
Researchers say mobile malware purveyors have been abusing a bug in the Google Android platform that lets them sneak malicious code into mobile apps and evade security scanning tools. Google says it has updated its app malware detection mechanisms in response to the new research.
At issue is a mobile malware obfuscation method identified by researchers at ThreatFabric, a security firm based in Amsterdam. Aleksandr Eremin, a senior malware analyst at the company, told KrebsOnSecurity they recently encountered a number of mobile banking trojans abusing a bug present in all Android OS versions that involves corrupting components of an app so that its new evil bits will be ignored as invalid by popular mobile security scanning tools, while the app as a whole gets accepted as valid by Android OS and successfully installed.
“There is malware that is patching the .apk file [the app installation file], so that the platform is still treating it as valid and runs all the malicious actions it’s designed to do, while at the same time a lot of tools designed to unpack and decompile these apps fail to process the code,” Eremin explained.
Eremin said ThreatFabric has seen this malware obfuscation method used a few times in the past, but in April 2023 it started finding many more variants of known mobile malware families leveraging it for stealth. The company has since attributed this increase to a semi-automated malware-as-a-service offering in the cybercrime underground that will obfuscate or “crypt” malicious mobile apps for a fee.
Eremin said Google flagged their initial May 9, 2023 report as “high” severity. More recently, Google awarded them a $5,000 bug bounty, even though it did not technically classify their finding as a security vulnerability.
“This was a unique situation in which the reported issue was not classified as a vulnerability and did not impact the Android Open Source Project (AOSP), but did result in an update to our malware detection mechanisms for apps that might try to abuse this issue,” Google said in a written statement.
Google also acknowledged that some of the tools it makes available to developers — including APK Analyzer — currently fail to parse such malicious applications and treat them as invalid, while still allowing them to be installed on user devices.
“We are investigating possible fixes for developer tools and plan to update our documentation accordingly,” Google’s statement continued.
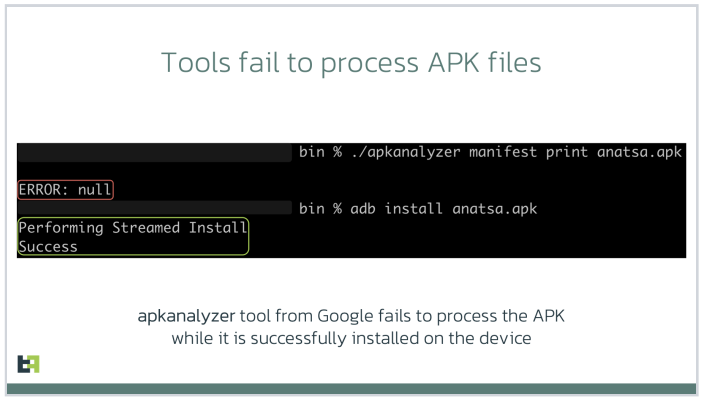
Image: ThreatFabric.
According to ThreatFabric, there are a few telltale signs that app analyzers can look for that may indicate a malicious app is abusing the weakness to masquerade as benign. For starters, they found that apps modified in this way have Android Manifest files that contain newer timestamps than the rest of the files in the software package.
More critically, the Manifest file itself will be changed so that the number of “strings” — plain text in the code, such as comments — specified as present in the app does match the actual number of strings in the software.
One of the mobile malware families known to be abusing this obfuscation method has been dubbed Anatsa, which is a sophisticated Android-based banking trojan that typically is disguised as a harmless application for managing files. Last month, ThreatFabric detailed how the crooks behind Anatsa will purchase older, abandoned file managing apps, or create their own and let the apps build up a considerable user base before updating them with malicious components.
ThreatFabric says Anatsa poses as PDF viewers and other file managing applications because these types of apps already have advanced permissions to remove or modify other files on the host device. The company estimates the people behind Anatsa have delivered more than 30,000 installations of their banking trojan via ongoing Google Play Store malware campaigns.
Google has come under fire in recent months for failing to more proactively police its Play Store for malicious apps, or for once-legitimate applications that later go rogue. This May 2023 story from Ars Technica about a formerly benign screen recording app that turned malicious after garnering 50,000 users notes that Google doesn’t comment when malware is discovered on its platform, beyond thanking the outside researchers who found it and saying the company removes malware as soon as it learns of it.
“The company has never explained what causes its own researchers and automated scanning process to miss malicious apps discovered by outsiders,” Ars’ Dan Goodin wrote. “Google has also been reluctant to actively notify Play users once it learns they were infected by apps promoted and made available by its own service.”
The Ars story mentions one potentially positive change by Google of late: A preventive measure available in Android versions 11 and higher that implements “app hibernation,” which puts apps that have been dormant into a hibernation state that removes their previously granted runtime permissions.













[This is Part III in a series on research conducted for a recent Hulu documentary on the 2015 hack of marital infidelity website AshleyMadison.com.]
In 2019, a Canadian company called Defiant Tech Inc. pleaded guilty to running LeakedSource[.]com, a service that sold access to billions of passwords and other data exposed in countless data breaches. KrebsOnSecurity has learned that the owner of Defiant Tech, a 32-year-old Ontario man named Jordan Evan Bloom, was hired in late 2014 as a developer for the marital infidelity site AshleyMadison.com. Bloom resigned from AshleyMadison citing health reasons in June 2015 — less than one month before unidentified hackers stole data on 37 million users — and launched LeakedSource three months later.

