
What color jersey will you be sporting this November and December? The World Cup is on its way to television screens around the world, and scores of fans are dreaming of cheering on their team at stadiums throughout Qatar. Meanwhile, cybercriminals are dreaming of stealing the personally identifiable information (PII) of fans seeking last-minute vacation and ticket deals.
Don’t let the threat of phishers and online scammers dampen your team spirit this World Cup tournament. Here are three common schemes cybercriminals will likely employ and a few tips to help you dribble around their clumsy offense and protect your identity, financial information, and digital privacy.
Phishers will be out in full force attempting to capitalize on World Cup fever. People wrapped up in the excitement may jump on offers that any other time of the year they would treat with skepticism. For example, in years past, fake contests and travel deals inundated email inboxes across the world. Some companies do indeed run legitimate giveaways, and cybercriminals slip in their phishing attempts among them.
If you receive an email or text saying that you’re the winner of a ticket giveaway, think back: Did you even enter a contest? If not, treat any “winner” notification with skepticism. It’s very rare for a company to automatically enter people into a drawing. Usually, companies want you to act – subscribe to a newsletter or engage with a social media post, for example – in exchange for your entry into their contest. Also, beware of emails that urge you to respond within a few hours to “claim your prize.” While it’s true that real contest winners must reply promptly, organized companies will likely give you at least a day if not longer to acknowledge receipt.
Traveling is rarely an inexpensive endeavor. Flights, hotels, rental cars, dining costs, and tourist attraction admission fees add up quickly. In the case of this year’s host country, Qatar, there’s an additional cost for American travelers: visas.
If you see package travel deals to the World Cup that seem too good to pass up … pass them up. Fake ads for ultra-cheap flights, hotels, and tickets may appear not only in your email inbox but also on your social media feed. Just because it’s an ad doesn’t mean it comes from a legitimate company. Legitimate travel companies will likely have professional-looking websites with clear graphics and clean website copy. Search for the name of the organization online and see what other people have to say about the company. If no search results appear or the website looks sloppy, proceed with caution or do not approach at all.
Regarding visas, be wary of anyone offering to help you apply for a visa. There are plenty of government-run websites that’ll walk you through the process, which isn’t difficult as long as you leave enough time for processing. Do not send your physical passport to anyone who is not a confirmed government official.
Even fans who’ve given up on watching World Cup matches in person aren’t out of the path of scams. Sites claiming to have crystal clear streams of every game could be malware spreaders in disguise. Malware and ransomware targeting home computers often lurk on sketchy sites. All it takes is a click on one bad link to let a cybercriminal or a virus into your device.
Your safest route to good-quality live game streams is through the official sites of your local broadcasting company or the official World Cup site. You may have to pay a fee, but in the grand scheme of things, that fee could be a lot less expensive than replacing or repairing an infected device.
Here’s an excellent rule to follow with any electronic correspondence: Never send anyone your passwords, routing and account number, passport information, or Social Security Number. A legitimate organization will never ask for your password, and it’s best to communicate any sensitive financial or identifiable information over the phone, not email or text as they can easily fall into the wrong hands. Also, do not wire large sums of money to someone you just met online.
Don’t let scams ruin your enjoyment of this year’s World Cup! With these tips, you should be able to avoid the most common schemes but to boost your confidence in your online presence, consider signing up for McAfee+. Think of McAfee+ as the ultimate goalkeeper who’ll block any cybercriminals looking to score on you. With identity monitoring, credit lock, unlimited VPN and antivirus, and more, you can surf safely and with peace of mind.
The post Watch Out for These 3 World Cup Scams appeared first on McAfee Blog.

It's very strange to have gone 1,051 days without spending more than a few hours apart, but here we are... very temporarily:
Only 15,501km away 😢 And only 4 days until I head back to Oslo 😊 pic.twitter.com/PDn1Syplig
— Troy Hunt (@troyhunt) November 20, 2022
Which means that right now, I'm throwing myself into a gazillion other things to keep me busy including how schools advise parents to manage devices, wrapping gup that HTML signature, asking probing questions about paying ransoms and, unbelievably, fighting off the most ridiculous claim of HIBP having been P'd. That last one especially, FFS, just listen...


