We have entered a world where uncertainty has become the normal operating mode for everyone. Within this new frontier, cybersecurity has become even more challenging. However, some cybersecurity professionals have stood out, using their unique skills and resourcefulness to protect the integrity of their businesses, and to withstand unpredictable and dynamically changing threats. In the end, they, and their businesses have emerged even stronger.
These accomplishments have lead them to be selected from over more than 700 Cisco Cybersecurity Advocates – who are also members of Cisco Insider Advocates – to join the League of Cybersecurity Heroes.
Cisco Insider Advocates is a peer networking community developed several years ago for Cisco customers around the globe. Currently, over 14,000 customers are using it to share technology insights, feedback, and best practices, and also to make meaningful connections with others in the industry. We at Cisco believe that when we connect, anything is possible, and the Insider Advocacy program is a great example of the great things that can happen when people come together.
As the global CISO of Mediapro, Roberto has deployed Cisco SecureX together with Umbrella, Secure Endpoint, Secure Firewall, ISE, NGIP, Threat Response, AnyConnect, and Web security. With this partnership, Mediapro has reduced its threat detection time by 90%. In addition, they have seen no false positives in their threat detection alerts. It is rare to boast of a 100% success rate, but they can boldly make that pronouncement. All of this has also benefitted Mediapro financially by incurring zero fines for any compliance issues
What do music, cybersecurity, and teaching all have in common? They all culminate in a readiness to perform. Equally, they all require collaboration, comfort with the unexpected, and a passion for the job. Blair exemplifies the best of these traits, and in doing so, he provides inspiration and excellence to all with whom he interacts. Watching Blair at work makes one wonder if there are more hours granted to him during a day than the average person. He is a time-maximizer, spending most of that time in the service of others.
Too often, cybersecurity certifications are treated derisively by some of the very professionals who need them most. This is not the case with Kevin, who can list the many benefits of attaining certifications. Kevin’s desire to improve his knowledge doesn’t stop with technology and cybersecurity. He is an avid reader of anything that can raise him up to be better than he was the day before. With a career that started in the US Marine Corps, Kevin continues to learn and grow, all the while remaining as masterful at a computer keyboard as he is his with his traditional 55-gallon-barrel BBQ smoker and grill.
Steve is a Senior Cybersecurity and Network Architect at Lake Trust Credit Union. Like most organizations, Lake Trust has had to transition to a completely remote workforce quickly, and thanks to Secure Network Analytics, they were able to transition the employees to work remotely while maintaining the same high level of visibility and protection in place. Steve was the subject of a case study about the benefits that Cisco products have brought to Lake Trust Credit Unions’ customers. He is currently collaborating to update that information to share more of his knowledge.
Being the Head of Information Technology is never an easy job. However, when food manufacturer, Leng-d’Or, was faced with a challenge during the pandemic that could have interrupted its production line, quick thinking, skilled leadership, and a close partnership with Cisco all lead to positive outcomes, and helped them to pull through stronger than before. Part of this success comes from Enric’s distinct understanding of the threats, solutions, and processes needed to bring security to a higher level for the Leng-d’Or organization. Enric also shares his success story very freely, adding immeasurable benefits to the security community.
Cybersecurity is truly a global discipline. Tony Dous proves this by practicing his craft as a Senior Network Security Engineer in Cairo, Egypt. Tony’s involvement with the Cisco community shows how no distance is too far for a motivated cybersecurity professional.
When John Patrick is on the job, there is no longer any feeling that the criminals are one-step ahead of the good guys. He adopted Umbrella together with Meraki to develop a proactive security approach inside his organization. John Patrick created a more unified network from a patchwork of disparate entities. In doing so, he reduced the complexity within the environment. Complexity is so often responsible for security gaps, and John Patrick’s work not only corrected those gaps, but he brought people together in the process. He and his team received great feedback from the employees, who enjoyed a consistent network experience.
We often hear stories about teenagers who become enamored with technology, leading to the fulfillment of a dream. Amit Gumber became interested in cybersecurity at an early age, pursued his passion and has worked in the field ever since. His sense of advocacy is best described in his own words: “I’m quite passionate about sharing knowledge and ideas with peers and participating in collaborative activities.” Amit’s use of Cisco technologies has helped HCL Technologies to stabilize and secure their environment.
One of the most important factors for success is insatiable curiosity. Mark Healey is a continuous learner, and he is an example of someone who enthusiastically shares his knowledge. Whether it is on a personal level, or through his high engagement as part of the Cisco Insider Advocates community, or as an active member of the Internet Society, Mark is an evangelist and a positive voice for cybersecurity.
Wouter holds a special designation, not only as a member of the League of Cybersecurity Heroes, but also as the recipient of the “Cybersecurity Defender of the Year” award. Wouter is an active participant in the cybersecurity community, working with an almost evangelical zeal towards sharing the importance of holistic cybersecurity. His contributions stand out towards making the cyber realm a safer place.
It is often said that the job of a cybersecurity professional in an educational facility is especially challenging. When that facility happens to be the largest in an entire country, with over 4,000 schools and universities, the job of protecting it can seem insurmountable. At AzEduNet, in Azerbaijan, Bahruz and his team is tasked with securing the network for its 1.5 Million students. With Cisco Secure, the security team reduced security incidents by 80%. This not only ensures access for the students, but also keeps the data safe.
Many people want to enter the cybersecurity profession, but few have the dedication and perseverance to fully embrace the skillset required to meet that goal. Walther Noel not only had the desire to refocus his career, but he proved it by earning the CyberOps Associate Certification. His accomplishment is a prime example of how one can step outside of their comfort zone to grow and thrive.
Pascual demonstrates how important it is to make the most of the learning opportunities in Cisco Insiders Advocates. While already a successful NOC engineer, he sought to advance his professional development by studying cybersecurity. He passed the CCNA CyberOps 200-201 exam, moving him closer to propelling his career to even higher achievements.
One of the noblest expressions of knowledge is the desire to freely share that information. Inderdeep lives up to this ideal, offering his expertise to all with no expectations of reciprocity. His charitable spirit has not gone unnoticed, as he has been a previous award winner for Cisco IT Blogs, as well as a designation on the Feedspot top 100 Networking Blog.
Being the first to try a new technology can be a risky proposition. However, as a COO, risk calculations are in one’s blood. Luigi, along with the Sara Assicurazioni organization, hails as the first company in Italy to embrace cloud technology. As a company with more than one million customers, this was a bold initiative that required careful planning, keen insight, and above all, collaboration. In the end, this has resulted not only in a digital transformation, but a business transformation.
Whether it is a technical achievement, a personal triumph, or a spirit of helping others, each member of our League of Cybersecurity Heroes proves how technology and humanity can work together to accomplish the impossible. Congratulations to all of them!
We’d love to hear what you think. Ask a Question, Comment Below, and Stay Connected with Cisco Secure on social!
Cisco Secure Social Channels
Instagram
Facebook
Twitter
LinkedIn
Few security career paths are linear. For Stephanie Frankel the journey to Cisco Secure was circuitous. The Ann Arbor, Michigan native studied journalism at the University of Michigan before managing communications for the Washington Capitals and NBC Sports. But after several stints at communications agencies, she charted a new path for herself in cybersecurity. Not only has her diverse background served as a strength in her current role as senior manager for strategy and operations, but it’s also informed her management philosophy.
After doing project management and account direction at consulting agencies, Frankel was interested in honing her skills and expertise on the client side. She had heard amazing things about Duo and wanted to stay in Ann Arbor and work for a company with local roots. After interviewing, Frankel realized that “working at Duo was a cool, exciting opportunity with a really awesome group of people.”
Frankel was on the ground running working as a technical project manager in research and development overseeing the Multi-Factor Authentication, applications and mobile engineering teams despite not having worked in information security before.
Duo’s security education allowed Frankel to understand the industry and is something she values for getting more people into the cybersecurity field. At Duo and Cisco Secure, employees come from a variety of backgrounds and some don’t have much (or any) experience with cybersecurity.
Robust educational programs build knowledge about security and specific products which empower new team members to grow and learn. Every team also has a learning and development budget for employees to quench their curiosity and enhance their knowledge through courses, books or other programs Manager of Global Employee Programs Anndrea Boris shared.
“People are open to having conversations and open to ideas and ways to solve those ideas. If you have an idea of how to solve a problem, no matter whether it’s your job or not, people are open and willing to listen to you.” – Stephanie Frankel
Something Frankel also appreciates most is that ideas are valued at Duo and Cisco Secure: “Even in my first job, I would have ideas and go to my boss or our head of engineering and say, ‘Hey, I think this could be a really cool opportunity, and I think it needs this.’ People are open to having conversations and open to ideas and ways to solve those ideas. If you have an idea of how to solve a problem, no matter whether it’s your job or not, people are willing to listen to you.”
After a year, Frankel moved from engineering to marketing to run operations for Duo’s in-house brand team, leading the team through a rebrand. “The team really rallied behind this new brand and it was amazing to see their pride and hard work when sharing it,” she said. With Frankel’s leadership, the team showcased not only the new look and feel of the brand but also the customer research that went into understanding the need for the change.

