
No cyber. It's literally a "cyber-free" week, as least far as the term relates to security things. Instead, I'm unboxing an armful of Insta360 goodies and lamenting the state of IoT whilst putting even more IoT things into our massive garage renovation. I'm enjoying it though. Honestly. I think...

Did I really need to get a connected BBQ? No more than I needed to connect most of the other things in the house which is to say "a bit useful but not entirely necessary". But it's a fascinating process when looked at through the lens of how accessible the technology is to your average person given it's embedded in a consumer-orientated product. In short - it's painful - but listen to this week's update to hear precisely why. Plus, there's a heap of new data breach and some really, really good news about the NTLM hashes now being available in Pwned Passwords. Enjoy 😊

Authorities in the United States and United Kingdom today levied financial sanctions against seven men accused of operating “Trickbot,” a cybercrime-as-a-service platform based in Russia that has enabled countless ransomware attacks and bank account takeovers since its debut in 2016. The U.S. Department of the Treasury says the Trickbot group is associated with Russian intelligence services, and that this alliance led to the targeting of many U.S. companies and government entities.
Initially a stealthy trojan horse program delivered via email and used to steal passwords, Trickbot evolved into “a highly modular malware suite that provides the Trickbot Group with the ability to conduct a variety of illegal cyber activities, including ransomware attacks,” the Treasury Department said.
A spam email from 2020 containing a Trickbot-infected attachment. Image: Microsoft.
“During the height of the COVID-19 pandemic in 2020, Trickbot targeted hospitals and healthcare centers, launching a wave of ransomware attacks against hospitals across the United States,” the sanctions notice continued. “In one of these attacks, the Trickbot Group deployed ransomware against three Minnesota medical facilities, disrupting their computer networks and telephones, and causing a diversion of ambulances. Members of the Trickbot Group publicly gloated over the ease of targeting the medical facilities and the speed with which the ransoms were paid to the group.”
Only one of the men sanctioned today is known to have been criminally charged in connection with hacking activity. According to the Treasury Department, the alleged senior leader of the Trickbot group is 34-year-old Russian national Vitaly “Bentley” Kovalev.
A New Jersey grand jury indicted Kovalev in 2012 after an investigation by the U.S. Secret Service determined that he ran a massive “money mule” scheme, which used phony job offers to trick people into laundering money stolen from hacked small to mid-sized businesses in the United States. The 2012 indictment against Kovalev relates to cybercrimes he allegedly perpetrated prior to the creation of Trickbot.
In 2015, Kovalev reportedly began filming a movie in Russia about cybercrime called “Botnet.” According to a 2016 story from Forbes.ru, Botnet’s opening scene was to depict the plight of Christina Svechinskaya, a Russian student arrested by FBI agents in September 2010.

