






Today, we released the latest issue of The Domain Name Industry Brief, which shows that the first quarter of 2023 closed with 354.0 million domain name registrations across all top-level domains (TLDs), an increase of 3.5 million domain name registrations, or 1.0%, compared to the fourth quarter of 2022.1,2 Domain name registrations also increased by 3.5 million, or 1.0%, year over year.1,2

Check out the latest issue of The Domain Name Industry Brief to see domain name stats from the first quarter of 2023, including:
This issue of the Domain Name Industry Brief includes a correction to the March 2023 issue, which incorrectly reported the number of domain name registrations in the .eu ccTLD.2 This was the result of a one-time error in the .eu domain name registration data, provided by ZookNIC, which has since been resolved.
To see past issues of The Domain Name Industry Brief, please visit https://verisign.com/dnibarchives.
The post Verisign Domain Name Industry Brief: 354.0 Million Domain Name Registrations in the First Quarter of 2023 appeared first on Verisign Blog.






s3-ep137-feat-1200












The number of phishing websites tied to domain name registrar Freenom dropped precipitously in the months surrounding a recent lawsuit from social networking giant Meta, which alleged the free domain name provider has a long history of ignoring abuse complaints about phishing websites while monetizing traffic to those abusive domains.
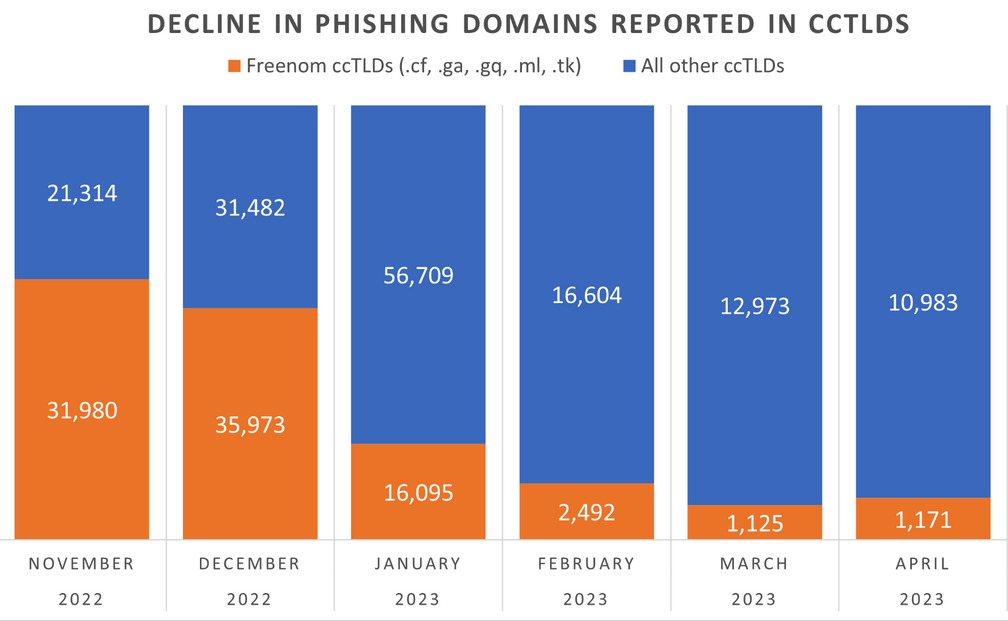
The volume of phishing websites registered through Freenom dropped considerably since the registrar was sued by Meta. Image: Interisle Consulting.
Freenom is the domain name registry service provider for five so-called “country code top level domains” (ccTLDs), including .cf for the Central African Republic; .ga for Gabon; .gq for Equatorial Guinea; .ml for Mali; and .tk for Tokelau.
Freenom has always waived the registration fees for domains in these country-code domains, but the registrar also reserves the right to take back free domains at any time, and to divert traffic to other sites — including adult websites. And there are countless reports from Freenom users who’ve seen free domains removed from their control and forwarded to other websites.
By the time Meta initially filed its lawsuit in December 2022, Freenom was the source of well more than half of all new phishing domains coming from country-code top-level domains. Meta initially asked a court to seal its case against Freenom, but that request was denied. Meta withdrew its December 2022 lawsuit and re-filed it in March 2023.
“The five ccTLDs to which Freenom provides its services are the TLDs of choice for cybercriminals because Freenom provides free domain name registration services and shields its customers’ identity, even after being presented with evidence that the domain names are being used for illegal purposes,” Meta’s complaint charged. “Even after receiving notices of infringement or phishing by its customers, Freenom continues to license new infringing domain names to those same customers.”
Meta pointed to research from Interisle Consulting Group, which discovered in 2021 and again last year that the five ccTLDs operated by Freenom made up half of the Top Ten TLDs most abused by phishers.
Interisle partner Dave Piscitello said something remarkable has happened in the months since the Meta lawsuit.
