




Domain searches in HIBP - that's the story this week - and I'm grateful for all the feedback I've received. I've had a few messages in particular since this live stream where people gave me some really excellent feedback to the point where I've now got a much clearer plan in head as to what this will look like. I need to keep writing code, revising the draft blog post to announce it then sometime in hopefully about a month, push it all live. What I'm zero'ing in on now is a free tier that covers most domains, a very low entry fee for almost every personal or small business case you can think of and then a few tiers above that to cover the rest. Do keep that feedback coming, it's all read, it's all taken onboard and I'm responding to absolutely everyone that sends it to me. If you're one of those people, thank you 😊

I spent most of this week's update on the tweaking I went through with Azure's API Management service and then using Cloudflare to stop a whole bunch of requests that really didn't need to go all the way to the origin (or at least all the way to the API gateway sitting in front of the origin Azure Function instance). I'm still blown away by how cool this is - tweak the firewall via a web UI to inspect traffic and respond differently based on a combination of headers and response codes and bam! A massive reduction in unnecessary traffic follows. That's so cool, I love cloud 😊


And so ends a long period of back-to-back weeks of conferences and talks. It's funny how these things seem to cluster together at times and whilst the last 6 or 8 weeks (I honestly lose track!) have been chaotic, I've now got a few weeks of much less pressure which will give me time to finally push out some HIBP stuff that's been in the wings for ages. I've just got to get through this weekend first, stay tuned for pics on social for that, it's going to be pretty epic 😎

This week's update is dominated by my experience with "Lena", the scammer from Gumtree who tried to fleece my wife of $800. There's a blow-by-blow rundown of how it all happened in this video and it's fascinating to think that these things can actually be successful given all the red flags. But they are, and in Australia alone innocent victims are stung to the tune of more than 3 billion dollars every year by fraudsters which is a staggering number. Understanding how these scams work and sharing that knowledge broadly with the less technical of those around us is part of how to combat this, so please share the tweet thread generously... and enjoy the entertainment 😊

The number of phishing websites tied to domain name registrar Freenom dropped precipitously in the months surrounding a recent lawsuit from social networking giant Meta, which alleged the free domain name provider has a long history of ignoring abuse complaints about phishing websites while monetizing traffic to those abusive domains.
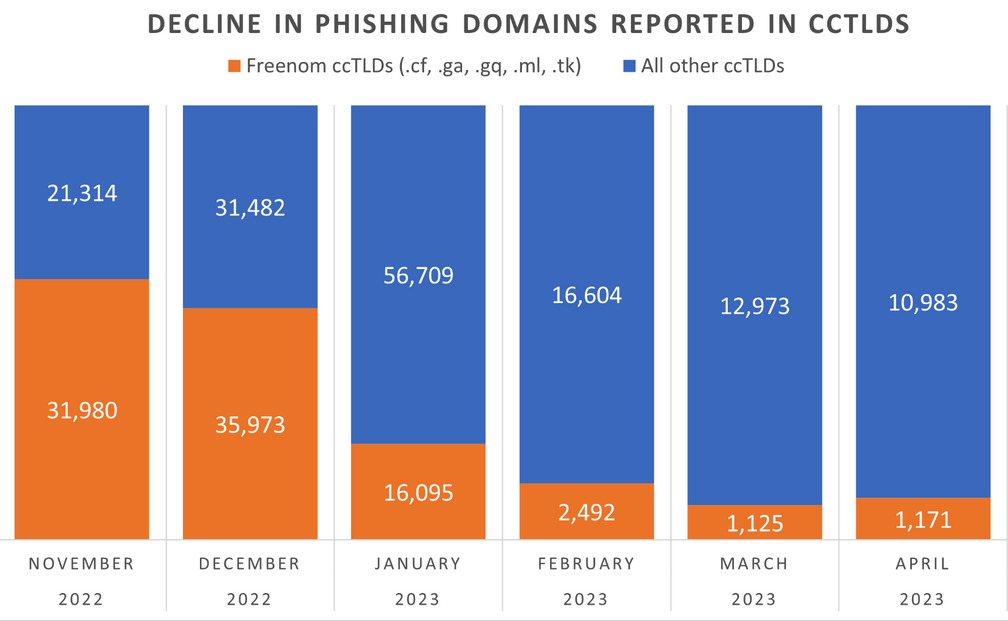
The volume of phishing websites registered through Freenom dropped considerably since the registrar was sued by Meta. Image: Interisle Consulting.
Freenom is the domain name registry service provider for five so-called “country code top level domains” (ccTLDs), including .cf for the Central African Republic; .ga for Gabon; .gq for Equatorial Guinea; .ml for Mali; and .tk for Tokelau.
Freenom has always waived the registration fees for domains in these country-code domains, but the registrar also reserves the right to take back free domains at any time, and to divert traffic to other sites — including adult websites. And there are countless reports from Freenom users who’ve seen free domains removed from their control and forwarded to other websites.
By the time Meta initially filed its lawsuit in December 2022, Freenom was the source of well more than half of all new phishing domains coming from country-code top-level domains. Meta initially asked a court to seal its case against Freenom, but that request was denied. Meta withdrew its December 2022 lawsuit and re-filed it in March 2023.
“The five ccTLDs to which Freenom provides its services are the TLDs of choice for cybercriminals because Freenom provides free domain name registration services and shields its customers’ identity, even after being presented with evidence that the domain names are being used for illegal purposes,” Meta’s complaint charged. “Even after receiving notices of infringement or phishing by its customers, Freenom continues to license new infringing domain names to those same customers.”
Meta pointed to research from Interisle Consulting Group, which discovered in 2021 and again last year that the five ccTLDs operated by Freenom made up half of the Top Ten TLDs most abused by phishers.
Interisle partner Dave Piscitello said something remarkable has happened in the months since the Meta lawsuit.
“We’ve observed a significant decline in phishing domains reported in the Freenom commercialized ccTLDs in months surrounding the lawsuit,” Piscitello wrote on Mastodon. “Responsible for over 60% of phishing domains reported in November 2022, Freenom’s percentage has dropped to under 15%.”
Interisle collects data from 12 major blocklists for spam, malware, and phishing, and it receives phishing-specific data from Spamhaus, Phishtank, OpenPhish and the APWG Ecrime Exchange. The company publishes historical data sets quarterly, both on malware and phishing.
Piscitello said it’s too soon to tell the full impact of the Freenom lawsuit, noting that Interisle’s sources of spam and phishing data all have different policies about when domains are removed from their block lists.
“One of the things we don’t have visibility into is how each of the blocklists determine to remove a URL from their lists,” he said. “Some of them time out [listed domains] after 14 days, some do it after 30, and some keep them forever.”
Freenom did not respond to requests for comment.
This is the second time in as many years that a lawsuit by Meta against a domain registrar has disrupted the phishing industry. In March 2020, Meta sued domain registrar giant Namecheap, alleging cybersquatting and trademark infringement.
The two parties settled the matter in April 2022. While the terms of that settlement have not been disclosed, new phishing domains registered through Namecheap declined more than 50 percent the following quarter, Interisle found.
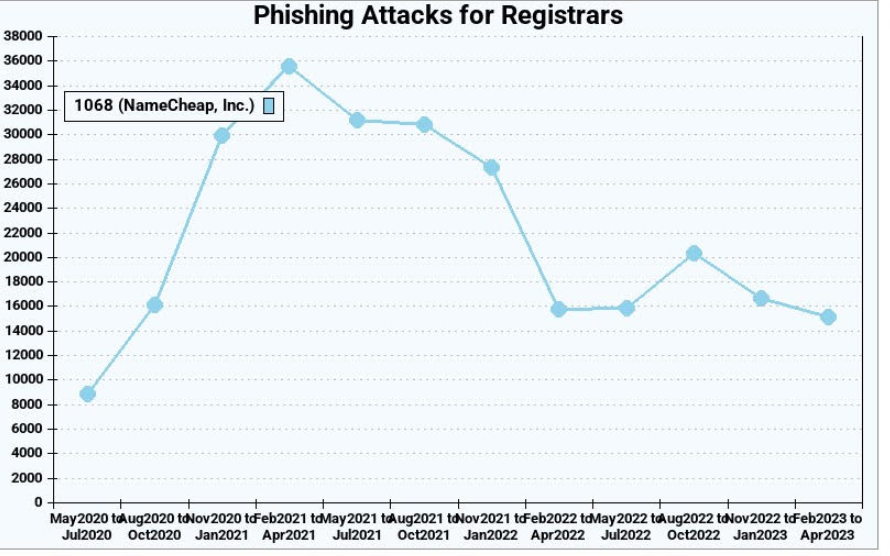
Phishing attacks using websites registered through Namecheap, before and after the registrar settled a lawsuit with Meta. Image: Interisle Consulting.
Unfortunately, the lawsuits have had little effect on the overall number of phishing attacks and phishing-related domains, which have steadily increased in volume over the years. Piscitello said the phishers tend to gravitate toward registrars that offer the least resistance and lowest price per domain. And with new top-level domains constantly being introduced, there is rarely a shortage of super low-priced domains.
“The abuse of a new top-level domain is largely the result of one registrar’s portfolio,” Piscitello told KrebsOnSecurity. “Alibaba or Namecheap or another registrar will run a promotion for a cheap domain, and then we’ll see flocking and migration of the phishers to that TLD. It’s like strip mining, where they’ll buy hundreds or thousands of domains, use those in a campaign, exhaust that TLD and then move on to another provider.”
Piscitello said despite the steep drop in phishing domains coming out of Freenom, the alternatives available to phishers are many. After all, there are more than 2,000 accredited domain registrars, not to mention dozens of services that let anyone set up a website for free without even owning a domain.
“There is no evidence that the trend line is even going to level off,” he said. “I think what the Meta lawsuit tells us is that litigation is like giving someone a standing eight count. It temporarily disrupts a process. And in that sense, litigation appears to be working.”






