One of the oldest malware tricks in the book — hacked websites claiming visitors need to update their Web browser before they can view any content — has roared back to life in the past few months. New research shows the attackers behind one such scheme have developed an ingenious way of keeping their malware from being taken down by security experts or law enforcement: By hosting the malicious files on a decentralized, anonymous cryptocurrency blockchain.
In August 2023, security researcher Randy McEoin blogged about a scam he dubbed ClearFake, which uses hacked WordPress sites to serve visitors with a page that claims you need to update your browser before you can view the content.
The fake browser alerts are specific to the browser you’re using, so if you’re surfing the Web with Chrome, for example, you’ll get a Chrome update prompt. Those who are fooled into clicking the update button will have a malicious file dropped on their system that tries to install an information stealing trojan.
Earlier this month, researchers at the Tel Aviv-based security firm Guardio said they tracked an updated version of the ClearFake scam that included an important evolution. Previously, the group had stored its malicious update files on Cloudflare, Guardio said.
But when Cloudflare blocked those accounts the attackers began storing their malicious files as cryptocurrency transactions in the Binance Smart Chain (BSC), a technology designed to run decentralized apps and “smart contracts,” or coded agreements that execute actions automatically when certain conditions are met.
Nati Tal, head of security at Guardio Labs, the research unit at Guardio, said the malicious scripts stitched into hacked WordPress sites will create a new smart contract on the BSC Blockchain, starting with a unique, attacker-controlled blockchain address and a set of instructions that defines the contract’s functions and structure. When that contract is queried by a compromised website, it will return an obfuscated and malicious payload.
“These contracts offer innovative ways to build applications and processes,” Tal wrote along with his Guardio colleague Oleg Zaytsev. “Due to the publicly accessible and unchangeable nature of the blockchain, code can be hosted ‘on-chain’ without the ability for a takedown.”
Tal said hosting malicious files on the Binance Smart Chain is ideal for attackers because retrieving the malicious contract is a cost-free operation that was originally designed for the purpose of debugging contract execution issues without any real-world impact.
“So you get a free, untracked, and robust way to get your data (the malicious payload) without leaving traces,” Tal said.
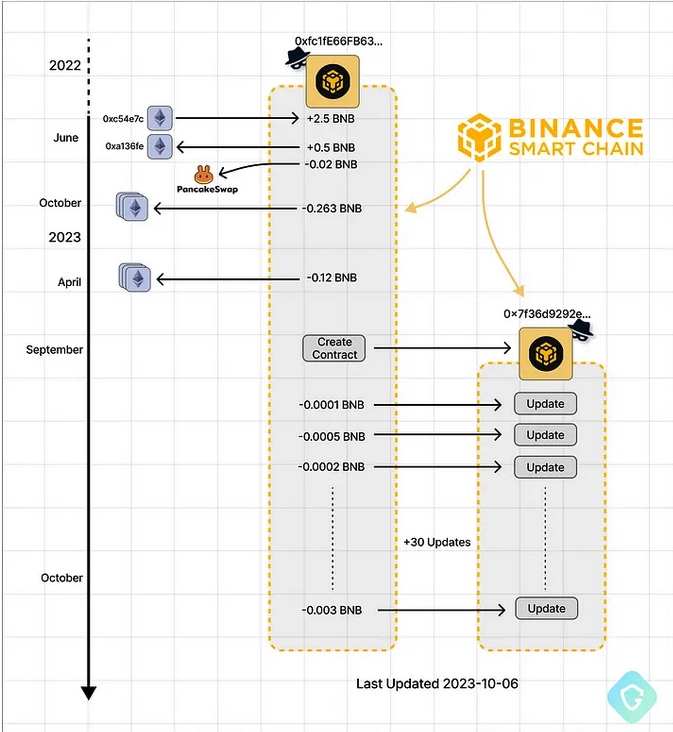
Attacker-controlled BSC addresses — from funding, contract creation, and ongoing code updates. Image: Guardio
In response to questions from KrebsOnSecurity, the BNB Smart Chain (BSC) said its team is aware of the malware abusing its blockchain, and is actively addressing the issue. The company said all addresses associated with the spread of the malware have been blacklisted, and that its technicians had developed a model to detect future smart contracts that use similar methods to host malicious scripts.
“This model is designed to proactively identify and mitigate potential threats before they can cause harm,” BNB Smart Chain wrote. “The team is committed to ongoing monitoring of addresses that are involved in spreading malware scripts on the BSC. To enhance their efforts, the tech team is working on linking identified addresses that spread malicious scripts to centralized KYC [Know Your Customer] information, when possible.”
Guardio says the crooks behind the BSC malware scheme are using the same malicious code as the attackers that McEoin wrote about in August, and are likely the same group. But a report published today by email security firm Proofpoint says the company is currently tracking at least four distinct threat actor groups that use fake browser updates to distribute malware.