Jordan Evan Bloom, posing in front of his Lamborghini.
On Jan. 15, 2018, the Royal Canadian Mounted Police (RCMP) charged then 27-year-old Bloom, of Thornhill, Ontario, with selling stolen personal identities online through the website LeakedSource[.]com.
LeakedSource was advertised on a number of popular cybercrime forums as a service that could help hackers break into valuable or high-profile accounts. LeakedSource also tried to pass itself off as a legal, legitimate business that was marketing to security firms and professionals.
The RCMP arrested Bloom in December 2017, and said he made approximately $250,000 selling hacked data, which included information on 37 million user accounts leaked in the 2015 Ashley Madison breach.
Subsequent press releases from the RCMP about the LeakedSource investigation omitted any mention of Bloom, and referred to the defendant only as Defiant Tech. In a legal settlement that is quintessentially Canadian, the matter was resolved in 2019 after Defiant Tech agreed to plead guilty. The RCMP declined to comment for this story.
The Impact Team, the hacker group that claimed responsibility for stealing and leaking the AshleyMadison user data, also leaked several years worth of email from then-CEO Noel Biderman. A review of those messages shows that Ashley Madison hired Jordan Evan Bloom as a PHP developer in December 2014 — even though the company understood that Bloom’s success as a programmer and businessman was tied to shady and legally murky enterprises.
Bloom’s recommendation came to Biderman via Trevor Sykes, then chief technology officer for Ashley Madison parent firm Avid Life Media (ALM). The following is an email from Sykes to Biderman dated Nov. 14, 2014:
“Greetings Noel,
“We’d like to offer Jordan Bloom the position of PHP developer reporting to Mike Morris for 75k CAD/Year. He did well on the test, but he also has a great understanding of the business side of things having run small businesses himself. This was an internal referral.”
When Biderman responded that he needed more information about the candidate, Sykes replied that Bloom was independently wealthy as a result of his forays into the shadowy world of “gold farming” — the semi-automated use of large numbers of player accounts to win some advantage that is usually related to cashing out game accounts or inventory. Gold farming is particularly prevalent in massively multiplayer online role-playing games (MMORPGs), such as RuneScape and World of Warcraft.
“In his previous experience he had been doing RMT (Real Money Trading),” Sykes wrote. “This is the practice of selling virtual goods in games for real world money. This is a grey market, which is usually against the terms and services of the game companies.” Here’s the rest of his message to Biderman:
“RMT sellers traditionally have a lot of problems with chargebacks, and payment processor compliance. During my interview with him, I spent some time focusing in on this. He had to demonstrate to the processor, Paypal, at the time he had a business and technical strategy to address his charge back rate.”
“He ran this company himself, and did all the coding, including the integration with the processors,” Sykes continued in his assessment of Bloom. “Eventually he was squeezed out by Chinese gold farmers, and their ability to market with much more investment than he could. In addition the cost of ‘farming’ the virtual goods was cheaper in China to do than in North America.”
The gold farming reference is fascinating because in 2017 KrebsOnSecurity published Who Ran LeakedSource?, which examined clues suggesting that one of the administrators of LeakedSource also was the admin of abusewith[.]us, a site unabashedly dedicated to helping people hack email and online gaming accounts.

An administrator account Xerx3s on Abusewithus.
Abusewith[.]us began in September 2013 as a forum for learning and teaching how to hack accounts at Runescape, an MMORPG set in a medieval fantasy realm where players battle for kingdoms and riches.
The currency with which Runescape players buy and sell weapons, potions and other in-game items are virtual gold coins, and many of Abusewith[dot]us’s early members traded in a handful of commodities: Phishing kits and exploits that could be used to steal Runescape usernames and passwords from fellow players; virtual gold plundered from hacked accounts; and databases from hacked forums and websites related to Runescape and other online games.
That 2017 report here interviewed a Michigan man who acknowledged being administrator of Abusewith[.]us, but denied being the operator of LeakedSource. Still, the story noted that LeakedSource likely had more than one operator, and breached records show Bloom was a prolific member of Abusewith[.]us.
In an email to all employees on Dec. 1, 2014, Ashley Madison’s director of HR said Bloom graduated from York University in Toronto with a degree in theoretical physics, and that he has been an active programmer since high school.
“He’s a proprietor of a high traffic multiplayer game and developer/publisher of utilities such as PicTrace,” the HR director enthused. “He will be a great addition to the team.”
PicTrace appears to have been a service that allowed users to glean information about anyone who viewed an image hosted on the platform, such as their Internet address, browser type and version number. A copy of pictrace[.]com from Archive.org in 2012 redirects to the domain qksnap.com, which DomainTools.com says was registered to a Jordan Bloom from Thornhill, ON that same year.
The street address listed in the registration records for qksnap.com — 204 Beverley Glen Blvd — also shows up in the registration records for leakadvisor[.]com, a domain registered in 2017 just months after Canadian authorities seized the servers running LeakedSource.
Pictrace, one of Jordan Bloom’s early IT successes.
A review of passive DNS records from DomainTools indicates that in 2013 pictrace[.]com shared a server with just a handful of other domains, including Near-Reality[.]com — a popular RuneScape Private Server (RSPS) game based on the RuneScape MMORPG.
Copies of near-reality[.]com from 2013 via Archive.org show the top of the community’s homepage was retrofitted with a message saying Near Reality was no longer available due to a copyright dispute. Although the site doesn’t specify the other party to the copyright dispute, it appears Near-Reality got sued by Jagex, the owner of RuneScape.
The message goes on to say the website will no longer “encourage, facilitate, enable or condone (i) any infringement of copyright in RuneScape or any other Jagex product; nor (ii) any breach of the terms and conditions of RuneScape or any other Jagex product.”

