Short'Em All is a URL scanning tool trusted by CTI Analysts and Security Researchers. It's designed to scan short URLs and provide insights into potential security risks or useful information. This tool automates the process of scanning URLs, allowing users to focus on analyzing the results.
Home Depot has confirmed that a third-party company accidentally exposed some of its employees' personal details after a criminal copy-pasted the data online.…
First, they came for hospitals, then it was charities and cancer centers. Now, cyber scumbags are coming for the puppies and kittens.…
Change Healthcare is allegedly being extorted by a second ransomware gang, mere weeks after recovering from an ALPHV attack.…
Infosec in brief Protecting your privacy online is hard. So hard, in fact, that even a top Israeli spy who managed to stay incognito for 20 years has found himself exposed after one basic error.…

I suggest, based on my experiences with data breaches over the years, that AT&T is about to have a very bad time of it. Class actions following data breaches have become all too common and I've written before about how much I despise them. The trouble for AT&T (in my non-legal but "hey, I'm the data breach guy" opinion), will be their denial of a breach in 2021 and the subsequent years in which tens of millions of social security numbers were floating around. As much as it's hard for the victim of identity theft to say "this happened because of that breach", it's also hard for the corporate victim of a breach to say that identity theft didn't happen because of their breach. Particularly in such a litigious part of the world, I wouldn't be at all surprised if the legal cost of this runs into the tens if not hundreds of millions of dollars. I doubt the plaintiffs will see much of this, but there's sure going to be some happy lawyers out there!

Kettle It's been about a week since the shock discovery of a hidden and truly sophisticated backdoor in the xz software library that ordinarily is used by countless systems.…
I tried to gather all the related Web Cache vulnerabilities techniques into one blog post.
Analysis You might think that when a government supplier fails in one of its key duties it would find itself shunned or at least feel financial pain.…
A self-service check-in terminal used in a German Ibis budget hotel was found leaking hotel room keycodes, and the researcher behind the discovery claims the issue could potentially affect hotels around Europe.…
My latest blog post
A study has concluded that Apple's privacy practices aren't particularly effective, because default apps on the iPhone and Mac have limited privacy settings and confusing configuration options.…
If ever there was an incident that brings the need for good infosec into sharp focus, this is the one: Japan's Hoya – a maker of eyeglass and contact lenses, plus kit used to make semiconductor manufacturing, flat panel displays, and hard disk drives – has halted some production and sales activity after experiencing an attack on its IT systems.…
Updated Uncle Sam is investigating claims that some miscreant stole and leaked classified information from the Pentagon and other national security agencies.…
Ivanti has committed to adopting a secure-by-design approach to security as it gears up for an organizational overhaul in response to the multiple vulnerabilities in Connect Secure exploited earlier this year.…
A cybercrook who has been setting up websites that mimic the self-destructing message service privnote.com accidentally exposed the breadth of their operations recently when they threatened to sue a software company. The disclosure revealed a profitable network of phishing sites that behave and look like the real Privnote, except that any messages containing cryptocurrency addresses will be automatically altered to include a different payment address controlled by the scammers.