Social networks are constantly battling inauthentic bot accounts that send direct messages to users promoting scam cryptocurrency investment platforms. What follows is an interview with a Russian hacker responsible for a series of aggressive crypto spam campaigns that recently prompted several large Mastodon communities to temporarily halt new registrations. According to the hacker, their spam software has been in private use until the last few weeks, when it was released as open source code.

Renaud Chaput is a freelance programmer working on modernizing and scaling the Mastodon project infrastructure — including joinmastodon.org, mastodon.online, and mastodon.social. Chaput said that on May 4, 2023, someone unleashed a spam torrent targeting users on these Mastodon communities via “private mentions,” a kind of direct messaging on the platform.
The messages said recipients had earned an investment credit at a cryptocurrency trading platform called moonxtrade[.]com. Chaput said the spammers used more than 1,500 Internet addresses across 400 providers to register new accounts, which then followed popular accounts on Mastodon and sent private mentions to the followers of those accounts.
Since then, the same spammers have used this method to advertise more than 100 different crypto investment-themed domains. Chaput said that at one point this month the volume of bot accounts being registered for the crypto spam campaign started overwhelming the servers that handle new signups at Mastodon.social.
“We suddenly went from like three registrations per minute to 900 a minute,” Chaput said. “There was nothing in the Mastodon software to detect that activity, and the protocol is not designed to handle this.”

One of the crypto investment scam messages promoted in the spam campaigns on Mastodon this month.
Seeking to gain a temporary handle on the spam wave, Chaput said he briefly disabled new account registrations on mastodon.social and mastondon.online. Shortly after that, those same servers came under a sustained distributed denial-of-service (DDoS) attack.
Chaput said whoever was behind the DDoS was definitely not using point-and-click DDoS tools, like a booter or stresser service.
“This was three hours non-stop, 200,000 to 400,000 requests per second,” Chaput said of the DDoS. “At first, they were targeting one path, and when we blocked that they started to randomize things. Over three hours the attack evolved several times.”
Chaput says the spam waves have died down since they retrofitted mastodon.social with a CAPTCHA, those squiggly letter and number combinations designed to stymie automated account creation tools. But he’s worried that other Mastodon instances may not be as well-staffed and might be easy prey for these spammers.
“We don’t know if this is the work of one person, or if this is [related to] software or services being sold to others,” Chaput told KrebsOnSecurity. “We’re really impressed by the scale of it — using hundreds of domains and thousands of Microsoft email addresses.”
Chaput said a review of their logs indicates many of the newly registered Mastodon spam accounts were registered using the same 0auth credentials, and that a domain common to those credentials was quot[.]pw.
The domain quot[.]pw has been registered and abandoned by several parties since 2014, but the most recent registration data available through DomainTools.com shows it was registered in March 2020 to someone in Krasnodar, Russia with the email address edgard011012@gmail.com.
This email address is also connected to accounts on several Russian cybercrime forums, including “__edman__,” who had a history of selling “logs” — large amounts of data stolen from many bot-infected computers — as well as giving away access to hacked Internet of Things (IoT) devices.
In September 2018, a user by the name “ципа” (phonetically “Zipper” in Russian) registered on the Russian hacking forum Lolzteam using the edgard0111012@gmail.com address. In May 2020, Zipper told another Lolzteam member that quot[.]pw was their domain. That user advertised a service called “Quot Project” which said they could be hired to write programming scripts in Python and C++.
“I make Telegram bots and other rubbish cheaply,” reads one February 2020 sales thread from Zipper.
Clicking the “open chat in Telegram” button on Zipper’s Lolzteam profile page launched a Telegram instant message chat window where the user Quotpw responded almost immediately. Asked if they were aware their domain was being used to manage a spam botnet that was pelting Mastodon instances with crypto scam spam, Quotpw confirmed the spam was powered by their software.
“It was made for a limited circle of people,” Quotpw said, noting that they recently released the bot software as open source on GitHub.
Quotpw went on to say the spam botnet was powered by well more than the hundreds of IP addresses tracked by Chaput, and that these systems were mostly residential proxies. A residential proxy generally refers to a computer or mobile device running some type of software that enables the system to be used as a pass-through for Internet traffic from others.
Very often, this proxy software is installed surreptitiously, such as through a “Free VPN” service or mobile app. Residential proxies also can refer to households protected by compromised home routers running factory-default credentials or outdated firmware.
Quotpw maintains they have earned more than $2,000 sending roughly 100,000 private mentions to users of different Mastodon communities over the past few weeks. Quotpw said their conversion rate for the same bot-powered direct message spam on Twitter is usually much higher and more profitable, although they conceded that recent adjustments to Twitter’s anti-bot CAPTCHA have put a crimp in their Twitter earnings.
“My partners (I’m programmer) lost time and money while ArkoseLabs (funcaptcha) introduced new precautions on Twitter,” Quotpw wrote in a Telegram reply. “On Twitter, more spam and crypto scam.”
Asked whether they felt at all conflicted about spamming people with invitations to cryptocurrency scams, Quotpw said in their hometown “they pay more for such work than in ‘white’ jobs” — referring to legitimate programming jobs that don’t involve malware, botnets, spams and scams.
“Consider salaries in Russia,” Quotpw said. “Any spam is made for profit and brings illegal money to spammers.”
Shortly after edgard011012@gmail.com registered quot[.]pw, the WHOIS registration records for the domain were changed again, to msr-sergey2015@yandex.ru, and to a phone number in Austria: +43.6607003748.
Constella Intelligence, a company that tracks breached data, finds that the address msr-sergey2015@yandex.ru has been associated with accounts at the mobile app site aptoide.com (user: CoolappsforAndroid) and vimeworld.ru that were created from different Internet addresses in Vienna, Austria.
A search in Skype on that Austrian phone number shows it belongs to a Sergey Proshutinskiy who lists his location as Vienna, Austria. The very first result that comes up when one searches that unusual name in Google is a LinkedIn profile for a Sergey Proshutinskiy from Vienna, Austria.
Proshutinskiy’s LinkedIn profile says he is a Class of 2024 student at TGM, which is a state-owned, technical and engineering school in Austria. His resume also says he is a data science intern at Mondi Group, an Austrian manufacturer of sustainable packaging and paper.
Mr. Proshutinskiy did not respond to requests for comment.
Quotpw denied being Sergey, and said Sergey was a friend who registered the domain as a birthday present and favor last year.
“Initially, I bought it for 300 rubles,” Quotpw explained. “The extension cost 1300 rubles (expensive). I waited until it expired and forgot to buy it. After that, a friend (Sergey) bought [the] domain and transferred access rights to me.”
“He’s not even an information security specialist,” Quotpw said of Sergey. “My friends do not belong to this field. None of my friends are engaged in scams or other black [hat] activities.”
It may seem unlikely that someone would go to all this trouble to spam Mastodon users over several weeks using an impressive number of resources — all for just $2,000 in profit. But it is likely that whoever is actually running the various crypto scam platforms advertised by Quotpw’s spam messages pays handsomely for any investments generated by their spam.
According to the FBI, financial losses from cryptocurrency investment scams dwarfed losses for all other types of cybercrime in 2022, rising from $907 million in 2021 to $2.57 billion last year.
Update, May 25, 10:30 a.m.: Corrected attribution of the Austrian school TGM.