A scene from the MMORPG RuneScape.
Near Reality also has a Facebook page that was last updated in 2019, when its owner posted a link to a news story about Defiant Tech’s guilty plea in the LeakedSource investigation. That Facebook page indicates Bloom also went by the nickname “Agentjags.”
“Just a quick PSA,” reads a post to the Near Reality Facebook page dated Jan. 21, 2018, which linked to a story about the charges against Bloom and a photo of Bloom standing in front of his lime-green Lamborghini. “Agentjags has got involved in some shady shit that may have compromised your personal details. I advise anyone who is using an old NR [Near Reality] password for anything remotely important should change it ASAP.”
By the beginning of 2016, Bloom was nowhere to be found, and was suspected of having fled his country for the Caribbean, according to the people commenting on the Near Reality Facebook page:
“Jordan aka Agentjags has gone missing,” wrote a presumed co-owner of the Facebook page. “He is supposedly hiding in St. Lucia, doing what he loved, scuba-diving. Any information to his whereabouts will be appreciated.”
KrebsOnSecurity ran the unusual nickname “AgentJags” through a search at Constella Intelligence, a commercial service that tracks breached data sets. That search returned just a few dozen results — and virtually all were accounts at various RuneScape-themed sites, including a half-dozen accounts at Abusewith[.]us.
Constella found other “AgentJags” accounts tied to the email address ownagegaming1@gmail.com. The marketing firm Apollo.io experienced a data breach several years back, and according to Apollo the email address ownagegaming1@gmail.com belongs to Jordan Bloom in Ontario.
Constella also revealed that the password frequently used by ownagegaming1@gmail.com across many sites was some variation on “niggapls,” which my 2017 report found was also the password used by the administrator of LeakedSource.
Constella discovered that the email eric.malek@rogers.com comes up when one searches for “AgentJags.” This is curious because emails leaked from Ashley Madison’s then-CEO Biderman show that Eric Malek from Toronto was the Ashley Madison employee who initially recommended Bloom for the PHP developer job.
According to DomainTools.com, Eric.Malek@rogers.com was used to register the domain devjobs.ca, which previously advertised “the most exciting developer jobs in Canada, delivered to you weekly.” Constella says eric.malek@rogers.com also had an account at Abusewith[.]us — under the nickname “Jags.”
Biderman’s email records show Eric Malek was also a PHP developer for Ashley Madison, and that he was hired into this position just a few months before Bloom — on Sept. 2, 2014. The CEO’s leaked emails show Eric Malek resigned from his developer position at Ashley Madison on June 19, 2015.
“Please note that Eric Malek has resigned from this position with Avid and his last day will be June 19th,” read a June 5, 2015 email from ALM’s HR director. “He is resigning to deal with some personal issues which include health issues. Because he is not sure how much time it will take to resolve, he is not requesting a leave of absence (his time off will be indefinite). Overall, he likes the company and plans to reach out to Trevor or I when the issues are resolved to see what is available at that time.”
A follow-up email from Biderman demanded, “want to know where he’s truly going….,” and it’s unclear whether there was friction with Malek’s departure. But ALM General Counsel Avi Weisman replied indicating that Malek probably would not sign an “Exit Acknowledgment Form” prior to leaving, and that the company had unanswered questions for Malek.
“Aneka should dig during exit interview,” Weisman wrote. “Let’s see if he balks at signing the Acknowledgment.”
Bloom’s departure notice from Ashley Madison’s HR person, dated June 23, 2015, read:
“Please note that Jordan Bloom has resigned from his position as PHP Developer with Avid. He is leaving for personal reasons. He has a neck issue that will require surgery in the upcoming months and because of his medical appointment schedule and the pain he is experiencing he can no longer commit to a full-time schedule. He may pick up contract work until he is back to 100%.”
A follow-up note to Biderman about this announcement read:
“Note that he has disclosed that he is independently wealthy so he can get by without FT work until he is on the mend. He has signed the Exit Acknowledgement Form already without issue. He also says he would consider reapplying to Avid in the future if we have opportunities available at that time.”
Perhaps Mr. Bloom hurt his neck from craning it around blind spots in his Lamborghini. Maybe it was from a bad scuba outing. Whatever the pain in Bloom’s neck was, it didn’t stop him from launching himself fully into LeakedSource[.]com, which was registered roughly one month after the Impact Team leaked data on 37 million Ashley Madison accounts.
Mr. Malek declined a request for comment. A now-deleted LinkedIn profile for Malek from December 2018 listed him as a “technical recruiter” from Toronto who also attended Mr. Bloom’s alma mater — York University. That resume did not mention Mr. Malek’s brief stint as a PHP developer at Ashley Madison.
“Developer, entrepreneur, and now technical recruiter of the most uncommon variety!” Mr. Malek’s LinkedIn profile enthused. “Are you a developer, or other technical specialist, interested in working with a recruiter who can properly understand your concerns and aspirations, technical, environmental and financial? Don’t settle for a ‘hack’; this is your career, let’s do it right! Connect with me on LinkedIn. Note: If you are not a resident of Canada/Toronto, I cannot help you.”
Mr. Bloom told KrebsOnSecurity he had no role in harming or hacking Ashley Madison. Bloom validated his identity by responding at one of the email addresses mentioned above, and agreed to field questions so long as KrebsOnSecurity agreed to publish our email conversation in full (PDF).
Bloom said Mr. Malek did recommend him for the Ashley Madison job, but that Mr. Malek also received a $5,000 referral bonus for doing so. Given Mr. Malek’s stated role as a technical recruiter, it seems likely he also recommended several other employees to Ashley Madison.
Bloom was asked whether anyone at the RCMP, Ashley Madison or any authority anywhere ever questioned him in connection with the July 2015 hack of Ashley Madison. He replied that he was called once by someone claiming to be from the Toronto Police Service asking if he knew anything about the Ashley Madison hack.
“The AM situation was not something they pursued according to the RCMP disclosure,” Bloom wrote. “Learning about the RCMP’s most advanced cyber investigative techniques and capabilities was very interesting though. I was eventually told information by a third party which included knowledge that law enforcement effectively knew who the hacker was, but didn’t have enough evidence to proceed with a case. That is the extent of my involvement with any authorities.”
As to his company’s guilty plea for operating LeakedSource, Bloom maintains that the judge at his preliminary inquiry found that even if everything the Canadian government alleged was true it would not constitute a violation of any law in Canada with respect the charges the RCMP leveled against him, which included unauthorized use of a computer and “mischief to data.”
“In Canada at the lower court level we are allowed to possess stolen information and manipulate our copies of them as we please,” Bloom said. “The judge however decided that a trial was required to determine whether any activities of mine were reckless, as the other qualifier of intentionally criminal didn’t apply. I will note here that nothing I was accused of doing would have been illegal if done in the United States of America according to their District Attorney. +1 for free speech in America vs freedom of expression in Canada.”
“Shortly after their having most of their case thrown out, the Government proposed an offer during a closed door meeting where they would drop all charges against me, provide full and complete personal immunity, and in exchange the Corporation which has since been dissolved would plead guilty,” Bloom continued. “The Corporation would also pay a modest fine.”
Bloom said he left Ashley Madison because he was bored, but he acknowledged starting LeakedSource partly in response to the Ashley Madison hack.
“I intended to leverage my gaming connections to get into security work including for other private servers such as Minecraft communities and others,” Bloom said. “After months of asking management for more interesting tasks, I became bored. Some days I had virtually nothing to do except spin in my chair so I would browse the source code for security holes to fix because I found it enjoyable.”
“I believe the decision to start LS [LeakedSource] was partly inspired by the AM hack itself, and the large number of people from a former friend group messaging me asking if XYZ person was in the leak after I revealed to them that I downloaded a copy and had the ability to browse it,” Bloom continued. “LS was never my idea – I was just a builder, and the only Canadian. In other countries it was never thought to be illegal on closer examination of their laws.”
Bloom said he still considers himself independently wealthy, and that still has the lime green Lambo. But he said he’s currently unemployed and can’t seem to land a job in what he views as his most promising career path: Information security.
“As I’m sure you’re aware, having negative media attention associated with alleged (key word) criminal activity can have a detrimental effect on employment, banking and relationships,” Bloom wrote. “I have no current interest in being a business owner, nor do I have any useful business ideas to be honest. I was and am interested in interesting Information Security/programming work but it’s too large of a risk for any business to hire someone who was formerly accused of a crime.”
If you liked this story, please consider reading the first two pieces in this series:
SEO Expert Hired and Fired by Ashley Madison Turned on Company, Promising Revenge
Top Suspect in 2015 Ashley Madison Hack Committed Suicide in 2014
There is a significant secondary marketplace where tickets can sell for several times their original value, opening the opportunity for scammers and fraud
The post Protect yourself from ticketing scams ahead of the Premier League Summer Series USA Tour appeared first on WeLiveSecurity








s3-ep100-js-1200




The United Parcel Service (UPS) says fraudsters have been harvesting phone numbers and other information from its online shipment tracking tool in Canada to send highly targeted SMS phishing (a.k.a. “smishing”) messages that spoofed UPS and other top brands. The missives addressed recipients by name, included details about recent orders, and warned that those orders wouldn’t be shipped unless the customer paid an added delivery fee.
In a snail mail letter sent this month to Canadian customers, UPS Canada Ltd. said it is aware that some package recipients have received fraudulent text messages demanding payment before a package can be delivered, and that it has been working with partners in its delivery chain to try to understand how the fraud was occurring.