“Our amazing team knew that for it to catch on internally we needed to help people understand the why. The team put together an amazing training and went around the company to help people understand the security buyer, the industry overall and our differentiators and how we could do all of this within the umbrella of Cisco,” she said.
Recognizing that she most enjoys and feels best suited for a strategic operations role, she had open conversations with her manager. “I told my boss, ‘It’s just not a great fit.’” Her manager was very supportive, and they worked through potential options. “You’ll find a lot of that at Cisco,” she said.
Now as senior manager in the Strategy and Operations Group within Cisco’s Security and Collaboration division, Frankel runs key initiatives for business operations that drive business growth. She is empowered to creatively solve problems and collaborate “with all the stakeholders within each group to move these programs forward, to understand the problems we’re looking to solve, create objectives, a program plan, and continue to track metrics and progress towards those ultimate goals,” she said.
A self-described “over communicator,” Frankel believes that as a leader, “the more you communicate and the more transparent you are, the better.” Frankel loves leading people who are experts in their fields and letting them do what they do best.
On the brand team, for example, she trusted her team’s expertise in producing stories, videos and animations to demystify Cisco’s security products.
“All I needed to do was give them the objective and the goals and they were able to come up with the solutions,” Frankel said.
She fondly remembers the boss at one of her first jobs out of college. In that job Frankel wrote press releases and wanted her boss to fully approve the final versions before sending them to the media. Once her boss told her, “Stephanie, if you keep giving it back to me, I will keep finding things to change. I trust you to know when it is ready to go.” That confidence in her so early in her career “gave me so much confidence in myself,” she said.
Frankel emulates his approach to management by recognizing that each employee has different needs in their lives, in their careers, and in how they like to receive feedback. From that boss Frankel first learned that for every piece of negative feedback, you must give four pieces of positive feedback for “someone to actually hear it because that’s how you balance things out in your mind.”

Frankel believes feedback is crucial for growth. “I don’t see how you can improve or grow without it, no matter what level of your career you’re at. Feedback shouldn’t be taken as negative, as much as it is a way for you to improve,” she said.
One of the most helpful things Frankel learned in a Cisco class for managers was the importance of asking a person if they are in a good place to receive critical feedback. “You might not be in the mindset to accept the feedback and to do something constructive with it,” she said. ”If you’re having a bad day or struggling, you could say, ‘You know what, I’m not going to be able to take it today, but let’s talk tomorrow and I’ll be in a better place to receive it.’’’
Frankel has spent the last year thriving in a role she never anticipated in an industry her college training in journalism didn’t fully prepare her for. The secret, she says, is keeping an open mind to new possibilities and a willingness to take on new challenges, even if you don’t feel 100% ready.
“A lot of it is getting real world experience and learning your way through it and knowing that there’s a lot of opportunities and a lot of people that are willing to teach you,” she said.

