Updated The open source R programming language – popular among statisticians and data scientists for performing visualization, machine learning, and suchlike – has patched an arbitrary code execution hole that scored a preliminary CVSS severity rating of 8.8 out of 10.…
This tutorial gives an example showing how to fuzz a function out of a compiled binary using AFL's QEMU mode.
A cyber-thief who snatched tens of thousands of patients' sensitive records from a psychotherapy clinic before blackmailing them and then leaking their files online has been caged for six years and three months.…
Updated UnitedHealth CEO Andrew Witty will tell US lawmakers Wednesday the cybercriminals who hit Change Healthcare with ransomware used stolen credentials to remotely access a Citrix portal that didn't have multi-factor authentication enabled.…
A former NSA employee has been sentenced to 262 months in prison for attempting to freelance as a Russian spy.…
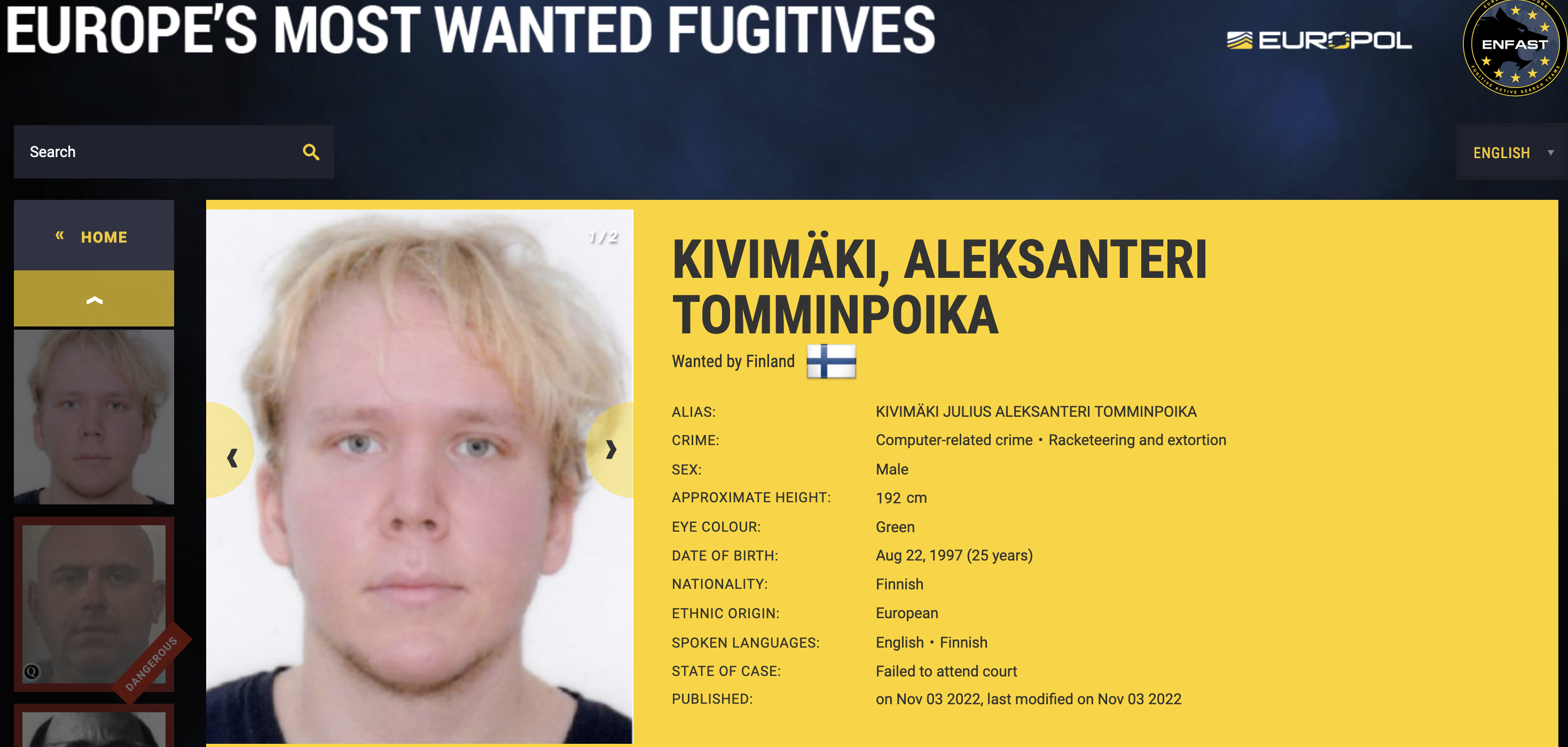
A 26-year-old Finnish man was sentenced to more than six years in prison today after being convicted of hacking into an online psychotherapy clinic, leaking tens of thousands of patient therapy records, and attempting to extort the clinic and patients.