Christina Svechinskaya, a money mule hired by Bentley who was arrested by the FBI in 2010.
Svechinskaya was one of Bentley’s money mules, most of whom were young Russian students on temporary travel visas in the United States. She was among 37 alleged mules charged with aiding an international cybercrime operation — basically, setting up phony corporate bank accounts for the sole purpose of laundering stolen funds.
Although she possessed no real hacking skills, Svechinskaya’s mugshot and social media photos went viral online and she was quickly dubbed “the world’s sexiest computer hacker” by the tabloids.
Kovalev’s Botnet film project was disrupted after Russian authorities raided the film production company’s offices as part of a cybercrime investigation. In February 2016, Reuters reported that the raid was connected to a crackdown on “Dyre,” a sophisticated trojan that U.S. federal investigators say was the precursor to the Trickbot malware. The Forbes.ru article cited sources close to the investigation who said the film studio was operating as a money-laundering front for the cybercrooks behind Dyre.
But shifting political winds in Russia would soon bring high treason charges against three of the Russian cybercrime investigators tied to the investigation into the film studio. In a major shakeup in 2017, the Kremlin levied treason charges against Sergey Mikhaylov, then deputy chief of Russia’s top anti-cybercrime unit.
Also charged with treason was Ruslan Stoyanov, then a senior employee at Russian security firm Kaspersky Lab [the Forbes.ru report from 2016 said investigators from Mikhaylov’s unit and Kaspersky Lab were present at the film company raid].
Russian media outlets have speculated that the men were accused of treason for helping American cybercrime investigators pursue top Russian hackers. However, the charges against both men were classified and have never been officially revealed. After their brief, closed trial, both men were convicted of treason. Mikhaylov was given a 22 year prison sentence; Stoyanov was sentenced to 14 years in prison.
In September 2021, the Kremlin issued treason charges against Ilya Sachkov, formerly head of the cybersecurity firm Group-IB. According to Reuters, Sachkov and his company were hired by the film studio “to advise the Botnet director and writers on the finer points of cybercrime.” Sachkov remains imprisoned in Russia pending his treason trial.
Trickbot was heavily used by Conti and Ryuk, two of Russia’s most ruthless and successful ransomware groups. Blockchain analysis firm Chainalysis estimates that in 2021 alone, Conti extorted more than USD $100 million from its hacking victims; Chainalysis estimates Ryuk extorted more than USD $150 million from its ransomware victims.
The U.S. cybersecurity firm CrowdStrike has long tracked the activities of Trickbot, Ryuk and Conti under the same moniker — “Wizard Spider” — which CrowdStrike describes as “a Russia-nexus cybercriminal group behind the core development and distribution of a sophisticated arsenal of criminal tools, that allow them to run multiple different types of operations.”
“CrowdStrike Intelligence has observed WIZARD SPIDER targeting multiple countries and industries such as academia, energy, financial services, government, and more,” said Adam Meyers, head of intelligence at CrowdStrike.
This is not the U.S. government’s first swipe at the Trickbot group. In early October 2020, KrebsOnSecurity broke the news that someone had launched a series of coordinated attacks designed to disrupt the Trickbot botnet. A week later, The Washington Post ran a story saying the attack on Trickbot was the work of U.S. Cyber Command, a branch of the Department of Defense headed by the director of the U.S. National Security Agency (NSA).
Days after Russia invaded Ukraine in February 2022, a Ukrainian researcher leaked several years of internal chat logs from the Conti ransomware gang. Those candid conversations offer a fascinating view into the challenges of running a sprawling criminal enterprise with more than 100 salaried employees. They also showed that Conti enjoyed protection from prosecution by Russian authorities, as long as the hacker group took care not to target Russian organizations.
In addition, the leaked Conti chats confirmed there was considerable overlap in the operation and leadership of Conti, Trickbot and Ryuk.
Michael DeBolt, chief intelligence officer at cybersecurity firm Intel 471, said the leaked Conti chats showed Bentley oversaw a team of coders tasked with ensuring that the Trickbot and Conti malware remained undetected by the different antivirus and security software vendors.
In the years prior to the emergence of Trickbot in 2016, Bentley worked closely on the Gameover ZeuS trojan, a peer-to-peer malware threat that infected between 500,000 and a million computers with an automated ransomware strain called Cryptolocker, DeBolt said.
The FBI has a standing $3 million bounty offered for the capture of Evgeny “Slavik” Bogachev, the alleged author of the Zeus trojan. And there are indications that Bentley worked directly with Bogachev. DeBolt pointed to an October 2014 discussion on the exclusive Russian hacking forum Mazafaka that included a complaint by a Russian hosting firm against a forum user by the name “Ferrari” who had failed to pay a $30,000 hosting bill.
In that discussion thread, it emerged that the hosting company thought it was filing a complaint against Slavik. But the Mazafaka member who vouched for Ferrari’s membership on the forum said they knew Ferrari as Bentley the mule handler, and at some point Slavik and Bentley must have been sharing the Ferrari user account.
“It is likely that Slavik (aka. Bogachev) and Bentley (aka. Kovalev) shared the same ‘Ferrari’ handle on the Mazafaka forum circa 2014, which suggests the two had a working relationship at that time, and supports the recent US and UK Government announcements regarding Kovalev’s past involvement in cybercrime predating Dyre or the Trickbot Group,” DeBolt said.
CrowdStrike’s Meyers said while Wizard Spider operations have significantly reduced following the demise of Conti in June 2022, today’s sanctions will likely cause temporary disruptions for the cybercriminal group while they look for ways to circumvent the financial restrictions — which make it illegal to transact with or hold the assets of sanctioned persons or entities.
“Often, when cybercriminal groups are disrupted, they will go dark for a time only to rebrand under a new name,” Meyers said.
The prosecution of Kovalev is being handled by the U.S. Attorney’s Office in New Jersey. A copy of the now-unsealed 2012 indictment of Kovalev is here (PDF).

