
Domain names ending in “.US” — the top-level domain for the United States — are among the most prevalent in phishing scams, new research shows. This is noteworthy because .US is overseen by the U.S. government, which is frequently the target of phishing domains ending in .US. Also, .US domains are only supposed to be available to U.S. citizens and to those who can demonstrate that they have a physical presence in the United States.
.US is the “country code top-level domain” or ccTLD of the United States. Most countries have their own ccTLDs: .MX for Mexico, for example, or .CA for Canada. But few other major countries in the world have anywhere near as many phishing domains each year as .US.
That’s according to The Interisle Consulting Group, which gathers phishing data from multiple industry sources and publishes an annual report on the latest trends. Interisle’s newest study examined six million phishing reports between May 1, 2022 and April 30, 2023, and found 30,000 .US phishing domains.
.US is overseen by the National Telecommunications and Information Administration (NTIA), an executive branch agency of the U.S. Department of Commerce. However, NTIA currently contracts out the management of the .US domain to GoDaddy, by far the world’s largest domain registrar.
Under NTIA regulations, the administrator of the .US registry must take certain steps to verify that their customers actually reside in the United States, or own organizations based in the U.S. But Interisle found that whatever GoDaddy was doing to manage that vetting process wasn’t working.
“The .US ‘nexus’ requirement theoretically limits registrations to parties with a national connection, but .US had very high numbers of phishing domains,” Interisle wrote. “This indicates a possible problem with the administration or application of the nexus requirements.”
Dean Marks is emeritus executive director for a group called the Coalition for Online Accountability, which has been critical of the NTIA’s stewardship of .US. Marks says virtually all European Union member state ccTLDs that enforce nexus restrictions also have massively lower levels of abuse due to their policies and oversight.
“Even very large ccTLDs, like .de for Germany — which has a far larger market share of domain name registrations than .US — have very low levels of abuse, including phishing and malware,” Marks told KrebsOnSecurity. “In my view, this situation with .US should not be acceptable to the U.S. government overall, nor to the US public.”
Marks said there are very few phishing domains ever registered in other ccTLDs that also restrict registrations to their citizens, such as .HU (Hungary), .NZ (New Zealand), and .FI (Finland), where a connection to the country, a proof of identity, or evidence of incorporation are required.
“Or .LK (Sri Lanka), where the acceptable use policy includes a ‘lock and suspend’ if domains are reported for suspicious activity,” Marks said. “These ccTLDs make a strong case for validating domain registrants in the interest of public safety.”
Sadly, .US has been a cesspool of phishing activity for many years. As far back as 2018, Interisle found .US domains were the worst in the world for spam, botnet (attack infrastructure for DDOS etc.) and illicit or harmful content. Back then, .US was being operated by a different contractor.
In response to questions from KrebsOnSecurity, GoDaddy said all .US registrants must certify that they meet the NTIA’s nexus requirements. But this appears to be little more than an affirmative response that is already pre-selected for all new registrants.
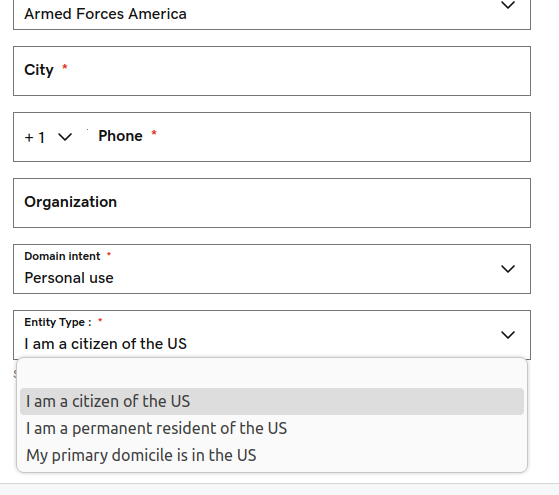
Attempting to register a .US domain through GoDaddy, for example, leads to a U.S. Registration Information page that auto-populates the nexus attestation field with the response, “I am a citizen of the US.” Other options include, “I am a permanent resident of the US,” and “My primary domicile is in the US.” It currently costs just $4.99 to obtain a .US domain through GoDaddy.
GoDaddy said it also conducts a scan of selected registration request information, and conducts “spot checks” on registrant information.
“We conduct regular reviews, per policy, of registration data within the Registry database to determine Nexus compliance with ongoing communications to registrars and registrants,” the company said in a written statement.
GoDaddy says it “is committed to supporting a safer online environment and proactively addressing this issue by assessing it against our own anti-abuse mitigation system.”