“We’ve observed a significant decline in phishing domains reported in the Freenom commercialized ccTLDs in months surrounding the lawsuit,” Piscitello wrote on Mastodon. “Responsible for over 60% of phishing domains reported in November 2022, Freenom’s percentage has dropped to under 15%.”
Interisle collects data from 12 major blocklists for spam, malware, and phishing, and it receives phishing-specific data from Spamhaus, Phishtank, OpenPhish and the APWG Ecrime Exchange. The company publishes historical data sets quarterly, both on malware and phishing.
Piscitello said it’s too soon to tell the full impact of the Freenom lawsuit, noting that Interisle’s sources of spam and phishing data all have different policies about when domains are removed from their block lists.
“One of the things we don’t have visibility into is how each of the blocklists determine to remove a URL from their lists,” he said. “Some of them time out [listed domains] after 14 days, some do it after 30, and some keep them forever.”
Freenom did not respond to requests for comment.
This is the second time in as many years that a lawsuit by Meta against a domain registrar has disrupted the phishing industry. In March 2020, Meta sued domain registrar giant Namecheap, alleging cybersquatting and trademark infringement.
The two parties settled the matter in April 2022. While the terms of that settlement have not been disclosed, new phishing domains registered through Namecheap declined more than 50 percent the following quarter, Interisle found.
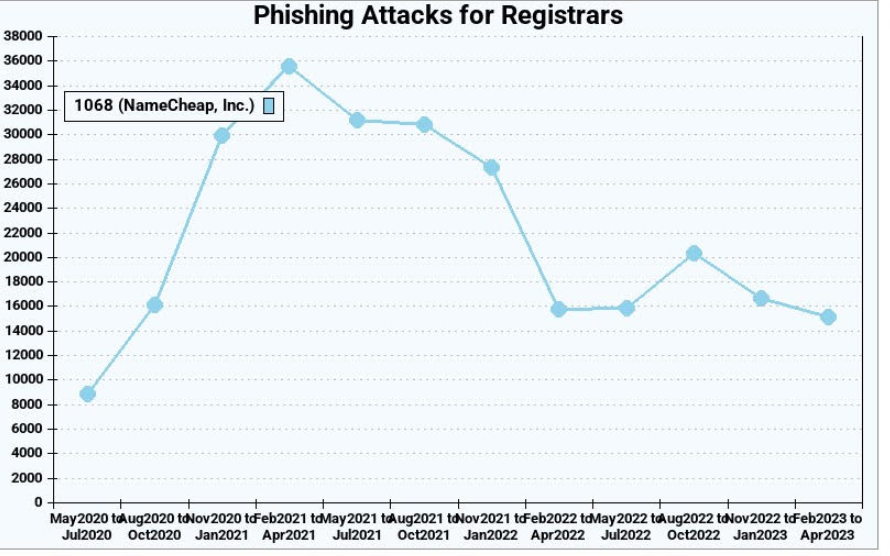
Phishing attacks using websites registered through Namecheap, before and after the registrar settled a lawsuit with Meta. Image: Interisle Consulting.
Unfortunately, the lawsuits have had little effect on the overall number of phishing attacks and phishing-related domains, which have steadily increased in volume over the years. Piscitello said the phishers tend to gravitate toward registrars that offer the least resistance and lowest price per domain. And with new top-level domains constantly being introduced, there is rarely a shortage of super low-priced domains.
“The abuse of a new top-level domain is largely the result of one registrar’s portfolio,” Piscitello told KrebsOnSecurity. “Alibaba or Namecheap or another registrar will run a promotion for a cheap domain, and then we’ll see flocking and migration of the phishers to that TLD. It’s like strip mining, where they’ll buy hundreds or thousands of domains, use those in a campaign, exhaust that TLD and then move on to another provider.”
Piscitello said despite the steep drop in phishing domains coming out of Freenom, the alternatives available to phishers are many. After all, there are more than 2,000 accredited domain registrars, not to mention dozens of services that let anyone set up a website for free without even owning a domain.
“There is no evidence that the trend line is even going to level off,” he said. “I think what the Meta lawsuit tells us is that litigation is like giving someone a standing eight count. It temporarily disrupts a process. And in that sense, litigation appears to be working.”








ispoof-1200









Microsoft today released software updates to fix at least four dozen security holes in its Windows operating systems and other software, including patches for two zero-day vulnerabilities that are already being exploited in active attacks.