To pivot professionally Frankel advises not feeling pigeonholed just because you studied a particular topic or have been in a certain industry for a long time. Take what you can from where you started such as storytelling and communications skills in the case of journalism for Frankel. While trying something new may require taking a different level or type of job “sometimes it’s worth it because you have that opportunity to grow and you might find you’re happier somewhere else,” she said.
When discerning professional steps Frankel recommends having open and honest conversations with yourself and others such as mentors.
“Cisco has so many mentorship programs and so many people that are knowledgeable about a lot of things,” she said. ”Just because your current role isn’t a great fit doesn’t mean that there’s not another good fit within the corporation, or it doesn’t mean that you can’t create your own good fit.”
Did you know that Cisco offers cybersecurity trainings and certifications? Start developing your cybersecurity skills today! And if you’re ready to jump into an exciting new career in security, check out the open roles at Cisco Secure and Duo Security.

We’d love to hear what you think. Ask a Question, Comment Below, and Stay Connected with Cisco Secure on social!
Cisco Secure Social Channels
As the world continues to face formidable challenges, one of the many things impacted is cybersecurity. While recent challenges have been varied, they have all contributed to great uncertainty. How can organizations stay strong and protect their environments amidst so much volatility?
Lately we’ve been talking a lot about security resilience, and how companies can embrace it to stay the course no matter what happens. By building a resilient security strategy, organizations can more effectively address unexpected disruptions and emerge stronger.
Through our Security Outcomes Study, Volume 2, we were able to benchmark how companies around the world are doing when it comes to cyber resilience. Recent blog posts have taken a look at security resilience in the EMEA and Americas regions, and this post assesses resilience in Asia Pacific, Japan and China (APJC).
While the Security Outcomes Study focuses on a dozen outcomes that contribute to overall security program success, for this analysis, we focused on four specific outcomes that are most critical for security resilience. These include: keeping up with the demands of the business, avoiding major cyber incidents, maintaining business continuity, and retaining talented personnel.
The following chart shows the proportion of organizations in each market within APJC that reported “excelling” in these four outcomes:

There is a lot of movement in this chart, but if you take a closer look, you will see that many of the percentage differences between markets are quite small. For example, 44.9% of organizations in the Philippines reported that they are proficient at keeping up with the business, with Mainland China closely following at 44.4%.
The biggest difference we see between the top spot and the bottom spot is around retaining security talent—42.4% of organizations in Australia reported that they were successful in that area, while only 18.3% of organizations in Hong Kong reported the same.
Next, we looked at the mean resilience score for each market in the region:

When we look at this, we can see the differences between the top six and bottom seven markets a bit more clearly. However, as the previous chart also showed, the differences are very slight. (When we take into account the gray error bars, they become even more slight.)
There are many factors that could contribute to these small differences when it comes to security resilience. But the most important thing to be gleaned from this data is how each market can improve its respective resilience level.
The Security Outcomes Study revealed the top five practices—what we refer to as “The Fab Five”—that make the most impact when it comes to enhancing security. The following chart outlines the Fab Five, and demonstrates how each market in the APJC region ranked its own strength across these practices.

If we look at Thailand, for example, 69.1% of organizations say they are adept at accurate threat detection, while only 28% of organizations in Taiwan say the same. Like in the previous charts, there is a lot of movement between how various markets reported their performance against these practices. However, it’s interesting to note that Taiwan remained consistent.
So does implementing the Fab Five improve resilience across organizations in APJC? Looking at the chart below, it’s safe to say that, yes, implementing the Fab Five does improve resilience. Organizations in APJC that did not implement any of the Fab Five practices ranked in the bottom 30% for resilience, whereas those that reported strength in all five rose to the top 30%.

While building resilience can sometimes seem like an elusive concept, we hope this data provides some concrete benchmarks to strive for in today’s security programs.
We’d love to hear what you think. Ask a Question, Comment Below, and Stay Connected with Cisco Secure on social!
Cisco Secure Social Channels
Instagram
Facebook
Twitter
LinkedIn

Today, we released the latest issue of The Domain Name Industry Brief, which shows that the first quarter of 2022 closed with 350.5 million domain name registrations across all top-level domains, an increase of 8.8 million domain name registrations, or 2.6%, compared to the fourth quarter of 2021.1,2 Domain name registrations have increased by 13.2 million, or 3.9%, year over year.1,2

Check out the latest issue of The Domain Name Industry Brief to see domain name stats from the first quarter of 2022, including:
• Top 10 Largest TLDs by Number of Reported Domain Names
• Top 10 Largest ccTLDs by Number of Reported Domain Names
• ngTLDs as Percentage of Total TLDs
• Geographical ngTLDs as Percentage of Total Corresponding Geographical TLDs
To see past issues of The Domain Name Industry Brief, please visit verisign.com/dnibarchives.
The post Verisign Q1 2022 Domain Name Industry Brief: 350.5 Million Domain Name Registrations in the First Quarter of 2022 appeared first on Verisign Blog.