I feel like the .zip TLD debate is one of those cases where it's very easy for the purest security view to overwhelm the practical human reality. I'm yet to see a single good argument that is likely to have real world consequences as far as phishing goes and whilst I understand the sentiment surrounding the confusion new TLDs with common file types, all "the sky is falling" commentary I've seen is speculative at best. But hey, there's no rolling it back now, we can start judging by what actually happens with the TLD rather than sitting around creating misuse hypotheses.


A late one this week as I cover from the non-stop conferencing that was the Azure user group in Perth, followed by the Cyber West keynote, then the social drinks that night, the flight back home straight into the AusCERT gala dinner, the panel on data governance that morning then wrapping up with the speed debate Friday arvo. I think that's all... Anyway, better later than never and nothing too serious in this week's update. Personally, I'm finding the house works the most fun to talk about so I'm going to hit the publish button on this post now then go back to drafting the blog series on everything we've done 😊





It's a bit of a mixed bag this week with a very light-hearted look at the death of the browser padlock icon (which has been replaced by an icon that looks like a sex act), and a much more serious discussion about divorce. It took a long time to write and be ready to publish that blog post, many years in fact, but I'm so glad I did. You don't have to scroll far through the responses to the launch tweet or the comments on the blog itself to get a sense of how it's impacted people, and as I said in the very opening of the post, this sort of openness tends to be really well received. Wherever you are in your own stage of life, I hope you enjoying reading that post and share it generously with those for whom it might just make a real difference.

