Authorities in Australia, the United Kingdom and the United States this week levied financial sanctions against a Russian man accused of stealing data on nearly 10 million customers of the Australian health insurance giant Medibank. 33-year-old Aleksandr Ermakov allegedly stole and leaked the Medibank data while working with one of Russia’s most destructive ransomware groups, but little more is shared about the accused. Here’s a closer look at the activities of Mr. Ermakov’s alleged hacker handles.

Aleksandr Ermakov, 33, of Russia. Image: Australian Department of Foreign Affairs and Trade.
The allegations against Ermakov mark the first time Australia has sanctioned a cybercriminal. The documents released by the Australian government included multiple photos of Mr. Ermakov, and it was clear they wanted to send a message that this was personal.
It’s not hard to see why. The attackers who broke into Medibank in October 2022 stole 9.7 million records on current and former Medibank customers. When the company refused to pay a $10 million ransom demand, the hackers selectively leaked highly sensitive health records, including those tied to abortions, HIV and alcohol abuse.
The U.S. government says Ermakov and the other actors behind the Medibank hack are believed to be linked to the Russia-backed cybercrime gang REvil.
“REvil was among the most notorious cybercrime gangs in the world until July 2021 when they disappeared. REvil is a ransomware-as-a-service (RaaS) operation and generally motivated by financial gain,” a statement from the U.S. Department of the Treasury reads. “REvil ransomware has been deployed on approximately 175,000 computers worldwide, with at least $200 million paid in ransom.”
The sanctions say Ermakov went by multiple aliases on Russian cybercrime forums, including GustaveDore, JimJones, and Blade Runner. A search on the handle GustaveDore at the cyber intelligence platform Intel 471 shows this user created a ransomware affiliate program in November 2021 called Sugar (a.k.a. Encoded01), which focused on targeting single computers and end-users instead of corporations.
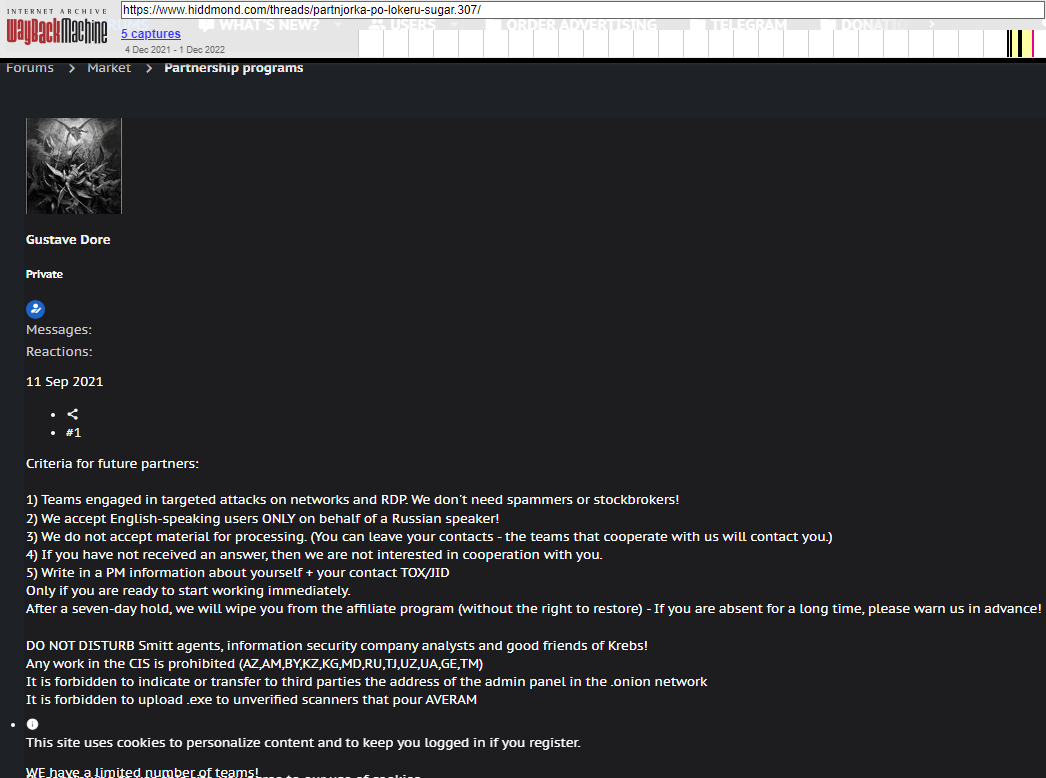
An ad for the ransomware-as-a-service program Sugar posted by GustaveDore warns readers against sharing information with security researchers, law enforcement, or “friends of Krebs.”
In November 2020, Intel 471 analysts concluded that GustaveDore’s alias JimJones “was using and operating several different ransomware strains, including a private undisclosed strain and one developed by the REvil gang.”
In 2020, GustaveDore advertised on several Russian discussion forums that he was part of a Russian technology firm called Shtazi, which could be hired for computer programming, web development, and “reputation management.” Shtazi’s website remains in operation today.
A Google-translated version of Shtazi dot ru. Image: Archive.org.
The third result when one searches for shtazi[.]ru in Google is an Instagram post from a user named Mikhail Borisovich Shefel, who promotes Shtazi’s services as if it were also his business. If this name sounds familiar, it’s because in December 2023 KrebsOnSecurity identified Mr. Shefel as “Rescator,” the cybercriminal identity tied to tens of millions of payment cards that were stolen in 2013 and 2014 from big box retailers Target and Home Depot, among others.
How close was the connection between GustaveDore and Mr. Shefel? The Treasury Department’s sanctions page says Ermakov used the email address ae.ermak@yandex.ru. A search for this email at DomainTools.com shows it was used to register just one domain name: millioner1[.]com. DomainTools further finds that a phone number tied to Mr. Shefel (79856696666) was used to register two domains: millioner[.]pw, and shtazi[.]net.
The December 2023 story here that outed Mr. Shefel as Rescator noted that Shefel recently changed his last name to “Lenin” and had launched a service called Lenin[.]biz that sells physical USSR-era Ruble notes bearing the image of Vladimir Lenin, the founding father of the Soviet Union. The Instagram account for Mr. Shefel includes images of stacked USSR-era Ruble notes, as well as multiple links to Shtazi.