“We stand against DNS abuse in any form and maintain multiple systems and protocols to protect all the TLDs we operate,” the statement continued. “We will continue to work with registrars, cybersecurity firms and other stakeholders to make progress with this complex challenge.”
Interisle found significant numbers of .US domains were registered to attack some of the United States’ most prominent companies, including Bank of America, Amazon, Apple, AT&T, Citi, Comcast, Microsoft, Meta, and Target.
“Ironically, at least 109 of the .US domains in our data were used to attack the United States government, specifically the United States Postal Service and its customers,” Interisle wrote. “.US domains were also used to attack foreign government operations: six .US domains were used to attack Australian government services, six attacked Great’s Britain’s Royal Mail, one attacked Canada Post, and one attacked the Denmark Tax Authority.”
The NTIA recently published a proposal that would allow GoDaddy to redact registrant data from WHOIS registration records. The current charter for .US specifies that all .US registration records be public.
Interisle argues that without more stringent efforts to verify a United States nexus for new .US domain registrants, the NTIA’s proposal will make it even more difficult to identify phishers and verify registrants’ identities and nexus qualifications.
In a written statement, the NTIA said DNS abuse is a priority issue for the agency, and that NTIA supports “evidence-based policymaking.”
“We look forward to reviewing the report and will engage with our contractor for the .US domain on steps that we can take not only to address phishing, but the other forms of DNS abuse as well,” the statement reads.
Interisle sources its phishing data from several places, including the Anti-Phishing Working Group (APWG), OpenPhish, PhishTank, and Spamhaus. For more phishing facts, see Interisle’s 2023 Phishing Landscape report (PDF).’
Update, Sept. 5, 1:44 p.m. ET: Updated story with statement provided today by the NTIA.
WormGPT, a private new chatbot service advertised as a way to use Artificial Intelligence (AI) to write malicious software without all the pesky prohibitions on such activity enforced by the likes of ChatGPT and Google Bard, has started adding restrictions of its own on how the service can be used. Faced with customers trying to use WormGPT to create ransomware and phishing scams, the 23-year-old Portuguese programmer who created the project now says his service is slowly morphing into “a more controlled environment.”
Image: SlashNext.com.
The large language models (LLMs) made by ChatGPT parent OpenAI or Google or Microsoft all have various safety measures designed to prevent people from abusing them for nefarious purposes — such as creating malware or hate speech. In contrast, WormGPT has promoted itself as a new, uncensored LLM that was created specifically for cybercrime activities.
WormGPT was initially sold exclusively on HackForums, a sprawling, English-language community that has long featured a bustling marketplace for cybercrime tools and services. WormGPT licenses are sold for prices ranging from 500 to 5,000 Euro.
“Introducing my newest creation, ‘WormGPT,’ wrote “Last,” the handle chosen by the HackForums user who is selling the service. “This project aims to provide an alternative to ChatGPT, one that lets you do all sorts of illegal stuff and easily sell it online in the future. Everything blackhat related that you can think of can be done with WormGPT, allowing anyone access to malicious activity without ever leaving the comfort of their home.”
In July, an AI-based security firm called SlashNext analyzed WormGPT and asked it to create a “business email compromise” (BEC) phishing lure that could be used to trick employees into paying a fake invoice.
“The results were unsettling,” SlashNext’s Daniel Kelley wrote. “WormGPT produced an email that was not only remarkably persuasive but also strategically cunning, showcasing its potential for sophisticated phishing and BEC attacks.”
A review of Last’s posts on HackForums over the years shows this individual has extensive experience creating and using malicious software. In August 2022, Last posted a sales thread for “Arctic Stealer,” a data stealing trojan and keystroke logger that he sold there for many months.
“I’m very experienced with malwares,” Last wrote in a message to another HackForums user last year.
Last has also sold a modified version of the information stealer DCRat, as well as an obfuscation service marketed to malicious coders who sell their creations and wish to insulate them from being modified or copied by customers.
Shortly after joining the forum in early 2021, Last told several different Hackforums users his name was Rafael and that he was from Portugal. HackForums has a feature that allows anyone willing to take the time to dig through a user’s postings to learn when and if that user was previously tied to another account.
That account tracing feature reveals that while Last has used many pseudonyms over the years, he originally used the nickname “ruiunashackers.” The first search result in Google for that unique nickname brings up a TikTok account with the same moniker, and that TikTok account says it is associated with an Instagram account for a Rafael Morais from Porto, a coastal city in northwest Portugal.
Reached via Instagram and Telegram, Morais said he was happy to chat about WormGPT.