eleceye-1200


As an avid internet surfer, you’ve most likely heard of cookies. No, we’re not talking about the ones filled with chocolate chips. We’re talking about the ones that allow you to log in to your favorite websites. Cookies may impact your online security, so check out these tips to manage them and keep your online accounts safe.
Ever wonder how a website saves the items you placed in your shopping cart last week, even though you closed the tab before making the purchase? This is made possible by cookies. According to the Federal Trade Commission, a cookie is information saved by your web browser. When you visit a website, the site may place a cookie on your web browser so it can recognize your device in the future. If you return to that site later, it can read that cookie to remember you from your last visit, keeping track of your activities over time.1
Cookies come in either the first-party or third-party variety. There’s no difference between the two in how they function, but rather in where and how you encountered them. First-party cookies belong to sites you visited first-hand in your browser. Third-party cookies, or “tracking cookies,” generally come from third-party advertising websites.
Although cookies generally function the same, there are technically two different types of cookies. Magic cookies refer to packets of information that are sent and received without changes. Historically, this would be used to log in to a computer database system, such as an internal business network. This concept predates the modern cookie we use today.
HTTP cookies are a repurposed version of the magic cookie built for internet browsing and managing online experiences. HTTP cookies help web developers give you more personalized, convenient website experiences. They allow sites to remember you, your website logins, and shopping carts so you can pick back up where you left off from your last visit. However, cybercriminals can manipulate HTTP cookies to spy on your online activity and steal your personal information.
Cookie hijacking (also known as session hijacking) is typically initiated when a cybercriminal sends you a fake login page. If you click the fake link, the thief can steal the cookie and capture anything you type while on the fraudulent website. Like a phishing attack, cookie hijacking allows a cybercriminal to steal personal information like usernames, passwords, and other important data held within the cookie. If you enter your information while on the fake website, the criminal can then put that cookie in their browser and impersonate you online. They may even change your credentials, locking you out of your account.
Sometimes, criminals initiate cookie hijacking attacks without a fake link. If you’re browsing on an unsecured, public Wi-Fi connection, hackers can easily steal your data that’s traveling through the connection. This can happen even if the site is secure and your username and password are encrypted.
Because the data in cookies doesn’t change, cookies themselves aren’t harmful. They can’t infect computers with viruses or malware. But if your cookies are hijacked as part of a cyberattack, a criminal could gain access to your browsing history and use cookies as the key to enter your locked accounts. For example, a hacker may steal your identity or confidential company information, purchase items in your online shopping carts, or loot your bank account.
Preventing cookie hijacking attacks can allow you to browse the internet with greater peace of mind. Follow these tips to not only safeguard your personal information but to also enhance your browsing experience:
Make it a habit to clear your cookie cache regularly to prevent cookie overload, which could slow your search speeds. Also, almost every browser has the option to enable/disable cookies on your computer. So if you don’t want them at all, your browser’s support section can walk you through how to disable them.
Although it’s convenient to not have to re-type your credentials into a website you frequently visit, autofill features could make it easier for a criminal to extract your data with cookie hijacking. Plus, autofill is risky if your physical device falls into the wrong hands. To browse more securely without having to constantly reenter your passwords, use a password manager like McAfee True Key. True Key makes it so you only have to remember one master password, and it encrypts the rest in a vault protected by one of the most secure encryption algorithms available.
Strong, unique passwords for each of your accounts, updated regularly, offer ample protection against hackers. Multi-factor authentication (MFA) adds yet another layer of security by double-checking your identity beyond your username and password, usually with a texted or emailed code. When your accounts offer MFA, always opt in.
Criminals can hijack your cookies if you’re browsing on an unsecured, public Wi-Fi connection. To prevent a criminal from swiping your data, use a virtual private network (VPN), a service that protects your data and privacy online. A VPN creates an encrypted tunnel that makes you anonymous by masking your IP address while connecting to public Wi-Fi hotspots. This is a great way to shield your information from online spies while you’re banking, shopping, or handling any kind of sensitive information online.
McAfee LiveSafe is an antivirus solution that protects your computer and mobile devices from suspicious web cookies by:
is an antivirus solution that protects your computer and mobile devices from suspicious web cookies by:
The post What Are Browser Cookies and How Do I Manage Them? appeared first on McAfee Blog.

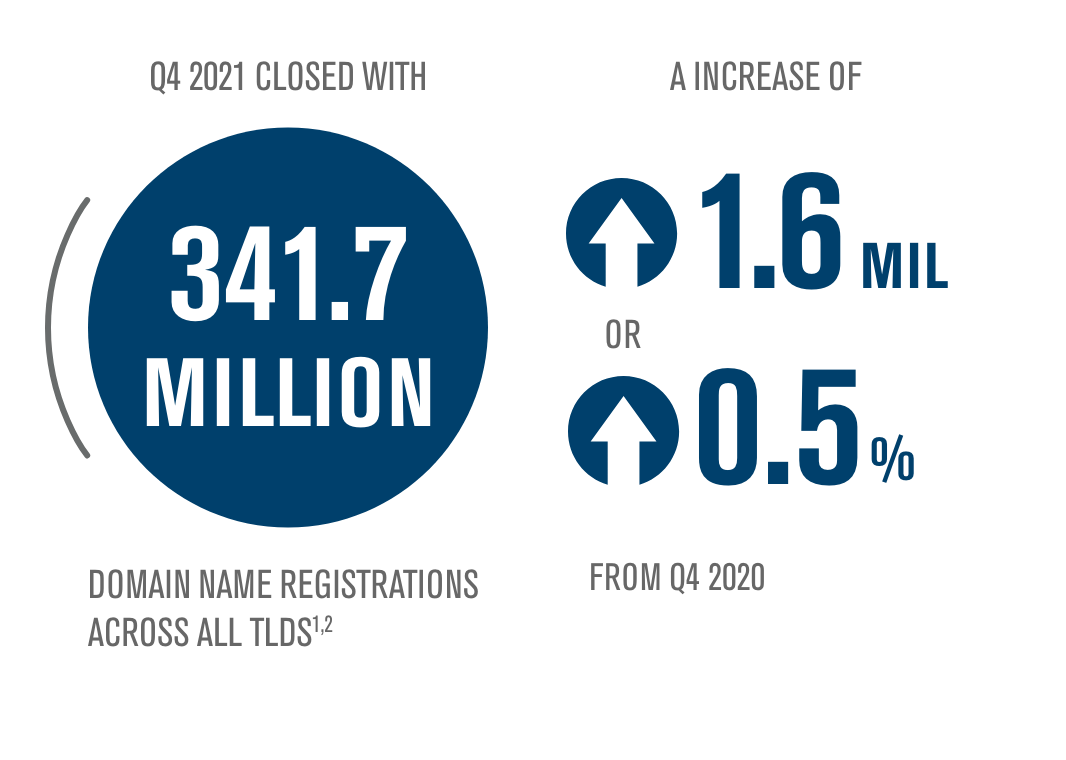
Today, we released the latest issue of The Domain Name Industry Brief, which shows that the fourth quarter of 2021 closed with 341.7 million domain name registrations across all top-level domains, an increase of 3.3 million domain name registrations, or 1.0%, compared to the third quarter of 2021.1,2 Domain name registrations have increased by 1.6 million, or 0.5%, year over year.1,2
Check out the latest issue of The Domain Name Industry Brief to see domain name stats from the fourth quarter of 2021, including:
• Top 10 Largest TLDs by Number of Reported Domain Names
• Top 10 Largest ccTLDs by Number of Reported Domain Names
• ngTLDs as Percentage of Total TLDs
• Geographical ngTLDs as Percentage of Total Corresponding Geographical TLDs
To see past issues of The Domain Name Industry Brief, please visit verisign.com/dnibarchives.
The post Verisign Q4 2021 The Domain Name Industry Brief: 341.7 Million Domain Name Registrations in the Fourth Quarter of 2021 appeared first on Verisign Blog.