Proofpoint notes that the core group behind the fake browser update scheme has been using this technique to spread malware for the past five years, primarily because the approach still works well.
“Fake browser update lures are effective because threat actors are using an end-user’s security training against them,” Proofpoint’s Dusty Miller wrote. “In security awareness training, users are told to only accept updates or click on links from known and trusted sites, or individuals, and to verify sites are legitimate. The fake browser updates abuse this training because they compromise trusted sites and use JavaScript requests to quietly make checks in the background and overwrite the existing website with a browser update lure. To an end user, it still appears to be the same website they were intending to visit and is now asking them to update their browser.”
More than a decade ago, this site published Krebs’s Three Rules for Online Safety, of which Rule #1 was, “If you didn’t go looking for it, don’t install it.” It’s nice to know that this technology-agnostic approach to online safety remains just as relevant today.
Amir Golestan, the 40-year-old CEO of the Charleston, S.C. based technology company Micfo LLC, has been sentenced to five years in prison for wire fraud. Golestan’s sentencing comes nearly two years after he pleaded guilty to using an elaborate network of phony companies to secure more than 735,000 Internet Protocol (IP) addresses from the American Registry for Internet Numbers (ARIN), the nonprofit which oversees IP addresses assigned to entities in the U.S., Canada, and parts of the Caribbean.

Amir Golestan, the former CEO of Micfo.
In 2018, ARIN sued Golestan and Micfo, alleging they had obtained hundreds of thousands of IP addresses under false pretenses. ARIN and Micfo settled that dispute in arbitration, with Micfo returning most of the addresses that it hadn’t already sold.
ARIN’s civil case caught the attention of federal prosecutors in South Carolina, who in May 2019 filed criminal wire fraud charges against Golestan, alleging he’d orchestrated a network of shell companies and fake identities to prevent ARIN from knowing the addresses were all going to the same buyer.
Prosecutors showed that each of those shell companies involved the production of notarized affidavits in the names of people who didn’t exist. As a result, the government was able to charge Golestan with 20 counts of wire fraud — one for each payment made by the phony companies that bought the IP addresses from ARIN.
Golestan initially sought to fight those charges. But on just the second day of his trial in November 2021, Golestan changed his mind and pleaded guilty to 20 counts of wire fraud in connection with the phantom companies he used to secure the IP addresses. Prosecutors estimated those addresses were valued at between $10 million and $14 million.
ARIN says the 5-year sentence handed down by the South Carolina judge “sends an important message of deterrence to other parties contemplating fraudulent schemes to obtain or transfer Internet resources.”
“Those who seek to defraud ARIN (or other Regional Internet Registries) are subject to costly and serious civil litigation, criminal charges, and, ultimately, a lengthy term of incarceration,” reads a statement from ARIN on Golestan’s sentencing.
By 2013, a number of Micfo’s customers had landed on the radar of Spamhaus, a group that many network operators rely upon to stem the tide of junk email. Shortly after Spamhaus started blocking Micfo’s IP address ranges, Micfo shifted gears and began reselling IP addresses mainly to companies marketing “virtual private networking” or VPN services that help customers hide their real IP addresses online.
Golestan did not respond to a request for comment. But in a 2020 interview with KrebsOnSecurity, Golestan claimed that Micfo was at one point responsible for brokering roughly 40 percent of the IP addresses used by the world’s largest VPN providers. Throughout that conversation, Golestan maintained his innocence, even as he explained that the creation of the phony companies was necessary to prevent entities like Spamhaus from interfering with his business going forward.
There are fewer than four billion so-called “Internet Protocol version 4” or IPv4 addresses available for use, but the vast majority of them have already been allocated. The global dearth of available IP addresses has turned them into a commodity wherein each IPv4 address can fetch between $15-$25 on the open market.
This has led to boom times for those engaged in the acquisition and sale of IP address blocks, but it has likewise emboldened those who specialize in absconding with and spamming from dormant IP address blocks without permission from the rightful owners.
The U.S Department of Justice says Golestan will serve 60 months in prison, followed by a 2-year term of court-ordered supervision. The Micfo CEO also was ordered to pay nearly $77,000 in restitution to ARIN for its work in assisting federal prosecutors.
Microsoft today issued security updates for more than 100 newly-discovered vulnerabilities in its Windows operating system and related software, including four flaws that are already being exploited. In addition, Apple recently released emergency updates to quash a pair of zero-day bugs in iOS.

Apple last week shipped emergency updates in iOS 17.0.3 and iPadOS 17.0.3 in response to active attacks. The patch fixes CVE-2023-42724, which attackers have been using in targeted attacks to elevate their access on a local device.