Following up on our previous blog, How to Stop the Popups, McAfee Labs saw a sharp decrease in the number of deceptive push notifications reported by McAfee consumers running Microsoft’s Edge browser on Windows.
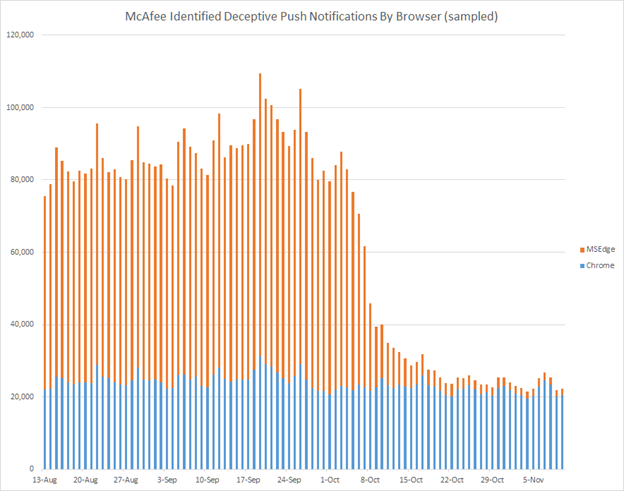
Such browser-delivered push messages appear as toaster pop-ups in the tray above the system clock and are meant to trick users into taking various actions, such as installing software, purchasing a subscription, or providing personal information.
Upon further investigation, this major drop seems to be associated with a change in the behavior of the Edge browser with two notable improvements over older versions.
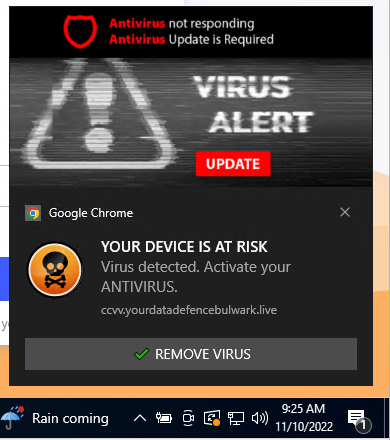
First, when users visit websites known to deliver deceptive push notifications, Edge blocks authorization prompts that could trick users into opting-in to receive popups:
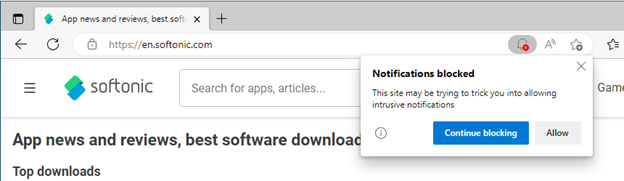
Second, when unwanted popups do occur, it is now easier than ever to disable them, on a per-site basis. Users can simply click the three dots (…) on the right of the notification and choose to “Turn off all notifications for” the domain responsible for the popup.

This is a great improvement over the previous experience of having to manually navigate browser settings to achieve the desired result.
Earlier this year, 9TO5Google reported a Chrome code change may be indicative of a similar crack down by Google on nefarious popups.
One can hope Google will follow Microsoft’s example to improve browser security and usability.
The post Microsoft’s Edge over Popups (and Google Chrome) appeared first on McAfee Blog.


puppi-car-1200




What a week to pick to be in Canberra. Planned well before things got cyber-crazy in Australia, I spent a few days catching up with folks in our capital and talking to the Australia Federal Police for scam awareness week. That it coincided with the dumping of Medibank customer health records made it an especially interesting time to talk with police, politicians and industry leaders. A bit of a bizarre, whirlwind week if I'm honest, but full of very positive encounters even though it coincided with such a demanding time for many of us in this industry down here.

A nonprofit organization is suing the state of Massachusetts on behalf of thousands of low-income families who were collectively robbed of more than a $1 million in food assistance benefits by card skimming devices secretly installed at cash machines and grocery store checkout lanes across the state. Federal law bars states from replacing these benefits using federal funds, and a recent rash of skimming incidents nationwide has disproportionately affected those receiving food assistance via state-issued prepaid debit cards.

