Google Cloud has put $1 million on the table to cover customers' unauthorized compute expenses stemming from cryptomining attacks if its sensors don't spot these illicit miners.…
Hyundai and Kia cars were stolen 977 times in New York City in the first four months of 2023, and authorities have had enough.…
Webinar Rubrik Zero Lab's annual report on the state of data security is not a comfortable read. And as if to prepare you for what lies inside, the company has called it 'The Hard Truths.'…
A curious case of a threat actor at the border between crimeware and cyberespionage
The post Asylum Ambuscade: crimeware or cyberespionage? appeared first on WeLiveSecurity
The timeworn adage that "those who don't learn from history are doomed to repeat it" can certainly be applied to cyber security. Microsoft is hoping to spare enterprises that use its cloud services from repeating history by sharing what it has learned.…
Sponsored Feature When Windows 11 launched in October 2021, one of its big selling points was a new security architecture. Microsoft designed it from the ground up with zero-trust principles in mind, refusing to trust the legitimacy of any single system component. Instead, everything must prove that it has not been compromised.…
The UK government will set a deadline for removing made-in-China surveillance cameras from "sensitive sites."…
Miscreants are using AI to create faked images of a sexual nature, which they then employ in sextortion schemes.…




Clop, the ransomware crew that has exploited the MOVEit vulnerability extensively to steal corporate data, has given victims a June 14 deadline to pay up or the purloined information will be leaked.…
Feature The world got a first glimpse into the US government's far-reaching surveillance of American citizens' communications – namely, their Verizon telephone calls – 10 years ago this week when Edward Snowden's initial leaks hit the press.…
How your voice assistant could do the bidding of a hacker – without you ever hearing a thing
The post Hear no evil: Ultrasound attacks on voice assistants appeared first on WeLiveSecurity
Three supporters of activists against a $90 million police training facility dubbed Cop City were arrested after the cops used PayPal data to bring money-laundering charges against the trio.…
One of the most expensive aspects of any cybercriminal operation is the time and effort it takes to constantly create large numbers of new throwaway email accounts. Now a new service offers to help dramatically cut costs associated with large-scale spam and account creation campaigns, by paying people to sell their email account credentials and letting customers temporarily rent access to a vast pool of established accounts at major providers.

The service in question — kopeechka[.]store — is perhaps best described as a kind of unidirectional email confirmation-as-a-service that promises to “save your time and money for successfully registering multiple accounts.”
“Are you working on large volumes and are costs constantly growing?” Kopeechka’s website asks. “Our service will solve all your problems.”
As a customer of this service, you don’t get full access to the email inboxes you are renting. Rather, you configure your botnet or spam machine to make an automated application programming interface (API) call to the Kopeechka service, which responds with a working email address at an email provider of your choosing.
Once you’ve entered the supplied email address into the new account registration page at some website or service, you tell Kopeechka which service or website you’re expecting an account confirmation link from, and they will then forward any new messages matching that description to your Kopeechka account panel.
Ensuring that customers cannot control inboxes rented through the service means that Kopeechka can rent the same email address to multiple customers (at least until that email address has been used to register accounts at most of the major online services).
Kopeechka also has multiple affiliate programs, including one that pays app developers for embedding Kopeechka’s API in their software. However, far more interesting is their program for rewarding people who choose to sell Kopeechka usernames and passwords for working email addresses.
Kopeechka means “penny” in Russian, which is generous verbiage (and coinage) for a service that charges a tiny fraction of a penny for access to account confirmation links. Their pricing fluctuates slightly based on which email provider you choose, but a form on the service’s homepage says a single confirmation message from apple.com to outlook.com costs .07 rubles, which is currently equal to about $0.00087 dollars.