Apple said it also patched CVE-2023-5217, which is not listed as a zero-day bug. However, as Bleeping Computer pointed out, this flaw is caused by a weakness in the open-source “libvpx” video codec library, which was previously patched as a zero-day flaw by Google in the Chrome browser and by Microsoft in Edge, Teams, and Skype products. For anyone keeping count, this is the 17th zero-day flaw that Apple has patched so far this year.
Fortunately, the zero-days affecting Microsoft customers this month are somewhat less severe than usual, with the exception of CVE-2023-44487. This weakness is not specific to Windows but instead exists within the HTTP/2 protocol used by the World Wide Web: Attackers have figured out how to use a feature of HTTP/2 to massively increase the size of distributed denial-of-service (DDoS) attacks, and these monster attacks reportedly have been going on for several weeks now.
Amazon, Cloudflare and Google all released advisories today about how they’re addressing CVE-2023-44487 in their cloud environments. Google’s Damian Menscher wrote on Twitter/X that the exploit — dubbed a “rapid reset attack” — works by sending a request and then immediately cancelling it (a feature of HTTP/2). “This lets attackers skip waiting for responses, resulting in a more efficient attack,” Menscher explained.
Natalie Silva, lead security engineer at Immersive Labs, said this flaw’s impact to enterprise customers could be significant, and lead to prolonged downtime.
“It is crucial for organizations to apply the latest patches and updates from their web server vendors to mitigate this vulnerability and protect against such attacks,” Silva said. In this month’s Patch Tuesday release by Microsoft, they have released both an update to this vulnerability, as well as a temporary workaround should you not be able to patch immediately.”
Microsoft also patched zero-day bugs in Skype for Business (CVE-2023-41763) and Wordpad (CVE-2023-36563). The latter vulnerability could expose NTLM hashes, which are used for authentication in Windows environments.
“It may or may not be a coincidence that Microsoft announced last month that WordPad is no longer being updated, and will be removed in a future version of Windows, although no specific timeline has yet been given,” said Adam Barnett, lead software engineer at Rapid7. “Unsurprisingly, Microsoft recommends Word as a replacement for WordPad.”
Other notable bugs addressed by Microsoft include CVE-2023-35349, a remote code execution weakness in the Message Queuing (MSMQ) service, a technology that allows applications across multiple servers or hosts to communicate with each other. This vulnerability has earned a CVSS severity score of 9.8 (10 is the worst possible). Happily, the MSMQ service is not enabled by default in Windows, although Immersive Labs notes that Microsoft Exchange Server can enable this service during installation.
Speaking of Exchange, Microsoft also patched CVE-2023-36778, a vulnerability in all current versions of Exchange Server that could allow attackers to run code of their choosing. Rapid7’s Barnett said successful exploitation requires that the attacker be on the same network as the Exchange Server host, and use valid credentials for an Exchange user in a PowerShell session.
For a more detailed breakdown on the updates released today, see the SANS Internet Storm Center roundup. If today’s updates cause any stability or usability issues in Windows, AskWoody.com will likely have the lowdown on that.
Please consider backing up your data and/or imaging your system before applying any updates. And feel free to sound off in the comments if you experience any difficulties as a result of these patches.
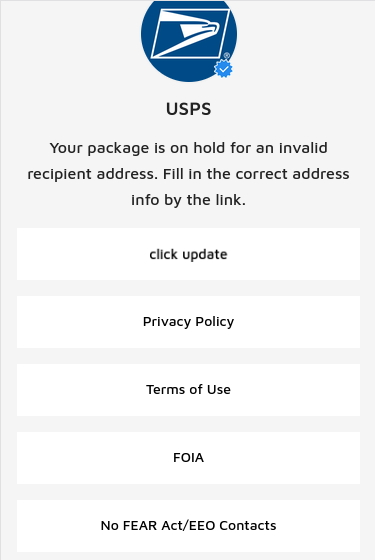
The fake USPS phishing page.
Recent weeks have seen a sizable uptick in the number of phishing scams targeting U.S. Postal Service (USPS) customers. Here’s a look at an extensive SMS phishing operation that tries to steal personal and financial data by spoofing the USPS, as well as postal services in at least a dozen other countries.
KrebsOnSecurity recently heard from a reader who received an SMS purporting to have been sent by the USPS, saying there was a problem with a package destined for the reader’s address. Clicking the link in the text message brings one to the domain usps.informedtrck[.]com.
The landing page generated by the phishing link includes the USPS logo, and says “Your package is on hold for an invalid recipient address. Fill in the correct address info by the link.” Below that message is a “Click update” button that takes the visitor to a page that asks for more information.
The remaining buttons on the phishing page all link to the real USPS.com website. After collecting your address information, the fake USPS site goes on to request additional personal and financial data.
This phishing domain was recently registered and its WHOIS ownership records are basically nonexistent. However, we can find some compelling clues about the extent of this operation by loading the phishing page in Developer Tools, a set of debugging features built into Firefox, Chrome and Safari that allow one to closely inspect a webpage’s code and operations.
