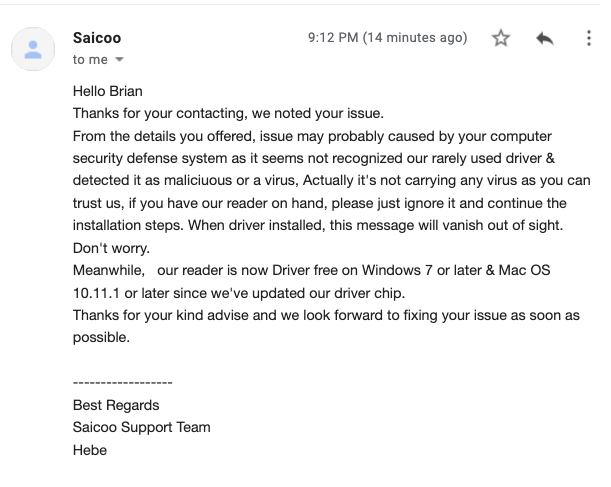
Saicoo’s response to KrebsOnSecurity.
The trouble with Saicoo’s apparently infected drivers may be little more than a case of a technology company having their site hacked and responding poorly. Will Dormann, a vulnerability analyst at CERT/CC, wrote on Twitter that the executable files (.exe) in the Saicoo drivers ZIP file were not altered by the Ramnit malware — only the included HTML files.
Dormann said it’s bad enough that searching for device drivers online is one of the riskiest activities one can undertake online.
“Doing a web search for drivers is a VERY dangerous (in terms of legit/malicious hit ratio) search to perform, based on results of any time I’ve tried to do it,” Dormann added. “Combine that with the apparent due diligence of the vendor outlined here, and well, it ain’t a pretty picture.”
But by all accounts, the potential attack surface here is enormous, as many federal employees clearly will purchase these readers from a myriad of online vendors when the need arises. Saicoo’s product listings, for example, are replete with comments from customers who self-state that they work at a federal agency (and several who reported problems installing drivers).
A thread about Mark’s experience on Twitter generated a strong response from some of my followers, many of whom apparently work for the U.S. government in some capacity and have government-issued CAC or PIV cards.
Two things emerged clearly from that conversation. The first was general confusion about whether the U.S. government has any sort of list of approved vendors. It does. The General Services Administration (GSA), the agency which handles procurement for federal civilian agencies, maintains a list of approved card reader vendors at idmanagement.gov (Saicoo is not on that list). [Thanks to @MetaBiometrics and @shugenja for the link!]
The other theme that ran through the Twitter discussion was the reality that many people find buying off-the-shelf readers more expedient than going through the GSA’s official procurement process, whether it’s because they were never issued one or the reader they were using simply no longer worked or was lost and they needed another one quickly.
“Almost every officer and NCO [non-commissioned officer] I know in the Reserve Component has a CAC reader they bought because they had to get to their DOD email at home and they’ve never been issued a laptop or a CAC reader,” said David Dixon, an Army veteran and author who lives in Northern Virginia. “When your boss tells you to check your email at home and you’re in the National Guard and you live 2 hours from the nearest [non-classified military network installation], what do you think is going to happen?”
Interestingly, anyone asking on Twitter about how to navigate purchasing the right smart card reader and getting it all to work properly is invariably steered toward militarycac.com. The website is maintained by Michael Danberry, a decorated and retired Army veteran who launched the site in 2008 (its text and link-heavy design very much takes one back to that era of the Internet and webpages in general). His site has even been officially recommended by the Army (PDF). Mark shared emails showing Saicoo itself recommends militarycac.com.

Image: Militarycac.com.
“The Army Reserve started using CAC logon in May 2006,” Danberry wrote on his “About” page. “I [once again] became the ‘Go to guy’ for my Army Reserve Center and Minnesota. I thought Why stop there? I could use my website and knowledge of CAC and share it with you.”
Danberry did not respond to requests for an interview — no doubt because he’s busy doing tech support for the federal government. The friendly message on Danberry’s voicemail instructs support-needing callers to leave detailed information about the issue they’re having with CAC/PIV card readers.
Dixon said Danberry has “done more to keep the Army running and connected than all the G6s [Army Chief Information Officers] put together.”
In many ways, Mr. Danberry is the equivalent of that little known software developer whose tiny open-sourced code project ends up becoming widely adopted and eventually folded into the fabric of the Internet. I wonder if he ever imagined 15 years ago that his website would one day become “critical infrastructure” for Uncle Sam?