Getting everything out nice and early today so we can get out there in hit the wake park in the balmy "well over 30C" weather (the radio is talking about "severe heatwave weather" as I write this). But hey, we're surrounded by water and a beer delivery is due today so no crisis 😎 There's also a heap more data breach news and I'll be putting that connected BBQ to use for the first time today, stay tuned for epic pics on all of the above over the coming hours!


Breaches all over the place today! Well, this past week, and there's some debate as to whether one of them is a breach, a scrape or if the term just doesn't matter anyway. Plus, we've been kitchen shopping, I'm helping friends out with connected doorbells and other random but somehow related things this week. Enjoy 😊

Well and truly back into the swing of things in the new year, I think what I've found most satisfying this week is to sit down and pump out a decent blog post on something technical. It's an itch I just haven't had enough time to scratch properly in recent times and I really hope Pwned or Bot makes up for that. I love that it's generating discussion (both for and against) and that it's causing people to stop and think about how we establish the legitimacy of identities in an increasingly bot-centric world. I hope you enjoy this week's update and all the conversation surrounding it.


Big week! So big, in fact, that I rushed into this week's update less prepared and made it a very casual one, which is just fine 😊 It's mostly password books and kitchen equipment this week, both topics which had far more engagement than I expected but made them all the more interesting. Next week I'll get back into the pattern of switching between last thing Friday and first thing Friday so it'll be my morning again on the 20th, see you then!


Strap yourself in, this is a big one! Big video, big breach (scrape?), and a big audience today. The Twitter incident consumed a heap of my time before, during and after this live stream, but then I go and get a sudden itch to do stuff like the number plate capturing and, well, there goes even more hours I don't have. But hey, I love what I do and I have no regrets, I hope you enjoy watching this week's vid 😊
Oh - one more thing: today I set up an official Mastodon account for HIBP. If you've got a footprint in the fediverse, please go and give the account a follow. There are a bunch of others out there that definitely aren't run by me, it's only this one, it only follows me personally and it has a verified website of haveibeenpwned.com so should be easy to find even if you don't follow the link above.


We made it! That's 2022 done and dusted, and what a year it was, both professionally and personally. It feels great to get to the end of the year with all the proverbial ducks lined up, some massive achievements now behind us (not least of which was the wedding), and a clean slate coming into 2023 to do amazing things. I'm super excited about next year and can't wait to share a whole bunch of new stuff over the coming 52 Fridays. For now though, here's the last of it from a pretty crazy year, enjoy 😊


It's my last weekly update on the road for a while! As enjoyable as travel is, I'm looking forward to getting back to a normal routine and really starting to smash out some of the goals I have for the coming year. For now though, I've published this a couple of days after recording, and a day after an awesome hot, beachside Christmas. Hope yours has been amazing too, see you from home next week 😊

Despite having both my tripod and mic in the wrong suitcase in the wrong place, Scott and I still pulled together a weekly vid from the Norwegian mountains. Much of this week is a combination of our travels here, responses to my tweets around cookie warnings and reactions to Elon's various decisions (and undecisions) on Twitter. Plus, there's the CoinTracker and Gemini breaches which appear to have stemmed from the SendGrid breach, the connection to that incident having been made by CoinTracker just after we had a friendly exchange about the description in HIBP 🙂
I'll leave you with some epic pics we snapped a few hours after this video, what a sight to behold, especially whilst sitting in the hot tub with good friends and cold beer 😊
— Troy Hunt (@troyhunt) December 17, 2022





For the first time in I don't know how long, I couldn't do this live. Turns out both cell and wifi in Lapland are, with the benefit of hindsight, exactly what you'd expect from a remote location in the Arctic circle. The rest of the place was pretty amazing though, and a good deal of this week's content has gone to that. Plus, there's the whole "Australia becoming the world's most cyber-secure country" goal which deserves discussion. Oh - and the tweet with that pic I discuss - I'll just leave that one here 😊
Sometimes, life feels like a fairytale. This is now my favourite photo ever ❤️ pic.twitter.com/lspKwVVSly
— Troy Hunt (@troyhunt) December 9, 2022