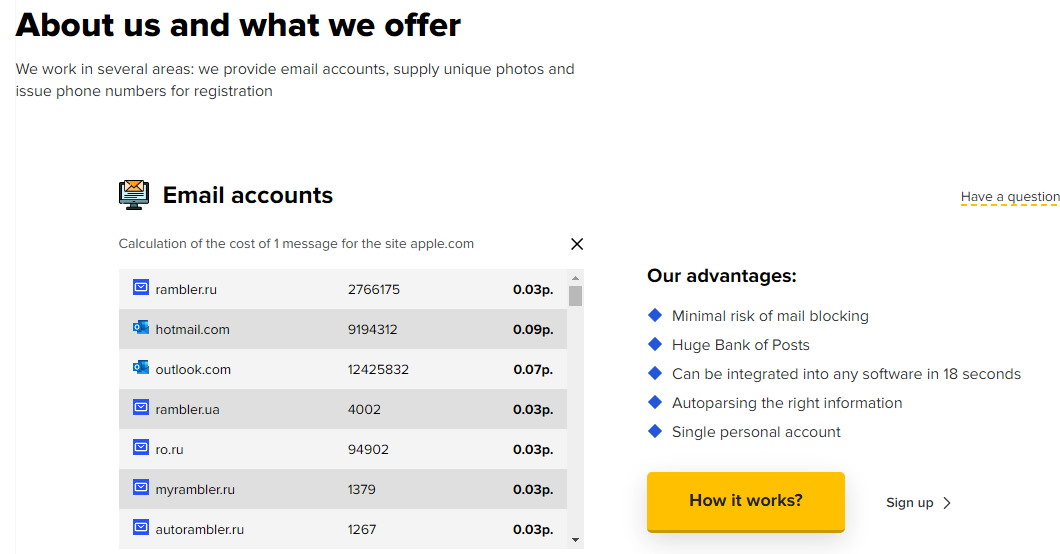
The pricing for Kopeechka works out to about a fraction of a penny per confirmation message.
“Emails can be uploaded to us for sale, and you will receive a percentage of purchases %,” the service explains. “You upload 1 mailbox of a certain domain, discuss percentage with our technical support (it depends on the liquidity of the domain and the number of downloaded emails).”
We don’t have to look very far for examples of Kopeechka in action. In May, KrebsOnSecurity interviewed a Russian spammer named “Quotpw“ who was mass-registering accounts on the social media network Mastodon in order to conduct a series of huge spam campaigns advertising scam cryptocurrency investment platforms.
Much of the fodder for that story came from Renaud Chaput, a freelance programmer working on modernizing and scaling the Mastodon project infrastructure — including joinmastodon.org, mastodon.online, and mastodon.social. Chaput told KrebsOnSecurity that his team was forced to temporarily halt all new registrations for these communities last month after the number of new registrations from Quotpw’s spam campaign started to overwhelm their systems.
“We suddenly went from like three registrations per minute to 900 a minute,” Chaput said. “There was nothing in the Mastodon software to detect that activity, and the protocol is not designed to handle this.”
After that story ran, Chaput said he discovered that the computer code powering Quotpw’s spam botnet (which has since been released as open source) contained an API call to Kopeechka’s service.
“It allows them to pool many bot-created or compromised emails at various providers and offer them to cyber criminals,” Chaput said of Kopeechka. “This is what they used to create thousands of valid Hotmail (and other) addresses when spamming on Mastodon. If you look at the code, it’s really well done with a nice API that forwards you the confirmation link that you can then fake click with your botnet.”
It’s doubtful anyone will make serious money selling email accounts to Kopeechka, unless of course that person already happens to run a botnet and has access to ridiculous numbers of email credentials. And in that sense, this service is genius: It essentially offers scammers a new way to wring extra income from resources that are already plentiful for them.
One final note about Quotpw and the spam botnet that ravaged Chaput’s Mastodon servers last month: Trend Micro just published a report saying Quotpw was spamming to earn money for a Russian-language affiliate program called “Impulse Team,” which pays people to promote cryptocurrency scams.
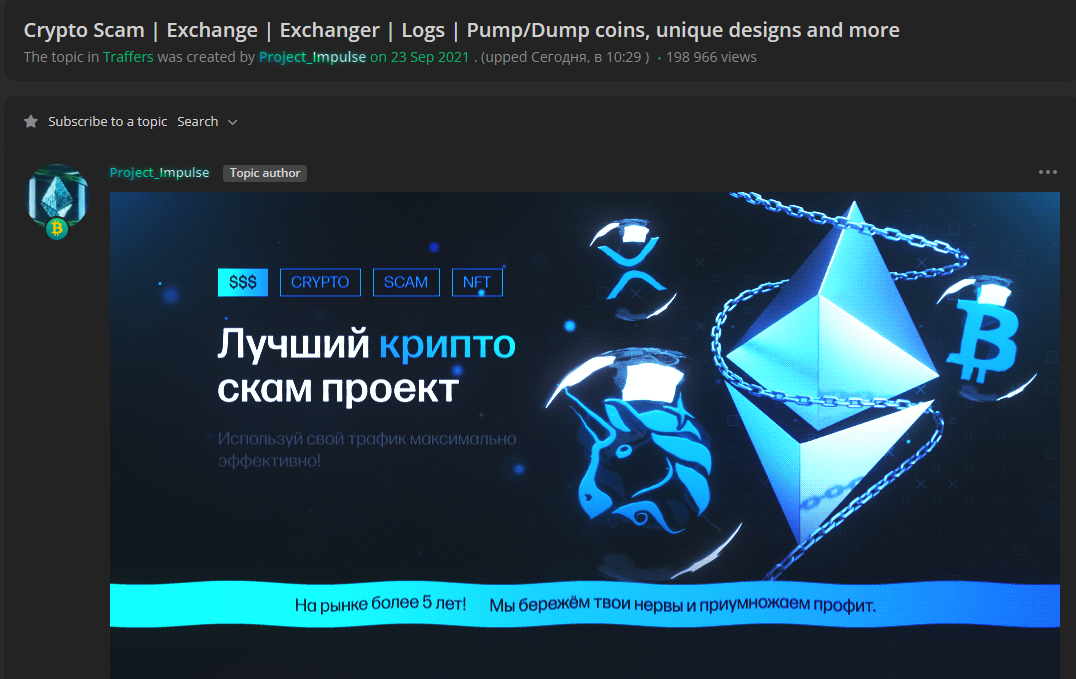
The crypto scam affiliate program “Project Impulse,” advertising in 2021.