The Massachusetts SNAP benefits card looks more like a library card than a payment card.
On Nov. 4, The Massachusetts Law Reform Institute (MLRI) filed a class action lawsuit on behalf of low-income families whose Supplemental Nutrition and Assistance Program (SNAP) benefits were stolen from their accounts. The SNAP program serves over a million people in Massachusetts, and 41 million people nationally.
“Over the past few months, thieves have stolen over a million SNAP dollars from thousands of Massachusetts families – putting their nutrition and economic stability at risk,” the MLRI said in a statement on the lawsuit. “The criminals attach a skimming device on a POS (point of sale) terminal to capture the household’s account information and PIN. The criminals then use that information to make a fake card and steal the SNAP benefits.”
In announcing the lawsuit, the MRLI linked to a story KrebsOnSecurity published last month that examined how skimming thieves increasingly are targeting SNAP payment card holders nationwide. The story looked at how the vast majority of SNAP benefit cards issued by the states do not include the latest chip technology that makes it more difficult and expensive for thieves to clone them.
The story also highlighted how SNAP cardholders usually have little recourse to recover any stolen funds — even in unlikely cases where the victim has gathered mountains of proof to show state and federal officials that the fraudulent withdrawals were not theirs.
Deborah Harris is a staff attorney at the MLRI. Harris said the goal of the lawsuit is to force Massachusetts to reimburse SNAP skimming victims using state funds, and to convince The U.S. Department of Agriculture (USDA) — which funds the program that states draw from — to change its policies and allow states to replace stolen benefits with federal funds.
“Ultimately we think it’s the USDA that needs to step up and tell states they have a duty to restore the stolen benefits, and that USDA will cover the cost at least until there is better security in place, such as chip cards,” Harris told KrebsOnSecurity.
“The losses we’re talking about are relatively small in the scheme of total SNAP expenditures which are billions,” she said. “But if you are a family that can’t pay for food because you suddenly don’t have money in your account, it’s devastating for the family.”
The USDA has not said it will help states restore the stolen funds. But on Oct. 31, 2022, the agency released guidance (PDF) whose primary instructions were included in an appendix titled, Card Security Options Available to Households. Notably, the USDA did not mention the idea of shifting to chip-based SNAP benefits cards.

The recently issued USDA guidance.
“The guidance generally continues to make households responsible for preventing the theft of their benefits as well as for suffering the loss when benefits are stolen through no fault of the household,” Harris said. “Many of the recommendations are not practical for households who don’t have a smartphone to receive text messages and aren’t able to change their PIN after each transaction and keep track of the new PIN.”
Harris said three of the four recommendations are not currently available in Massachusetts, and they are very likely not currently available in other states. For example, she said, Massachusetts households do not have the option of freezing or locking their cards between transactions. Nor do they receive alerts about transactions. And they most certainly don’t have any way to block out-of-state transactions.
“Perhaps these are options that [card] processors and states could provide, but they are not available now as far as we know,” Harris said. “Most likely they would take time to implement.”
The Center for Law and Social Policy (CLASP) recently published Five Ways State Agencies Can Support EBT Users at Risk of Skimming. CLASP says while it is true states can’t use federal funds to replace benefits unless the loss was due to a “system error,” states could use their own funds.
“Doing so will ensure families don’t have to go without food, gas money, or their rent for the month,” CLASP wrote.
That would help address the symptoms of card skimming, but not a root cause. Hardly anyone is suggesting the obvious, which is to equip SNAP benefit cards with the same security technology afforded to practically everyone else participating in the U.S. banking system.
There are several reasons most state-issued SNAP benefit cards do not include chips. For starters, nobody says they have to. Also, it’s a fair bit more expensive to produce chip cards versus plain old magnetic stripe cards, and many state assistance programs are chronically under-funded. Finally, there is no vocal (or at least well-heeled) constituency advocating for change.
A copy of the class action complaint filed by the MLRI is available here.