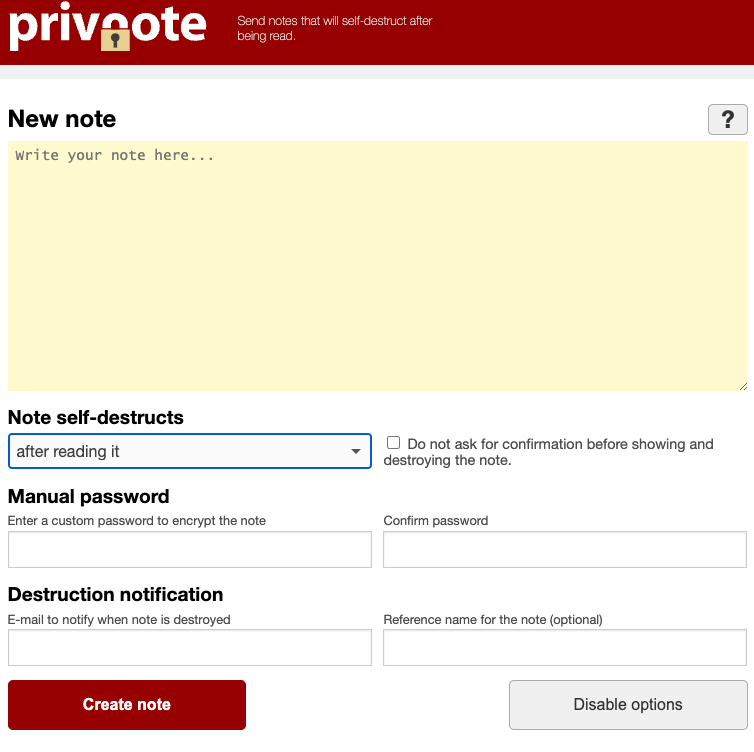
The real Privnote, at privnote.com.
Launched in 2008, privnote.com employs technology that encrypts each message so that even Privnote itself cannot read its contents. And it doesn’t send or receive messages. Creating a message merely generates a link. When that link is clicked or visited, the service warns that the message will be gone forever after it is read.
Privnote’s ease-of-use and popularity among cryptocurrency enthusiasts has made it a perennial target of phishers, who erect Privnote clones that function more or less as advertised but also quietly inject their own cryptocurrency payment addresses when a note is created that contains crypto wallets.
Last month, a new user on GitHub named fory66399 lodged a complaint on the “issues” page for MetaMask, a software cryptocurrency wallet used to interact with the Ethereum blockchain. Fory66399 insisted that their website — privnote[.]co — was being wrongly flagged by MetaMask’s “eth-phishing-detect” list as malicious.
“We filed a lawsuit with a lawyer for dishonestly adding a site to the block list, damaging reputation, as well as ignoring the moderation department and ignoring answers!” fory66399 threatened. “Provide evidence or I will demand compensation!”
MetaMask’s lead product manager Taylor Monahan replied by posting several screenshots of privnote[.]co showing the site did indeed swap out any cryptocurrency addresses.
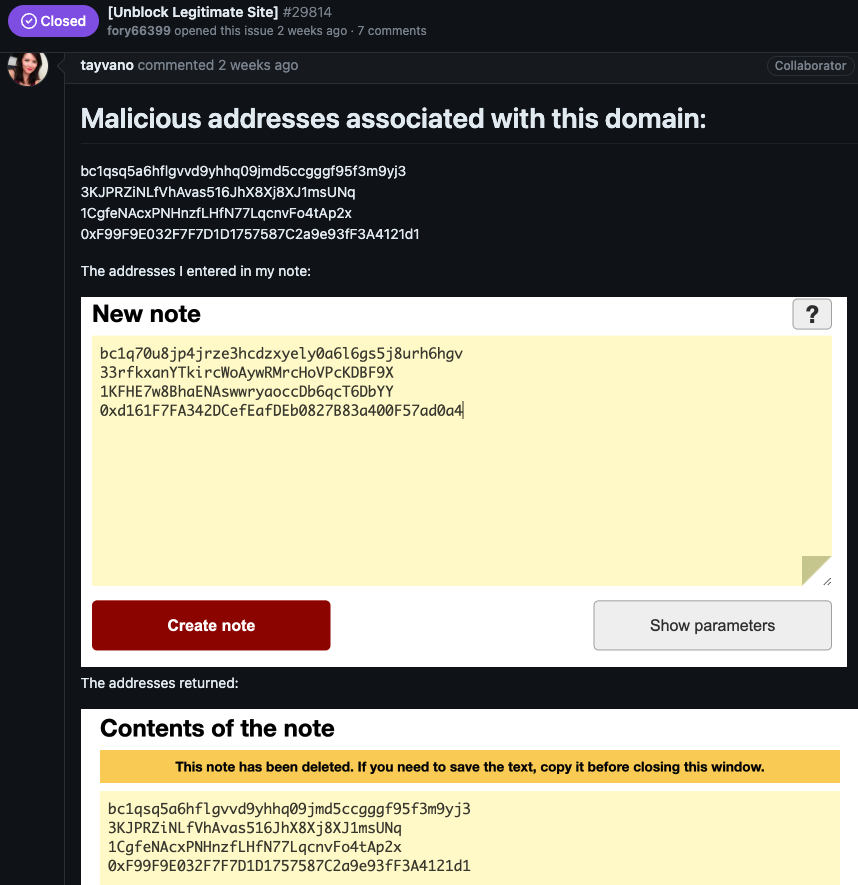
After being told where they could send a copy of their lawsuit, Fory66399 appeared to become flustered, and proceeded to mention a number of other interesting domain names:
You sent me screenshots from some other site! It’s red!!!!