A sprawling online company based in Georgia that has made tens of millions of dollars purporting to sell access to jobs at the United States Postal Service (USPS) has exposed its internal IT operations and database of nearly 900,000 customers. The leaked records indicate the network’s chief technology officer in Pakistan has been hacked for the past year, and that the entire operation was created by the principals of a Tennessee-based telemarketing firm that has promoted USPS employment websites since 2016.
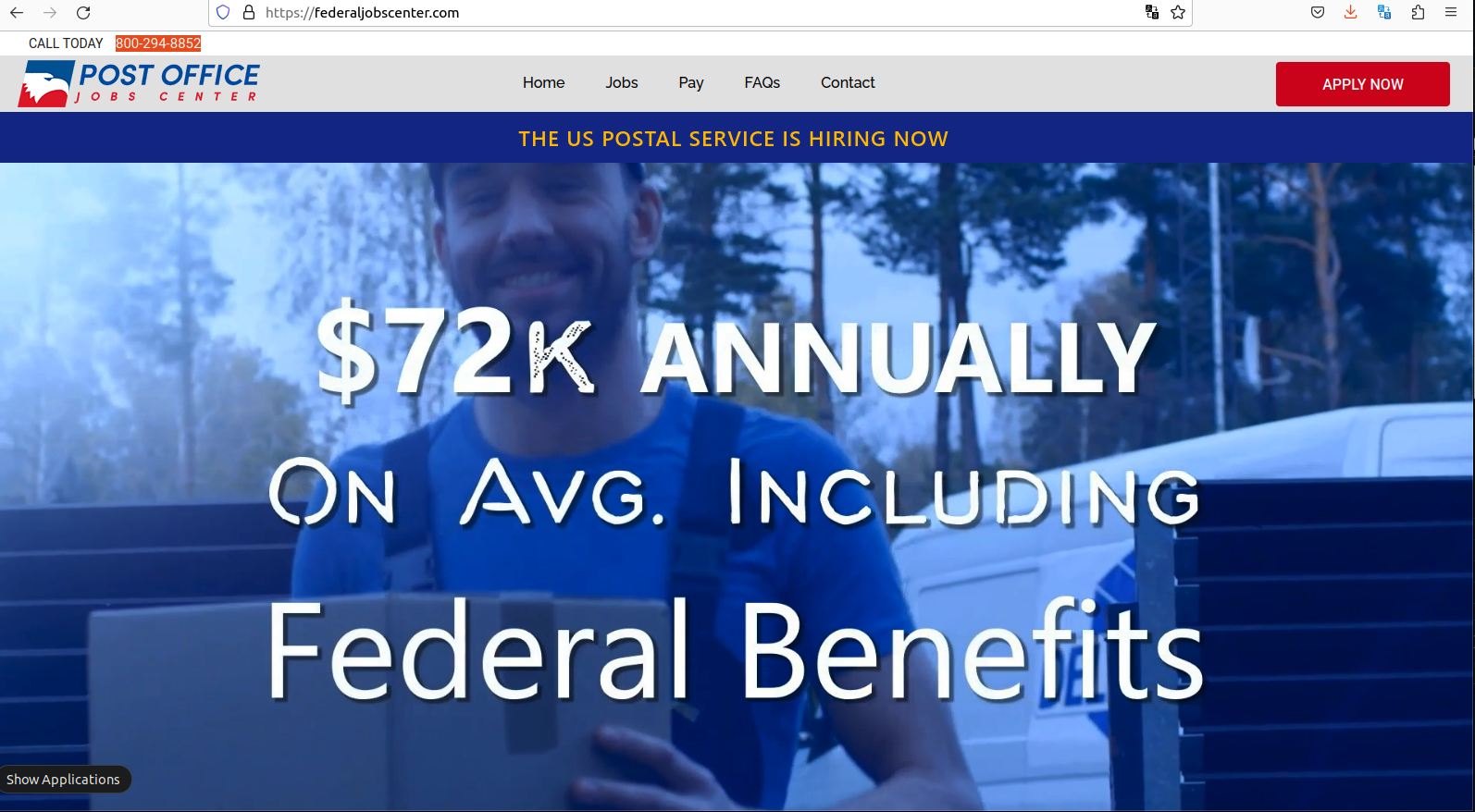
The website FederalJobsCenter promises to get you a job at the USPS in 30 days or your money back.
KrebsOnSecurity was recently contacted by a security researcher who said he found a huge tranche of full credit card records exposed online, and that at first glance the domain names involved appeared to be affiliated with the USPS.
Further investigation revealed a long-running international operation that has been emailing and text messaging people for years to sign up at a slew of websites that all promise they can help visitors secure employment at the USPS.
Sites like FederalJobsCenter[.]com also show up prominently in Google search results for USPS employment, and steer applicants toward making credit card “registration deposits” to ensure that one’s application for employment is reviewed. These sites also sell training, supposedly to help ace an interview with USPS human resources.
FederalJobsCenter’s website is full of content that makes it appear the site is affiliated with the USPS, although its “terms and conditions” state that it is not. Rather, the terms state that FederalJobsCenter is affiliated with an entity called US Job Services, which says it is based in Lawrenceville, Ga.
“US Job Services provides guidance, coaching, and live assistance to postal job candidates to help them perform better in each of the steps,” the website explains.
The site says applicants need to make a credit card deposit to register, and that this amount is refundable if the applicant is not offered a USPS job within 30 days after the interview process.
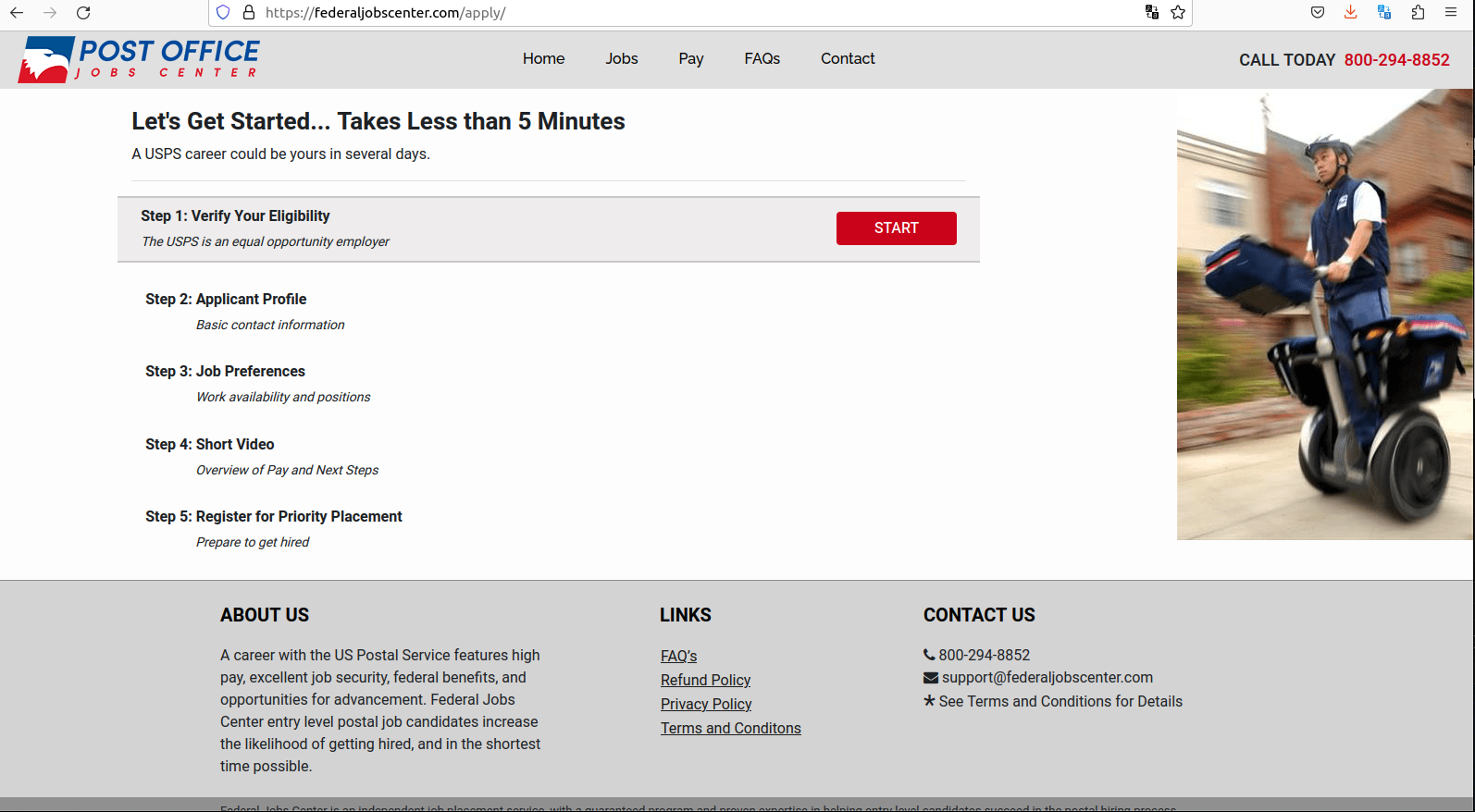
But a review of the public feedback on US Job Services and dozens of similar names connected to this entity over the years shows a pattern of activity: Applicants pay between $39.99 and $100 for USPS job coaching services, and receive little if anything in return. Some reported being charged the same amount monthly.
The U.S. Federal Trade Commission (FTC) has sued several times over the years to disrupt various schemes offering to help people get jobs at the Postal Service. Way back in 1998, the FTC and the USPS took action against several organizations that were selling test or interview preparation services for potential USPS employees.
“Companies promising jobs with the U.S. Postal Service are breaking federal law,” the joint USPS-FTC statement said.
In that 1998 case, the defendants behind the scheme were taking out classified ads in newspapers. Ditto for a case the FTC brought in 2005. By 2008, the USPS job exam preppers had shifted to advertising their schemes mostly online. And in 2013, the FTC won a nearly $5 million judgment against a Kentucky company purporting to offer such services.
Tim McKinlay authored a report last year at Affiliateunguru.com on whether the US Job Services website job-postal[.]com was legitimate or a scam. He concluded it was a scam based on several factors, including that the website listed multiple other names (suggesting it had recently switched names), and that he got nothing from the transaction with the job site.
“They openly admit they’re not affiliated with the US Postal Service, but claim to be experts in the field, and that, just by following the steps on their site, you easily pass the postal exams and get a job in no time,” McKinlay wrote. “But it’s really just a smoke and mirrors game. The site’s true purpose is to collect $46.95 from as many people as possible. And considering how popular this job is, they’re probably making a killing.”
KrebsOnSecurity was alerted to the data exposure by Patrick Barry, chief information officer at Charlotte, NC based Rebyc Security. Barry said he found that not only was US Job Services leaking its customer payment records in real-time and going back to 2016, but its website also leaked a log file from 2019 containing the site administrator’s contact information and credentials to the site’s back-end database.
Barry shared screenshots of that back-end database, which show the email address for the administrator of US Job Services is tab.webcoder@gmail.com. According to cyber intelligence platform Constella Intelligence, that email address is tied to the LinkedIn profile for a developer in Karachi, Pakistan named Muhammed Tabish Mirza.
A search on tab.webcoder@gmail.com at DomainTools.com reveals that email address was used to register several USPS-themed domains, including postal2017[.]com, postaljobscenter[.]com and usps-jobs[.]com.
