Infosec in brief Google Cloud has fixed an issue in which it gave away a little too much info in its audit logs to a service account.…
Will update when exploit PoC available.
A stolen Microsoft security key may have allowed Beijing-backed spies to break into a lot more than just Outlook and Exchange Online email accounts.…
VirusTotal today issued a mea culpa, saying a blunder earlier this week by one of its staff exposed information belonging to 5,600 customers, including the email addresses of US Cyber Command, FBI, and NSA employees.…
Many things have changed since 2018, such as the names of the companies in the Fortune 100 list. But one aspect of that vaunted list that hasn’t shifted much since is that very few of these companies list any security professionals within their top executive ranks.

The next time you receive a breach notification letter that invariably says a company you trusted places a top priority on customer security and privacy, consider this: Only five of the Fortune 100 companies currently list a security professional in the executive leadership pages of their websites. This is largely unchanged from five of the Fortune 100 in 2018, the last time KrebsOnSecurity performed this analysis.
A review of the executives pages published by the 2022 list of Fortune 100 companies found only five — BestBuy, Cigna, Coca-Cola, Disney and Walmart — that listed a Chief Security Officer (CSO) or Chief Information Security Officer (CISO) in their highest corporate ranks.
One-third of last year’s Fortune 100 companies included a Chief Technology Officer (CTO) in their executive stables; 40 listed Chief Information Officer (CIO) roles, but just 21 included a Chief Risk Officer (CRO).
As I noted in 2018, this is not to say that 95 percent of the Fortune 100 companies don’t have a CISO or CSO in their employ: A review of LinkedIn suggests that most of them in fact do have people in those roles, and experts say some of the largest multinational companies will have multiple people in these positions.
But it is interesting to note which executive positions the top companies deem worth publishing in their executive leadership pages. For example, 88 percent listed a Director of Human Resources (or “Chief People Officer”), and 37 out of 100 included a Chief Marketing Officer.
Not that these roles are somehow more or less important than that of a CISO/CSO within the organization. Nor is the average pay hugely different among all these roles. Yet, considering how much marketing (think consumer/customer data) and human resources (think employee personal/financial data) are impacted by your average data breach, it’s somewhat remarkable that more companies don’t list their chief security personnel among their top ranks.
One likely explanation as to why a great many companies still don’t include their security leaders within their highest echelons is that these employees do not report directly to the company’s CEO, board of directors, or Chief Risk Officer.
The CSO or CISO position traditionally has reported to an executive in a technical role, such as the CTO or CIO. But workforce experts say placing the CISO/CSO on unequal footing with the organization’s top leaders makes it more likely that cybersecurity and risk concerns will take a backseat to initiatives designed to increase productivity and generally grow the business.
“Separation of duties is a fundamental concept of security, whether we’re talking about cyber threats, employee fraud, or physical theft,” said Tari Schreider, an analyst with Datos Insights. “But that critical separation is violated every day with the CISO or CSO reporting to the heads of technology.”
IANS, an organization geared toward CISOs/CSOs and their teams, surveyed more than 500 organizations last year and found roughly 65 percent of CISOs still report to a technical leader, such as the CTO or CIO: IANS found 46 percent of CISOs reported to a CIO, with 15 percent reporting directly to a CTO.
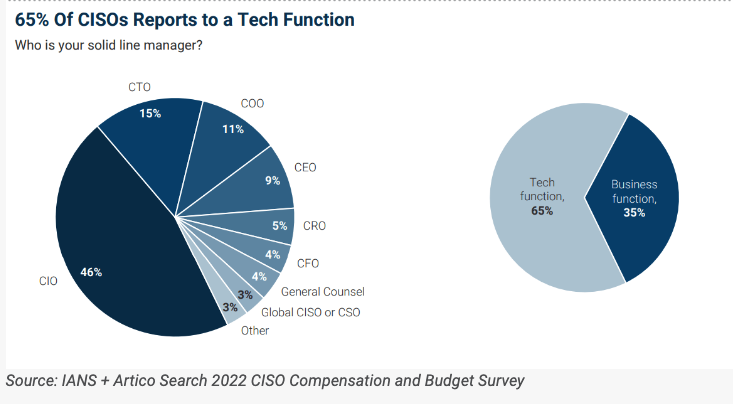
A survey last year by IANS found 65 percent of CISOs report to a tech function within organizations, such as the CTO or CIO. Image: IANS Research.
Schreider said one big reason many CISOs and CSOs aren’t listed in corporate executive biographies at major companies is that these positions often do not enjoy the same legal and insurance protections afforded to other officers within the company.
Typically, larger companies will purchase a “Directors and Officers” liability policy that covers legal expenses should one of the organization’s top executives find themselves dragged into court over some business failing on the part of their employer. But organizations that do not offer this coverage to their security leaders are unlikely to list those positions in their highest ranks, Schreider said.
“It’s frankly shocking,” Schreider said, upon hearing that only four of the Fortune 100 listed any security personnel in their top executive hierarchies. “If the company isn’t going to give them legal cover, then why give them the responsibility for security? Especially when CISOs and CSOs shouldn’t own the risk, yet the majority of them carry the mantle of responsibility and they tend to be scapegoats” when the organization eventually gets hacked, he said.
