A number of Discord communities focused on cryptocurrency have been hacked this past month after their administrators were tricked into running malicious Javascript code disguised as a Web browser bookmark.
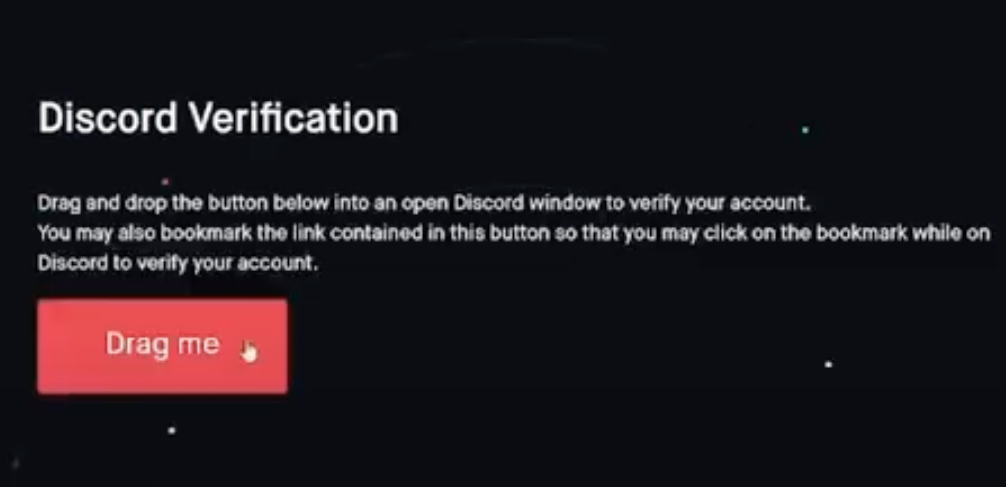
This attack involves malicious Javascript that is added to one’s browser by dragging a component from a web page to one’s browser bookmarks.
According to interviews with victims, several of the attacks began with an interview request from someone posing as a reporter for a crypto-focused news outlet online. Those who take the bait are sent a link to a Discord server that appears to be the official Discord of the crypto news site, where they are asked to complete a verification step to validate their identity.
As shown in this Youtube video, the verification process involves dragging a button from the phony crypto news Discord server to the bookmarks bar in one’s Web browser. From there, the visitor is instructed to go back to discord.com and then click the new bookmark to complete the verification process.
However, the bookmark is actually a clever snippet of Javascript that quietly grabs the user’s Discord token and sends it to the scammer’s website. The attacker then loads the stolen token into their own browser session and (usually late at night after the admins are asleep) posts an announcement in the targeted Discord about an exclusive “airdrop,” “NFT mint event” or some other potential money making opportunity for the Discord members.
The unsuspecting Discord members click the link provided by the compromised administrator account, and are asked to connect their crypto wallet to the scammer’s site, where it asks for unlimited spend approvals on their tokens, and subsequently drains the balance of any valuable accounts.
Meanwhile, anyone in the compromised Discord channel who notices the scam and replies is banned, and their messages are deleted by the compromised admin account.
Nicholas Scavuzzo is an associate at Ocean Protocol, which describes itself as an “open-source protocol that aims to allow businesses and individuals to exchange and monetize data and data-based services.” On May 22, an administrator for Ocean Protocol’s Discord server clicked a link in a direct message from a community member that prompted them to prove their identity by dragging a link to their bookmarks.
Scavuzzo, who is based in Maine, said the attackers waited until around midnight in his timezone time before using the administrator’s account to send out an unauthorized message about a new Ocean airdrop.
Scavuzzo said the administrator’s account was hijacked even though she had multi-factor authentication turned on.
“A CAPTCHA bot that allows Discord cookies to be accessed by the person hosting the CAPTCHA,” was how Scavuzzo described the attack. “I’ve seen all kinds of crypto scams, but I’ve never seen one like this.”