Check out the bottom portion of the screenshot below, and you’ll notice that this phishing site fails to load some external resources, including an image from a link called fly.linkcdn[.]to.
A search on this domain at the always-useful URLscan.io shows that fly.linkcdn[.]to is tied to a slew of USPS-themed phishing domains. Here are just a few of those domains (links defanged to prevent accidental clicking):
usps.receivepost[.]com
usps.informedtrck[.]com
usps.trckspost[.]com
postreceive[.]com
usps.trckpackages[.]com
usps.infortrck[.]com
usps.quicktpos[.]com
usps.postreceive].]com
usps.revepost[.]com
trackingusps.infortrck[.]com
usps.receivepost[.]com
usps.trckmybusi[.]com
postreceive[.]com
tackingpos[.]com
usps.trckstamp[.]com
usa-usps[.]shop
usps.infortrck[.]com
unlistedstampreceive[.]com
usps.stampreceive[.]com
usps.stamppos[.]com
usps.stampspos[.]com
usps.trckmypost[.]com
usps.trckintern[.]com
usps.tackingpos[.]com
usps.posinformed[.]com
As we can see in the screenshot below, the developer tools console for informedtrck[.]com complains that the site is unable to load a Google Analytics code — UA-80133954-3 — which apparently was rejected for pointing to an invalid domain.
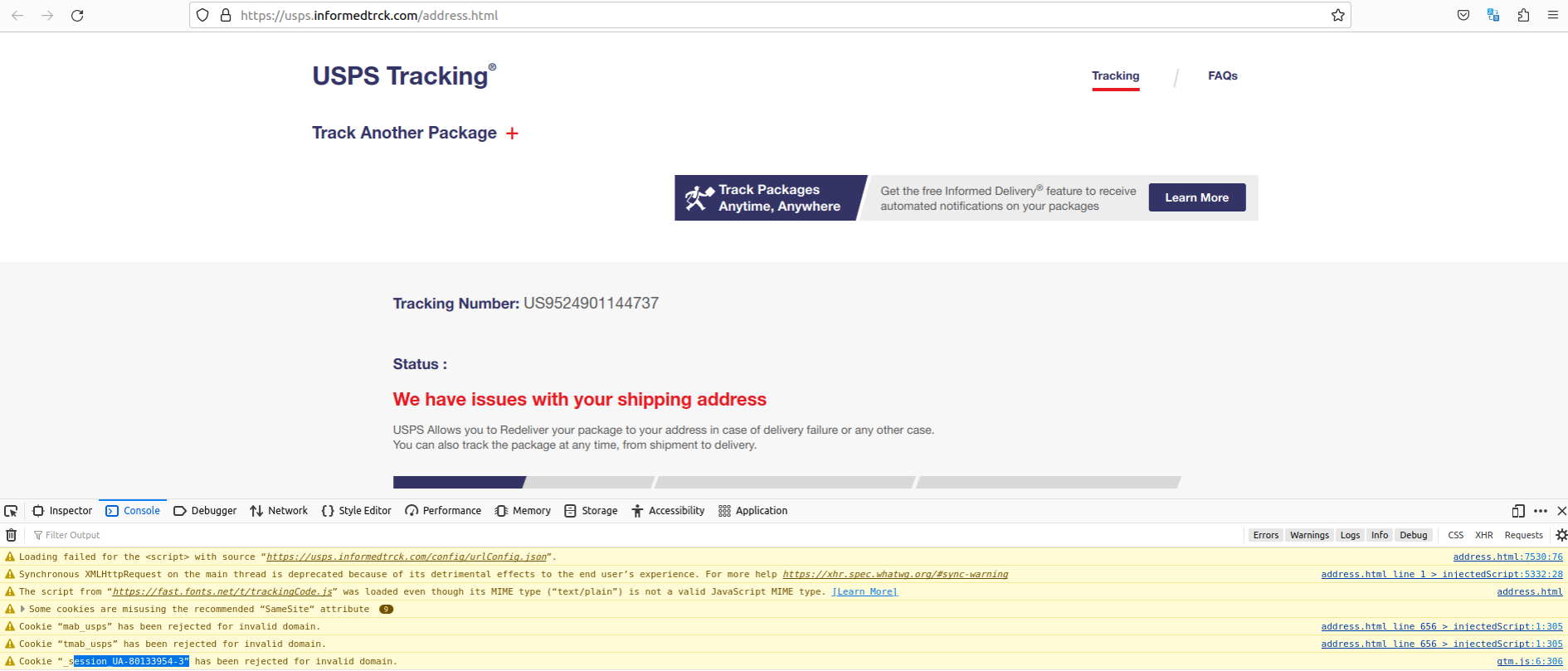
Notice the highlighted Google Analytics code exposed by a faulty Javascript element on the phishing website. Click to enlarge. That code actually belongs to the USPS.
