






Denis Emelyantsev, a 36-year-old Russian man accused of running a massive botnet called RSOCKS that stitched malware into millions of devices worldwide, pleaded guilty to two counts of computer crime violations in a California courtroom this week. The plea comes just months after Emelyantsev was extradited from Bulgaria, where he told investigators, “America is looking for me because I have enormous information and they need it.”

A copy of the passport for Denis Emelyantsev, a.k.a. Denis Kloster, as posted to his Vkontakte page in 2019.
First advertised in the cybercrime underground in 2014, RSOCKS was the web-based storefront for hacked computers that were sold as “proxies” to cybercriminals looking for ways to route their Web traffic through someone else’s device.
Customers could pay to rent access to a pool of proxies for a specified period, with costs ranging from $30 per day for access to 2,000 proxies, to $200 daily for up to 90,000 proxies.
Many of the infected systems were Internet of Things (IoT) devices, including industrial control systems, time clocks, routers, audio/video streaming devices, and smart garage door openers. Later in its existence, the RSOCKS botnet expanded into compromising Android devices and conventional computers.
In June 2022, authorities in the United States, Germany, the Netherlands and the United Kingdom announced a joint operation to dismantle the RSOCKS botnet. But that action did not name any defendants.
Inspired by that takedown, KrebsOnSecurity followed clues from the RSOCKS botnet master’s identity on the cybercrime forums to Emelyantsev’s personal blog, where he went by the name Denis Kloster. The blog featured musings on the challenges of running a company that sells “security and anonymity services to customers around the world,” and even included a group photo of RSOCKS employees.
“Thanks to you, we are now developing in the field of information security and anonymity!,” Kloster’s blog enthused. “We make products that are used by thousands of people around the world, and this is very cool! And this is just the beginning!!! We don’t just work together and we’re not just friends, we’re Family.”
But by the time that investigation was published, Emelyantsev had already been captured by Bulgarian authorities responding to an American arrest warrant. At his extradition hearing, Emelyantsev claimed he would prove his innocence in an U.S. courtroom.
“I have hired a lawyer there and I want you to send me as quickly as possible to clear these baseless charges,” Emelyantsev told the Bulgarian court. “I am not a criminal and I will prove it in an American court.”
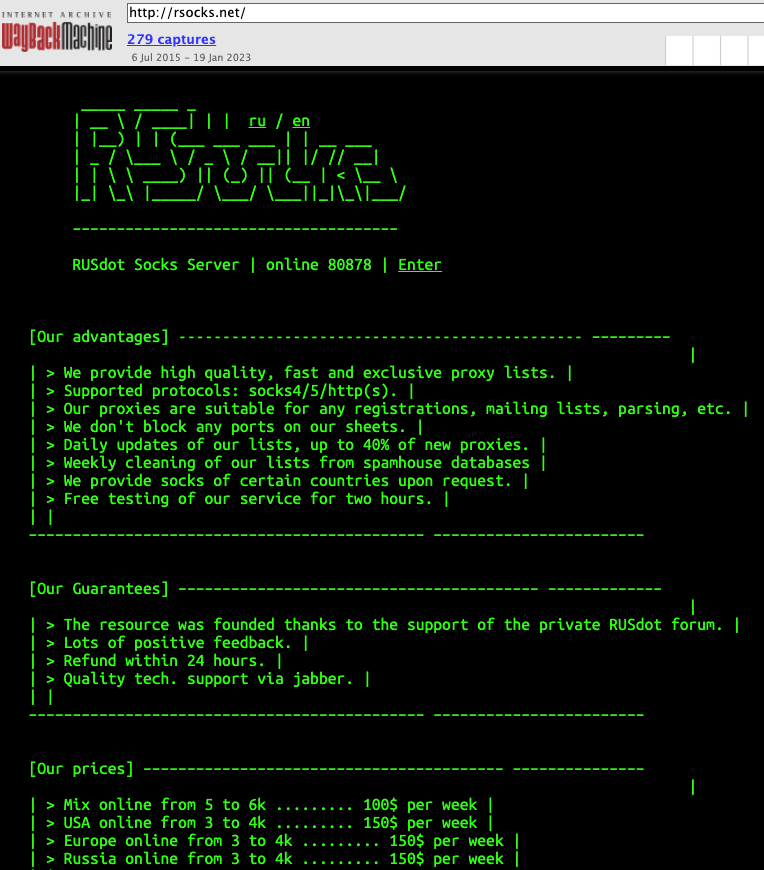
RSOCKS, circa 2016. At that time, RSOCKS was advertising more than 80,000 proxies. Image: archive.org.
Emelyantsev was far more than just an administrator of a large botnet. Behind the facade of his Internet advertising company based in Omsk, Russia, the RSOCKS botmaster was a major player in the Russian email spam industry for more than a decade.
Some of the top Russian cybercrime forums have been hacked over the years, and leaked private messages from those forums show the RSOCKS administrator claimed ownership of the RUSdot spam forum. RUSdot is the successor forum to Spamdot, a far more secretive and restricted community where most of the world’s top spammers, virus writers and cybercriminals collaborated for years before the forum imploded in 2010.
A Google-translated version of the Rusdot spam forum.
Indeed, the very first mentions of RSOCKS on any Russian-language cybercrime forums refer to the service by its full name as the “RUSdot Socks Server.”
Email spam — and in particular malicious email sent via compromised computers — is still one of the biggest sources of malware infections that lead to data breaches and ransomware attacks. So it stands to reason that as administrator of Russia’s most well-known forum for spammers, Emelyantsev probably knows quite a bit about other top players in the botnet spam and malware community.
It remains unclear whether Emelyantsev made good on his promise to spill that knowledge to American investigators as part of his plea deal. The case is being prosecuted by the U.S. Attorney’s Office for the Southern District of California, which has not responded to a request for comment.
Emelyantsev pleaded guilty on Monday to two counts, including damage to protected computers and conspiracy to damage protected computers. He faces a maximum of 20 years in prison, and is currently scheduled to be sentenced on April 27, 2023.