“You can ask me anything,” Morais said. “I’m an open book.”
Morais said he recently graduated from a polytechnic institute in Portugal, where he earned a degree in information technology. He said only about 30 to 35 percent of the work on WormGPT was his, and that other coders are contributing to the project. So far, he says, roughly 200 customers have paid to use the service.
“I don’t do this for money,” Morais explained. “It was basically a project I thought [was] interesting at the beginning and now I’m maintaining it just to help [the] community. We have updated a lot since the release, our model is now 5 or 6 times better in terms of learning and answer accuracy.”
WormGPT isn’t the only rogue ChatGPT clone advertised as friendly to malware writers and cybercriminals. According to SlashNext, one unsettling trend on the cybercrime forums is evident in discussion threads offering “jailbreaks” for interfaces like ChatGPT.
“These ‘jailbreaks’ are specialised prompts that are becoming increasingly common,” Kelley wrote. “They refer to carefully crafted inputs designed to manipulate interfaces like ChatGPT into generating output that might involve disclosing sensitive information, producing inappropriate content, or even executing harmful code. The proliferation of such practices underscores the rising challenges in maintaining AI security in the face of determined cybercriminals.”
Morais said they have been using the GPT-J 6B model since the service was launched, although he declined to discuss the source of the LLMs that power WormGPT. But he said the data set that informs WormGPT is enormous.
“Anyone that tests wormgpt can see that it has no difference from any other uncensored AI or even chatgpt with jailbreaks,” Morais explained. “The game changer is that our dataset [library] is big.”
Morais said he began working on computers at age 13, and soon started exploring security vulnerabilities and the possibility of making a living by finding and reporting them to software vendors.
“My story began in 2013 with some greyhat activies, never anything blackhat tho, mostly bugbounty,” he said. “In 2015, my love for coding started, learning c# and more .net programming languages. In 2017 I’ve started using many hacking forums because I have had some problems home (in terms of money) so I had to help my parents with money… started selling a few products (not blackhat yet) and in 2019 I started turning blackhat. Until a few months ago I was still selling blackhat products but now with wormgpt I see a bright future and have decided to start my transition into whitehat again.”
WormGPT sells licenses via a dedicated channel on Telegram, and the channel recently lamented that media coverage of WormGPT so far has painted the service in an unfairly negative light.
“We are uncensored, not blackhat!” the WormGPT channel announced at the end of July. “From the beginning, the media has portrayed us as a malicious LLM (Language Model), when all we did was use the name ‘blackhatgpt’ for our Telegram channel as a meme. We encourage researchers to test our tool and provide feedback to determine if it is as bad as the media is portraying it to the world.”
It turns out, when you advertise an online service for doing bad things, people tend to show up with the intention of doing bad things with it. WormGPT’s front man Last seems to have acknowledged this at the service’s initial launch, which included the disclaimer, “We are not responsible if you use this tool for doing bad stuff.”
But lately, Morais said, WormGPT has been forced to add certain guardrails of its own.
“We have prohibited some subjects on WormGPT itself,” Morais said. “Anything related to murders, drug traffic, kidnapping, child porn, ransomwares, financial crime. We are working on blocking BEC too, at the moment it is still possible but most of the times it will be incomplete because we already added some limitations. Our plan is to have WormGPT marked as an uncensored AI, not blackhat. In the last weeks we have been blocking some subjects from being discussed on WormGPT.”
Still, Last has continued to state on HackForums — and more recently on the far more serious cybercrime forum Exploit — that WormGPT will quite happily create malware capable of infecting a computer and going “fully undetectable” (FUD) by virtually all of the major antivirus makers (AVs).
“You can easily buy WormGPT and ask it for a Rust malware script and it will 99% sure be FUD against most AVs,” Last told a forum denizen in late July.
Asked to list some of the legitimate or what he called “white hat” uses for WormGPT, Morais said his service offers reliable code, unlimited characters, and accurate, quick answers.
“We used WormGPT to fix some issues on our website related to possible sql problems and exploits,” he explained. “You can use WormGPT to create firewalls, manage iptables, analyze network, code blockers, math, anything.”
Morais said he wants WormGPT to become a positive influence on the security community, not a destructive one, and that he’s actively trying to steer the project in that direction. The original HackForums thread pimping WormGPT as a malware writer’s best friend has since been deleted, and the service is now advertised as “WormGPT – Best GPT Alternative Without Limits — Privacy Focused.”
“We have a few researchers using our wormgpt for whitehat stuff, that’s our main focus now, turning wormgpt into a good thing to [the] community,” he said.
It’s unclear yet whether Last’s customers share that view.