Authored by: Christy Crimmins and Oliver Devane
Football (or Soccer as we call it in the U.S.) is the most popular sport in the world, with over 3.5 billion fans across the globe. On November 20th, the men’s World Cup kicks off (pun intended) in Qatar. This event, a tournament played by 32 national teams every four years, determines the sport’s world champion. It will also be one of the most-watched sporting events of at least the last four years (since the previous World Cup).
An event with this level of popularity and interest also attracts fraudsters and cyber criminals looking to capitalize on fans’ excitement. Here’s how to spot these scams and stay penalty-free during this year’s tournament.
Phishing is a tool that cybercriminals have used for years now. Most of us are familiar with the telltale signs—misspelled words, poor grammar, and a sender email whose email address makes no sense or whose phone number is unknown. But excitement and anticipation can cloud our judgment. What football fan wouldn’t be tempted to win a free trip to see their home team participate in the ultimate tournament? Cybercriminals are betting that this excitement will cloud fans’ judgment, leading them to click on nefarious links that ultimately download malware or steal personal information.
It’s important to realize that these messages can come via a variety of channels, including email, text messages, (also known as smishing) and other messaging channels like WhatsApp and Telegram. No matter what the source is, it’s essential to remain vigilant and pause to think before clicking links or giving out personal or banking information.
For more information on phishing and how to spot a phisher, see McAfee’s “What is Phishing?” blog.
According to ActionFraud, the UK’s national reporting center for fraud and cybercrime, thousands of people were victims of ticket fraud in 2019—and that’s just in the UK. Ticket fraud is when someone advertises tickets for sale, usually through a website or message board, collects the payment and then disappears, without the buyer ever receiving the ticket.
The World Cup is a prime (and lucrative) target for this type of scam, with fans willing to pay thousands of dollars to see their teams compete. Chances are most people have their tickets firmly in hand (or digital wallet) by now, but if you’re planning to try a last-minute trip, beware of this scam and make sure that you’re using a legitimate, reputable ticket broker. To be perfectly safe, stick with well-known ticket brokers and those who offer consumer protection. Also beware of sites that don’t accept debit or credit cards and only accept payment in the form of bitcoin or wire transfers such as the one on the fake ticket site below:
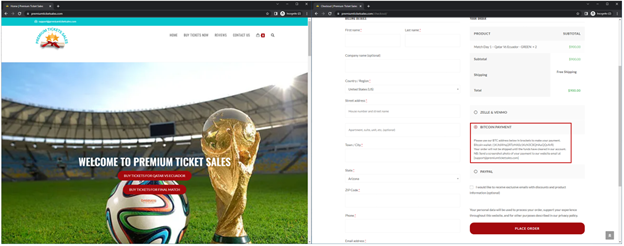
The red box on the right image shows that the ticket site accepts payment via Bitcoin.
Other red flags to look out for are websites that ask you to contact them to make payment and the only contact information is via WhatsApp.
Let’s be realistic—most of us are going to have to settle for watching the World Cup from the comfort of our own home, or the pub down the street. If you’re watching the tournament online, be sure that you’re using a legitimate streaming service. A quick Google of “FIFA World Cup 2022 Official Streaming” along with your country should get you the information you need to safely watch the event through official channels. The FIFA site itself is also a good source of information.
Illegal streaming sites usually contain deceptive ads and malware which can cause harm to your device.
In countries or regions where sports betting is legal, the 2022 World Cup is expected to drive an increase in activity. There’s no shortage of things to bet on, from a simple win/loss to the exact minute a goal will be scored by a particular player. Everything is subject to wager.
As with our previous examples, this increase in legitimate gambling brings with it an increase in deceptive activity. Online betting scams often start when users are directed to or search for gambling site and end up on a fraudulent one. After placing their bets and winning, users realize that while they may have “won” money, they are unable to withdraw it and are even sometimes asked to deposit even more money to make winnings available, and even then, they still won’t be. By the end of this process, the bettor has lost all their initial money (and then some, potentially) as well as any personal information they shared on the site.
Like other scams, users should be wary of sites that look hastily put together or are riddled with errors. Your best bet (yes, again, pun intended) is to look for an established online service that is approved by your government or region’s gaming commission. Finally, reading the fine print on incentives or bonuses is always a good idea. If something sounds too good to be true, it’s best to double-check.
For more on how you can bet online safely, and for details on how legalized online betting works in the U.S., check out our blog on the topic.
Using a free public Wi-Fi connection is risky. User data on these networks is unprotected, which makes it vulnerable to cyber criminals. Whether you’re traveling to Qatar for a match or watching the them with friends at your favorite pub, if you’re connecting to a public Wi-Fi connection, make sure you use a trusted VPN connection.
For more information on scams, visit our scam education page. Hopefully, with these tips, you’ll be able to enjoy and participate in some of the World Cup festivities, after all, fun is the goal!
The post Don’t Get Caught Offsides with These World Cup Scams appeared first on McAfee Blog.