On October 21, 2020, the Vastaamo Psychotherapy Center in Finland became the target of blackmail when a tormentor identified as “ransom_man” demanded payment of 40 bitcoins (~450,000 euros at the time) in return for a promise not to publish highly sensitive therapy session notes Vastaamo had exposed online.
Ransom_man announced on the dark web that he would start publishing 100 patient profiles every 24 hours. When Vastaamo declined to pay, ransom_man shifted to extorting individual patients. According to Finnish police, some 22,000 victims reported extortion attempts targeting them personally, targeted emails that threatened to publish their therapy notes online unless paid a 500 euro ransom.
Finnish prosecutors quickly zeroed in on a suspect: Julius “Zeekill” Kivimäki, a notorious criminal hacker convicted of committing tens of thousands of cybercrimes before he became an adult. After being charged with the attack in October 2022, Kivimäki fled the country. He was arrested four months later in France, hiding out under an assumed name and passport.
Antti Kurittu is a former criminal investigator who worked on an investigation involving Kivimäki’s use of the Zbot botnet, among other activities Kivimäki engaged in as a member of the hacker group Hack the Planet (HTP).
Kurittu said the prosecution had demanded at least seven years in jail, and that the sentence handed down was six years and three months. Kurittu said prosecutors knocked a few months off of Kivimäki’s sentence because he agreed to pay compensation to his victims, and that Kivimäki will remain in prison during any appeal process.
“I think the sentencing was as expected, knowing the Finnish judicial system,” Kurittu told KrebsOnSecurity. “As Kivimäki has not been sentenced to a non-suspended prison sentence during the last five years, he will be treated as a first-timer, his previous convictions notwithstanding.”
But because juvenile convictions in Finland don’t count towards determining whether somebody is a first-time offender, Kivimäki will end up serving approximately half of his sentence.
“This seems like a short sentence when taking into account the gravity of his actions and the life-altering consequences to thousands of people, but it’s almost the maximum the law allows for,” Kurittu said.
Kivimäki initially gained notoriety as a self-professed member of the Lizard Squad, a mainly low-skilled hacker group that specialized in DDoS attacks. But American and Finnish investigators say Kivimäki’s involvement in cybercrime dates back to at least 2008, when he was introduced to a founding member of what would soon become HTP.
Finnish police said Kivimäki also used the nicknames “Ryan”, “RyanC” and “Ryan Cleary” (Ryan Cleary was actually a member of a rival hacker group — LulzSec — who was sentenced to prison for hacking).
Kivimäki and other HTP members were involved in mass-compromising web servers using known vulnerabilities, and by 2012 Kivimäki’s alias Ryan Cleary was selling access to those servers in the form of a DDoS-for-hire service. Kivimäki was 15 years old at the time.
In 2013, investigators going through devices seized from Kivimäki found computer code that had been used to crack more than 60,000 web servers using a previously unknown vulnerability in Adobe’s ColdFusion software. KrebsOnSecurity detailed the work of HTP in September 2013, after the group compromised servers inside data brokers LexisNexis, Kroll, and Dun & Bradstreet.
The group used the same ColdFusion flaws to break into the National White Collar Crime Center (NWC3), a non-profit that provides research and investigative support to the U.S. Federal Bureau of Investigation (FBI).
As KrebsOnSecurity reported at the time, this small ColdFusion botnet of data broker servers was being controlled by the same cybercriminals who’d assumed control over SSNDOB, which operated one of the underground’s most reliable services for obtaining Social Security Number, dates of birth and credit file information on U.S. residents.
Kivimäki was responsible for making an August 2014 bomb threat against former Sony Online Entertainment President John Smedley that grounded an American Airlines plane. Kivimäki also was involved in calling in multiple fake bomb threats and “swatting” incidents — reporting fake hostage situations at an address to prompt a heavily armed police response to that location.
Ville Tapio, the former CEO of Vastaamo, was fired and also prosecuted following the breach. Ransom_man bragged about Vastaamo’s sloppy security, noting the company had used the laughably weak username and password “root/root” to protect sensitive patient records.
Investigators later found Vastaamo had originally been hacked in 2018 and again in 2019. In April 2023, a Finnish court handed down a three-month sentence for Tapio, but that sentence was suspended because he had no previous criminal record.
