

 Dark Reading:
Dark Reading:
By Vernon Keenan, Senior Industry Analyst, SalesforceDevops.net — February 8th 2022 at 15:00
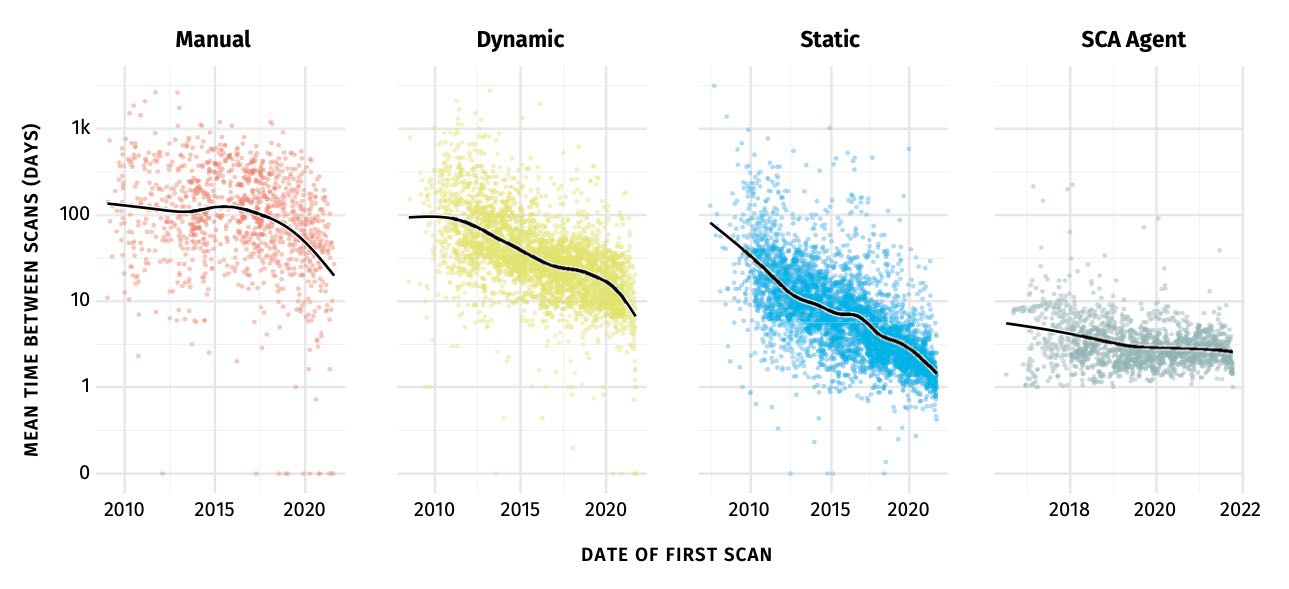
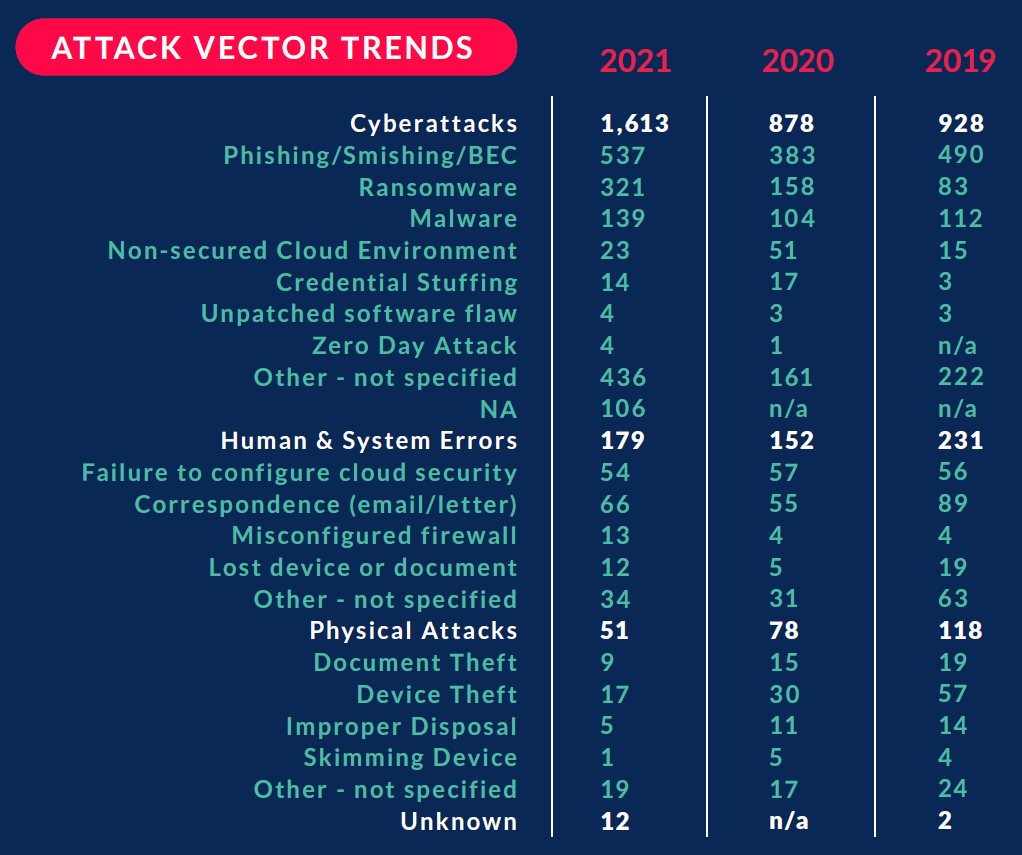
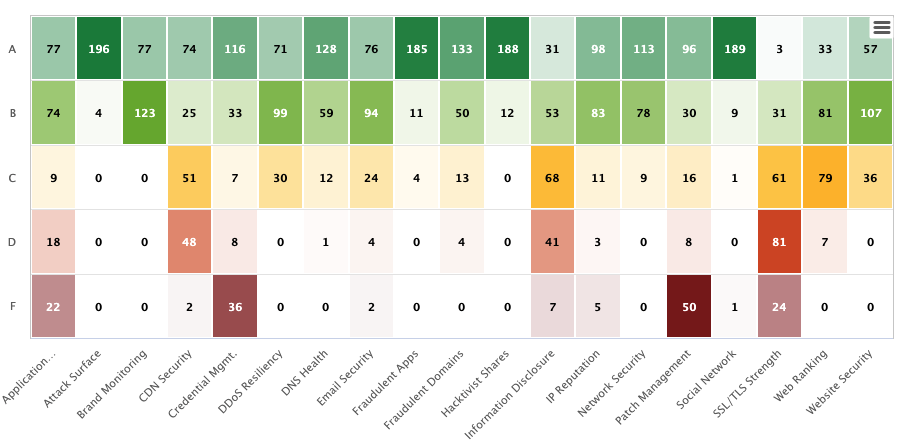
Some companies go too fast when it comes to SaaS, DevOps, and security, but smart developers and implementers will respect some basic guidelines to keep their product safe.


















































2_2020.jpg)