I feel like life is finally complete: I have beaches, sunshine and fast internet! (Yes, and of course an amazing wife, but that goes without saying 😊) For the folks asking via various channels, the speed is not exactly symmetrical at 1000/400 and I'm honestly not sure why that's the case here in Australia. I also had to shell out quite a bit extra to go from 50 up to a "business" plan of 400 up, but with the volumes of data I ship around it'll make a pretty big difference to the way I work over time. Also this week, much more on the work we're doing with HIBP from pricing the annual plans to a proper support system via Zendesk. I'm really hoping that by next week's update we'll have shipped the new rate limits too, stay tuned for that but for now, here's number 320:





Geez we've been getting hammered down here: Optus, MyDeal, Vinomofo, Medibank and now Australian Clinical Labs. It's crazy how much press interest there's been down here and whilst I think some of it is a bit hyperbolic, bringing the issue to the forefront and ensuring it's being discussed is certainly a good thing. Anyway, let's see what happens between now and next week's video, at this rate there'll be at least one more major Aussie breach to talk about!


Aussie breachapalooza! That what it feels like this week between Optus (ok, it was weeks ago but it's still in the news), Vinomofo, My Deal and the mother of all of them (at least as far as media interest goes), Medibank. That last one totally smashed my week out with unprecedented press enquiries, so is it any wonder I totally missed the Microsoft one? I read through that last one live in this week's video and as you'll hear, a breach of any kind is never a good look but what stands out for me about this one isn't the breach itself, rather the marketing effort SOCRadar has made around it. As I say in the video, it just feels... icky. See if you agree.





I decided to do something a bit different this week and mostly just answer questions from my talk at GOTO Copenhagen last week. I wasn't actually in Denmark this time, but a heap of really good questions came through and as I started reading them, I thought "this would actually make for a really good weekly update". So here we are, and those questions then spurned on a whole heap more from the live audience too so this week's video became one large Q&A. I hope you enjoy this one, let me know if I should do more of these in the future.


Geez it's nice to be home 😊 It's nice to live in a home that makes you feel that way when returning from a place as beautiful as Bali 😊 This week's video is dominated by the whole discussion around this tweet:
I love that part of the Microsoft Security Score for Identity in Azure improves your score if you *don't* enforce password rotation, what a sign of the times! Who out there still works somewhere that forces rotation (because "reasons")? pic.twitter.com/a2yQQvNRpa
— Troy Hunt (@troyhunt) October 6, 2022
I love this for the way it throws traditional logic out the window, logic we all knew sucked and I suspect the massive engagement the tweet drove is due to precisely that: Microsoft giving us all a good reason to whinge about a sucky practice that still prevails so broadly. So... I hope you enjoy listening to just how bad enforced password rotation sucks 😊


How's this weeks video for a view?! It's a stunning location here in Bali and it's just been the absolute most perfect spot for a honeymoon, especially after weeks of guests and celebrations. But whoever hacked and ransom'd Optus didn't care about me taking time out and I've done more media in the last week than I have in a long time. I don't mind, it's a fascinating story the way this has unfolded and that's where most of the time in this week's video has gone, I hope you enjoy my analysis of what has become a pretty crazy story back home in Australia.