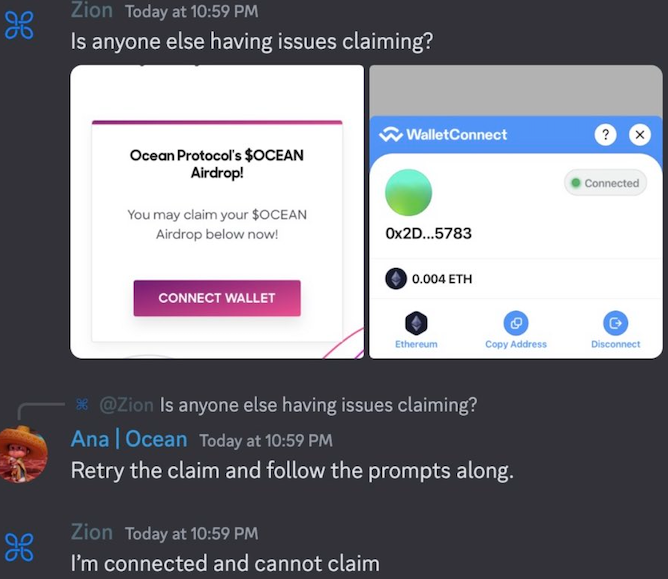
In this conversation, “Ana | Ocean” is a compromised Discord server administrator account promoting a phony airdrop.
Importantly, the stolen token only works for the attackers as long as its rightful owner doesn’t log out and back in, or else change their credentials.
Assuming the administrator can log in, that is. In Ocean’s case, one of the first things the intruders did once they swiped the administrator’s token was change the server’s access controls and remove all core Ocean team members from the server.
Fortunately for Ocean, Scavuzzo was able to reach the operator of the server that hosts the Discord channel, and have the channel’s settings reverted back to normal.
“Thankfully, we are a globally distributed team, so we have people awake at all hours,” Scavuzzo said, noting that Ocean is not aware of any Discord community members who fell for the phony airdrop offer, which was live for about 30 minutes. “This could have been a lot worse.”
On May 26, Aura Network reported on Twitter that its Discord server was compromised in a phishing attack that resulted in the deletion of Discord channels and the dissemination of fake Aura Network Airdrop Campaign links.
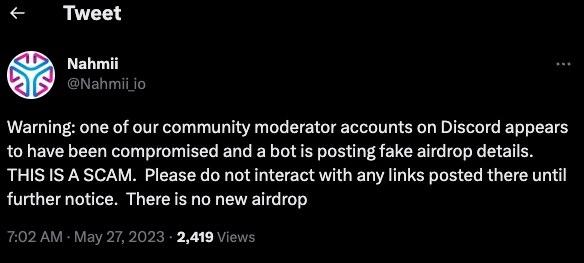
On May 27, Nahmii — a cryptocurrency technology based on the Ethereum blockchain — warned on Twitter that one of its community moderators on Discord was compromised and posting fake airdrop details.
On May 9, MetrixCoin reported that its Discord server was hacked, with fake airdrop details pushed to all users.
KrebsOnSecurity recently heard from a trusted source in the cybersecurity industry who dealt firsthand with one of these attacks and asked to remain anonymous.
“I do pro bono Discord security work for a few Discords, and I was approached by one of these fake journalists,” the source said. “I played along and got the link to their Discord, where they were pretending to be journalists from the Cryptonews website using several accounts.”
The source took note of all the Discord IDs of the admins of the fake Cryptonews Discord, so that he could ensure they were blocked from the Discords he helps to secure.
“Since I’ve been doing this for a while now, I’ve built up a substantial database of Discord users and messages, so often I can see these scammers’ history on Discord,” the source said.
In this case, he noticed a user with the “CEO” role in the fake Cryptonews Discord had been seen previously under another username — “Levatax.” Searching on that Discord ID and username revealed a young Turkish coder named Berk Yilmaz whose Github page linked to the very same Discord ID as the scammer CEO.
Reached via instant message on Telegram, Levatax said he’s had no involvement in such schemes, and that he hasn’t been on Discord since his Microsoft Outlook account was hacked months ago.