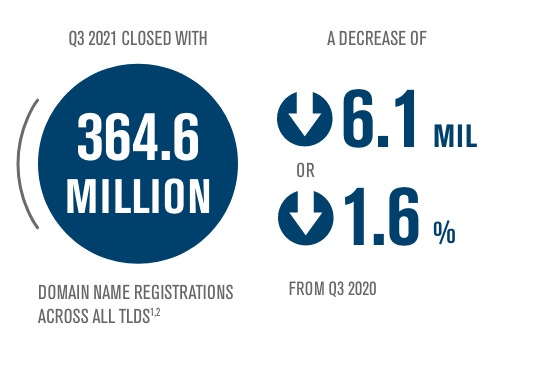
Today, we released the latest issue of The Domain Name Industry Brief, which shows that the third quarter of 2021 closed with 364.6 million domain name registrations across all top-level domains, a decrease of 2.7 million domain name registrations, or 0.7%, compared to the second quarter of 2021.1,2 Domain name registrations have decreased by 6.1 million, or 1.6%, year over year.1,2
Check out the latest issue of The Domain Name Industry Brief to see domain name stats from the third quarter of 2021, including:
The Domain Name Industry Brief this quarter also includes an overview of the ongoing community work to mitigate DNS security threats.
To see past issues of The Domain Name Industry Brief, please visit verisign.com/dnibarchives.
The post Verisign Q3 2021 The Domain Name Industry Brief: 364.6 Million Domain Name Registrations in the Third Quarter of 2021 appeared first on Verisign Blog.


















Spyware is tricky. Some types notify users that they’re monitoring activity. Others function in stealth mode and use the information they collect for nefarious purposes. Spyware is a type of software that collects data about online users and reports it to a company or an individual. What just about everyone can agree on is that anonymous browsing is looking more and more appealing and is likely the way of the future.
Here’s more about the types of spyware, which types are legal, and how you can scrub your device and live more confidently online.
Here are a few types of spyware and facts about each:
Is it legal? Definitely not!
What is its purpose? Criminal
Keyloggers are the most intrusive of the spyware variations. It does exactly as its name suggests: It takes note of keyboard strokes, logs them, and reports to the owner of the nefarious software. Once the cybercriminal has digitally looked over your shoulder at your online activity, they make note of your passwords, walk into your online accounts, and pilfer your private personal information. They could use this information to gain entry to your online bank accounts or steal your identity.
Keyloggers are downloaded onto devices (cellphones, tablets, laptops, or desktop computers) without the user’s knowledge. Cybercriminals can hide them within email attachments or in malicious web pages. So, the best way to steer clear of keyloggers is to never download attachments you’re unsure about and don’t visit sites that seem unprofessional. One rule of thumb is to mostly stick to URLs that begin with https and include a lock icon. These sites are almost always secure.
To determine if your device is infected with a keylogger, check your system’s performance. Is your device running slowly? See if there are any spikes in activity or unknown programs running in the background. This could indicate that your device is hosting a malicious program.
Is it legal? Sometimes
What is its purpose? Advertising and criminal
Adware is categorized as a type of spyware. It tracks users’ online activity and spits out targeted pop-up advertisements. If you have the pop-up blocker enabled on your browser, you’ll likely be spared from the annoyance. Additionally, pop-ups can slow your device, so that’s another reason to turn on the pop-up blocking feature. Legitimate adware often asks users to opt into targeted ads.
Adware turns malicious (and illegal) when it contains malware. Sometimes cyber criminals hide malware within pop-ups. It’s easy to accidentally hit a link within a pop-up when you’re aiming quickly for the X to close it.
It’s easy to spot a device with an adware infestation. First, the number of pop-ups will be out of control. Also, the device will crash often, run very slowly, and have a short battery life. An antivirus program will likely be able to identify and remove the culprit. You can also check out your system monitor and end tasks that are draining your device’s power.
Is it legal? Yes
What is its purpose? Advertising
Cookies are delicious, especially to advertisers who use them to better target ads and make profits selling collected user data to third-party companies. Cookies are sometimes categorized as spyware, because they log the websites you visit and report them. You may notice the banners on websites that ask you to accept cookies.
Many users today are uneasy with sharing their online activity with strangers and advertisers. Sometimes the ads that pop up on your social media feed or in sidebars seem a little too targeted and it feels like someone is listening in to your conversations and attempting to make a profit from them.
How to Browse Free of Spyware
To scrub cybercriminals from your devices and confuse advertisers, consider the following steps you can easily add to your daily routine:
The post How to Live a Digital Life Free of Spyware appeared first on McAfee Blog.