The Instagram account of Mikhail Borisovich Shefel, aka MikeMike aka Rescator.
Intel 471’s research revealed Ermakov was affiliated in some way with REvil because the stolen Medibank data was published on a blog that had one time been controlled by REvil affiliates who carried out attacks and paid an affiliate fee to the gang.
But by the time of the Medibank hack, the REvil group had mostly scattered after a series of high-profile attacks led to the group being disrupted by law enforcement. In November 2021, Europol announced it arrested seven REvil affiliates who collectively made more than $230 million worth of ransom demands since 2019. At the same time, U.S. authorities unsealed two indictments against a pair of accused REvil cybercriminals.
“The posting of Medibank’s data on that blog, however, indicated a connection with that group, although the connection wasn’t clear at the time,” Intel 471 wrote. “This makes sense in retrospect, as Ermakov’s group had also been a REvil affiliate.”
It is easy to dismiss sanctions like these as ineffective, because as long as Mr. Ermakov remains in Russia he has little to fear of arrest. However, his alleged role as an apparent top member of REvil paints a target on him as someone who likely possesses large sums of cryptocurrency, said Patrick Gray, the Australian co-host and founder of the security news podcast Risky Business.
“I’ve seen a few people poo-poohing the sanctions…but the sanctions component is actually less important than the doxing component,” Gray said. “Because this guy’s life just got a lot more complicated. He’s probably going to have to pay some bribes to stay out of trouble. Every single criminal in Russia now knows he is a vulnerable 33 year old with an absolute ton of bitcoin. So this is not a happy time for him.”
Update, Feb. 21, 1:10 p.m. ET: The Russian security firm F.A.C.C.T reports that Ermakov has been arrested in Russia, and charged with violating domestic laws that prohibit the creation, use and distribution of malicious computer programs.
“During the investigation, several defendants were identified who were not only promoting their ransomware, but also developing custom-made malicious software, creating phishing sites for online stores, and driving user traffic to fraudulent schemes popular in Russia and the CIS,” F.A.C.C.T. wrote. “Among those detained was the owner of the nicknames blade_runner, GistaveDore, GustaveDore, JimJones.”
























s3-ep100-js-1200










The U.S. government agency in charge of improving the nation’s cybersecurity posture is ordering all federal agencies to take new measures to restrict access to Internet-exposed networking equipment. The directive comes amid a surge in attacks targeting previously unknown vulnerabilities in widely used security and networking appliances.

