The rapper and social media personality Punchmade Dev is perhaps best known for his flashy videos singing the praises of a cybercrime lifestyle. With memorable hits such as “Internet Swiping” and “Million Dollar Criminal” earning millions of views, Punchmade has leveraged his considerable following to peddle tutorials on how to commit financial crimes online. But until recently, there wasn’t much to support a conclusion that Punchmade was actually doing the cybercrime things he promotes in his songs.

Images from Punchmade Dev’s Twitter/X account show him displaying bags of cash and wearing a functional diamond-crusted payment card skimmer.
Punchmade Dev’s most controversial mix — a rap called “Wire Fraud Tutorial” — was taken down by Youtube last summer for violating the site’s rules. Punchmade shared on social media that the video’s removal was prompted by YouTube receiving a legal process request from law enforcement officials.
The 24-year-old rapper told reporters he wasn’t instructing people how to conduct wire fraud, but instead informing his fans on how to avoid being victims of wire fraud. However, this is difficult to discern from listening to the song, which sounds very much like a step-by-step tutorial on how to commit wire fraud.
“Listen up, I’m finna show y’all how to hit a bank,” Wire Fraud Tutorial begins. “Just pay attention, this is a quick way to jug in any state. First you wanna get a bank log from a trusted site. Do your research because the information must be right.”
And even though we’re talking about an individual who regularly appears in videos wearing a half-million dollars worth of custom jewelry draped around his arm and neck (including the functional diamond-encrusted payment card skimming device pictured above), there’s never been much evidence that Punchmade was actually involved in committing cybercrimes himself. Even his most vocal critics acknowledged that the whole persona could just be savvy marketing.
That changed recently when Punchmade’s various video and social media accounts began promoting a new web shop that is selling stolen payment cards and identity data, as well as hacked financial accounts and software for producing counterfeit checks.
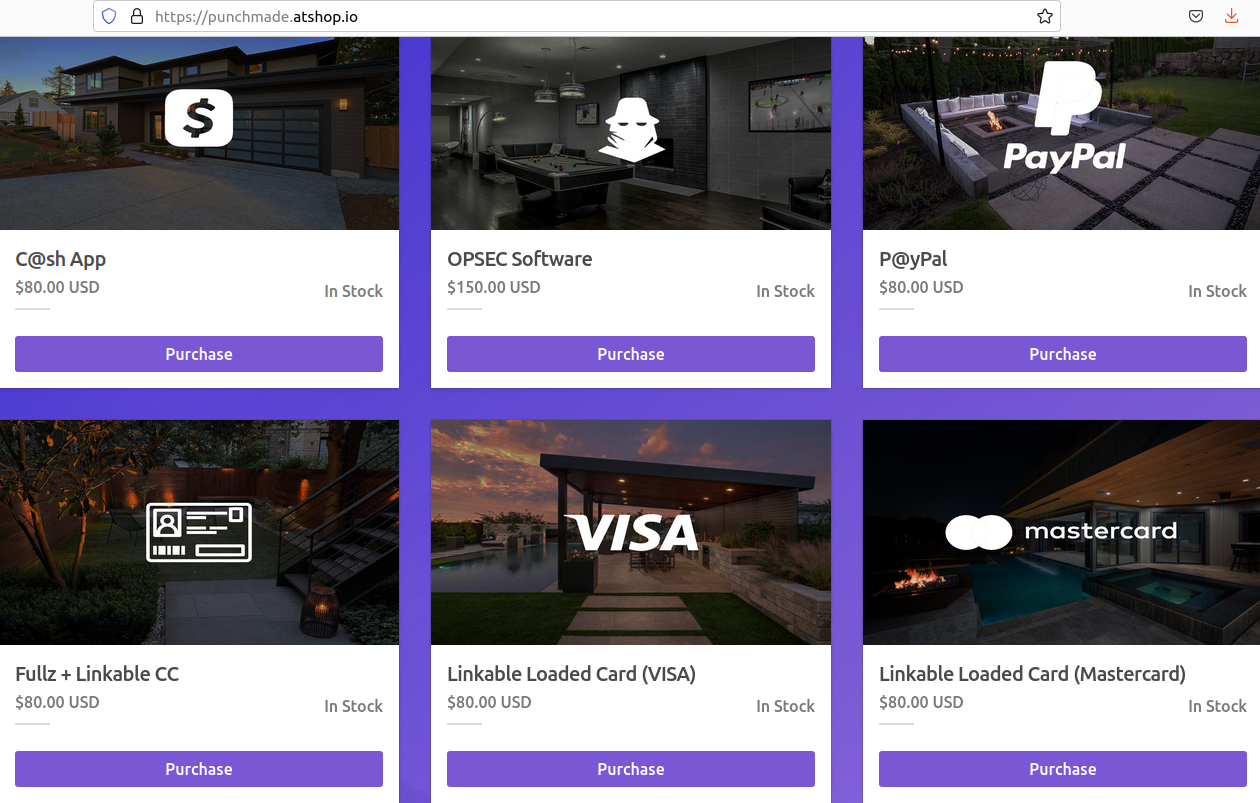
Punchmade Dev’s shop.