The valid domain for that Google Analytics code is the official usps.com website. According to dnslytics.com, that same analytics code has shown up on at least six other nearly identical USPS phishing pages dating back nearly as many years, including onlineuspsexpress[.]com, which DomainTools.com says was registered way back in September 2018 to an individual in Nigeria.
A different domain with that same Google Analytics code that was registered in 2021 is peraltansepeda[.]com, which archive.org shows was running a similar set of phishing pages targeting USPS users. DomainTools.com indicates this website name was registered by phishers based in Indonesia.
DomainTools says the above-mentioned USPS phishing domain stamppos[.]com was registered in 2022 via Singapore-based Alibaba.com, but the registrant city and state listed for that domain says “Georgia, AL,” which is not a real location.
Alas, running a search for domains registered through Alibaba to anyone claiming to reside in Georgia, AL reveals nearly 300 recent postal phishing domains ending in “.top.” These domains are either administrative domains obscured by a password-protected login page, or are .top domains phishing customers of the USPS as well as postal services serving other countries.
Those other nations include the Australia Post, An Post (Ireland), Correos.es (Spain), the Costa Rican post, the Chilean Post, the Mexican Postal Service, Poste Italiane (Italy), PostNL (Netherlands), PostNord (Denmark, Norway and Sweden), and Posti (Finland). A complete list of these domains is available here (PDF).
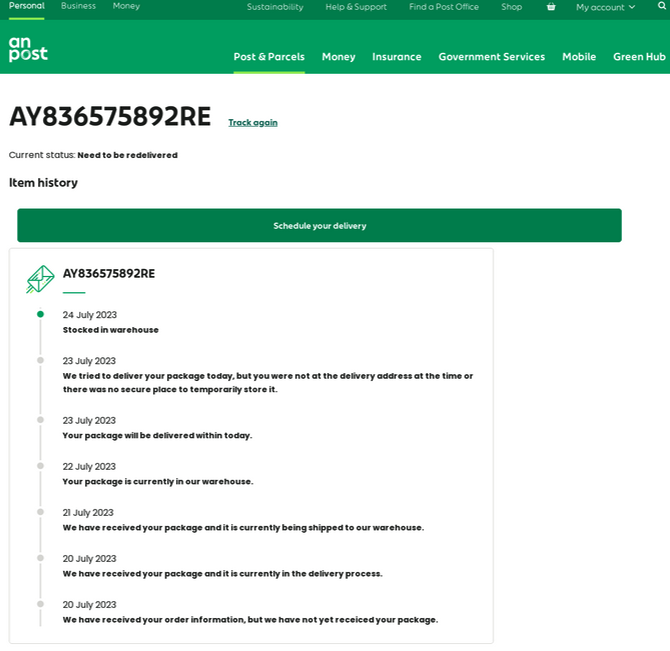
A phishing page targeting An Post, the state-owned provider of postal services in Ireland.
The Georgia, AL domains at Alibaba also encompass several that spoof sites claiming to collect outstanding road toll fees and fines on behalf of the governments of Australia, New Zealand and Singapore.
An anonymous reader wrote in to say they submitted fake information to the above-mentioned phishing site usps.receivepost[.]com via the malware sandbox any.run. A video recording of that analysis shows that the site sends any submitted data via an automated bot on the Telegram instant messaging service.
The traffic analysis just below the any.run video shows that any data collected by the phishing site is being sent to the Telegram user @chenlun, who offers to sell customized source code for phishing pages. From a review of @chenlun’s other Telegram channels, it appears this account is being massively spammed at the moment — possibly thanks to public attention brought by this story.
Meanwhile, researchers at DomainTools recently published a report on an apparently unrelated but equally sprawling SMS-based phishing campaign targeting USPS customers that appears to be the work of cybercriminals based in Iran.
Phishers tend to cast a wide net and often spoof entities that are broadly used by the local population, and few brands are going to have more household reach than domestic mail services. In June, the United Parcel Service (UPS) disclosed that fraudsters were abusing an online shipment tracking tool in Canada to send highly targeted SMS phishing messages that spoofed the UPS and other brands.
With the holiday shopping season nearly upon us, now is a great time to remind family and friends about the best advice to sidestep phishing scams: Avoid clicking on links or attachments that arrive unbidden in emails, text messages and other mediums. Most phishing scams invoke a temporal element that warns of negative consequences should you fail to respond or act quickly.
If you’re unsure whether the message is legitimate, take a deep breath and visit the site or service in question manually — ideally, using a browser bookmark so as to avoid potential typosquatting sites.
Update: Added information about the Telegram bot and any.run analysis.