The recent letter from UPS about SMS phishers harvesting shipment details and phone numbers from its website.
“During that review, UPS discovered a method by which a person who searched for a particular package or misused a package look-up tool could obtain more information about the delivery, potentially including a recipient’s phone number,” the letter reads. “Because this information could be misused by third parties, including potentially in a smishing scheme, UPS has taken steps to limit access to that information.”
The written notice goes on to say UPS believes the data exposure “affected packages for a small group of shippers and some of their customers from February 1, 2022 to April 24, 2023.”
As early as April 2022, KrebsOnSecurity began receiving tips from Canadian readers who were puzzling over why they’d just received one of these SMS phishing messages that referenced information from a recent order they’d legitimately placed at an online retailer.
In March, 2023, a reader named Dylan from British Columbia wrote in to say he’d received one of these shipping fee scam messages not long after placing an order to buy gobs of building blocks directly from Lego.com. The message included his full name, phone number, and postal code, and urged him to click a link to mydeliveryfee-ups[.]info and pay a $1.55 delivery fee that was supposedly required to deliver his Legos.
“From searching the text of this phishing message, I can see that a lot of people have experienced this scam, which is more convincing because of the information the phishing text contains,” Dylan wrote. “It seems likely to me that UPS is leaking information somehow about upcoming deliveries.”
Josh is a reader who works for a company that ships products to Canada, and in early January 2023 he inquired whether there was any information about a breach at UPS Canada.
“We’ve seen many of our customers targeted with a fraudulent UPS text message scheme after placing an order,” Josh said. “A link is provided (often only after the customer responds to the text) which takes you to a captcha page, followed by a fraudulent payment collection page.”
Pivoting on the domain in the smishing message sent to Dylan shows the phishing domain shared an Internet host in Russia [91.215.85-166] with nearly two dozen other smishing related domains, including upsdelivery[.]info, legodelivery[.]info, adidascanadaltd[.]com, crocscanadafee[.]info, refw0234apple[.]info, vista-printcanada[.]info and telus-ca[.]info.
The inclusion of big-name brands in the domains of these UPS smishing campaigns suggests the perpetrators had the ability to focus their lookups on UPS customers who had recently ordered items from specific companies.
Attempts to visit these domains with a web browser failed, but loading them in a mobile device (or in my case, emulating a mobile device using a virtual machine and Developer Tools in Firefox) revealed the first stage of this smishing attack. As Josh mentioned, what first popped up was a CAPTCHA; after the visitor solved the CAPTCHA, they were taken through several more pages that requested the user’s full name, date of birth, credit card number, address, email and phone number.
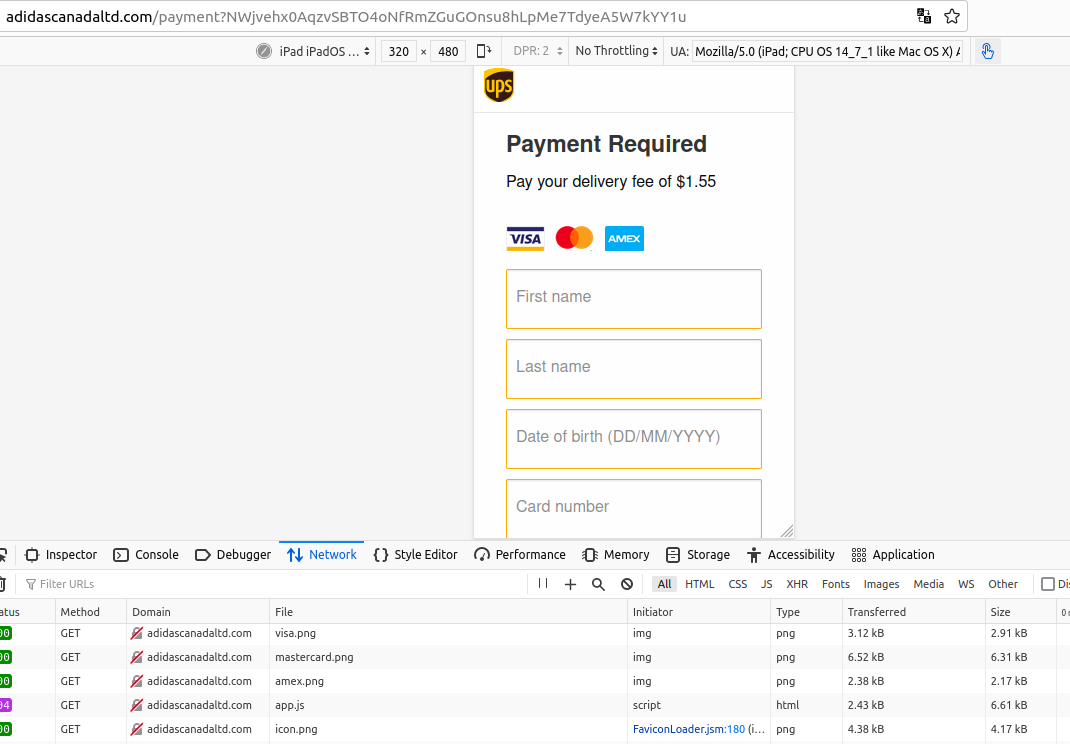
A smishing website targeting Canadians who recently purchased from Adidas online. The site would only load in a mobile browser.
In April 2022, KrebsOnSecurity heard from Alex, the CEO of a technology company in Canada who asked to leave his last name out of this story. Alex reached out when he began receiving the smishing messages almost immediately after ordering two sets of Airpods directly from Apple’s website.
What puzzled Alex most was that he’d instructed Apple to send the Airpods as a gift to two different people, and less than 24 hours later the phone number he uses for his Apple account received two of the phishing messages, both of which contained salutations that included the names of the people for whom he’d bought Airpods.
“I’d put the recipient as different people on my team, but because it was my phone number on both orders I was the one getting the texts,” Alex explained. “That same day, I got text messages referring to me as two different people, neither of whom were me.”
Alex said he believes UPS Canada either doesn’t fully understand what happened yet, or it is being coy about what it knows. He said the wording of UPS’s response misleadingly suggests the smishing attacks were somehow the result of hackers randomly looking up package information via the company’s tracking website.
Alex said it’s likely that whoever is responsible figured out how to query the UPS Canada website for only pending orders from specific brands, perhaps by exploiting some type of application programming interface (API) that UPS Canada makes or made available to its biggest retail partners.
“It wasn’t like I put the order through [on Apple.ca] and some days or weeks later I got a targeted smishing attack,” he said. “It was more or less the same day. And it was as if [the phishers] were being notified the order existed.”
The letter to UPS Canada customers does not mention whether any other customers in North America were affected, and it remains unclear whether any UPS customers outside of Canada may have been targeted.
In a statement provided to KrebsOnSecurity, Sandy Springs, Ga. based UPS [NYSE:UPS] said the company has been working with partners in the delivery chain to understand how that fraud was being perpetrated, as well as with law enforcement and third-party experts to identify the cause of this scheme and to put a stop to it.
“Law enforcement has indicated that there has been an increase in smishing impacting a number of shippers and many different industries,” reads an email from Brian Hughes, director of financial and strategy communications at UPS.
“Out of an abundance of caution, UPS is sending privacy incident notification letters to individuals in Canada whose information may have been impacted,” Hughes said. “We encourage our customers and general consumers to learn about the ways they can stay protected against attempts like this by visiting the UPS Fight Fraud website.”