The tornote.io website has a different color altogether
The privatenote,io website also has a different color! What’s wrong?????
A search at DomainTools.com for privatenote[.]io shows it has been registered to two names over as many years, including Andrey Sokol from Moscow and Alexandr Ermakov from Kiev. There is no indication these are the real names of the phishers, but the names are useful in pointing to other sites targeting Privnote since 2020.
DomainTools says other domains registered to Alexandr Ermakov include pirvnota[.]com, privatemessage[.]net, privatenote[.]io, and tornote[.]io.
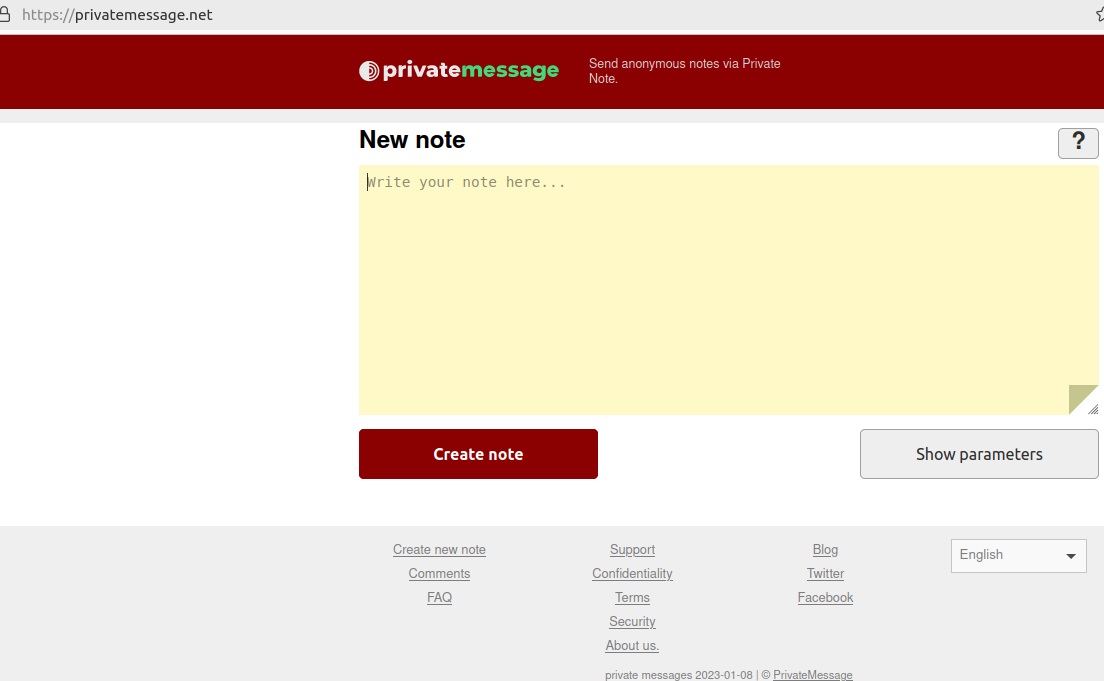
A screenshot of the phishing domain privatemessage dot net.