The official Punchmadedev account on Instagram links to many of the aforementioned rap videos and tutorials on cybercriming, as well as to Punchmadedev’s other profiles and websites. Among them is mainpage[.]me/punchmade, which includes the following information for “Punchmade Empire ®”
-212,961 subscribers
#1 source on Telegram
Contact: @whopunchmade
24/7 shop: https://punchmade[.]atshop[.]io
Visiting that @whopunchmade Telegram channel shows this user is promoting punchmade[.]atshop[.]io, which is currently selling hacked bank accounts and payment cards with high balances.

Clicking “purchase” on the C@sh App offering, for example, shows that for $80 the buyer will receive logins to Cash App accounts with balances between $3,000 and $5,000. “If you buy this item you’ll get my full support on discord/telegram if there is a problem!,” the site promises. Purchases can be made in cryptocurrencies, and checking out prompts one to continue payment at Coinbase.com.
Another item for sale, “Fullz + Linkable CC,” promises “ID Front + Back, SSN with 700+ Credit Score, and Linkable CC” or credit card. That also can be had for $80 in crypto.
Punchmade has fashioned his public persona around a collection of custom-made, diamond-covered necklaces that are as outlandish and gaudy as they are revelatory. My favorite shot from one of Punchmade’s videos features at least three of these monstrosities: One appears to be a boring old diamond and gold covered bitcoin, but the other two necklaces tell us something about where Punchmade is from:

Notice the University of Kentucky logo, and the Lexington, Ky skyline.
One of them includes the logo and mascot of the University of Kentucky. The other, an enormous diamond studded skyline, appears to have been designed based on the skyline in Lexington, Ky:

The “About” page on Punchmade Dev’s Spotify profile describes him as “an American artist, rapper, musician, producer, director, entrepreneur, actor and investor.” “Punchmade Dev is best known for his creative ways to use technology, video gaming, and social media to build a fan base,” the profile continues.
The profile explains that he launched his own record label in 2021 called Punchmade Records, where he produces his own instrumentals and edits his own music videos.
A search on companies that include the name “punchmade” at the website of the Kentucky Secretary of State brings up just one record: OBN Group LLC, in Lexington, Ky. This November 2021 record includes a Certificate of Assumed Name, which shows that Punchmade LLC is the assumed name of OBN Group LLC.
The president of OBN Group LLC is listed as Devon Turner. A search on the Secretary of State website for other businesses tied to Devon Turner reveals just one other record: A now-defunct entity called DevTakeFlightBeats Inc.
The breach tracking service Constella Intelligence finds that Devon Turner from Lexington, Ky. used the email address obndevpayments@gmail.com. A lookup on this email at DomainTools.com shows it was used to register the domain foreverpunchmade[.]com, which is registered to a Devon Turner in Lexington, Ky. A copy of this site at archive.org indicates it once sold Punchmade Dev-branded t-shirts and other merchandise.
Mr. Turner did not respond to multiple requests for comment.
Searching online for Devon Turner and “Punchmade” brings up a video from @brainjuiceofficial, a YouTube channel that focuses on social media celebrities. @Brainjuiceofficial says Turner was born in October 2000, the oldest child of a single mother of five whose husband was not in the picture.

Devon Turner, a.k.a. “Punchmade Dev,” in an undated photo.
