Australia's government has used the "significant cyber incidents" sanctions regime it introduced in 2021 for the first time, against a Russian named Aleksandr Gennadievich Ermakov whom authorities have deemed responsible for the 2022 attack on health insurer Medibank Private.…
More than 600 IP addresses are launching thousands of exploit attempts against CVE-2023-22527 – a critical bug in out–of-date versions of Atlassian Confluence Data Center and Server – according to non-profit security org Shadowserver.…
AerCap, the world's largest aircraft leasing company, has reported a ransomware infection that occurred earlier this month, but claims it hasn't yet suffered any financial losses yet and all its systems are under control.…
For a country that prides itself on being free, America does seem to have an awful lot of spying going on, as the new Street Surveillance Hub from the Electronic Frontier Foundation shows.…
Critics are accusing major tech companies of not sticking to the rules when it comes to registering vulnerabilities with the appropriate authorities.…
The LockBit ransomware gang is claiming an attack on submarine sandwich slinger Subway, alleging it has made off with a platter of data.…
A financial services company that illegally dispatched tens of thousands of spam messages promising to help the recipients magically wipe away their debts is itself now a debtor to the UK’s data regulator.…
Sponsored Feature Ransomware is used by cybercriminals to steal and encrypt critical business data before demanding payment for its restoration. It represents one of, if not the most, serious cybersecurity threat currently facing governments, public/private sector organizations and enterprises around the world.…
Infosec in brief Conor Brian Fitzpatrick – aka "Pompourin," a former administrator of notorious leak site BreachForums – has been sentenced to 20 years of supervised release.…

They're an odd thing, credential lists. Whether they're from a stealer as in this week's Naz.API incident, or just aggregated from multiple data breaches (which is also in Naz.API), I inevitably get some backlash after loading them: "this doesn't tell me anything useful, why are you loading this?!" The answer is easy: because that's what the vast majority of people want me to do:
If I have a MASSIVE spam list full of personal data being sold to spammers, should I load it into @haveibeenpwned?
— Troy Hunt (@troyhunt) November 15, 2016
Spam lists are the same kettle of fish in that once you learn you're in one, I can't provide you any further info about where it came from and there's no recourse available to you. You're just in there, good luck! And if you do find yourself in one of these lists and are unhappy not that you're in there, but rather that I've told you you're in there, you have 2 easy options:
Or, if you've come along to HIBP, done a search and then been unhappy with me, my guitar lessons blog post is an entertaining read 😊
That's all from Europe folks, see you from the sunny side next week!

A VMware security vulnerability has been exploited by Chinese cyberspies since late 2021, according to Mandiant, in what has been a busy week for nation-state espionage news.…
Five people have been accused of pulling off a "brazen" scam that involved submitting more than $7 million in fake work expense claims to an IT consultancy to bankroll hotel stays, a cruise, visits to strip clubs, and more.…
A Canadian man who says he’s been falsely charged with orchestrating a complex e-commerce scam is seeking to clear his name. His case appears to involve “triangulation fraud,” which occurs when a consumer purchases something online — from a seller on Amazon or eBay, for example — but the seller doesn’t actually own the item for sale. Instead, the seller purchases the item from an online retailer using stolen payment card data. In this scam, the unwitting buyer pays the scammer and receives what they ordered, and very often the only party left to dispute the transaction is the owner of the stolen payment card.
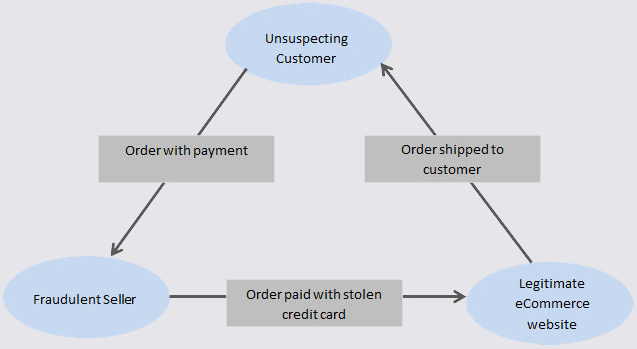
Triangulation fraud. Image: eBay Enterprise.
Timothy Barker, 56, was until recently a Band Manager at Duncan’s First Nation, a First Nation in northwestern Alberta, Canada. A Band Manager is responsible for overseeing the delivery of all Band programs, including community health services, education, housing, social assistance, and administration.
Barker told KrebsOnSecurity that during the week of March 31, 2023 he and the director of the Band’s daycare program discussed the need to purchase items for the community before the program’s budget expired for the year.
“There was a rush to purchase items on the Fiscal Year 2023 timeline as the year ended on March 31,” Barker recalled.
Barker said he bought seven “Step2 All Around Playtime Patio with Canopy” sets from a seller on Amazon.ca, using his payment card on file to pay nearly $2,000 for the items.