Mr. Mirza declined to respond to questions, but the exposed database information was removed from the Internet almost immediately after KrebsOnSecurity shared the offending links.
A “Campaigns” tab on that web panel listed several advertising initiatives tied to US Job Services websites, with names like “walmart drip campaign,” “hiring activity due to virus,” “opt-in job alert SMS,” and “postal job opening.”
Another page on the US Job Services panel included a script for upselling people who call in response to email and text message solicitations, with an add-on program that normally sells for $1,200 but is being “practically given away” for a limited time, for just $49.
“There’s something else we have you can take advantage of that can help you make more money,” the script volunteers. “It’s an easy to use 12-month career development plan and program to follow that will result in you getting any job you want, not just at the post office….anywhere…and then getting promoted rapidly.”
It’s bad enough that US Job Services was leaking customer data: Constella Intelligence says the email address tied to Mr. Mirza shows up in more than a year’s worth of “bot logs” created by a malware infection from the Redline infostealer.
Constella reports that for roughly a year between 2021 and 2022, a Microsoft Windows device regularly used by Mr. Mirza and his colleagues was actively uploading all of the device’s usernames, passwords and authentication cookies to cybercriminals based in Russia.
The web-based backend for US Job Services lists more than 160 people under its “Users & Teams” tab. This page indicates that access to the consumer and payment data collected by US Job Services is currently granted to several other coders who work with Mr. Mirza in Pakistan, and to multiple executives, contractors and employees working for a call center in Murfreesboro, Tennessee.
The call center — which operates as Nextlevelsupportcenters[.]com and thenextlevelsupport[.]com — curiously has several key associates with a history of registering USPS jobs-related domain names.
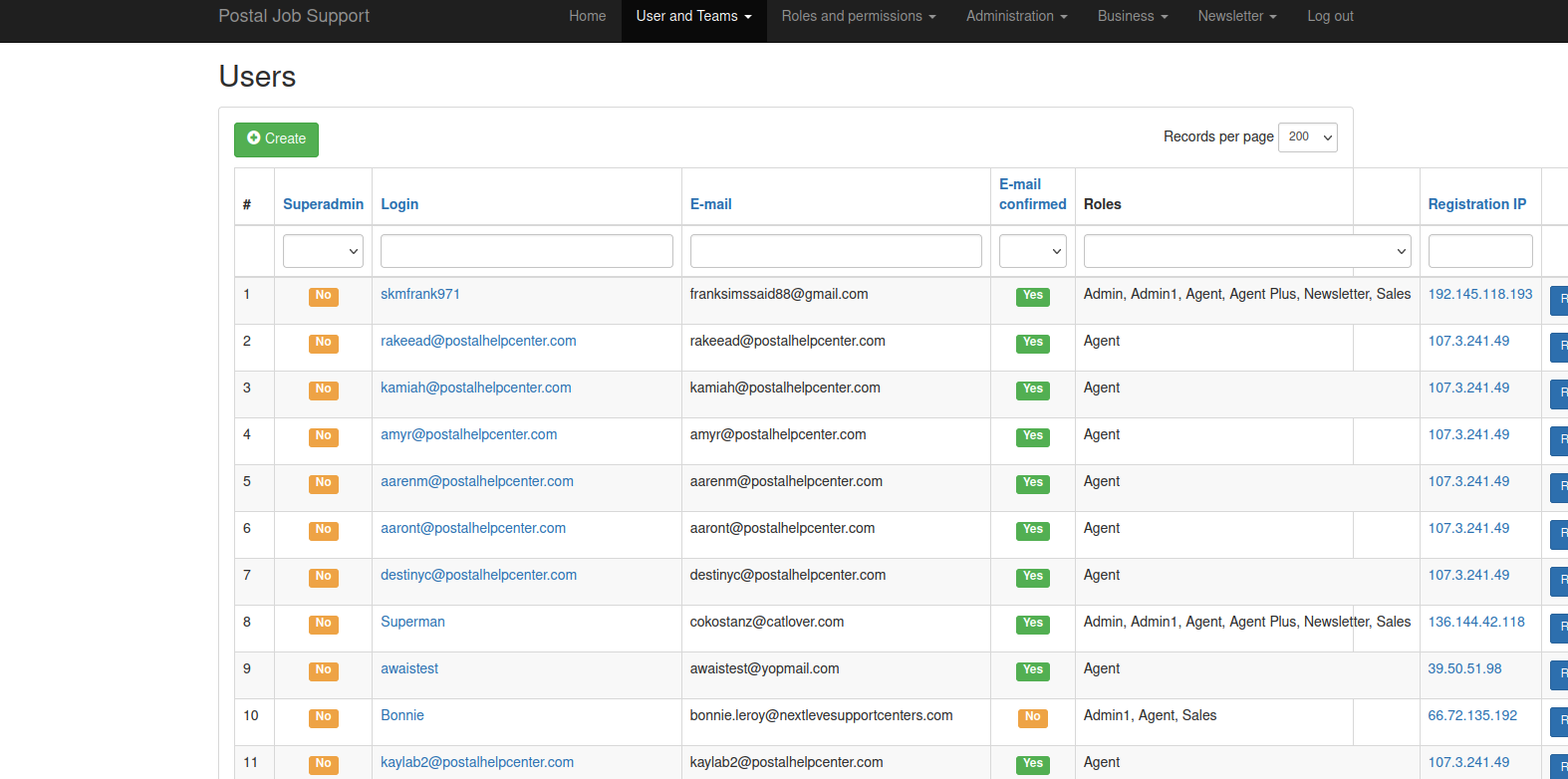
The US Job Services website has more than 160 users, including most of the employees at Next Level Support.
The website for NextLevelSupport says it was founded in 2017 by a Gary Plott, whose LinkedIn profile describes him as a seasoned telecommunications industry expert. The leaked backend database for US Job Services says Plott is a current administrator on the system, along with several other Nextlevel founders listed on the company’s site.
Reached via telephone, Plott initially said his company was merely a “white label” call center that multiple clients use to interact with customers, and that the content their call center is responsible for selling on behalf of US Job Services was not produced by NextLevelSupport.
“A few years ago, we started providing support for this postal product,” Plott said. “We didn’t develop the content but agreed we would support it.”
Interestingly, DomainTools says the Gmail address used by Plott in the US Jobs system was also used to register multiple USPS job-related domains, including postaljobssite[.]com, postalwebsite[.]com, usps-nlf[.]com, usps-nla[.]com.
Asked to reconcile this with his previous statement, Plott said he never did anything with those sites but acknowledged that his company did decide to focus on the US Postal jobs market from the very beginning.
Plott said his company never refuses to issue a money-back request from a customer, because doing so would result in costly chargebacks for NextLevel (and presumably for the many credit card merchant accounts apparently set up by Mr. Mirza).
“We’ve never been deceptive,” Plott said, noting that customers of the US Job Services product receive a digital download with tips on how to handle a USPS interview, as well as unlimited free telephone support if they need it.
“We’ve never told anyone we were the US Postal Service,” Plott continued. “We make sure people fully understand that they are not required to buy this product, but we think we can help you and we have testimonials from people we have helped. But ultimately you as the customer make that decision.”
An email address in the US Job Services teams page for another user — Stephanie Dayton — was used to register the domains postalhiringreview[.]com, and postalhiringreviewboard[.]org back in 2014. Reached for comment, Ms. Dayton said she has provided assistance to Next Level Support Centers with their training and advertising, but never in the capacity as an employee.
Perhaps the most central NextLevel associate who had access to US Job Services was Russell Ramage, a telemarketer from Warner Robins, Georgia. Ramage is listed in South Carolina incorporation records as the owner of a now-defunct call center service called Smart Logistics, a company whose name appears in the website registration records for several early and long-running US Job Services sites.