The registration records for pirvnota[.]com at one point were updated from Andrey Sokol to “BPW” as the registrant organization, and “Tambov district” in the registrant state/province field. Searching DomainTools for domains that include both of these terms reveals pirwnote[.]com.
Other Privnote phishing domains that also phoned home to the same Internet address as pirwnote[.]com include privnode[.]com, privnate[.]com, and prevnóte[.]com. Pirwnote[.]com is currently selling security cameras made by the Chinese manufacturer Hikvision, via an Internet address based in Hong Kong.
It appears someone has gone to great lengths to make tornote[.]io seem like a legitimate website. For example, this account at Medium has authored more than a dozen blog posts in the past year singing the praises of Tornote as a secure, self-destructing messaging service. However, testing shows tornote[.]io will also replace any cryptocurrency addresses in messages with their own payment address.
These malicious note sites attract visitors by gaming search engine results to make the phishing domains appear prominently in search results for “privnote.” A search in Google for “privnote” currently returns tornote[.]io as the fifth result. Like other phishing sites tied to this network, Tornote will use the same cryptocurrency addresses for roughly 5 days, and then rotate in new payment addresses.
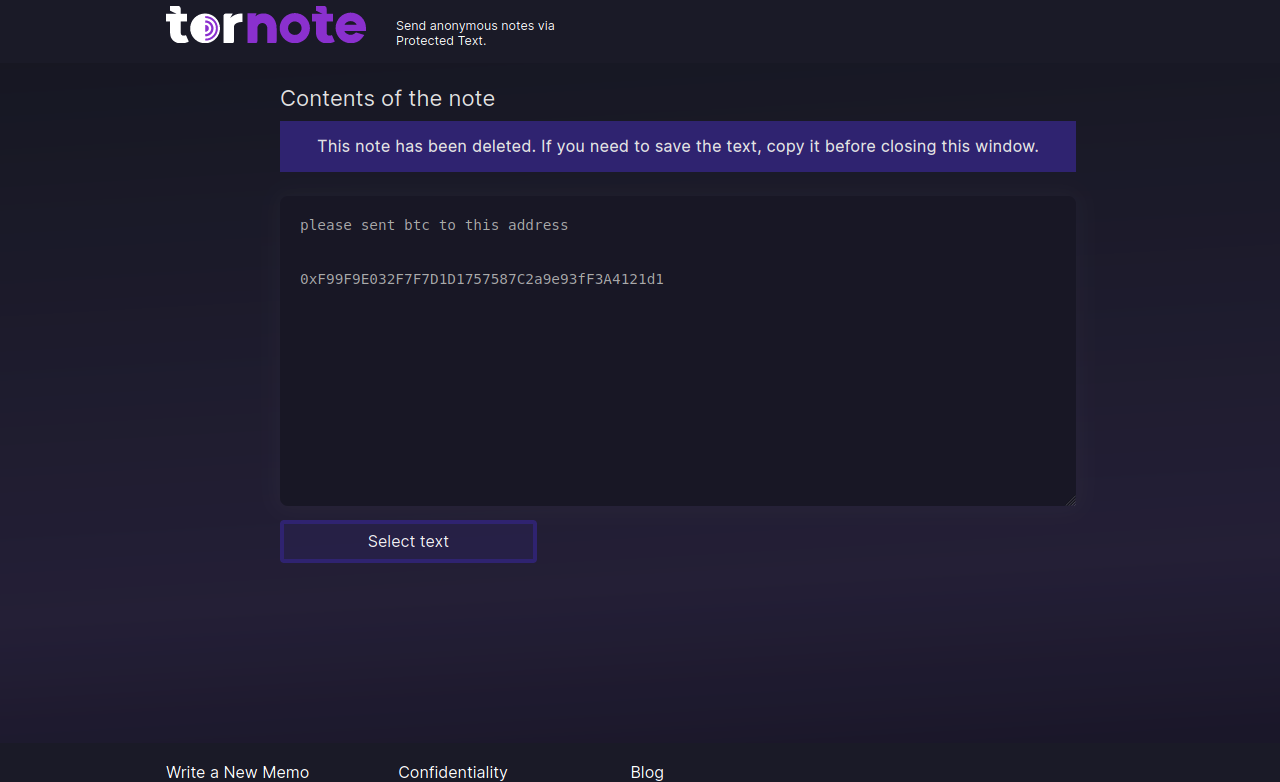
Tornote changed the cryptocurrency address entered into a test note to this address controlled by the phishers.