On the morning of April 7, Barker’s Facebook account received several nasty messages from an Ontario woman he’d never met. She demanded to know why he’d hacked her Walmart account and used it to buy things that were being shipped to his residence. Barker shared a follow-up message from the woman, who later apologized for losing her temper.
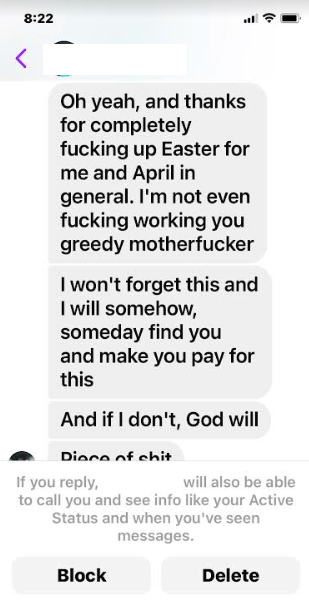
One of several messages from the Ontario woman whose Walmart account was used to purchase the goods that Barker ordered from Amazon.
“If this is not the person who did this to me, I’m sorry, I’m pissed,” the lady from Ontario said. “This order is being delivered April 14th to the address above. If not you, then someone who has the same name. Now I feel foolish.”
On April 12, 2023, before the Amazon purchases had even arrived at his home, Barker received a call from an investigator with the Royal Canadian Mounted Police (RCMP), who said Barker urgently needed to come down to the local RCMP office for an interview related to “an investigation.” Barker said the officer wouldn’t elaborate at the time on the nature of the investigation, and that he told the officer he was in Halifax for several days but could meet after his return home.
According to Barker, the investigator visited his home anyway the following day and began questioning his wife, asking about his whereabouts, his work, and when he might return home.
On April 14, six boxes arrived to partially fulfill his Amazon order; another box was delayed, and the Amazon.ca seller he’d purchased from said the remaining box was expected to ship the following week. Barker said he was confused because all six boxes came from Walmart instead of Amazon, and the shipping labels had his name and address on them but carried a contact phone number in Mexico.
Three days later, the investigator called again, demanding he submit to an interview.
“He then asked where my wife was and what her name is,” Barker said. “He wanted to know her itinerary for the day. I am now alarmed and frightened — this doesn’t feel right.”
Barker said he inquired with a local attorney about a consultation, but that the RCMP investigator showed up at his house before he could speak to the lawyer. The investigator began taking pictures of the boxes from his Amazon order.
“The [investigator] derisively asked why would anyone order so many play sets?” Barker said. “I started to give the very logical answer that we are helping families improve their children’s home life and learning for toddlers when he cut me off and gave the little speech about giving a statement after my arrest. He finally told me that he believes that I used someone’s credit card in Ontario to purchase the Walmart products.”
Eager to clear his name, Barker said he shared with the police copies of his credit card bills and purchase history at Amazon. But on April 21, the investigator called again to say he was coming to arrest Barker for theft.
“He said that if I was home at five o’clock then he would serve the papers at the house and it would go easy and I wouldn’t have to go to the station,” Barker recalled. “If I wasn’t home, then he would send a search team to locate me and drag me to the station. He said he would kick the door down if I didn’t answer my phone. He said he had every right to break our door down.”
Barker said he briefly conferred with an attorney about how to handle the arrest. Later that evening, the RCMP arrived with five squad cars and six officers.
“I asked if handcuffs were necessary – there is no danger of violence,” Barker said. “I was going to cooperate. His response was to turn me around and cuff me. He walked me outside and stood me beside the car for a full 4 or 5 minutes in full view of all the neighbors.”
Barker believes he and the Ontario woman are both victims of triangulation fraud, and that someone likely hacked the Ontario woman’s Walmart account and added his name and address as a recipient.
But he says he has since lost his job as a result of the arrest, and now he can’t find new employment because he has a criminal record. Barker’s former employer — Duncan’s First Nation — did not respond to requests for comment.
“In Canada, a criminal record is not a record of conviction, it’s a record of charges and that’s why I can’t work now,” Barker said. “Potential employers never find out what the nature of it is, they just find out that I have a criminal arrest record.”
Barker said that right after his arrest, the RCMP called the Ontario woman and told her they’d solved the crime and arrested the perpetrator.
“They even told her my employer had put me on administrative leave,” he said. “Surely, they’re not allowed to do that.”
Contacted by KrebsOnSecurity, the woman whose Walmart account was used to fraudulently purchase the child play sets said she’s not convinced this was a case of triangulation fraud. She declined to elaborate on why she believed this, other than to say the police told her Barker was a bad guy.
“I don’t think triangulation fraud was used in this case,” she said. “My actual Walmart.ca account was hacked and an order was placed on my account, using my credit card. The only thing Mr. Barker did was to order the item to be delivered to his address in Alberta.”