There’s little rest for your hard-working smartphone. If you’re like many professionals today, you use it for work, play, and a mix of personal business in between. Now, what if something went wrong with that phone, like loss or theft? Worse yet, what if your smartphone got hacked? Let’s try and keep that from happening to you.
Globally, plenty of people pull double duty with their smartphones. In Spain, one survey found that 55% of people use the same phone for a mix of personal and and work activity. The same survey showed that up to half of people interviewed in Japan, Australia, and the U.S. do so as well, while nations like the UK and Germany trailed at 31% and 23% respectively.
Whether these figures trend on the low or high end, the security implications remain constant. A smartphone loaded with business and personal data makes for a desirable target. Hackers target smartphones because they’re often unprotected, which gives hackers an easy “in” to your personal information and to any corporate networks you may use. It’s like two hacks with one stone.
Put simply, as a working professional with a smartphone, you’re a high-value target.
As both a parent and a professional, I put together a few things you can do to protect your smartphone from hacks so that you can keep your personal and work life safe:
First up, the basics. Locking your phone with facial ID, a fingerprint, pattern or a pin is your most basic form of protection, particularly in the event of loss or theft. (Your options will vary depending on the device, operating system, and manufacturer.) Take it a step further for even more protection. Secure the accounts on your phone with strong passwords and use two-factor authentication on the apps that offer it, which doubles your line of defense.
Or, put another way, don’t hop onto public Wi-Fi networks without protection. A VPN masks your connection from hackers allowing you to connect privately when you are on unsecure public networks at airports, cafes, hotels, and the like. With a VPN connection, you’ll know that your sensitive data, documents, and activities you do are protected from snooping, which is definitely a great feeling given the amount of personal and professional business we manage with our smartphones.
Both Google Play and Apple’s App Store have measures in place to help prevent potentially dangerous apps from making it into their stores. Malicious apps are often found outside of the app stores, which can run in the background and compromise your personal data like passwords, credit card numbers, and more—practically everything that you keep on your phone. Further, when you are in the app stores, look closely at the descriptions and reviews for apps before you download them. Malicious apps and counterfeits can still find their way into stores, and here are a few ways you can keep those bad apps from getting onto your phone.
Backing up your phone is always a good idea for two reasons:
Both iPhones and Android phones have straightforward ways of backing up your phone regularly.
Worst case scenario—your phone is gone. Really gone. Either it’s hopelessly lost or got stolen. What now? Lock it remotely or even wipe its data entirely. While that last bit about wiping the phone seems like a drastic move, if you maintain regular backups as mentioned above, your data is secure in the cloud—ready for you to restore. In all, this means that hackers won’t be able to access you, or your company’s, sensitive information—which can keep you out of trouble and your professional business safe. Apple provides iOS users with a step-by-step guide for remotely wiping devices, and Google offers up a guide for Android users as well.
We all download apps, use them once, and then forget they are on our phone. Take a few moments to swipe through your screen and see which ones you’re truly done with and delete them along with their data. Some apps have an account associated with them that may store data off your phone as well. Take the extra step and delete those accounts so any off-phone data is deleted.
The reason for this is that every extra app is another app that needs updating or that may have a security issue associated with it. In a time of data breaches and vulnerabilities, deleting old apps is a smart move. As for the ones you keep, update them regularly and turn on auto-updates if that’s an option. Updates not only introduce new features to apps, but they also often address security issues too.
With so much of your life on your phone, getting security software installed on it can protect you and the things you keep on your phone. Whether you’re an Android owner or iOS owner, mobile security software can keep your data, your shopping, and payments secure.
The post 7 Tips to Protect Your Smartphone from Getting Hacked appeared first on McAfee Blog.

Spooky season is among us, and ghosts and goblins aren’t the only things hiding in the shadows. Online threats are also lurking in the darkness, preparing to haunt devices and cause some hocus pocus for unsuspecting users. This Halloween season, researchers have found virtual zombies and witches among us – a new trojan that rises from the dead no matter how many times it’s deleted and malicious code that casts an evil spell to steal users’ credit card data.
Let’s unlock the mystery of these threats so you can avoid cyber-scares and continue to live your online life free from worry.
Just like zombies, malware can be a challenge to destroy. Oftentimes, it requires a user to completely wipe their device by backing up files, reinstalling the operating system, and starting from scratch. But what if this isn’t enough to stop the digital walking dead from wreaking havoc on your device?
Recently, a new type of Trojan has risen from the dead to haunt users no matter how many times it’s deleted. This zombie-like malware attaches itself to a user’s Windows 10 startup system, making it immune to system wipes since the malware can’t be found on the device’s hard drive. This stealthy malware hides on the device’s motherboard and creates a Trojan file that reinstalls the malware if the user tries to remove it. Once it sets itself up in the darkness, the malware scans for users’ private documents and sends them to an unknown host, leaving the user’s device in a ghoulish state.
A malware misfortune isn’t the only thing that users should beware of this Halloween. Cybercriminals have also managed to inject malicious code into a wireless provider’s web platform, casting an evil spell to steal users’ credit card data. The witches and warlocks allegedly responsible for casting this evil spell are part of a Magecart spin-off group that’s known for its phishing prowess. To pull off this attack, they plated a credit card skimmer onto the wireless provider’s checkout page. This allowed the hackers to exfiltrate users’ credit card data whenever they made a purchase – a spell that’s difficult to break.
While these threats might seem like just another Halloween trick, there are other forces at play. According to McAfee’s Quarterly Threats Report from July 2020, threats like malware phishing and trojans have proven opportunistic for cybercriminals as users spend more and more time online – whether it be working from home, distance learning, or connecting with friends and loved ones. In fact, McAfee Labs observed 375 threats per minute in Q1 2020 alone.
So, as hackers continue to adapt their techniques to take advantage of users spending more time online, it’s important that people educate themselves on emerging threats so they can take necessary precautions and live their digital lives free from worry.
Fortunately, there are a number of steps you can take to prevent these threats from haunting your digital life. Follow these tips to keep cybersecurity tricks at bay this spooky season:
Zombie malware is easily spread by phishing, which is when scammers try to trick you out of your private information or money. If you receive an email from an unknown user, it’s best to proceed with caution. Don’t click on any links or open any attachments in the email and delete the message altogether.
Look over your credit card accounts and bank statements often to check whether someone is fraudulently using your financial data – you can even sign up for transaction alerts that your bank or credit card company may provide. If you see any charges that you did not make, report it to the authorities immediately.
Add an extra layer of protection with a security solution like McAfee® Total Protection to help safeguard your digital life from malware and other threats. McAfee Total Protection also includes McAfee® WebAdvisor – web protection that enables users to sidestep attacks before they happen with clear warnings of risky websites, links, and files.
To stay updated on all things McAfee and on top of the latest consumer and mobile security threats, follow @McAfee_Home on Twitter, listen to our podcast Hackable?, and ‘Like’ us on Facebook.
The post Trick or Treat: Avoid These Spooky Threats This Halloween appeared first on McAfee Blogs.