Throughout 2023, Tornote was hosted with the Russian provider DDoS-Guard, at the Internet address 186.2.163[.]216. A review of the passive DNS records tied to this address shows that apart from subdomains dedicated to tornote[.]io, the main other domain at this address was hkleaks[.]ml.
In August 2019, a slew of websites and social media channels dubbed “HKLEAKS” began doxing the identities and personal information of pro-democracy activists in Hong Kong. According to a report (PDF) from Citizen Lab, hkleaks[.]ml was the second domain that appeared as the perpetrators began to expand the list of those doxed.
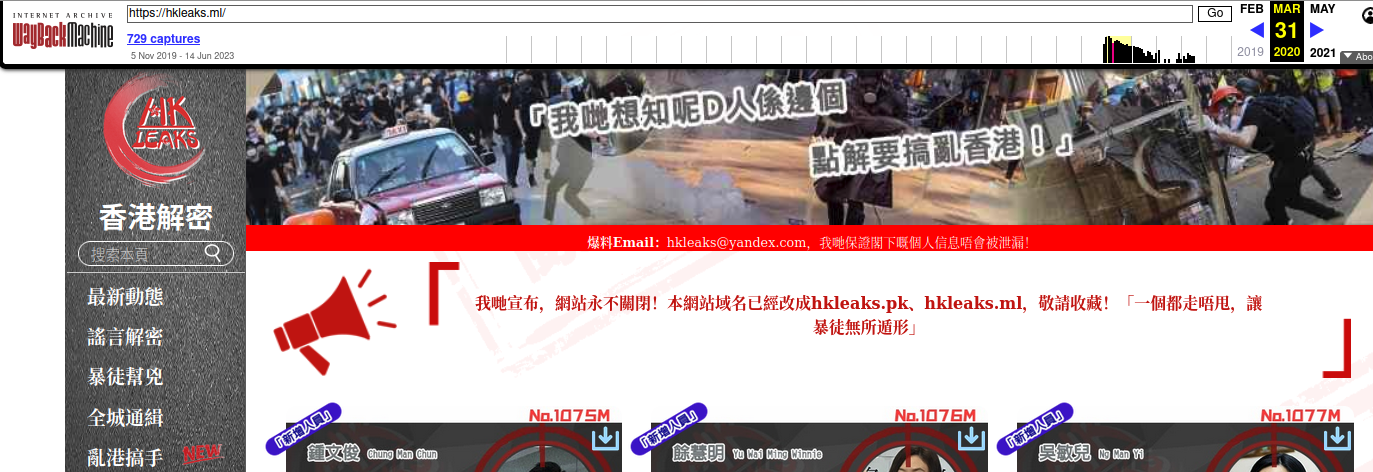
HKleaks, as indexed by The Wayback Machine.
DomainTools shows there are more than 1,000 other domains whose registration records include the organization name “BPW” and “Tambov District” as the location. Virtually all of those domains were registered through one of two registrars — Hong Kong-based Nicenic and Singapore-based WebCC — and almost all appear to be phishing or pill-spam related.
Among those is rustraitor[.]info, a website erected after Russia invaded Ukraine in early 2022 that doxed Russians perceived to have helped the Ukrainian cause.