The victim shaming site operated by the Snatch ransomware group is leaking data about its true online location and internal operations, as well as the Internet addresses of its visitors, KrebsOnSecurity has found. The leaked data suggest that Snatch is one of several ransomware groups using paid ads on Google.com to trick people into installing malware disguised as popular free software, such as Microsoft Teams, Adobe Reader, Mozilla Thunderbird, and Discord.
First spotted in 2018, the Snatch ransomware group has published data stolen from hundreds of organizations that refused to pay a ransom demand. Snatch publishes its stolen data at a website on the open Internet, and that content is mirrored on the Snatch team’s darknet site, which is only reachable using the global anonymity network Tor.
KrebsOnSecurity has learned that Snatch’s darknet site exposes its “server status” page, which includes information about the true Internet addresses of users accessing the website.
Refreshing this page every few seconds shows that the Snatch darknet site generates a decent amount of traffic, often attracting thousands of visitors each day. But by far the most frequent repeat visitors are coming from Internet addresses in Russia that either currently host Snatch’s clear web domain names or recently did.
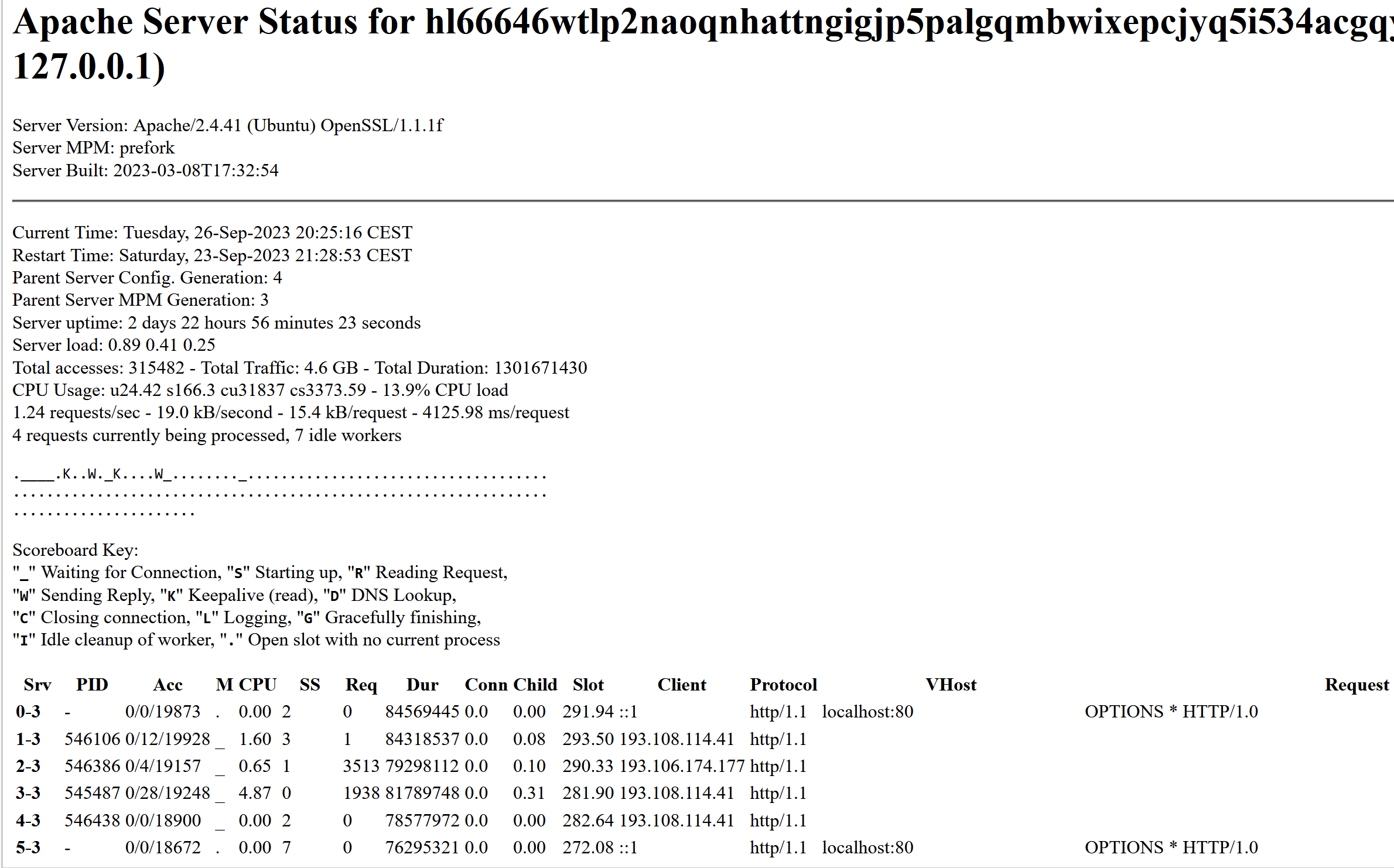
The Snatch ransomware gang’s victim shaming site on the darknet is leaking data about its visitors. This “server status” page says that Snatch’s website is on Central European Summer Time (CEST) and is powered by OpenSSL/1.1.1f, which is no longer supported by security updates.