The video says the six-foot five Turner played basketball, track and football in high school, but that he gradually became obsessed with playing the video game NBA 2K17 and building a following of people watching him play the game competitively online.
According to this brief documentary, Turner previously streamed his NBA 2K17 videos on a YouTube channel called DevTakeFlight, although he originally went by the nickname OBN Dev.
“Things may eventually catch up to Devon if he isn’t careful,” @Brainjuiceofficial observed, noting that Turner has been shot at before, and also robbed at an ATM while flexing a bunch of cash for a picture and wearing $500k in jewelry. “Although you have a lot of people that are into what you do, there are a lot of people waiting for you to slip up.”
A California man who lost $100,000 in a 2021 SIM-swapping attack is suing the unknown holder of a cryptocurrency wallet that harbors his stolen funds. The case is thought to be the first in which a federal court has recognized the use of information included in a bitcoin transaction — such as a link to a civil claim filed in federal court — as reasonably likely to provide notice of the lawsuit to the defendant. Experts say the development could make it easier for victims of crypto heists to recover stolen funds through the courts without having to wait years for law enforcement to take notice or help.

Ryan Dellone, a healthcare worker in Fresno, Calif., asserts that thieves stole his bitcoin on Dec. 14, 2021, by executing an unauthorized SIM-swap that involved an employee at his mobile phone provider who switched Dellone’s phone number over to a new device the attackers controlled.
Dellone says the crooks then used his phone number to break into his account at Coinbase and siphon roughly $100,000 worth of cryptocurrencies. Coinbase is also named as a defendant in the lawsuit, which alleges the company ignored multiple red flags, and that it should have detected and stopped the theft. Coinbase did not respond to requests for comment.
Working with experts who track the flow of funds stolen in cryptocurrency heists, Dellone’s lawyer Ethan Mora identified a bitcoin wallet that was the ultimate destination of his client’s stolen crypto. Mora says his client has since been made aware that the bitcoin address in question is embroiled in an ongoing federal investigation into a cryptocurrency theft ring.
Mora said it’s unclear if the bitcoin address that holds his client’s stolen money is being held by the government or by the anonymous hackers. Nevertheless, he is pursuing a novel legal strategy that allows his client to serve notice of the civil suit to that bitcoin address — and potentially win a default judgment to seize his client’s funds within — without knowing the identity of his attackers or anything about the account holder.
In a civil lawsuit seeking monetary damages, a default judgment is usually entered on behalf of the plaintiff if the defendant fails to respond to the complaint within a specified time. Assuming that the cybercriminals who stole the money don’t dispute Dellone’s claim, experts say the money could be seized by cryptocurrency exchanges if the thieves ever tried to move it or spend it.
The U.S. courts have generally held that if you’re going to sue someone, you have to provide some kind of meaningful and timely communication about that lawsuit to the defendant in a way that is reasonably likely to provide them notice.
Not so long ago, you had track down your defendant and hire someone to physically serve them with a copy of the court papers. But legal experts say the courts have evolved their thinking in recent years about what constitutes meaningful service, and now allow notification via email.
On Dec. 14, 2023, a federal judge in the Eastern District of California granted Dellone permission to serve notice of his lawsuit directly to the suspected hackers’ bitcoin address — using a short message that was attached to roughly $100 worth of bitcoin Mora sent to the address.
Bitcoin transactions are public record, and each transaction can be sent along with an optional short message. The message uses what’s known as an “OP RETURN,” or an instruction of the Bitcoin scripting language that allows users to attach metadata to a transaction — and thus save it on the blockchain.
In the $100 bitcoin transaction Mora sent to the disputed bitcoin address, the OP RETURN message read: “OSERVICE – SUMMONS, COMPLAINT U.S. Dist. E.D. Cal. LINK: t.ly/123cv01408_service,” which is a short link to a copy of the lawsuit hosted on Google Drive.
“The courts are adapting to the new style of service of process,” said Mark Rasch, a former federal prosecutor at the U.S. Department of Justice. “And that’s helpful and useful and necessary.”
Rasch said Mora’s strategy could force the government to divulge information about their case, or else explain to a judge why the plaintiff shouldn’t be able to recover their stolen funds without further delay. Rasch said it could be that Dellone’s stolen crypto was seized as part of a government asset forfeiture, but that either way there is no reason Uncle Sam should hold some cybercrime victims’ life savings indefinitely.