According to the state of Georgia, Russell Ramage was the registered agent of several USPS job-themed companies.
The leaked records show the email address used by Ramage also registered multiple USPS jobs-related domains, including postalhiringcenter[.]com, postalhiringreviews[.]com, postaljobs-email[.]com, and postaljobssupport1[.]com.
A review of business incorporation records in Georgia indicate Ramage was the registered agent for at least three USPS-related companies over the years, including Postal Career Placement LLC, Postal Job Services Inc., and Postal Operations Inc. All three companies were founded in 2015, and are now dissolved.
An obituary dated February 2023 says Russell Ramage recently passed away at the age of 41. No cause of death was stated, but the obituary goes on to say that Russ “Rusty” Ramage was “preceded in death by his mother, Anita Lord Ramage, pets, Raine and Nola and close friends, Nicole Reeves and Ryan Rawls.”
In 2014, then 33-year-old Ryan “Jootgater” Rawls of Alpharetta, Georgia pleaded guilty to conspiring to distribute controlled substances. Rawls also grew up in Warner Robins, and was one of eight suspects charged with operating a secret darknet narcotics ring called the Farmer’s Market, which federal prosecutors said trafficked in millions of dollars worth of controlled substances.
Reuters reported that an eighth suspect in that case had died by the time of Rawls’ 2014 guilty plea, although prosecutors declined to offer further details about that. According to his obituary, Ryan Christopher Rawls died at the age of 38 on Jan. 28, 2019.
In a comment on Ramage’s memorial wall, Stephanie Dayton said she began working with Ramage in 2006.
“Our friendship far surpassed a working one, we had a very close bond and became like brother and sister,” Dayton wrote. “I loved Russ deeply and he was like family. He was truly one of the best human beings I have ever known. He was kind and sweet and truly cared about others. Never met anyone like him. He will be truly missed. RIP brother.”
The FTC and USPS note that while applicants for many entry-level postal jobs are required to take a free postal exam, the tests are usually offered only every few years in any particular district, and there are no job placement guarantees based on score.
“If applicants pass the test by scoring at least 70 out of 100, they are placed on a register, ranked by their score,” the FTC explained. “When a position becomes open, the local post office looks to the applicable register for that geographic location and calls the top three applicants. The score is only one of many criteria taken into account for employment. The exams test general aptitude, something that cannot necessarily be increased by studying.”
The FTC says anyone interested in a job at the USPS should inquire at their local postal office, where applicants generally receive a free packet of information about required exams. More information about job opportunities at the postal service is available at the USPS’s careers website.
Michael Martel, spokesperson for the United States Postal Inspection Service, said in a written statement that the USPS has no affiliation with the websites or companies named in this story.
“To learn more about employment with USPS, visit USPS.com/careers,” Martel wrote. “If you are the victim of a crime online report it to the FBI’s Internet Crime Complaint Center (IC3) at www.ic3.gov. To report fraud committed through or toward the USPS, its employees, or customers, report it to the United States Postal Inspection Service (USPIS) at www.uspis.gov/report.”
According to the leaked back-end server for US Job Services, here is a list of the current sites selling this product:
usjobshelpcenter[.]com
usjobhelpcenter[.]com
job-postal[.]com
localpostalhiring[.]com
uspostalrecruitment[.]com
postalworkerjob[.]com
next-level-now[.]com
postalhiringcenters[.]com
postofficehiring[.]com
postaljobsplacement[.]com
postal-placement[.]com
postofficejobopenings[.]com
postalexamprep[.]com
postaljobssite[.]com
postalwebsite[.]com
postalcareerscenters[.]com
postal-hiring[.]com
postal-careers[.]com
postal-guide[.]com
postal-hiring-guide[.]com
postal-openings[.]com
postal-placement[.]com
postofficeplacements[.]com
postalplacementservices[.]com
postaljobs20[.]com
postal-jobs-placement[.]com
postaljobopenings[.]com
postalemployment[.]com
postaljobcenters[.]com
postalmilitarycareers[.]com
epostaljobs[.]com
postal-job-center[.]com
postalcareercenter[.]com
postalhiringcenters[.]com
postal-job-center[.]com
postalcareercenter[.]com
postalexamprep[.]com
postalplacementcenters[.]com
postalplacementservice[.]com
postalemploymentservices[.]com
uspostalhiring[.]com
I stand by my expression in the image above. It's a perfectly accurate representation of how I looked after receiving the CityJerks breach, clicking on the link to the website then seeing what it actually was 😳 Fortunately, the published email address on their site did go through to someone at TruckerSucker (😳😳) so they're aware of the breach and that it's circulating broadly via a public hacking website. That segment is last up in this week's video and I do give fair warning just in case you're not in the best environment to be watching that part of the update. Viewer discretion advised!