The U.S. government agency in charge of improving the nation’s cybersecurity posture is ordering all federal agencies to take new measures to restrict access to Internet-exposed networking equipment. The directive comes amid a surge in attacks targeting previously unknown vulnerabilities in widely used security and networking appliances.

Under a new order from the Cybersecurity and Infrastructure Security Agency (CISA), federal agencies will have 14 days to respond to any reports from CISA about misconfigured or Internet-exposed networking equipment. The directive applies to any networking devices — such as firewalls, routers and load balancers — that allow remote authentication or administration.
The order requires federal departments to limit access so that only authorized users on an agency’s local or internal network can reach the management interfaces of these devices. CISA’s mandate follows a slew of recent incidents wherein attackers exploited zero-day flaws in popular networking products to conduct ransomware and cyber espionage attacks on victim organizations.
Earlier today, incident response firm Mandiant revealed that since at least October 2022, Chinese cyber spies have been exploiting a zero-day vulnerability in many email security gateway (ESG) appliances sold by California-based Barracuda Networks to hoover up email from organizations using these devices.
Barracuda was alerted to the exploitation of a zero-day in its products in mid-May, and two days later the company pushed a security update to address the flaw in all affected devices. But last week, Barracuda took the highly unusual step of offering to replace compromised ESGs, evidently in response to malware that altered the systems in such a fundamental way that they could no longer be secured remotely with software updates.
According to Mandiant, a previously unidentified Chinese hacking group was responsible for exploiting the Barracuda flaw, and appeared to be searching through victim organization email records for accounts “belonging to individuals working for a government with political or strategic interest to [China] while this victim government was participating in high-level, diplomatic meetings with other countries.”
When security experts began raising the alarm about a possible zero-day in Barracuda’s products, the Chinese hacking group altered their tactics, techniques and procedures (TTPs) in response to Barracuda’s efforts to contain and remediate the incident, Mandiant found.
Mandiant said the attackers will continue to change their tactics and malware, “especially as network defenders continue to take action against this adversary and their activity is further exposed by the infosec community.”
Meanwhile, this week we learned more details about the ongoing exploitation of a zero-day flaw in a broad range of virtual private networking (VPN) products made by Fortinet — devices many organizations rely on to facilitate remote network access for employees.
On June 11, Fortinet released a half-dozen security updates for its FortiOS firmware, including a weakness that researchers said allows an attacker to run malware on virtually any Fortinet SSL VPN appliance. The researchers found that just being able to reach the management interface for a vulnerable Fortinet SSL VPN appliance was enough to completely compromise the devices.
“This is reachable pre-authentication, on every SSL VPN appliance,” French vulnerability researcher Charles Fol tweeted. “Patch your #Fortigate.”
In details published on June 12, Fortinet confirmed that one of the vulnerabilities (CVE-2023-27997) is being actively exploited. The company said it discovered the weakness in an internal code audit that began in January 2023 — when it learned that Chinese hackers were exploiting a different zero-day flaw in its products.
Shodan.io, the search engine made for finding Internet of Things devices, reports that there are currently more than a half-million vulnerable Fortinet devices reachable via the public Internet.
The new cybersecurity directive from CISA orders agencies to remove any networking device management interfaces from the internet by making them only accessible from an internal enterprise network (CISA recommends an isolated management network). CISA also says agencies should “deploy capabilities, as part of a Zero Trust Architecture, that enforce access control to the interface through a policy enforcement point separate from the interface itself (preferred action).”

Security experts say CISA’s directive highlights the reality that cyberspies and ransomware gangs are making it increasingly risky for organizations to expose any devices to the public Internet, because these groups have strong incentives to probe such devices for previously unknown security vulnerabilities.
The most glaring example of this dynamic can be seen in the frequency with which ransomware groups have discovered and pounced on zero-day flaws in widely-used file transfer applications. One ransomware gang in particular — Cl0p — has repeatedly exploited zero day bugs in various file transfer appliances to extort tens of millions of dollars from hundreds of ransomware victims.
On February 2, KrebsOnSecurity broke the news that attackers were exploiting a zero-day vulnerability in the GoAnywhere file transfer appliance by Fortra. By the time security updates were available to fix the vulnerability, Cl0p had already used it to steal data from more than a hundred organizations running Fortra’s appliance.
According to CISA, on May 27, Cl0p began exploiting a previously unknown flaw in MOVEit Transfer, a popular Internet-facing file transfer application. MOVEit parent Progress Software has since released security updates to address the weakness, but Cl0p claims to have already used it to compromise hundreds of victim organizations. TechCrunch has been tracking the fallout from victim organizations, which range from banks and insurance providers to universities and healthcare entities.
The always on-point weekly security news podcast Risky Business has recently been urging organizations to jettison any and all FTP appliances, noting that Cl0p (or another crime gang) is likely to visit the same treatment on other FTP appliance vendors.
But that sound advice doesn’t exactly scale for mid-tier networking devices like Barracuda ESGs or Fortinet SSL VPNs, which are particularly prominent in small to mid-sized organizations.
“It’s not like FTP services, you can’t tell an enterprise [to] turn off the VPN [because] the productivity hit of disconnecting the VPN is terminal, it’s a non-starter,” Risky Business co-host Adam Boileau said on this week’s show. “So how to mitigate the impact of having to use a domain-joined network appliance at the edge of your network that is going to get zero-day in it? There’s no good answer.”
Risky Business founder Patrick Gray said the COVID-19 pandemic breathed new life into entire classes of networking appliances that rely on code which was never designed with today’s threat models in mind.
“In the years leading up to the pandemic, the push towards identity-aware proxies and zero trust everything and moving away from this type of equipment was gradual, but it was happening,” Gray said. “And then COVID-19 hit and everybody had to go work from home, and there really was one option to get going quickly — which was to deploy VPN concentrators with enterprise features.”
Gray said the security industry had been focused on building the next generation of remote access tools that are more security-hardened, but when the pandemic hit organizations scrambled to cobble together whatever they could.
“The only stuff available in the market was all this old crap that is not QA’d properly, and every time you shake them CVEs fall out,” Gray remarked, calling the pandemic, “a shot in the arm” to companies like Fortinet and Barracuda.
“They sold so many VPNs through the pandemic and this is the hangover,” Gray said. “COVID-19 extended the life of these companies and technologies, and that’s unfortunate.”
It’s not often that a zero-day vulnerability causes a network security vendor to urge customers to physically remove and decommission an entire line of affected hardware — as opposed to just applying software updates. But experts say that is exactly what transpired this week with Barracuda Networks, as the company struggled to combat a sprawling malware threat which appears to have undermined its email security appliances in such a fundamental way that they can no longer be safely updated with software fixes.