In December 2021, Google filed a civil lawsuit against two Russian men thought to be responsible for operating Glupteba, one of the Internet’s largest and oldest botnets. The defendants, who initially pursued a strategy of counter suing Google for interfering in their sprawling cybercrime business, later brazenly offered to dismantle the botnet in exchange for payment from Google. The judge in the case was not amused, found for the plaintiff, and ordered the defendants and their U.S. attorney to pay Google’s legal fees.
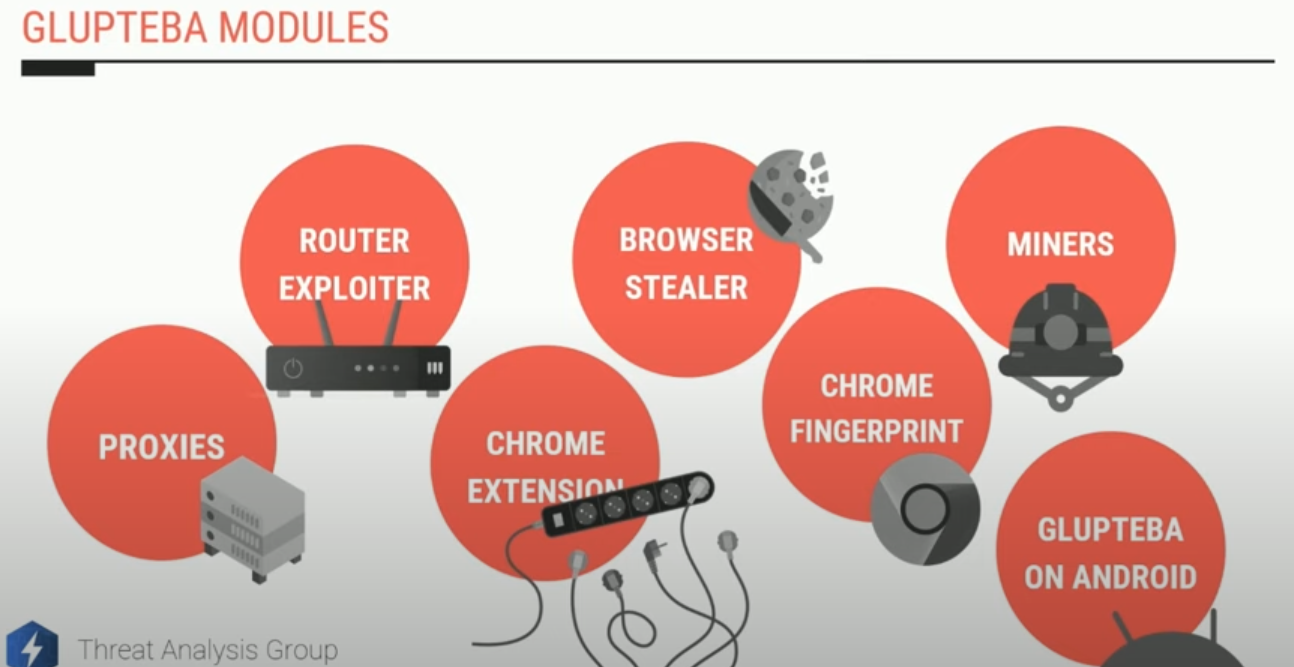
A slide from a talk given in Sept. 2022 by Google researcher Luca Nagy. https://www.youtube.com/watch?v=5Gz6_I-wl0E&t=6s
Glupteba is a rootkit that steals passwords and other access credentials, disables security software, and tries to compromise other devices on the victim network — such as Internet routers and media storage servers — for use in relaying spam or other malicious traffic.
Collectively, the tens of thousands of systems infected with Glupteba on any given day feed into a number of major cybercriminal businesses: The botnet’s proprietors sell the credential data they steal, use the botnet to place disruptive ads on the infected computers, and mine cryptocurrencies. Glupteba also rents out infected systems as “proxies,” directing third-party traffic through the infected devices to disguise the origin of the traffic.
In June 2022, KrebsOnSecurity showed how the malware proxy services RSOCKS and AWMProxy were entirely dependent on the Glupteba botnet for fresh proxies, and that the founder of AWMProxy was Dmitry Starovikov — one of the Russian men named in Google’s lawsuit.
Google sued Starovikov and 15 other “John Doe” defendants, alleging violations of the Racketeer Influenced and Corrupt Organizations Act (RICO), the Computer Fraud and Abuse Act, trademark and unfair competition law, and unjust enrichment.
In June, Google and the named defendants agreed that the case would proceed as a nonjury action because Google had withdrawn its claim for damages — seeking only injunctive relief to halt the operations of the botnet.
The defendants, who worked for a Russian firm called “Valtron” that was also named in the lawsuit, told Google that they were interested in settling. The defendants said they could potentially help Google by taking the botnet offline.
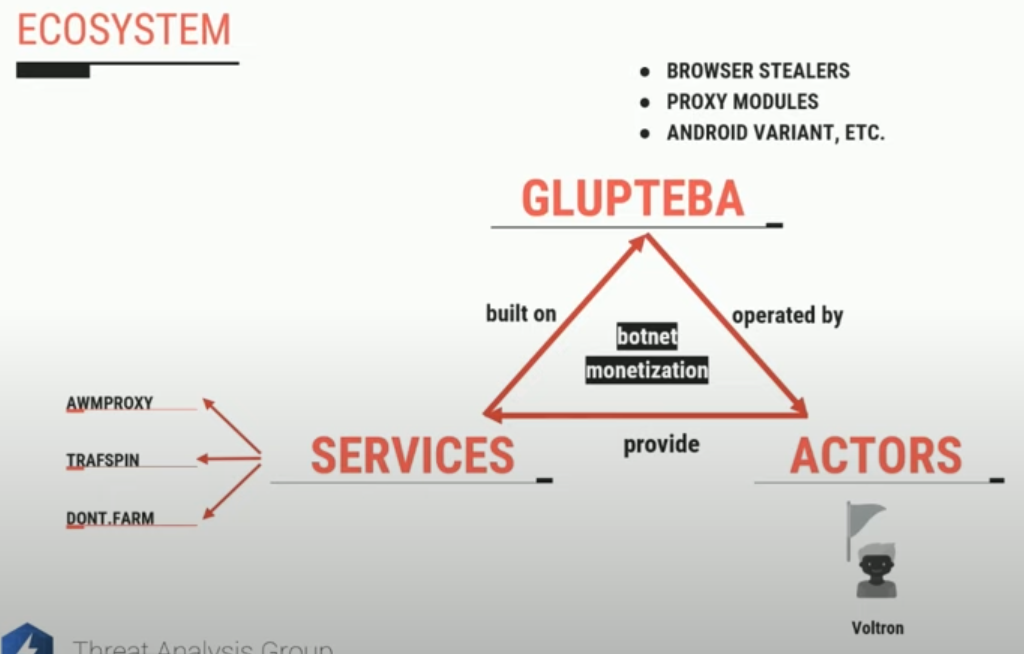
Another slide from Google researcher Luca Nagy’s September 2022 talk on Glupteba.