Wow, what a week! Of course there's lots of cyber / tech stuff in this week's update, but it was really only the embedded tweet below on my mind so I'm going to leave you with this then come to you from somewhere much more exotic than usual (and I reckon that's a pretty high bar for me!) next week 😎
Absolutely over the moon to formally make @Charlotte_Hunt_ a part of our family ❤️ 💍 pic.twitter.com/XfahXElboC
— Troy Hunt (@troyhunt) September 21, 2022


I came so close to skipping this week's video. I'm surrounded by family, friends and my amazing wife to be in only a couple of days. But... this video has been my constant companion through very difficult times, and I'm happy to still being doing it at the best of times 😊 So, with that, I'm signing out and heading off to do something much more important. See you next week.
Taking a bit of time off Twitter while @charlottelyng and I do more important things 💍 👰♀️ pic.twitter.com/9JJrPM9kWX
— Troy Hunt (@troyhunt) September 13, 2022


I'm so excited to see the book finally out and awesome feedback coming in, but I'm disappointed with this week's video. I frankly wasn't in the right frame of mind to do it justice (it's been a very hard road up until this point, for various reasons), then my connection dropped out halfway through and I had to roll to 5G, and now I'm hearing (both from other people and with my own ears), a constant background noise being picked up by the mic. Argh! But, that's the reality of scheduled live streams and for better or worse, you end up getting the "warts and all" version. It is what it is, and next week's will be better 😊

Well, after a crazy amount of work, a lot of edits, reflection, and feedback cycles, "Pwned" is almost here:
This better be a sizzling read @troyhunt or I'll be crashing the wedding in ways never done before.
— Mike Thompson (@AppSecBloke) August 30, 2022
Also, I thought they'd cancelled Neighbours? 😉❤️ pic.twitter.com/jrYIKtL0Uh
The preview cycle is in full swing with lots of feedback coming in and revisions being made before we push it live to the masses. This is really exciting and I can't wait to get the book out there in front of everyone, stay tuned 😊

Phishers are enjoying remarkable success using text messages to steal remote access credentials and one-time passcodes from employees at some of the world’s largest technology companies and customer support firms. A recent spate of SMS phishing attacks from one cybercriminal group has spawned a flurry of breach disclosures from affected companies, which are all struggling to combat the same lingering security threat: The ability of scammers to interact directly with employees through their mobile devices.