The Barracuda Email Security Gateway (ESG) 900 appliance.
Campbell, Calif. based Barracuda said it hired incident response firm Mandiant on May 18 after receiving reports about unusual traffic originating from its Email Security Gateway (ESG) devices, which are designed to sit at the edge of an organization’s network and scan all incoming and outgoing email for malware.
On May 19, Barracuda identified that the malicious traffic was taking advantage of a previously unknown vulnerability in its ESG appliances, and on May 20 the company pushed a patch for the flaw to all affected appliances (CVE-2023-2868).
In its security advisory, Barracuda said the vulnerability existed in the Barracuda software component responsible for screening attachments for malware. More alarmingly, the company said it appears attackers first started exploiting the flaw in October 2022.
But on June 6, Barracuda suddenly began urging its ESG customers to wholesale rip out and replace — not patch — affected appliances.
“Impacted ESG appliances must be immediately replaced regardless of patch version level,” the company’s advisory warned. “Barracuda’s recommendation at this time is full replacement of the impacted ESG.”
In a statement, Barracuda said it will be providing the replacement product to impacted customers at no cost, and that not all ESG appliances were compromised.
“No other Barracuda product, including our SaaS email solutions, were impacted by this vulnerability,” the company said. “If an ESG appliance is displaying a notification in the User Interface, the ESG appliance had indicators of compromise. If no notification is displayed, we have no reason to believe that the appliance has been compromised at this time.”
Nevertheless, the statement says that “out of an abundance of caution and in furtherance of our containment strategy, we recommend impacted customers replace their compromised appliance.”
“As of June 8, 2023, approximately 5% of active ESG appliances worldwide have shown any evidence of known indicators of compromise due to the vulnerability,” the statement continues. “Despite deployment of additional patches based on known IOCs, we continue to see evidence of ongoing malware activity on a subset of the compromised appliances. Therefore, we would like customers to replace any compromised appliance with a new unaffected device.”
Rapid7‘s Caitlin Condon called this remarkable turn of events “fairly stunning,” and said there appear to be roughly 11,000 vulnerable ESG devices still connected to the Internet worldwide.
“The pivot from patch to total replacement of affected devices is fairly stunning and implies the malware the threat actors deployed somehow achieves persistence at a low enough level that even wiping the device wouldn’t eradicate attacker access,” Condon wrote.
Barracuda said the malware was identified on a subset of appliances that allowed the attackers persistent backdoor access to the devices, and that evidence of data exfiltration was identified on some systems.
Rapid7 said it has seen no evidence that attackers are using the flaw to move laterally within victim networks. But that may be small consolation for Barracuda customers now coming to terms with the notion that foreign cyberspies probably have been hoovering up all their email for months.
Nicholas Weaver, a researcher at University of California, Berkeley’s International Computer Science Institute (ICSI), said it is likely that the malware was able to corrupt the underlying firmware that powers the ESG devices in some irreparable way.
“One of the goals of malware is to be hard to remove, and this suggests the malware compromised the firmware itself to make it really hard to remove and really stealthy,” Weaver said. “That’s not a ransomware actor, that’s a state actor. Why? Because a ransomware actor doesn’t care about that level of access. They don’t need it. If they’re going for data extortion, it’s more like a smash-and-grab. If they’re going for data ransoming, they’re encrypting the data itself — not the machines.”
In addition to replacing devices, Barracuda says ESG customers should also rotate any credentials connected to the appliance(s), and check for signs of compromise dating back to at least October 2022 using the network and endpoint indicators the company has released publicly.
Update, June 9, 11:55 a.m. ET: Barracuda has issued an updated statement about the incident, portions of which are now excerpted above.


s3-ep138-1200

One of the most expensive aspects of any cybercriminal operation is the time and effort it takes to constantly create large numbers of new throwaway email accounts. Now a new service offers to help dramatically cut costs associated with large-scale spam and account creation campaigns, by paying people to sell their email account credentials and letting customers temporarily rent access to a vast pool of established accounts at major providers.