But the court expressed frustration that the defendants were unwilling to consent to a permanent injunction, and at the same time were unable to articulate why an injunction forbidding them from engaging in unlawful activities would pose a problem.
“The Defendants insisted that they were not engaged in criminal activity, and that any alleged activity in which they were engaged was legitimate,” U.S. District Court Judge Denise Cote wrote. “Nevertheless, the Defendants resisted entry of a permanent injunction, asserting that Google’s use of the preliminary injunction had disrupted their normal business operations.”
While the defendants represented that they had the ability to dismantle the Glupteba botnet, when it came time for discovery — the stage in a lawsuit where both parties can compel the production of documents and other information pertinent to their case — the attorney for the defendants told the court his clients had been fired by Valtron in late 2021, and thus no longer had access to their work laptops or the botnet.
The lawyer for the defendants — New York-based cybercrime defense attorney Igor Litvak — told the court he first learned about his clients’ termination from Valtron on May 20, a fact Judge Cote said she found “troubling” given statements he made to the court after that date representing that his clients still had access to the botnet.
The court ultimately suspended the discovery process against Google, saying there was reason to believe the defendants sought discovery only “to learn whether they could circumvent the steps Google has taken to block the malware.”
On September 6, Litvak emailed Google that his clients were willing to discuss settlement.
“The parties held a call on September 8, at which Litvak explained that the Defendants would be willing to provide Google with the private keys for Bitcoin addresses associated with the Glupteba botnet, and that they would promise not to engage in their alleged criminal activity in the future (without any admission of wrongdoing),” the judge wrote.
“In exchange, the Defendants would receive Google’s agreement not to report them to law enforcement, and a payment of $1 million per defendant, plus $110,000 in attorney’s fees,” Judge Cote continued. “The Defendants stated that, although they do not currently have access to the private keys, Valtron would be willing to provide them with the private keys if the case were settled. The Defendants also stated that they believe these keys would help Google shut down the Glupteba botnet.”