The European Commission has launched formal proceedings against Meta, alleging failure to properly monitor distribution by "foreign actors" of political misinformation before June's European elections.…
Apple's grudging accommodation of European antitrust rules by allowing third-party app stores on iPhones has left users of its Safari browser exposed to potential web activity tracking.…
The FCC on Monday fined four major US telcos almost $200 million for "illegally" selling subscribers' location information to data brokers.…
Google says it stopped 2.28 million Android apps from being published in its official Play Store last year because they violated security rules.…
The U.S. Federal Communications Commission (FCC) today levied fines totaling nearly $200 million against the four major carriers — including AT&T, Sprint, T-Mobile and Verizon — for illegally sharing access to customers’ location information without consent.
![]()
The fines mark the culmination of a more than four-year investigation into the actions of the major carriers. In February 2020, the FCC put all four wireless providers on notice that their practices of sharing access to customer location data were likely violating the law.
The FCC said it found the carriers each sold access to its customers’ location information to ‘aggregators,’ who then resold access to the information to third-party location-based service providers.
“In doing so, each carrier attempted to offload its obligations to obtain customer consent onto downstream recipients of location information, which in many instances meant that no valid customer consent was obtained,” an FCC statement on the action reads. “This initial failure was compounded when, after becoming aware that their safeguards were ineffective, the carriers continued to sell access to location information without taking reasonable measures to protect it from unauthorized access.”
The FCC’s findings against AT&T, for example, show that AT&T sold customer location data directly or indirectly to at least 88 third-party entities. The FCC found Verizon sold access to customer location data (indirectly or directly) to 67 third-party entities. Location data for Sprint customers found its way to 86 third-party entities, and to 75 third-parties in the case of T-Mobile customers.
The commission said it took action after Sen. Ron Wyden (D-Ore.) sent a letter to the FCC detailing how a company called Securus Technologies had been selling location data on customers of virtually any major mobile provider to law enforcement officials.
That same month, KrebsOnSecurity broke the news that LocationSmart — a data aggregation firm working with the major wireless carriers — had a free, unsecured demo of its service online that anyone could abuse to find the near-exact location of virtually any mobile phone in North America.
The carriers promised to “wind down” location data sharing agreements with third-party companies. But in 2019, reporting at Vice.com showed that little had changed, detailing how reporters were able to locate a test phone after paying $300 to a bounty hunter who simply bought the data through a little-known third-party service.
Sen. Wyden said no one who signed up for a cell plan thought they were giving permission for their phone company to sell a detailed record of their movements to anyone with a credit card.
“I applaud the FCC for following through on my investigation and holding these companies accountable for putting customers’ lives and privacy at risk,” Wyden said in a statement today.
The FCC fined Sprint and T-Mobile $12 million and $80 million respectively. AT&T was fined more than $57 million, while Verizon received a $47 million penalty. Still, these fines represent a tiny fraction of each carrier’s annual revenues. For example, $47 million is less than one percent of Verizon’s total wireless service revenue in 2023, which was nearly $77 billion.
The fine amounts vary because they were calculated based in part on the number of days that the carriers continued sharing customer location data after being notified that doing so was illegal (the agency also considered the number of active third-party location data sharing agreements). The FCC notes that AT&T and Verizon each took more than 320 days from the publication of the Times story to wind down their data sharing agreements; T-Mobile took 275 days; Sprint kept sharing customer location data for 386 days.
Update, 6:25 p.m. ET: Clarified that the FCC launched its investigation at the request of Sen. Wyden.
Updated Canadian pharmacy chain London Drugs closed all of its stores over the weekend until further notice following a "cybersecurity incident."…
The French government has tabled an offer to buy key assets of ailing IT giant Atos after the company late last week almost doubled its estimate of the cash it will need to stay afloat in the near future.…
Smart device manufacturers will have to play by new rules in the UK as of today, with laws coming into force to make it more difficult for cybercriminals to break into hardware such as phones and tablets.…
The UK Competition and Markets Authority (CMA) still has privacy and competition concerns about Google's Privacy Sandbox advertising toolkit, which explains why the ad giant recently again delayed its plan to drop third-party cookies in Chrome until 2025.…
Sponsored Feature As business enters the 2020s, organizations find themselves protecting fast-expanding digital estates using security concepts that are decades old.…
Updated - Infosec in brief They say sunlight is the best disinfectant, and that appears to have been true in the case of Discord data harvesting site Spy.pet – as it was recently and swiftly dismantled after its existence and purpose became known.…

Banks. They screw us on interest rates, they screw us on fees and they screw us on passwords. Remember the old "bank grade security" adage? I took this saying to task almost a decade ago now but it seems that at least as far as password advice goes, they really haven't learned. This week, Commbank is telling people to use a password manager but just not for their bank password, and ANZ bank is forcing people to rotate their passwords once a year because, uh, hackers? Ah well, as I always end up lamenting, it's a great time to be in this industry! 🤣