The service in question — kopeechka[.]store — is perhaps best described as a kind of unidirectional email confirmation-as-a-service that promises to “save your time and money for successfully registering multiple accounts.”
“Are you working on large volumes and are costs constantly growing?” Kopeechka’s website asks. “Our service will solve all your problems.”
As a customer of this service, you don’t get full access to the email inboxes you are renting. Rather, you configure your botnet or spam machine to make an automated application programming interface (API) call to the Kopeechka service, which responds with a working email address at an email provider of your choosing.
Once you’ve entered the supplied email address into the new account registration page at some website or service, you tell Kopeechka which service or website you’re expecting an account confirmation link from, and they will then forward any new messages matching that description to your Kopeechka account panel.
Ensuring that customers cannot control inboxes rented through the service means that Kopeechka can rent the same email address to multiple customers (at least until that email address has been used to register accounts at most of the major online services).
Kopeechka also has multiple affiliate programs, including one that pays app developers for embedding Kopeechka’s API in their software. However, far more interesting is their program for rewarding people who choose to sell Kopeechka usernames and passwords for working email addresses.
Kopeechka means “penny” in Russian, which is generous verbiage (and coinage) for a service that charges a tiny fraction of a penny for access to account confirmation links. Their pricing fluctuates slightly based on which email provider you choose, but a form on the service’s homepage says a single confirmation message from apple.com to outlook.com costs .07 rubles, which is currently equal to about $0.00087 dollars.
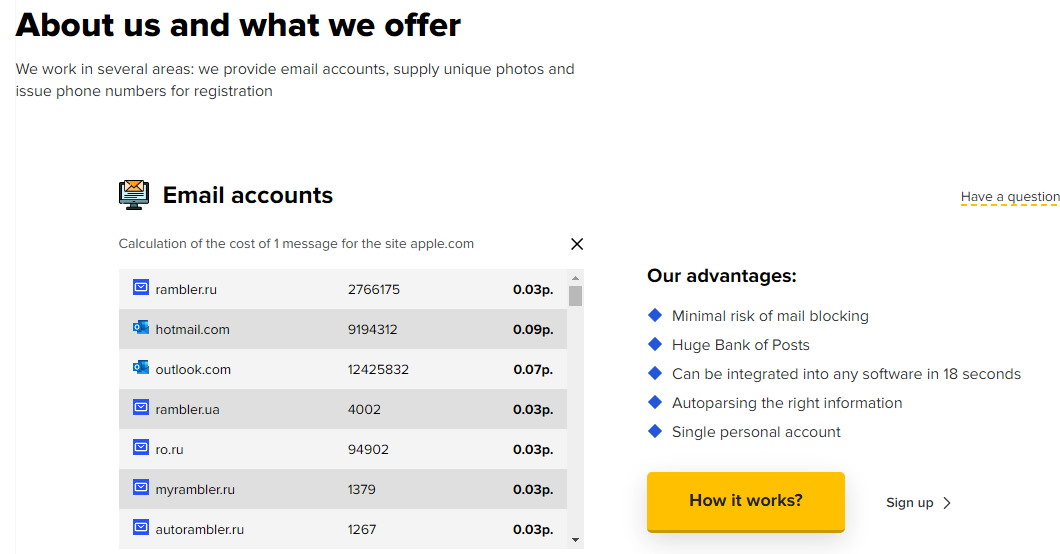
The pricing for Kopeechka works out to about a fraction of a penny per confirmation message.
“Emails can be uploaded to us for sale, and you will receive a percentage of purchases %,” the service explains. “You upload 1 mailbox of a certain domain, discuss percentage with our technical support (it depends on the liquidity of the domain and the number of downloaded emails).”
We don’t have to look very far for examples of Kopeechka in action. In May, KrebsOnSecurity interviewed a Russian spammer named “Quotpw“ who was mass-registering accounts on the social media network Mastodon in order to conduct a series of huge spam campaigns advertising scam cryptocurrency investment platforms.
Much of the fodder for that story came from Renaud Chaput, a freelance programmer working on modernizing and scaling the Mastodon project infrastructure — including joinmastodon.org, mastodon.online, and mastodon.social. Chaput told KrebsOnSecurity that his team was forced to temporarily halt all new registrations for these communities last month after the number of new registrations from Quotpw’s spam campaign started to overwhelm their systems.
“We suddenly went from like three registrations per minute to 900 a minute,” Chaput said. “There was nothing in the Mastodon software to detect that activity, and the protocol is not designed to handle this.”
After that story ran, Chaput said he discovered that the computer code powering Quotpw’s spam botnet (which has since been released as open source) contained an API call to Kopeechka’s service.
“It allows them to pool many bot-created or compromised emails at various providers and offer them to cyber criminals,” Chaput said of Kopeechka. “This is what they used to create thousands of valid Hotmail (and other) addresses when spamming on Mastodon. If you look at the code, it’s really well done with a nice API that forwards you the confirmation link that you can then fake click with your botnet.”
It’s doubtful anyone will make serious money selling email accounts to Kopeechka, unless of course that person already happens to run a botnet and has access to ridiculous numbers of email credentials. And in that sense, this service is genius: It essentially offers scammers a new way to wring extra income from resources that are already plentiful for them.
One final note about Quotpw and the spam botnet that ravaged Chaput’s Mastodon servers last month: Trend Micro just published a report saying Quotpw was spamming to earn money for a Russian-language affiliate program called “Impulse Team,” which pays people to promote cryptocurrency scams.
The crypto scam affiliate program “Project Impulse,” advertising in 2021.
Websites under the banner of the Impulse Scam Crypto Project are all essentially “advanced fee” scams that tell people they have earned a cryptocurrency investment credit. Upon registering at the site, visitors are told they need to make a minimum deposit on the service to collect the award. However, those who make the initial investment never hear from the site again, and their money is gone.
Interestingly, Trend Micro says the scammers behind the Impulse Team also appear to be operating a fake reputation service called Scam-Doc[.]com, a website that mimics the legitimate Scamdoc.com for measuring the trustworthiness and authenticity of various sites. Trend notes that the phony reputation site routinely gave high trust ratings to a variety of cryptocurrency scam and casino websites.
“We can only suppose that either the same cybercriminals run operations involving both or that several different cybercriminals share the scam-doc[.]com site,” the Trend researchers wrote.
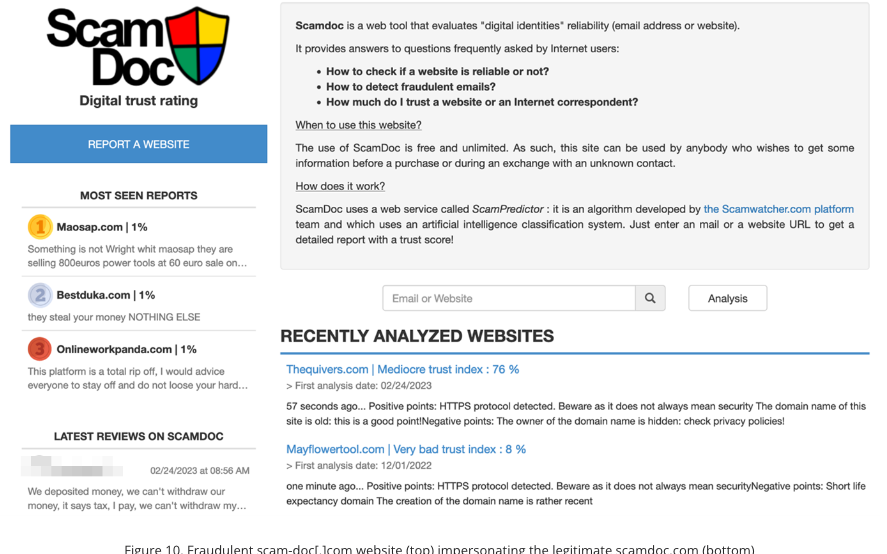
The ScamDoc fake reputation websites, which were apparently used to help make fake crypto investment platforms look more trustworthy. Image: Trend Micro.
According to the FBI, financial losses from cryptocurrency investment scams dwarfed losses for all other types of cybercrime in 2022, rising from $907 million in 2021 to $2.57 billion last year.