A shocking number of organizations — including banks and healthcare providers — are leaking private and sensitive information from their public Salesforce Community websites, KrebsOnSecurity has learned. The data exposures all stem from a misconfiguration in Salesforce Community that allows an unauthenticated user to access records that should only be available after logging in.
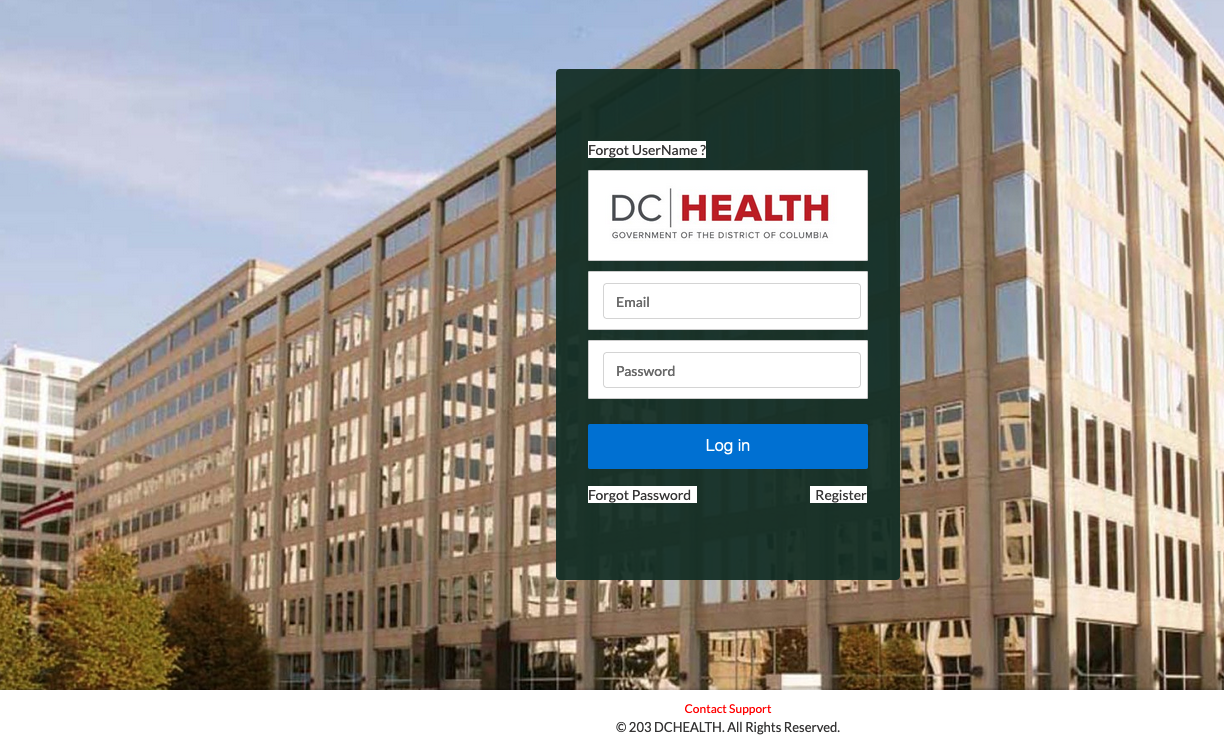
A researcher found DC Health had five Salesforce Community sites exposing data.
Salesforce Community is a widely-used cloud-based software product that makes it easy for organizations to quickly create websites. Customers can access a Salesforce Community website in two ways: Authenticated access (requiring login), and guest user access (no login required). The guest access feature allows unauthenticated users to view specific content and resources without needing to log in.
However, sometimes Salesforce administrators mistakenly grant guest users access to internal resources, which can cause unauthorized users to access an organization’s private information and lead to potential data leaks.
Until being contacted by this reporter on Monday, the state of Vermont had at least five separate Salesforce Community sites that allowed guest access to sensitive data, including a Pandemic Unemployment Assistance program that exposed the applicant’s full name, Social Security number, address, phone number, email, and bank account number.
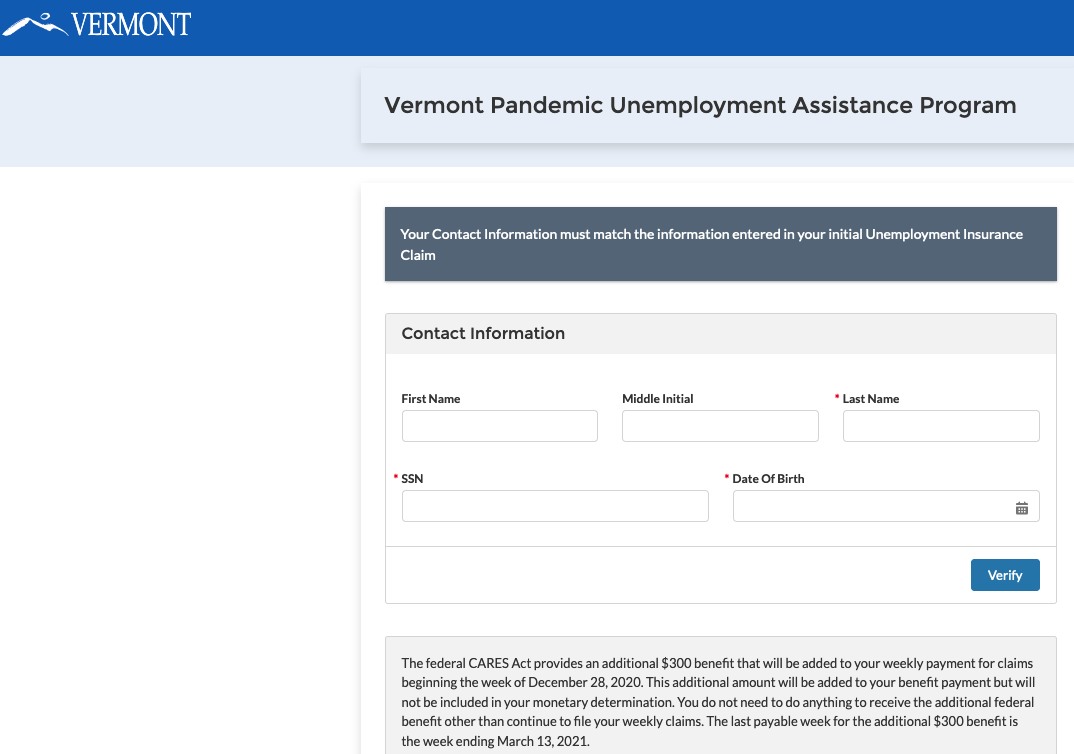
This misconfigured Salesforce Community site from the state of Vermont was leaking pandemic assistance loan application data, including names, SSNs, email address and bank account information.
Vermont’s Chief Information Security Officer Scott Carbee said his security teams have been conducting a full review of their Salesforce Community sites, and already found one additional Salesforce site operated by the state that was also misconfigured to allow guest access to sensitive information.
“My team is frustrated by the permissive nature of the platform,” Carbee said.
Carbee said the vulnerable sites were all created rapidly in response to the Coronavirus pandemic, and were not subjected to their normal security review process.
“During the pandemic, we were largely standing up tons of applications, and let’s just say a lot of them didn’t have the full benefit of our dev/ops process,” Carbee said. “In our case, we didn’t have any native Salesforce developers when we had to suddenly stand up all these sites.”
Earlier this week, KrebsOnSecurity notified Columbus, Ohio-based Huntington Bank that its recently acquired TCF Bank had a Salesforce Community website that was leaking documents related to commercial loans. The data fields in those loan applications included name, address, full Social Security number, title, federal ID, IP address, average monthly payroll, and loan amount.
Huntington Bank has disabled the leaky TCF Bank Salesforce website. Matthew Jennings, deputy chief information security officer at Huntington, said the company was still investigating how the misconfiguration occurred, how long it lasted, and how many records may have been exposed.
KrebsOnSecurity learned of the leaks from security researcher Charan Akiri, who said he wrote a program that identified hundreds of other organizations running misconfigured Salesforce pages. But Akiri said he’s been wary of probing too far, and has had difficulty getting responses from most of the organizations he has notified to date.
“In January and February 2023, I contacted government organizations and several companies, but I did not receive any response from these organizations,” Akiri said. “To address the issue further, I reached out to several CISOs on LinkedIn and Twitter. As a result, five companies eventually fixed the problem. Unfortunately, I did not receive any responses from government organizations.”
The problem Akiri has been trying to raise awareness about came to the fore in August 2021, when security researcher Aaron Costello published a blog post explaining how misconfigurations in Salesforce Community sites could be exploited to reveal sensitive data (Costello subsequently published a follow-up post detailing how to lock down Salesforce Community sites).
On Monday, KrebsOnSecurity used Akiri’s findings to notify Washington D.C. city administrators that at least five different public DC Health websites were leaking sensitive information. One DC Health Salesforce Community website designed for health professionals seeking to renew licenses with the city leaked documents that included the applicant’s full name, address, Social Security number, date of birth, license number and expiration, and more.
Akiri said he notified the Washington D.C. government in February about his findings, but received no response. Reached by KrebsOnSecurity, interim Chief Information Security Officer Mike Rupert initially said the District had hired a third party to investigate, and that the third party confirmed the District’s IT systems were not vulnerable to data loss from the reported Salesforce configuration issue.
But after being presented with a document including the Social Security number of a health professional in D.C. that was downloaded in real-time from the DC Health public Salesforce website, Rupert acknowledged his team had overlooked some configuration settings.
Washington, D.C. health administrators are still smarting from a data breach earlier this year at the health insurance exchange DC Health Link, which exposed personal information for more than 56,000 users, including many members of Congress.
That data later wound up for sale on a top cybercrime forum. The Associated Press reports that the DC Health Link breach was likewise the result of human error, and said an investigation revealed the cause was a DC Health Link server that was “misconfigured to allow access to the reports on the server without proper authentication.”
Salesforce says the data exposures are not the result of a vulnerability inherent to the Salesforce platform, but they can occur when customers’ access control permissions are misconfigured.
“As previously communicated to all Experience Site and Sites customers, we recommend utilizing the Guest User Access Report Package to assist in reviewing access control permissions for unauthenticated users,” reads a Salesforce advisory from Sept. 2022. “Additionally, we suggest reviewing the following Help article, Best Practices and Considerations When Configuring the Guest User Profile.”
In a written statement, Salesforce said it is actively focused on data security for organizations with guest users, and that it continues to release “robust tools and guidance for our customers,” including:
Control Which Users Experience Cloud Site Users Can See
Best Practices and Considerations When Configuring the Guest User Profile
“We’ve also continued to update our Guest User security policies, beginning with our Spring ‘21 release with more to come in Summer ‘23,” the statement reads. “Lastly, we continue to proactively communicate with customers to help them understand the capabilities available to them, and how they can best secure their instance of Salesforce to meet their security, contractual, and regulatory obligations.”

