Updated The Akira ransomware gang is claiming responsiblity for the "cybersecurity incident" at British bath bomb merchant.…
A former Trickbot developer has been sent down for five years and four months for his role in infecting American hospitals and businesses with ransomware and other malware, costing victims tens of millions of dollars in losses.…
Google continues to struggle with cybercriminals running malicious ads on its search platform to trick people into downloading booby-trapped copies of popular free software applications. The malicious ads, which appear above organic search results and often precede links to legitimate sources of the same software, can make searching for software on Google a dicey affair.
Google says keeping users safe is a top priority, and that the company has a team of thousands working around the clock to create and enforce their abuse policies. And by most accounts, the threat from bad ads leading to backdoored software has subsided significantly compared to a year ago.
But cybercrooks are constantly figuring out ingenious ways to fly beneath Google’s anti-abuse radar, and new examples of bad ads leading to malware are still too common.
For example, a Google search earlier this week for the free graphic design program FreeCAD produced the following result, which shows that a “Sponsored” ad at the top of the search results is advertising the software available from freecad-us[.]org. Although this website claims to be the official FreeCAD website, that honor belongs to the result directly below — the legitimate freecad.org.
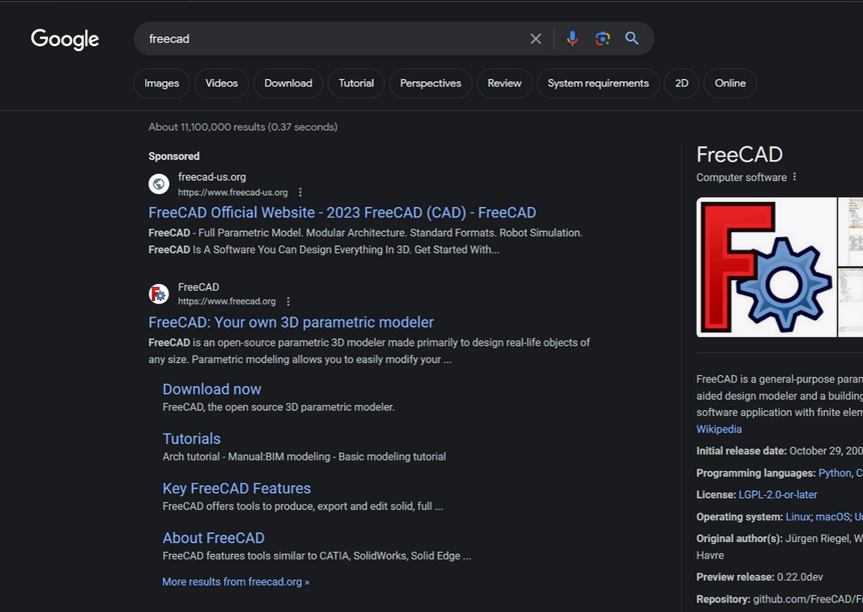
How do we know freecad-us[.]org is malicious? A review at DomainTools.com show this domain is the newest (registered Jan. 19, 2024) of more than 200 domains at the Internet address 93.190.143[.]252 that are confusingly similar to popular software titles, including dashlane-project[.]com, filezillasoft[.]com, keepermanager[.]com, and libreofficeproject[.]com.
Some of the domains at this Netherlands host appear to be little more than software review websites that steal content from established information sources in the IT world, including Gartner, PCWorld, Slashdot and TechRadar.
Other domains at 93.190.143[.]252 do serve actual software downloads, but none of them are likely to be malicious if one visits the sites through direct navigation. If one visits openai-project[.]org and downloads a copy of the popular Windows desktop management application Rainmeter, for example, the file that is downloaded has the same exact file signature as the real Rainmeter installer available from rainmeter.net.
But this is only a ruse, says Tom Hegel, principal threat researcher at the security firm Sentinel One. Hegel has been tracking these malicious domains for more than a year, and he said the seemingly benign software download sites will periodically turn evil, swapping out legitimate copies of popular software titles with backdoored versions that will allow cybercriminals to remotely commander the systems.
“They’re using automation to pull in fake content, and they’re rotating in and out of hosting malware,” Hegel said, noting that the malicious downloads may only be offered to visitors who come from specific geographic locations, like the United States. “In the malicious ad campaigns we’ve seen tied to this group, they would wait until the domains gain legitimacy on the search engines, and then flip the page for a day or so and then flip back.”
In February 2023, Hegel co-authored a report on this same network, which Sentinel One has dubbed MalVirt (a play on “malvertising”). They concluded that the surge in malicious ads spoofing various software products was directly responsible for a surge in malware infections from infostealer trojans like IcedID, Redline Stealer, Formbook and AuroraStealer.