s3-ep137-feat-1200

Code-signing certificates are supposed to help authenticate the identity of software publishers, and provide cryptographic assurance that a signed piece of software has not been altered or tampered with. Both of these qualities make stolen or ill-gotten code-signing certificates attractive to cybercriminal groups, who prize their ability to add stealth and longevity to malicious software. This post is a deep dive on “Megatraffer,” a veteran Russian hacker who has practically cornered the underground market for malware focused code-signing certificates since 2015.
A review of Megatraffer’s posts on Russian crime forums shows this user began peddling individual stolen code-signing certs in 2015 on the Russian-language forum Exploit, and soon expanded to selling certificates for cryptographically signing applications and files designed to run in Microsoft Windows, Java, Adobe AIR, Mac and Microsoft Office.
Megatraffer explained that malware purveyors need a certificate because many antivirus products will be far more interested in unsigned software, and because signed files downloaded from the Internet don’t tend to get blocked by security features built into modern web browsers. Additionally, newer versions of Microsoft Windows will complain with a bright yellow or red alert message if users try to install a program that is not signed.
“Why do I need a certificate?” Megatraffer asked rhetorically in their Jan. 2016 sales thread on Exploit. “Antivirus software trusts signed programs more. For some types of software, a digital signature is mandatory.”
At the time, Megatraffer was selling unique code-signing certificates for $700 apiece, and charging more than twice that amount ($1,900) for an “extended validation” or EV code-signing cert, which is supposed to only come with additional identity vetting of the certificate holder. According to Megatraffer, EV certificates were a “must-have” if you wanted to sign malicious software or hardware drivers that would reliably work in newer Windows operating systems.
Part of Megatraffer’s ad. Image: Ke-la.com.
Megatraffer has continued to offer their code-signing services across more than a half-dozen other Russian-language cybercrime forums, mostly in the form of sporadically available EV and non-EV code-signing certificates from major vendors like Thawte and Comodo.
More recently, it appears Megatraffer has been working with ransomware groups to help improve the stealth of their malware. Shortly after Russia invaded Ukraine in February 2022, someone leaked several years of internal chat logs from the Conti ransomware gang, and those logs show Megatraffer was working with the group to help code-sign their malware between July and October 2020.
According to cyber intelligence firm Intel 471, Megatraffer has been active on more than a half-dozen crime forums from September 2009 to the present day. And on most of these identities, Megatraffer has used the email address 774748@gmail.com. That same email address also is tied to two forum accounts for a user with the handle “O.R.Z.”
Constella Intelligence, a company that tracks exposed databases, finds that 774748@gmail.com was used in connection with just a handful of passwords, but most frequently the password “featar24“. Pivoting off of that password reveals a handful of email addresses, including akafitis@gmail.com.
Intel 471 shows akafitis@gmail.com was used to register another O.R.Z. user account — this one on Verified[.]ru in 2008. Prior to that, akafitis@gmail.com was used as the email address for the account “Fitis,” which was active on Exploit between September 2006 and May 2007. Constella found the password “featar24” also was used in conjunction with the email address spampage@yandex.ru, which is tied to yet another O.R.Z. account on Carder[.]su from 2008.
The email address akafitis@gmail.com was used to create a Livejournal blog profile named Fitis that has a large bear as its avatar. In November 2009, Fitis wrote, “I am the perfect criminal. My fingerprints change beyond recognition every few days. At least my laptop is sure of it.”
Fitis’s Livejournal account. Image: Archive.org.
Fitis’s real-life identity was exposed in 2010 after two of the biggest sponsors of pharmaceutical spam went to war with each other, and large volumes of internal documents, emails and chat records seized from both spam empires were leaked to this author. That protracted and public conflict formed the backdrop of my 2014 book — “Spam Nation: The Inside Story of Organized Cybercrime, from Global Epidemic to Your Front Door.”
One of the leaked documents included a Microsoft Excel spreadsheet containing the real names, addresses, phone numbers, emails, street addresses and WebMoney addresses for dozens of top earners in Spamit — at the time the most successful pharmaceutical spam affiliate program in the Russian hacking scene and one that employed most of the top Russian botmasters.
That document shows Fitis was one of Spamit’s most prolific recruiters, bringing more than 75 affiliates to the Spamit program over several years prior to its implosion in 2010 (and earning commissions on any future sales from all 75 affiliates).
The document also says Fitis got paid using a WebMoney account that was created when its owner presented a valid Russian passport for a Konstantin Evgenievich Fetisov, born Nov. 16, 1982 and residing in Moscow. Russian motor vehicle records show two different vehicles are registered to this person at the same Moscow address.
The most interesting domain name registered to the email address spampage@yahoo.com, fittingly enough, is fitis[.]ru, which DomainTools.com says was registered in 2005 to a Konstantin E. Fetisov from Moscow.
The Wayback Machine at archive.org has a handful of mostly blank pages indexed for fitis[.]ru in its early years, but for a brief period in 2007 it appears this website was inadvertently exposing all of its file directories to the Internet.
One of the exposed files — Glavmed.html — is a general invitation to the infamous Glavmed pharmacy affiliate program, a now-defunct scheme that paid tens of millions of dollars to affiliates who advertised online pill shops mainly by hacking websites and manipulating search engine results. Glavmed was operated by the same Russian cybercriminals who ran the Spamit program.

A Google translated ad circa 2007 recruiting for the pharmacy affiliate program Glavmed, which told interested applicants to contact the ICQ number used by Fitis, a.k.a. MegaTraffer. Image: Archive.org.
Archive.org shows the fitis[.]ru webpage with the Glavmed invitation was continuously updated with new invite codes. In their message to would-be Glavmed affiliates, the program administrator asked applicants to contact them at the ICQ number 165540027, which Intel 471 found was an instant messenger address previously used by Fitis on Exploit.
The exposed files in the archived version of fitis[.]ru include source code for malicious software, lists of compromised websites used for pharmacy spam, and a handful of what are apparently personal files and photos. Among the photos is a 2007 image labeled merely “fitis.jpg,” which shows a bespectacled, bearded young man with a ponytail standing next to what appears to be a newly-married couple at a wedding ceremony.
Mr. Fetisov did not respond to requests for comment.
As a veteran organizer of affiliate programs, Fitis did not waste much time building a new moneymaking collective after Spamit closed up shop. New York City-based cyber intelligence firm Flashpoint found that Megatraffer’s ICQ was the contact number for Himba[.]ru, a cost-per-acquisition (CPA) program launched in 2012 that paid handsomely for completed application forms tied to a variety of financial instruments, including consumer credit cards, insurance policies, and loans.
“Megatraffer’s entrenched presence on cybercrime forums strongly suggests that malicious means are used to source at least a portion of traffic delivered to HIMBA’s advertisers,” Flashpoint observed in a threat report on the actor.
Intel 471 finds that Himba was an active affiliate program until around May 2019, when it stopping paying its associates.

Fitis’s Himba affiliate program, circa February 2014. Image: Archive.org.
Flashpoint notes that in September 2015, Megatraffer posted a job ad on Exploit seeking experienced coders to work on browser plugins, installers and “loaders” — basically remote access trojans (RATs) that establish communication between the attacker and a compromised system.
“The actor specified that he is looking for full-time, onsite help either in his Moscow or Kiev locations,” Flashpoint wrote.
A peek under the hood of a cybercrime operation and what you can do to avoid being an easy target for similar ploys
The post Tricks of the trade: How a cybercrime ring operated a multi‑level fraud scheme appeared first on WeLiveSecurity