I feel like a significant portion of this week's video went to discussing "the Coinbase breach that wasn't a Coinbase breach". There are various services out there that are used by the likes of password managers to alert their customers to new breaches (including HIBP in 1Password) and whoever Dashlane is using frankly, royally cocked up the attribution. What was a garden variety list of email addresses someone had just chucked the "Coinbase" name on had absolutely nothing to do with a breach of the crypto company. It's frustrating to watch, and I suspect that will come through when you watch the video too. See what you think.

We learned some remarkable new details this week about the recent supply-chain attack on VoIP software provider 3CX. The lengthy, complex intrusion has all the makings of a cyberpunk spy novel: North Korean hackers using legions of fake executive accounts on LinkedIn to lure people into opening malware disguised as a job offer; malware targeting Mac and Linux users working at defense and cryptocurrency firms; and software supply-chain attacks nested within earlier supply chain attacks.
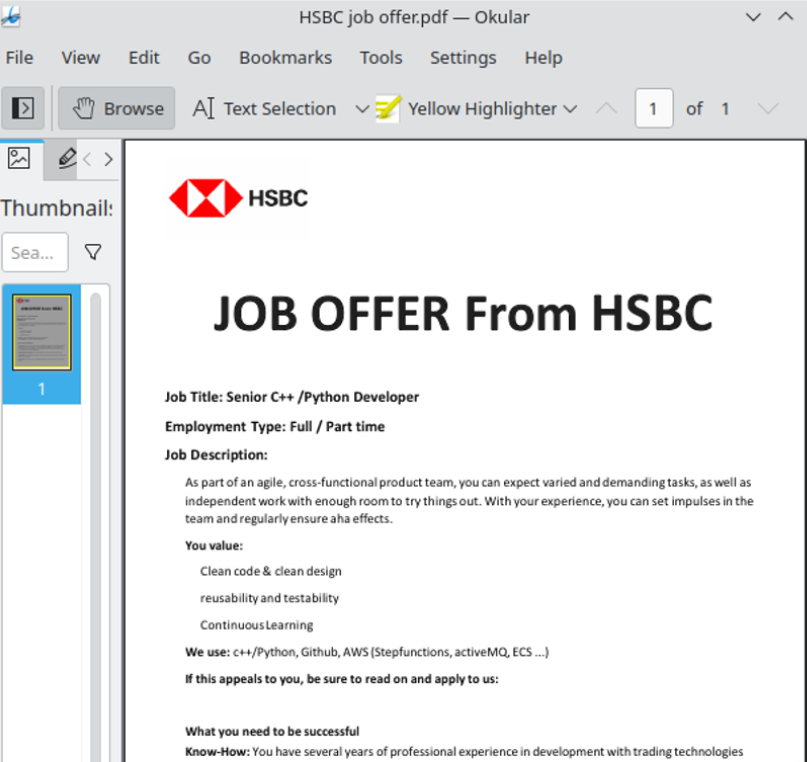
Researchers at ESET say this job offer from a phony HSBC recruiter on LinkedIn was North Korean malware masquerading as a PDF file.
In late March 2023, 3CX disclosed that its desktop applications for both Windows and macOS were compromised with malicious code that gave attackers the ability to download and run code on all machines where the app was installed. 3CX says it has more than 600,000 customers and 12 million users in a broad range of industries, including aerospace, healthcare and hospitality.
3CX hired incident response firm Mandiant, which released a report on Wednesday that said the compromise began in 2022 when a 3CX employee installed a malware-laced software package distributed via an earlier software supply chain compromise that began with a tampered installer for X_TRADER, a software package provided by Trading Technologies.
“This is the first time Mandiant has seen a software supply chain attack lead to another software supply chain attack,” reads the April 20 Mandiant report.
Mandiant found the earliest evidence of compromise uncovered within 3CX’s network was through the VPN using the employee’s corporate credentials, two days after the employee’s personal computer was compromised.
“Eventually, the threat actor was able to compromise both the Windows and macOS build environments,” 3CX said in an April 20 update on their blog.
Mandiant concluded that the 3CX attack was orchestrated by the North Korean state-sponsored hacking group known as Lazarus, a determination that was independently reached earlier by researchers at Kaspersky Lab and Elastic Security.
Mandiant found the compromised 3CX software would download malware that sought out new instructions by consulting encrypted icon files hosted on GitHub. The decrypted icon files revealed the location of the malware’s control server, which was then queried for a third stage of the malware compromise — a password stealing program dubbed ICONICSTEALER.
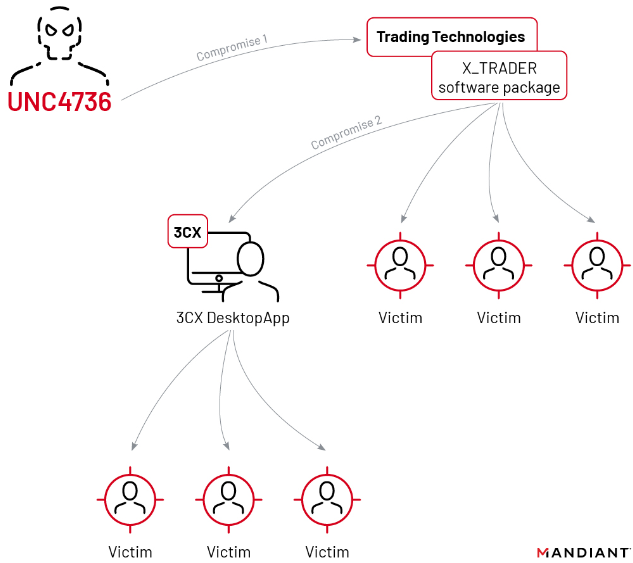
The double supply chain compromise that led to malware being pushed out to some 3CX customers. Image: Mandiant.
Meanwhile, the security firm ESET today published research showing remarkable similarities between the malware used in the 3CX supply chain attack and Linux-based malware that was recently deployed via fake job offers from phony executive profiles on LinkedIn. The researchers said this was the first time Lazarus had been spotted deploying malware aimed at Linux users.
As reported in a series last summer here, LinkedIn has been inundated this past year by fake executive profiles for people supposedly employed at a range of technology, defense, energy and financial companies. In many cases, the phony profiles spoofed chief information security officers at major corporations, and some attracted quite a few connections before their accounts were terminated.
Mandiant, Proofpoint and other experts say Lazarus has long used these bogus LinkedIn profiles to lure targets into opening a malware-laced document that is often disguised as a job offer. This ongoing North Korean espionage campaign using LinkedIn was first documented in August 2020 by ClearSky Security, which said the Lazarus group operates dozens of researchers and intelligence personnel to maintain the campaign globally.
Microsoft Corp., which owns LinkedIn, said in September 2022 that it had detected a wide range of social engineering campaigns using a proliferation of phony LinkedIn accounts. Microsoft said the accounts were used to impersonate recruiters at technology, defense and media companies, and to entice people into opening a malicious file. Microsoft found the attackers often disguised their malware as legitimate open-source software like Sumatra PDF and the SSH client Putty.
Microsoft attributed those attacks to North Korea’s Lazarus hacking group, although they’ve traditionally referred to this group as “ZINC“. That is, until earlier this month, when Redmond completely revamped the way it names threat groups; Microsoft now references ZINC as “Diamond Sleet.”
The ESET researchers said they found a new fake job lure tied to an ongoing Lazarus campaign on LinkedIn designed to compromise Linux operating systems. The malware was found inside of a document that offered an employment contract at the multinational bank HSBC.
“A few weeks ago, a native Linux payload was found on VirusTotal with an HSBC-themed PDF lure,” wrote ESET researchers Peter Kalnai and Marc-Etienne M.Leveille. “This completes Lazarus’s ability to target all major desktop operating systems. In this case, we were able to reconstruct the full chain, from the ZIP file that delivers a fake HSBC job offer as a decoy, up until the final payload.”
ESET said the malicious PDF file used in the scheme appeared to have a file extension of “.pdf,” but that this was a ruse. ESET discovered that the dot in the filename wasn’t a normal period but instead a Unicode character (U+2024) representing a “leader dot,” which is often used in tables of contents to connect section headings with the page numbers on which those sections begin.
“The use of the leader dot in the filename was probably an attempt to trick the file manager into treating the file as an executable instead of a PDF,” the researchers continued. “This could cause the file to run when double-clicked instead of opening it with a PDF viewer.”
ESET said anyone who opened the file would see a decoy PDF with a job offer from HSBC, but in the background the executable file would download additional malware payloads. The ESET team also found the malware was able to manipulate the program icon displayed by the malicious PDF, possibly because fiddling with the file extension could cause the user’s system to display a blank icon for the malware lure.
Kim Zetter, a veteran Wired.com reporter and now independent security journalist, interviewed Mandiant researchers who said they expect “many more victims” will be discovered among the customers of Trading Technologies and 3CX now that news of the compromised software programs is public.
“Mandiant informed Trading Technologies on April 11 that its X_Trader software had been compromised, but the software maker says it has not had time to investigate and verify Mandiant’s assertions,” Zetter wrote in her Zero Day newsletter on Substack. For now, it remains unclear whether the compromised X_Trader software was downloaded by people at other software firms.
If there’s a silver lining here, the X_Trader software had been decommissioned in April 2020 — two years before the hackers allegedly embedded malware in it.
“The company hadn’t released new versions of the software since that time and had stopped providing support for the product, making it a less-than-ideal vector for the North Korean hackers to infect customers,” Zetter wrote.

A bit late this week as I've prioritised time out with the family doing as many New Zealand adventure things as we can. And we've seriously maxed out the time, as you can see via the FB link below. But that hasn't stopped a couple of new data breaches flowing into HIBP nor me having some pretty direct thoughts on the premise that the vast bulk of IT pros are being told not to report data breaches. I hope you enjoy this impromptu vid from a faraway location at an odd time, I'll be back to normal again next week.






Next time I post a poll about something as simple as "when is next Friday", I don't expect I'll get as much interest. Of course "next time" will be whatever poll follows the last one, not the poll that falls after that one! But more seriously, I cannot think of a better example of ambiguous language that's open to interpretation and so easily avoided (hello MM-DD people!)
Also, Genesis Market and Operation Cookie Monster. This is just amazing stuff and a testament to a coalition of law enforcement agencies across the globe that have now made well over 100 arrests. Off the back of the NCA's DDoS market honeypot, the BreachForums admin arrest and the takedown of RaidForums before that, if you're playing in this space you'd have to be looking over your shoulder by now. Interesting times in cyber(crime) space.




Most of this week's video went on talking about the UniFi Dream Wall. What a unit! I mean it's big, but then it wraps a lot of stuff up in the one device too. If you watch this and have thoughts on how I can integrate it into the new garage such that it doesn't clash with the dark theme, I'd love to hear about it. I'll share more once I set it up in the coming weeks but for now, enjoy this week's video 🙂