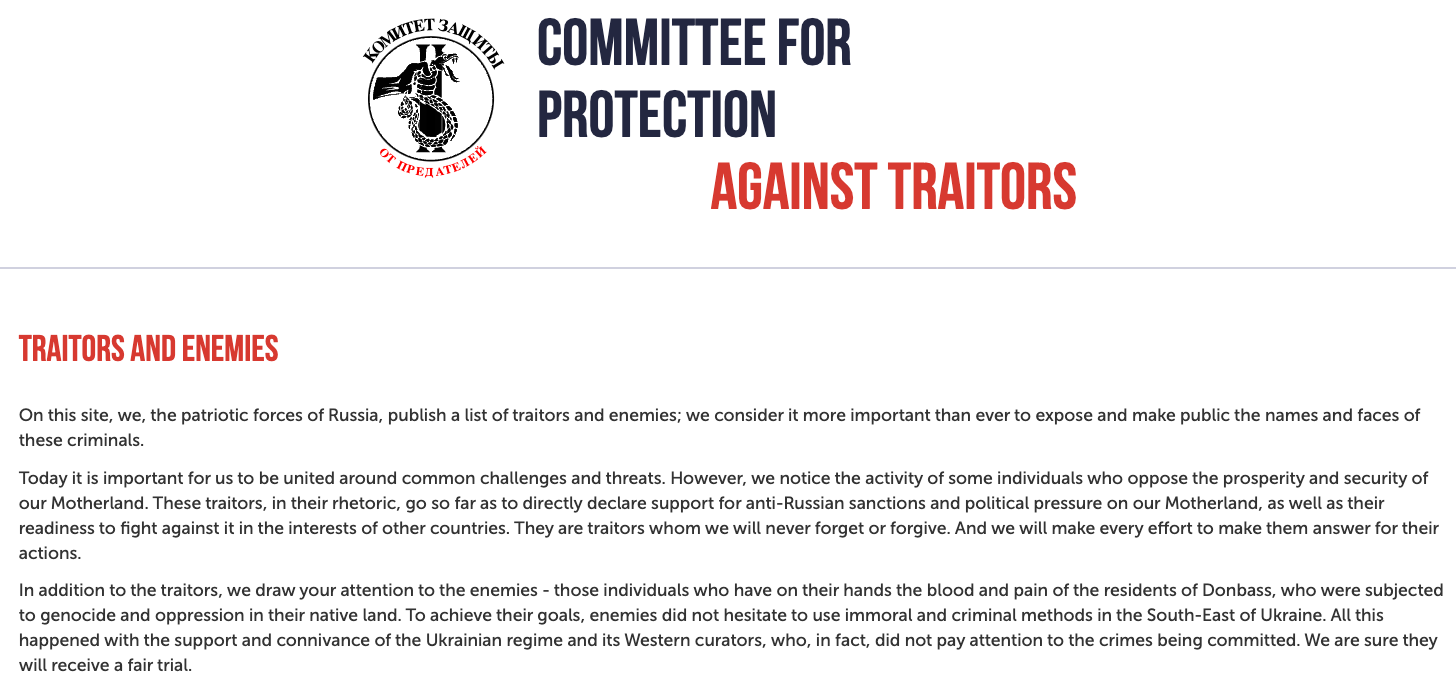
An archive.org copy of Rustraitor.
In keeping with the overall theme, these phishing domains appear focused on stealing usernames and passwords to some of the cybercrime underground’s busiest shops, including Brian’s Club. What do all the phished sites have in common? They all accept payment via virtual currencies.
It appears MetaMask’s Monahan made the correct decision in forcing these phishers to tip their hand: Among the websites at that DDoS-Guard address are multiple MetaMask phishing domains, including metarrnask[.]com, meternask[.]com, and rnetamask[.]com.
How profitable are these private note phishing sites? Reviewing the four malicious cryptocurrency payment addresses that the attackers swapped into notes passed through privnote[.]co (as pictured in Monahan’s screenshot above) shows that between March 15 and March 19, 2024, those address raked in and transferred out nearly $18,000 in cryptocurrencies. And that’s just one of their phishing websites.
Leicester City Council is finally admitting its "cyber incident" was carried out by a ransomware gang and that data was stolen, hours after the criminals forced its hand.…
Sponsored Post Artificial intelligence (AI) offers enormous commercial potential but also substantial risks to data security if it is harnessed by cyber criminals intent on stealing or corrupting sensitive information for their own gain.…