Schreider said while Datos Insights focuses mostly on the financial and insurance industries, a recent Datos survey echoes the IANS findings from last year. Datos surveyed 25 of the largest financial institutions by asset size (two of which are no longer in existence), and found just 22 percent of CSOs/CISOs reported to the CEO. A majority — 65 percent — had their CSOs/CISOs reporting to either a CTO or CIO.
“I’ve looked at these types of statistics for years and they’ve never really changed that much,” Schreider said. “The CISO or CSO is in the purview of the technical stack from a management perspective. Right, wrong or indifferent, that’s what’s happening.”
Earlier this year, IT consulting firm Accenture released results from surveying more than 3,000 respondents from 15 industries across 14 countries about their security maturity levels. Accenture found that only about one-third of the organizations they surveyed had enough security maturity under their belts to have integrated security into virtually every aspect of their businesses — and this includes having CISOs or CSOs report to someone in charge of overseeing risk for the business as a whole.
Not surprisingly, Accenture also found that only a third of respondents considered cybersecurity risk “to a great extent” when evaluating overall enterprise risk.
“This highlights there is still some way to go to make cybersecurity a proactive, strategic necessity within the business,” the report concluded.
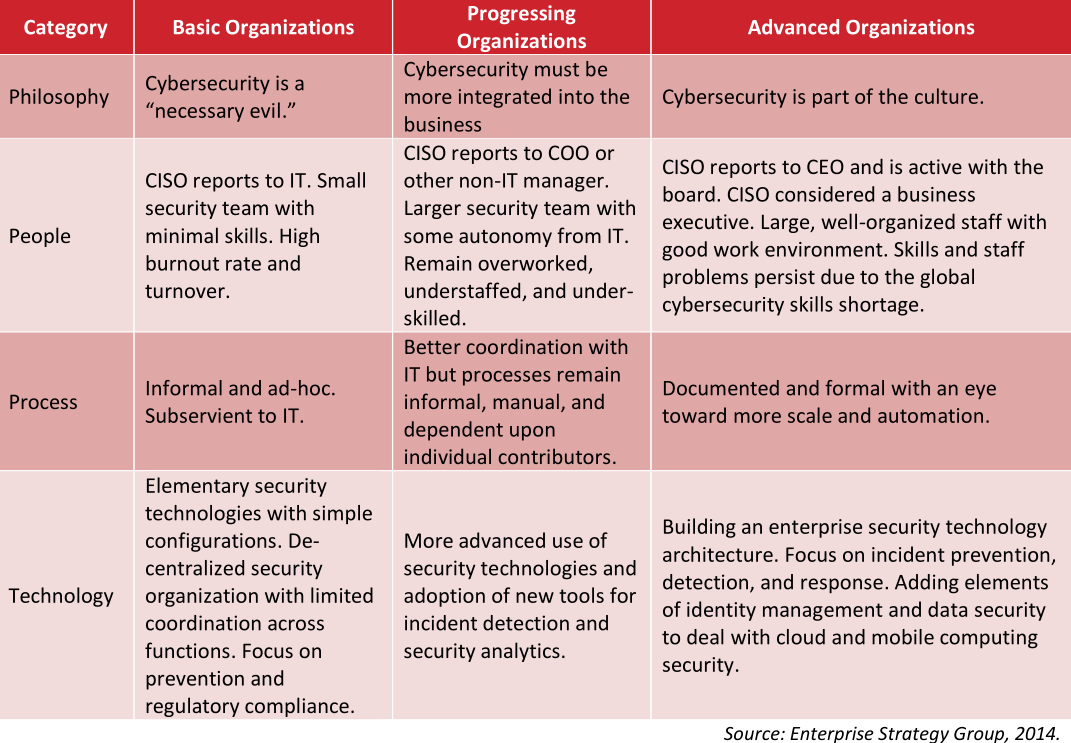
One way of depicting the different stages of security maturity.
A spreadsheet tracking the prevalence of security leaders on the executive pages of the 2022 Fortune 100 firms is available here.
Update, July 23: Somehow overlooked Disney’s CSO listed on their leadership page. The story copy above has been updated to reflect that.
Hey all,
I help maintain dnsReaper which is a subdomain takeover tool. It's free, available on GitHub and docker and looks for domains vulnerable to domain takeovers.
Today we've added 2 new integrations!
Project discovery have a massive database of subdomains called CHAOS and you can now query and test domains in dnsReaper.
We've also added SecurityTrails, which also has a huge public subdomain list.
This means that you can just point dnsReaper at a bug bounty domain and let it run. There will be false positives for sure, but we have 61 signatures so hopefully there will be some nice easy findings too.
Our blog post on the new features is here:
https://punksecurity.co.uk/blog/dnsreaper_pd/
Our GitHub is over here:
https://github.com/punk-security/dnsReaper
It's a free tool that we built just to highlight this issue and educate. Please give it a star and share it, we'd appreciate it.