If you’re thinking career change or career shift, there’s a field that has an estimated 4 million jobs open. Cybersecurity.
According to survey and research data from the International Cybersecurity Organization (ICS)2, there’s a cybersecurity workforce gap—a terrifically high volume of jobs left unfilled. Published in 2019, the gap they identified looked like this:
Needless to say, there’s opportunity in the field for both technical and non-technical roles.
Here’s an important thing to keep in mind about cybersecurity:, it’s not solely about understanding technology. It’s about understanding people too and how people and technology interact.
The moment you see cybersecurity through that broader lens, you can see how the field opens widely to encompass a range of roles. Of course, there are analysts and engineers, yet it also includes other roles like digital forensics and cyber investigation, healthcare information security, cryptography, and even cyber law. Additionally, there’s needed expertise in the realms of privacy, governance, ethics, and even digital ethics. And if you take a role with a security company such as ours, the opportunity further extends to positions in account management, marketing, and operations. (In fact, you can drop by our careers page for a look at our current openings and what workday life is like around here.)
There are plenty of reasons. Above that data published in 2019, our unprecedented reliance on the internet to work, learn, and stay connected in 2020, demand for cybersecurity jobs is yet more so on the rise. As so many of us turned increasingly to the internet to get through our day, the same is true for hackers and crooks.
With that, let’s take a quick look at several of the factors working in your favor as you consider a change.
We’ve all seen the news stories of major breaches at big retailers, credit reporting agencies, hotels, and even healthcare providers. It’s not just the private sector that’s been grappling with cybersecurity concerns, there’s need in the public sector as well—like municipalities. In all, every organization needs cybersecurity (just as we all need cybersecurity for our homes), and thus there’s plenty of opportunity out there. Using just one of the many possible cybersecurity roles as an example, the U.S. Bureau of Labor Statistics predicts a 32% increase in demand for information security analysts through 2028—which is far higher than the average of other professions.
In fact, the same (ICS)2 survey discovered that only 42% of current cybersecurity pros said that their first job after higher education was in the field of cybersecurity. In other words, the majority of cybersecurity pros ended up that way by some means of career shift or change. And they got there through certifications and training rather than by way of a degree from a college or university.
Our own Chief Human Resources Officer, Chatelle Lynch, put it quite well in an interview with Business Insider just a few weeks ago: “It’s no secret that the demand for cybersecurity staff has steadily grown over the past decade,” she says. “This means opportunity, so if you don’t have a degree, don’t let that slow you down. You may have unique work experience or relevant certifications, alternative learning, or transferable skills that you need to make sure you highlight when applying and interviewing.”
For example, she goes on to say that prior military service, IT experience, and volunteer or hobbyist activities (even online gaming) are a good foundation for cybersecurity roles.
These skills absolutely apply, and they’re sought after skills as well. The ability to work independently, lead projects, write and document well, and particularly strong people skills are vital for a role where you’ll be interfacing with numerous individuals, departments, and business units. Likewise, as called out above, certain roles focus more on the non-technical side of security solutions.
The beauty of making a career change to cybersecurity is that there are plenty of ways you can get it done at home and on your time.
If you’re just getting started, you can test the waters for free or at relatively low cost with a Massively Open Online Course (MOOC) that gives you the basics on cybersecurity. Future Learn’s “Introduction to Cybersecurity” from The Open University is one example of an intro program, as is the University of Michigan’s “Securing Digital Democracy” class that’s offered through Coursera.
If you’re already an IT pro or have a strong technical background, there are similar MOOC courses available that cater to your current level of knowledge and skill. The University of Maryland’s “Cybersecurity Specialization” and “Usable Security” are geared accordingly.
For a list of cybersecurity programs available online, drop by CyberDegrees.org. Their listing is one of many good places to start.
Other free and low-cost avenues out there include subscribing to some security bloggers, grabbing some hands-on work with coding and IT networking fundamentals from online learning companies like Udemy, Codecademy, and Khan Academy, or joining some online cybersecurity groups for a little professional networking. In all, there’s plenty of opportunity to learn from others, both in structured class settings and in more unstructured peer and mentorship relationships.
When you’re ready to start your job search, there’s a good chance that your interview will be conducted online. Online interviews have been part of the job-hunting landscape for a few years now, yet with many employers enacting work from home measures, it’s the way hiring gets done right now. I expect this to continue, as employers have embraced its many benefits, particularly in the early stages of interviews. If the prospect of an online interview is new to you, I put together a pair of articles this spring that can help.
As you make the jump, here’s the most important thing you’ll need: a love of technology and a desire to protect the people who use it. If you can combine a drive to understand both technology and people better with the further drive to see it all through, you’ll be well on your way. Like any career shift or change, there’s work ahead, yet it’s my impression that our field is a welcoming and supportive one—and very much on a keen lookout for new talent.
To stay updated on all things McAfee and for more resources on staying secure from home, follow @McAfee_Home on Twitter, listen to our podcast Hackable?, and ‘Like’ us on Facebook.
The post Career change? Cybersecurity companies are hiring. appeared first on McAfee Blogs.
Introduction Browsers have become an inherent part of our virtual life and we all make use of browsers for surfing the internet in some or the other way. Also, browsers can be used not only for surfing, we can make use of browsers for navigating through the file system of the OS. You might have […]
The post Browser Forensics: IE 11 appeared first on Infosec Resources.
Introduction In the previous article, we understood how print functions like printf work. This article provides further definition of Format String vulnerabilities. We will begin by discussing how Format Strings can be used in an unusual way, which is a starting point to understanding Format String exploits. Next, we will understand what kind of mistakes […]
The post Format String Vulnerabilities: Use and Definitions appeared first on Infosec Resources.
Introduction In the previous articles, we discussed printing functions, format strings and format string vulnerabilities. This article provides an overview of how Format String vulnerabilities can be exploited. In this article, we will begin by solving a simple challenge to leak a secret from memory. In the next article, we will discuss another example, where […]
The post How to exploit Format String Vulnerabilities appeared first on Infosec Resources.
Introduction: This article provides an overview of various techniques that can be used to mitigate Format String vulnerabilities. In addition to the mitigations that are offered by the compilers & operating systems, we will also discuss preventive measures that can be used while writing programs in languages susceptible to Format String vulnerabilities. Techniques to prevent […]
The post How to mitigate Format String Vulnerabilities appeared first on Infosec Resources.