Hegel noted that the spike in malicious software-themed ads came not long after Microsoft started blocking by default Office macros in documents downloaded from the Internet. He said the volume of the current malicious ad campaigns from this group appears to be relatively low compared to a year ago.
“It appears to be same campaign continuing,” Hegel said. “Last January, every Google search for ‘Autocad’ led to something bad. Now, it’s like they’re paying Google to get one out of every dozen of searches. My guess it’s still continuing because of the up-and-down [of the] domains hosting malware and then looking legitimate.”
Several of the websites at this Netherlands host (93.190.143[.]252) are currently blocked by Google’s Safebrowsing technology, and labeled with a conspicuous red warning saying the website will try to foist malware on visitors who ignore the warning and continue.
But it remains a mystery why Google has not similarly blocked more than 240+ other domains at this same host, or else removed them from its search index entirely. Especially considering there is nothing else but these domains hosted at that Netherlands IP address, and because they have all remained at that address for the past year.
In response to questions from KrebsOnSecurity, Google said maintaining a safe ads ecosystem and keeping malware off of its platforms is a priority across Google.
“Bad actors often employ sophisticated measures to conceal their identities and evade our policies and enforcement, sometimes showing Google one thing and users something else,” Google said in a written statement. “We’ve reviewed the ads in question, removed those that violated our policies, and suspended the associated accounts. We’ll continue to monitor and apply our protections.”
Google says it removed 5.2 billion ads in 2022, and restricted more than 4.3 billion ads and suspended over 6.7 million advertiser accounts. The company’s latest ad safety report says Google in 2022 blocked or removed 1.36 billion advertisements for violating its abuse policies.
Some of the domains referenced in this story were included in Sentinel One’s February 2023 report, but dozens more have been added since, such as those spoofing the official download sites for Corel Draw, Github Desktop, Roboform and Teamviewer.
This October 2023 report on the FreeCAD user forum came from a user who reported downloading a copy of the software from freecadsoft[.]com after seeing the site promoted at the top of a Google search result for “freecad.” Almost a month later, another FreeCAD user reported getting stung by the same scam.
“This got me,” FreeCAD forum user “Matterform” wrote on Nov. 19, 2023. “Please leave a report with Google so it can flag it. They paid Google for sponsored posts.”
Sentinel One’s report didn’t delve into the “who” behind this ongoing MalVirt campaign, and there are precious few clues that point to attribution. All of the domains in question were registered through webnic.cc, and several of them display a placeholder page saying the site is ready for content. Viewing the HTML source of these placeholder pages shows many of the hidden comments in the code are in Cyrillic.
Trying to track the crooks using Google’s Ad Transparency tools didn’t lead far. The ad transparency record for the malicious ad featuring freecad-us[.]org (in the screenshot above) shows that the advertising account used to pay for the ad has only run one previous ad through Google search: It advertised a wedding photography website in New Zealand.
The apparent owner of that photography website did not respond to requests for comment, but it’s also likely his Google advertising account was hacked and used to run these malicious ads.
US securities lender EquiLend has pulled a number of its systems offline after a security "incident" in which an attacker gained "unauthorized access".…
HPE has become the latest tech giant to admit it has been compromised by Russian operatives.…
A US court has rejected spyware vendor NSO Group's motion to dismiss a lawsuit filed by Apple that alleges the developer violated computer fraud and other laws by infecting customers' iDevices with its surveillance software.…
Updated The UK's Caravan and Motorhome Club (CAMC) is battling a suspected cyberattack with members reporting widespread IT outages for the past five days.…
Security experts are wasting no time in publishing working exploits for a critical vulnerability in Fortra GoAnywhere MFT, which was publicly disclosed just over a day ago.…
Comment For most organizations – especially security vendors – disclosing a corporate email breach, in which executives' internal messages and attachments were stolen, would noticeably ding their stock prices.…
A password-less database containing an estimated 1.3 million sets of Dutch COVID-19 testing records was left exposed to the open internet, and it's not clear if anyone is taking responsibility.…
The idea that AI could generate super-potent and undetectable malware has been bandied about for years – and also already debunked. However, an article published today by the UK National Cyber Security Centre (NCSC) suggests there is a "realistic possibility" that by 2025, the most sophisticated attackers’ tools will improve markedly thanks to AI models informed by data describing successful cyber-hits.…
CISA Director Jen Easterly has confirmed she was the subject of a swatting attempt on December 30 after a bogus report of a shooting at her home.…
A Baltimore man faces a potential maximum 20-year prison sentence after being charged for his alleged role in running an online service that sold personal data which was later used for financial fraud.…
Southern Water confirmed this morning that criminals broke into its IT systems, making off with a "limited amount of data."…