Google rejected the defendants’ offer as extortionate, and reported it to law enforcement. Judge Cote also found Litvak was complicit in the defendants’ efforts to mislead the court, and ordered him to join his clients in paying Google’s legal fees.
“It is now clear that the Defendants appeared in this Court not to proceed in good faith to defend against Google’s claims but with the intent to abuse the court system and discovery rules to reap a profit from Google,” Judge Cote wrote.
Litvak has filed a motion to reconsider (PDF), asking the court to vacate the sanctions against him. He said his goal is to get the case back into court.
“The judge was completely wrong to issue sanctions,” Litvak said in an interview with KrebsOnSecurity. “From the beginning of the case, she acted as if she needed to protect Google from something. If the court does not decide to vacate the sanctions, we will have to go to the Second Circuit (Court of Appeals) and get justice there.”
In a statement on the court’s decision, Google said it will have significant ramifications for online crime, and that since its technical and legal attacks on the botnet last year, Google has observed a 78 percent reduction in the number of hosts infected by Glupteba.
“While Glupteba operators have resumed activity on some non-Google platforms and IoT devices, shining a legal spotlight on the group makes it less appealing for other criminal operations to work with them,” reads a blog post from Google’s General Counsel Halimah DeLaine Prado and vice president of engineering Royal Hansen. “And the steps [Google] took last year to disrupt their operations have already had significant impact.”
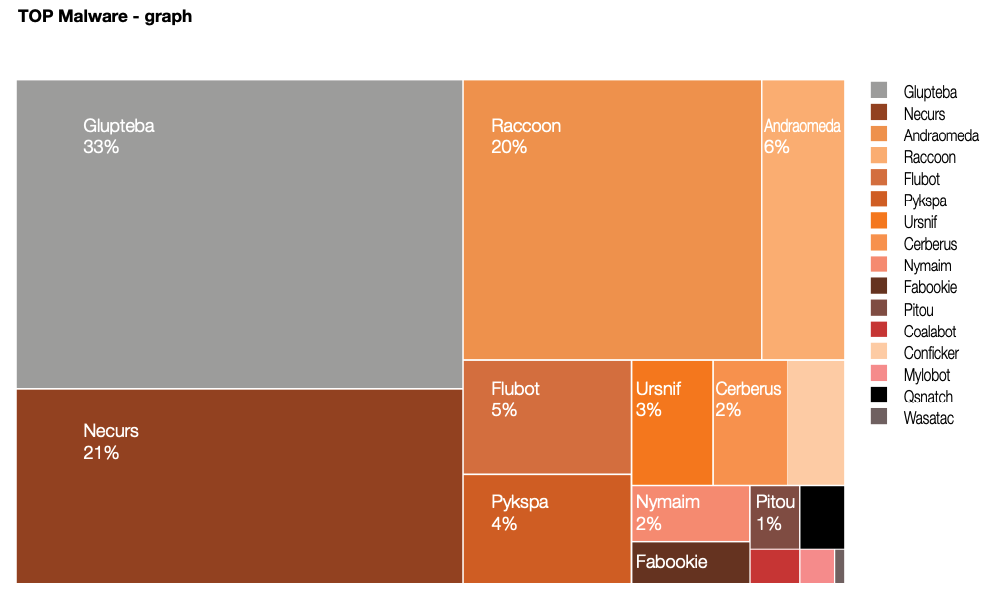
A report from the Polish computer emergency response team (CERT Orange Polksa) found Glupteba was the biggest malware threat in 2021.
We're in Copenhagen! Scott and family joined us in Oslo for round 2 of wedding celebrations this week before jumping on the ferry to Copenhagen and seeing the sights here. There's lots of cyber things in this week's vid relating to HIBP's birthday, Medibank and financial penalties for breaches, but I'm just going to leave you with one of the most amazing moments of my life captured in pics:
🇳🇴 ❤️ 👰♀️ 🤵 pic.twitter.com/pPY49DArIF
— Troy Hunt (@troyhunt) December 2, 2022