Probably the most active Internet address accessing Snatch’s darknet site is 193.108.114[.]41, which is a server in Yekaterinburg, Russia that hosts several Snatch domains, including snatchteam[.]top, sntech2ch[.]top, dwhyj2[.]top and sn76930193ch[.]top. It could well be that this Internet address is showing up frequently because Snatch’s clear-web site features a toggle button at the top that lets visitors switch over to accessing the site via Tor.
Another Internet address that showed up frequently in the Snatch server status page was 194.168.175[.]226, currently assigned to Matrix Telekom in Russia. According to DomainTools.com, this address also hosts or else recently hosted the usual coterie of Snatch domains, as well as quite a few domains phishing known brands such as Amazon and Cashapp.
The Moscow Internet address 80.66.64[.]15 accessed the Snatch darknet site all day long, and that address also housed the appropriate Snatch clear-web domains. More interestingly, that address is home to multiple recent domains that appear confusingly similar to known software companies, including libreoff1ce[.]com and www-discord[.]com.
This is interesting because the phishing domains associated with the Snatch ransomware gang were all registered to the same Russian name — Mihail Kolesnikov, a name that is somewhat synonymous with recent phishing domains tied to malicious Google ads.
Kolesnikov could be a nod to a Russian general made famous during Boris Yeltsin’s reign. Either way, it’s clearly a pseudonym, but there are some other commonalities among these domains that may provide insight into how Snatch and other ransomware groups are sourcing their victims.
DomainTools says there are more than 1,300 current and former domain names registered to Mihail Kolesnikov between 2013 and July 2023. About half of the domains appear to be older websites advertising female escort services in major cities around the United States (e.g. the now-defunct pittsburghcitygirls[.]com).
The other half of the Kolesnikov websites are far more recent phishing domains mostly ending in “.top” and “.app” that appear designed to mimic the domains of major software companies, including www-citrix[.]top, www-microsofteams[.]top, www-fortinet[.]top, ibreoffice[.]top, www-docker[.]top, www-basecamp[.]top, ccleaner-cdn[.]top, adobeusa[.]top, and www.real-vnc[.]top.
In August 2023, researchers with Trustwave Spiderlabs said they encountered domains registered to Mihail Kolesnikov being used to disseminate the Rilide information stealer trojan.
But it appears multiple crime groups may be using these domains to phish people and disseminate all kinds of information-stealing malware. In February 2023, Spamhaus warned of a huge surge in malicious ads that were hijacking search results in Google.com, and being used to distribute at least five different families of information stealing trojans, including AuroraStealer, IcedID/Bokbot, Meta Stealer, RedLine Stealer and Vidar.
For example, Spamhaus said victims of these malicious ads would search for Microsoft Teams in Google.com, and the search engine would often return a paid ad spoofing Microsoft or Microsoft Teams as the first result — above all other results. The malicious ad would include a logo for Microsoft and at first glance appear to be a safe and trusted place to download the Microsoft Teams client.
However, anyone who clicked on the result was whisked away instead to mlcrosofteams-us[.]top — yet another malicious domain registered to Mr. Kolesnikov. And while visitors to this website may believe they are only downloading the Microsoft Teams client, the installer file includes a copy of the IcedID malware, which is really good at stealing passwords and authentication tokens from the victim’s web browser.
The founder of the Swiss anti-abuse website abuse.ch told Spamhaus it is likely that some cybercriminals have started to sell “malvertising as a service” on the dark web, and that there is a great deal of demand for this service.
In other words, someone appears to have built a very profitable business churning out and promoting new software-themed phishing domains and selling that as a service to other cybercriminals. Or perhaps they are simply selling any stolen data (and any corporate access) to active and hungry ransomware group affiliates.
The tip about the exposed “server status” page on the Snatch darkweb site came from @htmalgae, the same security researcher who alerted KrebsOnSecurity earlier this month that the darknet victim shaming site run by the 8Base ransomware gang was inadvertently left in development mode.
That oversight revealed not only the true Internet address of the hidden 8Base site (in Russia, naturally), but also the identity of a programmer in Moldova who apparently helped to develop the 8Base code.
@htmalgae said the idea of a ransomware group’s victim shaming site leaking data that they did not intend to expose is deliciously ironic.
“This is a criminal group that shames others for not protecting user data,” @htmalgae said. “And here they are leaking their user data.”
All of the malware mentioned in this story is designed to run on Microsoft Windows devices. But Malwarebytes recently covered the emergence of a Mac-based information stealer trojan called AtomicStealer that was being advertised through malicious Google ads and domains that were confusingly similar to software brands.