In mid-June 2022, a flood of SMS phishing messages began targeting employees at commercial staffing firms that provide customer support and outsourcing to thousands of companies. The missives asked users to click a link and log in at a phishing page that mimicked their employer’s Okta authentication page. Those who submitted credentials were then prompted to provide the one-time password needed for multi-factor authentication.
The phishers behind this scheme used newly-registered domains that often included the name of the target company, and sent text messages urging employees to click on links to these domains to view information about a pending change in their work schedule.
The phishing sites leveraged a Telegram instant message bot to forward any submitted credentials in real-time, allowing the attackers to use the phished username, password and one-time code to log in as that employee at the real employer website. But because of the way the bot was configured, it was possible for security researchers to capture the information being sent by victims to the public Telegram server.
This data trove was first reported by security researchers at Singapore-based Group-IB, which dubbed the campaign “0ktapus” for the attackers targeting organizations using identity management tools from Okta.com.
“This case is of interest because despite using low-skill methods it was able to compromise a large number of well-known organizations,” Group-IB wrote. “Furthermore, once the attackers compromised an organization they were quickly able to pivot and launch subsequent supply chain attacks, indicating that the attack was planned carefully in advance.”
It’s not clear how many of these phishing text messages were sent out, but the Telegram bot data reviewed by KrebsOnSecurity shows they generated nearly 10,000 replies over approximately two months of sporadic SMS phishing attacks targeting more than a hundred companies.
A great many responses came from those who were apparently wise to the scheme, as evidenced by the hundreds of hostile replies that included profanity or insults aimed at the phishers: The very first reply recorded in the Telegram bot data came from one such employee, who responded with the username “havefuninjail.”
Still, thousands replied with what appear to be legitimate credentials — many of them including one-time codes needed for multi-factor authentication. On July 20, the attackers turned their sights on internet infrastructure giant Cloudflare.com, and the intercepted credentials show at least three employees fell for the scam.
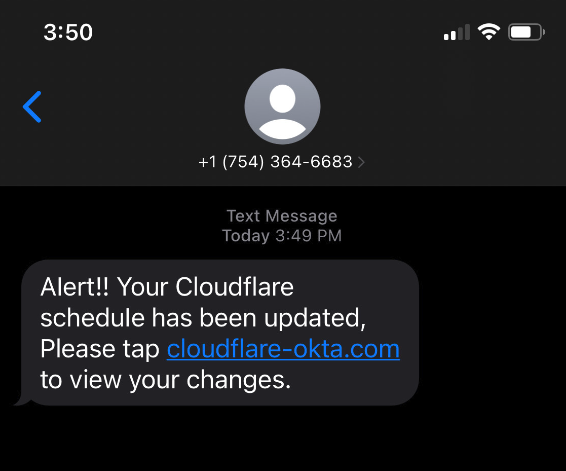
Image: Cloudflare.com
In a blog post earlier this month, Cloudflare said it detected the account takeovers and that no Cloudflare systems were compromised. Cloudflare said it does not rely on one-time passcodes as a second factor, so there was nothing to provide to the attackers. But Cloudflare said it wanted to call attention to the phishing attacks because they would probably work against most other companies.
“This was a sophisticated attack targeting employees and systems in such a way that we believe most organizations would be likely to be breached,” Cloudflare CEO Matthew Prince wrote. “On July 20, 2022, the Cloudflare Security team received reports of employees receiving legitimate-looking text messages pointing to what appeared to be a Cloudflare Okta login page. The messages began at 2022-07-20 22:50 UTC. Over the course of less than 1 minute, at least 76 employees received text messages on their personal and work phones. Some messages were also sent to the employees family members.”
On three separate occasions, the phishers targeted employees at Twilio.com, a San Francisco based company that provides services for making and receiving text messages and phone calls. It’s unclear how many Twilio employees received the SMS phishes, but the data suggest at least four Twilio employees responded to a spate of SMS phishing attempts on July 27, Aug. 2, and Aug. 7.
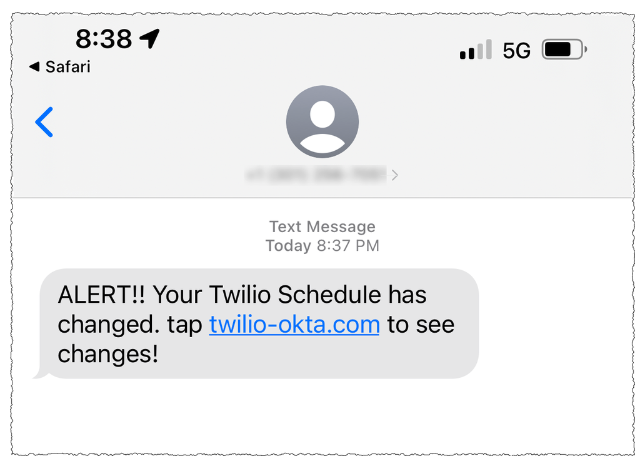
On that last date, Twilio disclosed that on Aug. 4 it became aware of unauthorized access to information related to a limited number of Twilio customer accounts through a sophisticated social engineering attack designed to steal employee credentials.
“This broad based attack against our employee base succeeded in fooling some employees into providing their credentials,” Twilio said. “The attackers then used the stolen credentials to gain access to some of our internal systems, where they were able to access certain customer data.”
That “certain customer data” included information on roughly 1,900 users of the secure messaging app Signal, which relied on Twilio to provide phone number verification services. In its disclosure on the incident, Signal said that with their access to Twilio’s internal tools the attackers were able to re-register those users’ phone numbers to another device.
On Aug. 25, food delivery service DoorDash disclosed that a “sophisticated phishing attack” on a third-party vendor allowed attackers to gain access to some of DoorDash’s internal company tools. DoorDash said intruders stole information on a “small percentage” of users that have since been notified. TechCrunch reported last week that the incident was linked to the same phishing campaign that targeted Twilio.
This phishing gang apparently had great success targeting employees of all the major mobile wireless providers, but most especially T-Mobile. Between July 10 and July 16, dozens of T-Mobile employees fell for the phishing messages and provided their remote access credentials.
“Credential theft continues to be an ongoing issue in our industry as wireless providers are constantly battling bad actors that are focused on finding new ways to pursue illegal activities like this,” T-Mobile said in a statement. “Our tools and teams worked as designed to quickly identify and respond to this large-scale smishing attack earlier this year that targeted many companies. We continue to work to prevent these types of attacks and will continue to evolve and improve our approach.”
This same group saw hundreds of responses from employees at some of the largest customer support and staffing firms, including Teleperformanceusa.com, Sitel.com and Sykes.com. Teleperformance did not respond to requests for comment. KrebsOnSecurity did hear from Christopher Knauer, global chief security officer at Sitel Group, the customer support giant that recently acquired Sykes. Knauer said the attacks leveraged newly-registered domains and asked employees to approve upcoming changes to their work schedules.
Knauer said the attackers set up the phishing domains just minutes in advance of spamming links to those domains in phony SMS alerts to targeted employees. He said such tactics largely sidestep automated alerts generated by companies that monitor brand names for signs of new phishing domains being registered.
“They were using the domains as soon as they became available,” Knauer said. “The alerting services don’t often let you know until 24 hours after a domain has been registered.”
On July 28 and again on Aug. 7, several employees at email delivery firm Mailchimp provided their remote access credentials to this phishing group. According to an Aug. 12 blog post, the attackers used their access to Mailchimp employee accounts to steal data from 214 customers involved in cryptocurrency and finance.
On Aug. 15, the hosting company DigitalOcean published a blog post saying it had severed ties with MailChimp after its Mailchimp account was compromised. DigitalOcean said the MailChimp incident resulted in a “very small number” of DigitalOcean customers experiencing attempted compromises of their accounts through password resets.
According to interviews with multiple companies hit by the group, the attackers are mostly interested in stealing access to cryptocurrency, and to companies that manage communications with people interested in cryptocurrency investing. In an Aug. 3 blog post from email and SMS marketing firm Klaviyo.com, the company’s CEO recounted how the phishers gained access to the company’s internal tools, and used that to download information on 38 crypto-related accounts.