Do yourself a favor: Open a new browser tab and head to your search engine of choice. Type in your full name and home address. Then, see what pops up.
Are the results sparking an ember of unease in the back of your brain? Whether you’re a private person online or you’re comfortable sharing your daily life updates on social media, there are likely to be several personal details about you on sites that shouldn’t have that information. Some of these sites may be data brokerage websites.
Data brokerage sites are legal and are mostly used by annoying advertisers, though cybercriminals may also use them maliciously. The average person has their information for sale on 31 data brokerage sites, and 95% of people have their personal information on sale without their permission.
So how do you scrub the internet of your personal details to keep your identity secure? McAfee Personal Data Cleanup is a service that prevents your personal information from being collected and sold online. Here’s why you should consider taking a few easy steps now to give you peace of mind about the security of your personally identifiable information (PII).
Attack surface is a term usually applied to corporate security, but it’s a great visualization for everyday people going about their personal online errands and entertainment. An attack surface is the number of possible entry points a cybercriminal could weasel their way through to get at your valuable and private information. Entry points include your social media profiles, your online shopping accounts, and data brokerage sites. The fewer entry points you have, the harder it is for cybercriminals to find and exploit them.
While Social Security Numbers (SSNs) are generally revered as the piece of PII to guard most closely, a cybercriminal can still damage your identity with just your name and an address, email address, or phone number. For example, they can request new passwords or multifactor authentication one-time passcodes to break their way into online banking or shopping accounts. Security breaches are happening to huge companies all over the world. All it takes is for your SSN to be leaked in one of them, for a cybercriminal to piece together your digital clone and use it to harm your identity or credit.
Personal Data Cleanup minimizes your attack surface by removing as much PII as possible that’s floating around the internet, just waiting for someone to buy it.
When you’re aware of how many unauthorized vendors are selling your PII, it could be the wakeup call you need start adopting more cautious online habits. For instance, oversharing on social media leaks a lot of valuable details that a savvy criminal can then use to take educated guesses at your passwords or craft a social engineering plot catered just to you.
The present is as good a time as any to start protecting your identity for the future; however, getting started is often the most difficult step. It can seem overwhelming to reach out to every data brokerage site individually and request they remove your info. Personal Data Cleanup can be your partner not only in beginning the cleanup process but in monitoring your data security to keep your online presence as minimal as possible. The service scans the internet’s riskiest sites and then, before deleting your information from these sites, runs it by you to confirm. Then, it will continually monitor those same sites, as your information will likely reappear every two to four months.
Do not underestimate the tenacity of a cybercriminal. Even for people who have the attitude that their PII is bound to be somewhere online and that it’s no big deal, McAfee Personal Data Cleanup manages three key steps in the data removal process: scanning, removing, and monitoring. So, even if you’re not convinced that data brokerage sites are a threat, the process is too easy to put off any longer!
For those who are concerned about their online privacy, full-service Personal Data Cleanup is included in McAfee+ Ultimate, which is the complete package to let you live your online life in private. McAfee+ Ultimate also includes identity monitoring and identity theft resolution services, unlimited VPN, credit lock, and much more.
In 2021, more than 1.4 million identity theft complaints were filed to the Federal Trade Commission.1 Identity theft can occur to anyone, so take steps today, starting with data brokerage sites, to live a more secure and more private digital life.
1Federal Trade Commission, “New Data Shows FTC Received 2.8 Million Fraud Reports from Consumers in 2021”
The post McAfee Personal Data Cleanup: Your Partner in Living a More Private Online Life appeared first on McAfee Blog.
Finally, after nearly 3 long years, I'm back in Norway! We're here at last, leaving our sunny paradise for a winter wonderland. It's almost surreal given how much has happened in that time, not just the pandemic but returning to Oslo with Charlotte as my Norwegian wife is super cool 😎 Other things this week are not so different, namely people complaining on Twitter (albeit also complaining about Twitter). As I find myself continually caveating, YMMV but it does feel like events are being overly dramatised by some at present. Time will tell, but I think we'll all still be using the platform to complain about things just as effectively in a year from now as we are today 🙂