First up in May’s zero-day flaws is CVE-2023-29336, which is an “elevation of privilege” weakness in Windows which has a low attack complexity, requires low privileges, and no user interaction. However, as the SANS Internet Storm Center points out, the attack vector for this bug is local.
“Local Privilege escalation vulnerabilities are a key part of attackers’ objectives,” said Kevin Breen, director of cyber threat research at Immersive Labs. “Once they gain initial access they will seek administrative or SYSTEM-level permissions. This can allow the attacker to disable security tooling and deploy more attacker tools like Mimikatz that lets them move across the network and gain persistence.”
The zero-day patch that has received the most attention so far is CVE-2023-24932, which is a Secure Boot Security Feature Bypass flaw that is being actively exploited by “bootkit” malware known as “BlackLotus.” A bootkit is dangerous because it allows the attacker to load malicious software before the operating system even starts up.
According to Microsoft’s advisory, an attacker would need physical access or administrative rights to a target device, and could then install an affected boot policy. Microsoft gives this flaw a CVSS score of just 6.7, rating it as “Important.”
Adam Barnett, lead software engineer at Rapid7, said CVE-2023-24932 deserves a considerably higher threat score.
“Microsoft warns that an attacker who already has Administrator access to an unpatched asset could exploit CVE-2023-24932 without necessarily having physical access,” Barnett said. “Therefore, the relatively low CVSSv3 base score of 6.7 isn’t necessarily a reliable metric in this case.”
Barnett said Microsoft has provided a supplementary guidance article specifically calling out the threat posed by BlackLotus malware, which loads ahead of the operating system on compromised assets, and provides attackers with an array of powerful evasion, persistence, and Command & Control (C2) techniques, including deploying malicious kernel drivers, and disabling Microsoft Defender or Bitlocker.
“Administrators should be aware that additional actions are required beyond simply applying the patches,” Barnett advised. “The patch enables the configuration options necessary for protection, but administrators must apply changes to UEFI config after patching. The attack surface is not limited to physical assets, either; Windows assets running on some VMs, including Azure assets with Secure Boot enabled, also require these extra remediation steps for protection. Rapid7 has noted in the past that enabling Secure Boot is a foundational protection against driver-based attacks. Defenders ignore this vulnerability at their peril.”
In addition to the two zero-days fixed this month, Microsoft also patched five remote code execution (RCE) flaws in Windows, two of which have notably high CVSS scores.
CVE-2023-24941 affects the Windows Network File System, and can be exploited over the network by making an unauthenticated, specially crafted request. Microsoft’s advisory also includes mitigation advice. The CVSS for this vulnerability is 9.8 – the highest of all the flaws addressed this month.
Meanwhile, CVE-2023-28283 is a critical bug in the Windows Lightweight Directory Access Protocol (LDAP) that allows an unauthenticated attacker to execute malicious code on the vulnerable device. The CVSS for this vulnerability is 8.1, but Microsoft says exploiting the flaw may be tricky and unreliable for attackers.
Another vulnerability patched this month that was disclosed publicly before today (but not yet seen exploited in the wild) is CVE-2023-29325, a weakness in Microsoft Outlook and Explorer that can be exploited by attackers to remotely install malware. Microsoft says this vulnerability can be exploited merely by viewing a specially-crafted email in the Outlook Preview Pane.
“To help protect against this vulnerability, we recommend users read email messages in plain text format,” Microsoft’s writeup on CVE-2023-29325 advises.
“If an attacker were able to exploit this vulnerability, they would gain remote access to the victim’s account, where they could deploy additional malware,” Immersive’s Breen said. “This kind of exploit will be highly sought after by e-crime and ransomware groups where, if successfully weaponized, could be used to target hundreds of organizations with very little effort.”
For more details on the updates released today, check out roundups by Action1, Automox and Qualys, If today’s updates cause any stability or usability issues in Windows, AskWoody.com will likely have the lowdown on that.
Please consider backing up your data and/or imaging your system before applying any updates. And feel free to sound off in the comments if you experience any problems as a result of these patches.