A flow chart of the attacks by the SMS phishing group known as 0ktapus and ScatterSwine. Image: Amitai Cohen for Wiz.io. twitter.com/amitaico.
The ubiquity of mobile phones became a lifeline for many companies trying to manage their remote employees throughout the Coronavirus pandemic. But these same mobile devices are fast becoming a liability for organizations that use them for phishable forms of multi-factor authentication, such as one-time codes generated by a mobile app or delivered via SMS.
Because as we can see from the success of this phishing group, this type of data extraction is now being massively automated, and employee authentication compromises can quickly lead to security and privacy risks for the employer’s partners or for anyone in their supply chain.
Unfortunately, a great many companies still rely on SMS for employee multi-factor authentication. According to a report this year from Okta, 47 percent of workforce customers deploy SMS and voice factors for multi-factor authentication. That’s down from 53 percent that did so in 2018, Okta found.
Some companies (like Knauer’s Sitel) have taken to requiring that all remote access to internal networks be managed through work-issued laptops and/or mobile devices, which are loaded with custom profiles that can’t be accessed through other devices.
Others are moving away from SMS and one-time code apps and toward requiring employees to use physical FIDO multi-factor authentication devices such as security keys, which can neutralize phishing attacks because any stolen credentials can’t be used unless the phishers also have physical access to the user’s security key or mobile device.
This came in handy for Twitter, which announced last year that it was moving all of its employees to using security keys, and/or biometric authentication via their mobile device. The phishers’ Telegram bot reported that on June 16, 2022, five employees at Twitter gave away their work credentials. In response to questions from KrebsOnSecurity, Twitter confirmed several employees were relieved of their employee usernames and passwords, but that its security key requirement prevented the phishers from abusing that information.
Twitter accelerated its plans to improve employee authentication following the July 2020 security incident, wherein several employees were phished and relieved of credentials for Twitter’s internal tools. In that intrusion, the attackers used Twitter’s tools to hijack accounts for some of the world’s most recognizable public figures, executives and celebrities — forcing those accounts to tweet out links to bitcoin scams.
“Security keys can differentiate legitimate sites from malicious ones and block phishing attempts that SMS 2FA or one-time password (OTP) verification codes would not,” Twitter said in an Oct. 2021 post about the change. “To deploy security keys internally at Twitter, we migrated from a variety of phishable 2FA methods to using security keys as our only supported 2FA method on internal systems.”
Update, 6:02 p.m. ET: Clarified that Cloudflare does not rely on TOTP (one-time multi-factor authentication codes) as a second factor for employee authentication.