“The government doesn’t need the crypto as evidence, but in a forfeiture action the money goes to the government,” Rasch said. “But it was never the government’s money, and that doesn’t help the victim. The government should be providing information to the victims of cryptocurrency theft so that their attorneys can go get the money back themselves.”
Nick Bax is a security researcher who specializes in tracing the labyrinthine activity of criminals trying to use cryptocurrency exchanges and other financial instruments to launder the proceeds of cybercrime. Bax said Mora’s method could allow more victims to stake legitimate legal claims to their stolen funds.
“If you get a default judgment against a bitcoin address, for example, and then down the road that bitcoin gets sent to an exchange that complies with or abides by U.S. court orders, then it’s yours,” Bax said. “I’ve seen funds with a court order on them get frozen by the exchanges that decided it made sense to comply with orders from a U.S. federal court.”
Bax’s research was featured in a Sept. 2023 story here about how experts now believe it’s likely hackers are cracking open some of the password vaults stolen in the 2022 data breach at LastPass.
“I’ve talked to a lot victims who have had life-changing amounts of money being seized and would like that money back,” Bax said. “A big goal here is just making civil cases more efficient. Because then people can help themselves and they don’t need to rely solely on law enforcement with its limited resources. And that’s really the goal: To scale this and make it economically viable.”
While Dellone’s lawsuit may be the first time anyone has obtained approval from a federal judge to use bitcoin to notify another party of a civil action, the technique has been used in several recent unrelated cases involving other cryptocurrencies, including Ethereum and NFTs.
The law firm DLAPiper writes that in November 2022, the U.S. District Court for the Southern District of Florida “authorized service of a lawsuit seeking the recovery of stolen digital assets by way of a non-fungible token or NFT containing the text of the complaint and summons, as well as a hyperlink to a website created by the plaintiffs containing all pleadings and orders in the action.”
In approving Dellone’s request for service via bitcoin transaction, the judge overseeing the case cited a recent New York Superior Court ruling in a John Doe case brought by victims seeking to unmask the crooks behind a $1.3 million cyberheist.
In the New York case, the state trial court found it was acceptable for the plaintiffs to serve notice of the suit via cryptocurrency transactions because the defendants regularly used the Blockchain address to which the tokens were sent, and had recently done so. Also, the New York court found that because the account in question contained a significant sum of money, it was unlikely to be abandoned or forgotten.
“Thus the court inferred the defendants were likely to access the account in the future,” wrote Judge Helena M. March-Kuchta, for the Eastern District of California, summarizing the New York case. “Finally, the plaintiff had no alternative means of contacting these unknown defendants.”
Experts say regardless of the reason for a cryptocurrency theft or loss — whether it’s from a romance scam or a straight-up digital mugging — it’s important for victims to file an official report both with their local police and with the FBI’s Internet Crime Complaint Center (ic3.gov). The IC3 collects reports on cybercrime and sometimes bundles victim reports into cases for DOJ/FBI prosecutors and investigators.
The hard truth is that most victims will never see their stolen funds again. But sometimes federal investigators win minor victories and manage to seize or freeze crypto assets that are known to be associated with specific crimes and criminals. In those cases, the government will eventually make an effort to find, contact and in some cases remunerate known victims.
It might take many years for this process to unfold. But if and when they do make that effort, federal investigators are likely to focus their energies and attention responding to victims who staked a claim and can support it with documentation.
But have no illusions that any of this is likely to happen in a timeframe that is meaningful to victims in the short run. For example, in 2013 the U.S. government seized the assets of the virtual currency Liberty Reserve, massively disrupting a major vehicle for laundering the proceeds of cybercrime and other illegal activities.
When the government offered remuneration to Liberty Reserve account holders who wished to make a financial loss claim and supply supporting documentation, KrebsOnSecurity filed a claim. There wasn’t money much in my Liberty Reserve account; I simply wanted to know how long it would take for federal investigators to follow up on my claim, or indeed if they would at all.
In 2020 KrebsOnSecurity was contacted by an investigator with the U.S. Internal Revenue Service (IRS) who was seeking to discuss my claim. The investigator said they would have called sooner, but that it had taken that long for the IRS to gain legal access to the funds seized in the 2013 Liberty Reserve takedown.