Under a new order from the Cybersecurity and Infrastructure Security Agency (CISA), federal agencies will have 14 days to respond to any reports from CISA about misconfigured or Internet-exposed networking equipment. The directive applies to any networking devices — such as firewalls, routers and load balancers — that allow remote authentication or administration.
The order requires federal departments to limit access so that only authorized users on an agency’s local or internal network can reach the management interfaces of these devices. CISA’s mandate follows a slew of recent incidents wherein attackers exploited zero-day flaws in popular networking products to conduct ransomware and cyber espionage attacks on victim organizations.
Earlier today, incident response firm Mandiant revealed that since at least October 2022, Chinese cyber spies have been exploiting a zero-day vulnerability in many email security gateway (ESG) appliances sold by California-based Barracuda Networks to hoover up email from organizations using these devices.
Barracuda was alerted to the exploitation of a zero-day in its products in mid-May, and two days later the company pushed a security update to address the flaw in all affected devices. But last week, Barracuda took the highly unusual step of offering to replace compromised ESGs, evidently in response to malware that altered the systems in such a fundamental way that they could no longer be secured remotely with software updates.
According to Mandiant, a previously unidentified Chinese hacking group was responsible for exploiting the Barracuda flaw, and appeared to be searching through victim organization email records for accounts “belonging to individuals working for a government with political or strategic interest to [China] while this victim government was participating in high-level, diplomatic meetings with other countries.”
When security experts began raising the alarm about a possible zero-day in Barracuda’s products, the Chinese hacking group altered their tactics, techniques and procedures (TTPs) in response to Barracuda’s efforts to contain and remediate the incident, Mandiant found.
Mandiant said the attackers will continue to change their tactics and malware, “especially as network defenders continue to take action against this adversary and their activity is further exposed by the infosec community.”
Meanwhile, this week we learned more details about the ongoing exploitation of a zero-day flaw in a broad range of virtual private networking (VPN) products made by Fortinet — devices many organizations rely on to facilitate remote network access for employees.
On June 11, Fortinet released a half-dozen security updates for its FortiOS firmware, including a weakness that researchers said allows an attacker to run malware on virtually any Fortinet SSL VPN appliance. The researchers found that just being able to reach the management interface for a vulnerable Fortinet SSL VPN appliance was enough to completely compromise the devices.
“This is reachable pre-authentication, on every SSL VPN appliance,” French vulnerability researcher Charles Fol tweeted. “Patch your #Fortigate.”
In details published on June 12, Fortinet confirmed that one of the vulnerabilities (CVE-2023-27997) is being actively exploited. The company said it discovered the weakness in an internal code audit that began in January 2023 — when it learned that Chinese hackers were exploiting a different zero-day flaw in its products.
Shodan.io, the search engine made for finding Internet of Things devices, reports that there are currently more than a half-million vulnerable Fortinet devices reachable via the public Internet.
The new cybersecurity directive from CISA orders agencies to remove any networking device management interfaces from the internet by making them only accessible from an internal enterprise network (CISA recommends an isolated management network). CISA also says agencies should “deploy capabilities, as part of a Zero Trust Architecture, that enforce access control to the interface through a policy enforcement point separate from the interface itself (preferred action).”

Security experts say CISA’s directive highlights the reality that cyberspies and ransomware gangs are making it increasingly risky for organizations to expose any devices to the public Internet, because these groups have strong incentives to probe such devices for previously unknown security vulnerabilities.
The most glaring example of this dynamic can be seen in the frequency with which ransomware groups have discovered and pounced on zero-day flaws in widely-used file transfer applications. One ransomware gang in particular — Cl0p — has repeatedly exploited zero day bugs in various file transfer appliances to extort tens of millions of dollars from hundreds of ransomware victims.
On February 2, KrebsOnSecurity broke the news that attackers were exploiting a zero-day vulnerability in the GoAnywhere file transfer appliance by Fortra. By the time security updates were available to fix the vulnerability, Cl0p had already used it to steal data from more than a hundred organizations running Fortra’s appliance.
According to CISA, on May 27, Cl0p began exploiting a previously unknown flaw in MOVEit Transfer, a popular Internet-facing file transfer application. MOVEit parent Progress Software has since released security updates to address the weakness, but Cl0p claims to have already used it to compromise hundreds of victim organizations. TechCrunch has been tracking the fallout from victim organizations, which range from banks and insurance providers to universities and healthcare entities.
The always on-point weekly security news podcast Risky Business has recently been urging organizations to jettison any and all FTP appliances, noting that Cl0p (or another crime gang) is likely to visit the same treatment on other FTP appliance vendors.
But that sound advice doesn’t exactly scale for mid-tier networking devices like Barracuda ESGs or Fortinet SSL VPNs, which are particularly prominent in small to mid-sized organizations.
“It’s not like FTP services, you can’t tell an enterprise [to] turn off the VPN [because] the productivity hit of disconnecting the VPN is terminal, it’s a non-starter,” Risky Business co-host Adam Boileau said on this week’s show. “So how to mitigate the impact of having to use a domain-joined network appliance at the edge of your network that is going to get zero-day in it? There’s no good answer.”
Risky Business founder Patrick Gray said the COVID-19 pandemic breathed new life into entire classes of networking appliances that rely on code which was never designed with today’s threat models in mind.
“In the years leading up to the pandemic, the push towards identity-aware proxies and zero trust everything and moving away from this type of equipment was gradual, but it was happening,” Gray said. “And then COVID-19 hit and everybody had to go work from home, and there really was one option to get going quickly — which was to deploy VPN concentrators with enterprise features.”
Gray said the security industry had been focused on building the next generation of remote access tools that are more security-hardened, but when the pandemic hit organizations scrambled to cobble together whatever they could.
“The only stuff available in the market was all this old crap that is not QA’d properly, and every time you shake them CVEs fall out,” Gray remarked, calling the pandemic, “a shot in the arm” to companies like Fortinet and Barracuda.
“They sold so many VPNs through the pandemic and this is the hangover,” Gray said. “COVID-19 extended the life of these companies and technologies, and that’s unfortunate.”


s3-ep138-1200



s3-ep137-feat-1200







































s3-ep124-auth--1200



































































pic-1200
























s3-ep100-js-1200






