Dark Reading:
Dark Reading:
By Robert Lemos, Contributing Writer, Dark Reading — July 18th 2022 at 16:00
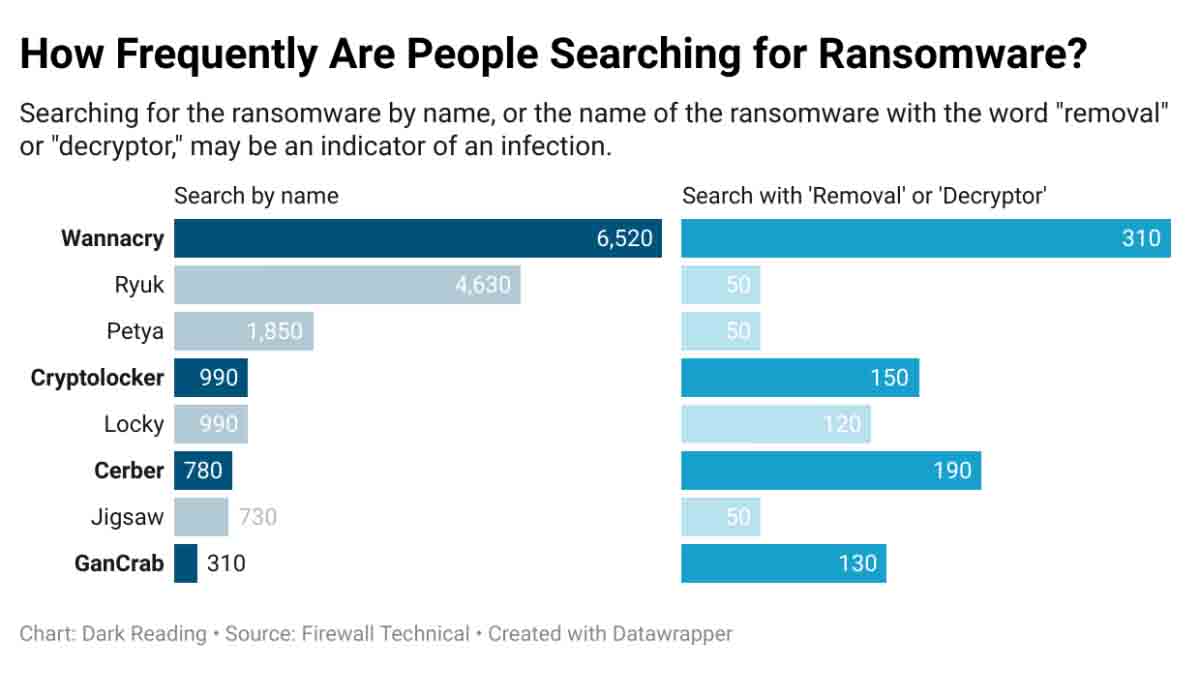
Telecom and business services see the highest level of attacks, but the two most common ransomware families, which continue to be LockBit and Conti, are seen less often.