Barker shared with this author all of the documentation he gave to the RCMP, including screenshots of his Amazon.ca account showing that the items in dispute were sold by a seller named “Adavio,” and that the merchant behind this name was based in Turkey.
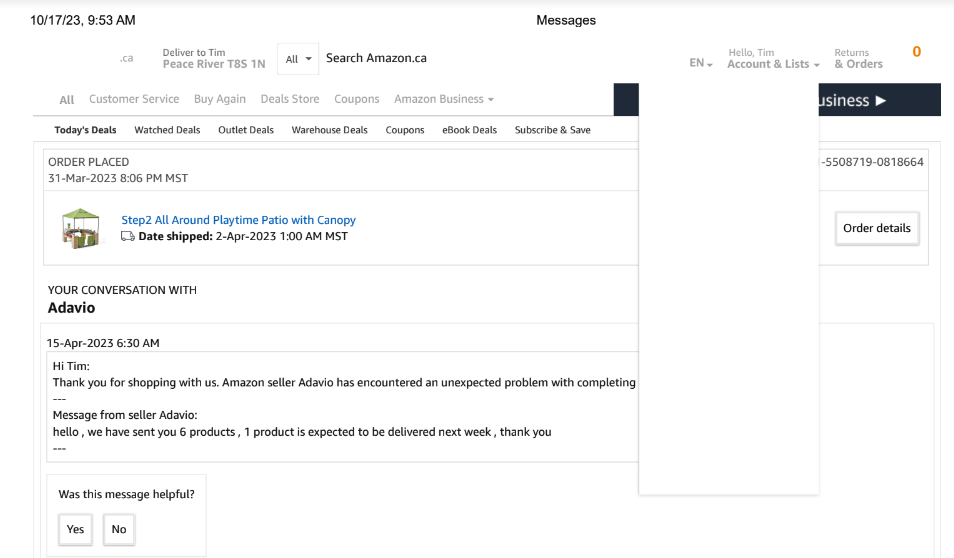
That Adavio account belongs to a young computer engineering student and “SEO expert” based in Adana, Turkey who did not respond to requests for comment.
Amazon.ca said it conducted an investigation and found that Mr. Barker never filed a complaint about the seller or transaction in question. The company noted that Adavio currently has a feedback rating of 4.5 stars out of 5.
“Amazon works hard to provide customers with a great experience and it’s our commitment to go above and beyond to make things right for customers,” Amazon.ca said in a written statement. “If a customer has an issue with an order, they may flag to Amazon through our Customer Service page.”
Barker said when he went to file a complaint with Amazon last year he could no longer find the Adavio account on the website, and that the site didn’t have a category for the type of complaint he wanted to file.
When he first approached KrebsOnSecurity about his plight last summer, Barker said he didn’t want any media attention to derail the chances of having his day in court, and confronting the RCMP investigator with evidence proving that he was being wrongfully prosecuted and maligned.
But a week before his court date arrived at the end of November 2023, prosecutors announced the charges against him would be stayed, meaning they had no immediate plans to prosecute the case further but that the investigation could still be reopened at some point in the future.
The RCMP declined to comment for this story, other than to confirm they had issued a stay of proceedings in the case.
Barker says the stay has left him in legal limbo — denying him the ability to clear his name, while giving the RCMP a free pass for a botched investigation. He says he has considered suing the investigating officer for defamation, but has been told by his attorney that the bar for success in such cases against the government is extremely high.
“I’m a 56-year-old law-abiding citizen, and I haven’t broken any laws,” Barker said, wondering aloud who would be stupid enough to use someone else’s credit card and have the stolen items shipped directly to their home.
“Their putting a stay on the proceedings without giving any evidence or explanation allows them to cover up bad police work,” he said. “It’s all so stupid.”
Triangulation fraud is hardly a new thing. KrebsOnSecurity first wrote about it from an e-commerce vendor’s perspective in 2015, but the scam predates that story by many years and is now a well-understood problem. The Canadian authorities should either let Mr. Barker have his day in court, or drop the charges altogether.
VF Corporation, parent company of clothes and footwear brands including Vans and North Face, says 35.5 million customers were impacted in some way when criminals broke into their systems in December.…
A security researcher in Germany has been fined €3,000 ($3,300, £2,600) for finding and reporting an e-commerce database vulnerability that was exposing almost 700,000 customer records.…
Two US government agencies, the Cybersecurity and Infrastructure Security Agency (CISA) and Federal Bureau of Investigation (FBI), warned on Wednesday that drones made in China could be used to gather information on critical infrastructure.…
Updated The largest bank in the United States repels 45 billion cyberattack attempts per day, one of its leaders claimed at the World Economic Forum in Davos. …
As the US mulls legislation that would see the Cyber Safety Review Board (CSRB) become a permanent fixture in the government's cyber defense armory, experts are calling for substantial changes in the way it's organized.…
Ransomware attacks are being linked to a litany of psychological and physical illnesses reported by infosec professionals, and in some cases blamed for hospitalizations.…