Please be extra careful when you are searching online for popular software titles. Cracked, pirated copies of major software titles are a frequent source of infostealer infections, as are these rogue ads masquerading as search results. Make sure to double-check you are actually at the domain you believe you’re visiting *before* you download and install anything.
Stay tuned for Part II of this post, which includes a closer look at the Snatch ransomware group and their founder.
Further reading:
@HTMalgae’s list of the top Internet addresses seen accessing Snatch’s darknet site
Ars Technica: Until Further Notice Think Twice Before Using Google to Download Software
Bleeping Computer: Hackers Abuse Google Ads to Spread Malware in Legit Software
In December 2022, KrebsOnSecurity broke the news that a cybercriminal using the handle “USDoD” had infiltrated the FBI‘s vetted information sharing network InfraGard, and was selling the contact information for all 80,000 members. The FBI responded by reverifying InfraGard members and by seizing the cybercrime forum where the data was being sold. But on Sept. 11, 2023, USDoD resurfaced after a lengthy absence to leak sensitive employee data stolen from the aerospace giant Airbus, while promising to visit the same treatment on top U.S. defense contractors.
In a post on the English language cybercrime forum BreachForums, USDoD leaked information on roughly 3,200 Airbus vendors, including names, addresses, phone numbers, and email addresses. USDoD claimed they grabbed the data by using passwords stolen from a Turkish airline employee who had third-party access to Airbus’ systems.
USDoD didn’t say why they decided to leak the data on the 22nd anniversary of the 9/11 attacks, but there was definitely an aircraft theme to the message that accompanied the leak, which concluded with the words, “Lockheed martin, Raytheon and the entire defense contractos [sic], I’m coming for you [expletive].”
Airbus has apparently confirmed the cybercriminal’s account to the threat intelligence firm Hudson Rock, which determined that the Airbus credentials were stolen after a Turkish airline employee infected their computer with a prevalent and powerful info-stealing trojan called RedLine.
Info-stealers like RedLine typically are deployed via opportunistic email malware campaigns, and by secretly bundling the trojans with cracked versions of popular software titles made available online. Credentials stolen by info-stealers often end up for sale on cybercrime shops that peddle purloined passwords and authentication cookies (these logs also often show up in the malware scanning service VirusTotal).
Hudson Rock said it recovered the log files created by a RedLine infection on the Turkish airline employee’s system, and found the employee likely infected their machine after downloading pirated and secretly backdoored software for Microsoft Windows.
Hudson Rock says info-stealer infections from RedLine and a host of similar trojans have surged in recent years, and that they remain “a primary initial attack vector used by threat actors to infiltrate organizations and execute cyberattacks, including ransomware, data breaches, account overtakes, and corporate espionage.”
The prevalence of RedLine and other info-stealers means that a great many consequential security breaches begin with cybercriminals abusing stolen employee credentials. In this scenario, the attacker temporarily assumes the identity and online privileges assigned to a hacked employee, and the onus is on the employer to tell the difference.
In addition to snarfing any passwords stored on or transmitted through an infected system, info-stealers also siphon authentication cookies or tokens that allow one to remain signed-in to online services for long periods of time without having to resupply one’s password and multi-factor authentication code. By stealing these tokens, attackers can often reuse them in their own web browser, and bypass any authentication normally required for that account.
Microsoft Corp. this week acknowledged that a China-backed hacking group was able to steal one of the keys to its email kingdom that granted near-unfettered access to U.S. government inboxes. Microsoft’s detailed post-mortem cum mea culpa explained that a secret signing key was stolen from an employee in an unlucky series of unfortunate events, and thanks to TechCrunch we now know that the culprit once again was “token-stealing malware” on the employee’s system.
In April 2023, the FBI seized Genesis Market, a bustling, fully automated cybercrime store that was continuously restocked with freshly hacked passwords and authentication tokens stolen by a network of contractors who deployed RedLine and other info-stealer malware.
In March 2023, the FBI arrested and charged the alleged administrator of BreachForums (aka Breached), the same cybercrime community where USDoD leaked the Airbus data. In June 2023, the FBI seized the BreachForums domain name, but the forum has since migrated to a new domain.
Unsolicited email continues to be a huge vector for info-stealing malware, but lately the crooks behind these schemes have been gaming the search engines so that their malicious sites impersonating popular software vendors actually appear before the legitimate vendor’s website. So take special care when downloading software to ensure that you are in fact getting the program from the original, legitimate source whenever possible.
Also, unless you really know what you’re doing, please don’t download and install pirated software. Sure, the cracked program might do exactly what you expect it to do, but the chances are good that it is also laced with something nasty. And when all of your passwords are stolen and your important accounts have been hijacked or sold, you will wish you had simply paid for the real thing.