In July 2015, I did my first threat webinar. I had planned to do it on a monthly basis, and never imagined I would still be doing it five years later, but here I am, still creating monthly webinars. I still do. I started the webinar series to help people understand the different threats targeting our customers and I have always tried to focus on three areas:
|
|
This last point, discussing technologies versus solutions, has been one of the key items I try to follow as much as possible – after all, the goal of my webinars is to be educational, not a sales pitch.
Coming from a technical background, BS in Electrical Engineering from Michigan State University (Go Spartans!!), I enjoy learning about the new technologies being used to detect the latest threats and to ensure you know what to look for when selecting a vendor and/or a security solution. Over the years, I’ve discussed everything from APTs, coinminers, exploits, messaging threats, ransomware, underground activity and lots in between. It is pretty easy to find topics to discuss, as there is so much going on in our industry, and with the malicious actors regularly shifting their tactics, techniques and procedures, I can keep the content fairly fresh.
I really enjoy having guest speakers on my webinars to mix things up a bit for the viewers as well, as I know my limitations – there are just too many threats out there to keep up with all of them. The main reason I love doing the threat webinars is that I enjoy sharing information and teaching others about our industry and the threats affecting them. If you want to check out any of my previous five years of webinars you can watch them here.
For my fifth year anniversary I wanted to try something different and I would like to do an open Q&A session. As I’ve never done this before, it will certainly be an interesting experience for me, but hopefully for you as well. I hope I can answer a majority of your questions, but I know some of you are way too smart for me, so please bear with me.
Our registration page for this webinar allows you to submit any pre-session questions that I’ll answer throughout the webinar. You can ask me anything that is on your mind and if I cannot get to your question, I’ll do my best to answer you afterwards in an email.
I hope to continue to do these webinars for the foreseeable future and I would like to end my post by thanking each and every one of you who has participated in my webinars over the years. It has been a pleasure, and I look forward to answering your questions.
Take care, stay healthy, and keep on smiling!
Jon
The post Ask Me Anything – Celebrating The Fifth Anniversary Of My Monthly Threat Webinar appeared first on .

Risk decisions are the foundation of information security. Sadly, they are also one of the most often misunderstood parts of information security.
This is bad enough on its own but can sink any effort at education as an organization moves towards a DevOps philosophy.
To properly evaluate the risk of an event, two components are required:
Unfortunately, teams—and humans in general—are reasonably good at the first part and unreasonably bad at the second.
This is a problem.
It’s a problem that is amplified when security starts to integration with teams in a DevOps environment. Originally presented as part of AllTheTalks.online, this talk examines the ins and outs of risk decisions and how we can start to work on improving how our teams handle them.
The post Risk Decisions in an Imperfect World appeared first on .
 So much for a quiet January! By now you must have heard about the new Microsoft® vulnerability CVE-2020-0601, first disclosed by the NSA (making it the first Windows bug publicly attributed to the National Security Agency). This vulnerability is found in a cryptographic component that has a range of functions—an important one being the ability to digitally sign software, which certifies that the software has not been tampered with. Using this vulnerability, attackers can sign malicious executables to make them look legitimate, leading to potentially disastrous man-in-the-middle attacks.
So much for a quiet January! By now you must have heard about the new Microsoft® vulnerability CVE-2020-0601, first disclosed by the NSA (making it the first Windows bug publicly attributed to the National Security Agency). This vulnerability is found in a cryptographic component that has a range of functions—an important one being the ability to digitally sign software, which certifies that the software has not been tampered with. Using this vulnerability, attackers can sign malicious executables to make them look legitimate, leading to potentially disastrous man-in-the-middle attacks.
Here’s the good news. Microsoft has already released a patch to protect against any exploits stemming from this vulnerability. But here’s the catch: You have to patch!
While Trend Micro offers industry-leading virtual patching capabilities via our endpoint, cloud, and network security solutions, the best protection against vulnerabilities is to deploy a real patch from the software vendor. Let me say it again for effect – the best protection against this very serious vulnerability is to ensure the affected systems are patched with Microsoft’s latest security update.
We understand how difficult it can be to patch systems in a timely manner, so we created a valuable tool that will test your endpoints to see if whether they have been patched against this latest threat or if they are still vulnerable. Additionally, to ensure you are protected against any potential threats, we have just released additional layers of protection in the form of IPS rules for Trend Micro Deep Security and Trend Micro Vulnerability Protection
and Trend Micro Vulnerability Protection (including Trend Micro Apex One
(including Trend Micro Apex One ). This was rolled out to help organizations strengthen their overall security posture and provide some protection during lengthy patching processes.
). This was rolled out to help organizations strengthen their overall security posture and provide some protection during lengthy patching processes.
You can download our Trend Micro Vulnerability Assessment Tool right now to see if you are protected against the latest Microsoft vulnerability. And while you’re at it, check out our latest Knowledge Based Article for additional information on this new vulnerability along with Trend Micro security capabilities that help protect customers like you 24/7. Even during those quiet days in January.
The post Don’t Let the Vulnera-Bullies Win. Use our free tool to see if you are patched against Vulnerability CVE-2020-0601 appeared first on .