Websites under the banner of the Impulse Scam Crypto Project are all essentially “advanced fee” scams that tell people they have earned a cryptocurrency investment credit. Upon registering at the site, visitors are told they need to make a minimum deposit on the service to collect the award. However, those who make the initial investment never hear from the site again, and their money is gone.
Interestingly, Trend Micro says the scammers behind the Impulse Team also appear to be operating a fake reputation service called Scam-Doc[.]com, a website that mimics the legitimate Scamdoc.com for measuring the trustworthiness and authenticity of various sites. Trend notes that the phony reputation site routinely gave high trust ratings to a variety of cryptocurrency scam and casino websites.
“We can only suppose that either the same cybercriminals run operations involving both or that several different cybercriminals share the scam-doc[.]com site,” the Trend researchers wrote.
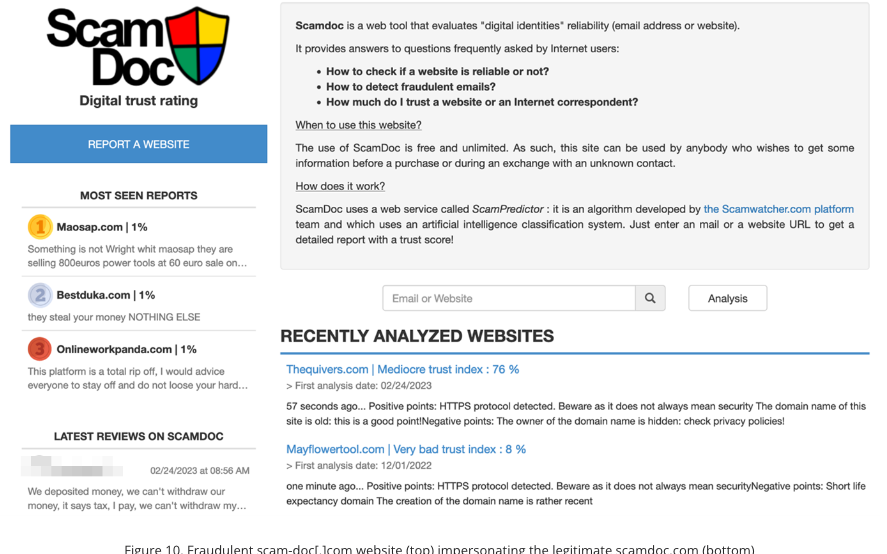
The ScamDoc fake reputation websites, which were apparently used to help make fake crypto investment platforms look more trustworthy. Image: Trend Micro.
According to the FBI, financial losses from cryptocurrency investment scams dwarfed losses for all other types of cybercrime in 2022, rising from $907 million in 2021 to $2.57 billion last year.
The US Ninth Circuit Court of Appeals last week ruled that Enigma Software Group can pursue its long standing complaint against rival security firm Malwarebytes for classifying its software as "potentially unwanted programs" or PUPs.…
The US federal government's ban on TikTok has been extended to include devices used by its many contractors - even those that are privately owned. The bottom line: if some electronics are used for government work, it better not have any ByteDance bits on it. …
Microsoft is being fined $20 million by the US Federal Trade Commission for violating the Children's Online Privacy Protection Act (COPPA) by illegally gathering kids' personal information and retaining it without parental consent.…
An American university founded in 1833 is facing a bunch of class action lawsuits after the personal data of nearly 100,000 people was stolen from its tech infrastructure.…




Plus, 7 ways to tell that you downloaded a sketchy app and 7 tips for staying safe from mobile security threats in the future
The post 7 tips for spotting a fake mobile app appeared first on WeLiveSecurity