“The interesting thing [is] that I didn’t use Discord since few months or even social media because of the political status of Turkey,” Levatax explained, referring to the recent election in his country. “The only thing I confirm is losing my Outlook account which connected to my Discord, and I’m already in touch with Microsoft to recover it.”
The verification method used in the above scam involves a type of bookmark called a “bookmarklet” that stores Javascript code as a clickable link in the bookmarks bar at the top of one’s browser.
While bookmarklets can be useful and harmless, malicious Javascript that is executed in the browser by the user is especially dangerous. So please avoid adding (or dragging) any bookmarks or bookmarklets to your browser unless it was your idea in the first place.








ispoof-1200














The U.S. Federal Bureau of Investigation (FBI) this week seized 13 domain names connected to “booter” services that let paying customers launch crippling distributed denial-of-service (DDoS) attacks. Ten of the domains are reincarnations of DDoS-for-hire services the FBI seized in December 2022, when it charged six U.S. men with computer crimes for allegedly operating booters.
Booter services are advertised through a variety of methods, including Dark Web forums, chat platforms and even youtube.com. They accept payment via PayPal, Google Wallet, and/or cryptocurrencies, and subscriptions can range in price from just a few dollars to several hundred per month. The services are generally priced according to the volume of traffic to be hurled at the target, the duration of each attack, and the number of concurrent attacks allowed.
The websites that saw their homepages replaced with seizure notices from the FBI this week include booter services like cyberstress[.]org and exoticbooter[.]com, which the feds say were used to launch millions of attacks against millions of victims.
“School districts, universities, financial institutions and government websites are among the victims who have been targeted in attacks launched by booter services,” federal prosecutors in Los Angeles said in a statement.
Purveyors of booters or “stressers” claim they are not responsible for how customers use their services, and that they aren’t breaking the law because — like most security tools — these services can be used for good or bad purposes. Most booter sites employ wordy “terms of use” agreements that require customers to agree they will only stress-test their own networks — and that they won’t use the service to attack others.
But the DOJ says these disclaimers usually ignore the fact that most booter services are heavily reliant on constantly scanning the Internet to commandeer misconfigured devices that are critical for maximizing the size and impact of DDoS attacks. What’s more, none of the services seized by the government required users to demonstrate that they own the Internet addresses being stress-tested, something a legitimate testing service would insist upon.
This is the third in a series of U.S. and international law enforcement actions targeting booter services. In December 2022, the feds seized four-dozen booter domains and charged six U.S. men with computer crimes related to their alleged ownership of the popular DDoS-for-hire services. In December 2018, the feds targeted 15 booter sites, and three booter store defendants who later pleaded guilty.
While the FBI’s repeated seizing of booter domains may seem like an endless game of virtual Whac-a-Mole, continuously taking these services offline imposes high enough costs for the operators that some of them will quit the business altogether, says Richard Clayton, director of Cambridge University’s Cybercrime Centre.
In 2020, Clayton and others published “Cybercrime is Mostly Boring,” an academic study on the quality and types of work needed to build, maintain and defend illicit enterprises that make up a large portion of the cybercrime-as-a-service market. The study found that operating a booter service effectively requires a mind-numbing amount of constant, tedious work that tends to produce high burnout rates for booter service operators — even when the service is operating efficiently and profitably.
For example, running an effective booter service requires a substantial amount of administrative work and maintenance, much of which involves constantly scanning for, commandeering and managing large collections of remote systems that can be used to amplify online attacks, Clayton said. On top of that, building brand recognition and customer loyalty takes time.
“If you’re running a booter and someone keeps taking your domain or hosting away, you have to then go through doing the same boring work all over again,” Clayton told KrebsOnSecurity. “One of the guys the FBI arrested in December [2022] spent six months moaning that he lost his servers, and could people please lend him some money to get it started again.”
In a statement released Wednesday, prosecutors in Los Angeles said four of the six men charged last year for running booter services have since pleaded guilty. However, at least one of the defendants from the 2022 booter bust-up — John M. Dobbs, 32, of Honolulu, HI — has pleaded not guilty and is signaling he intends to take his case to trial.
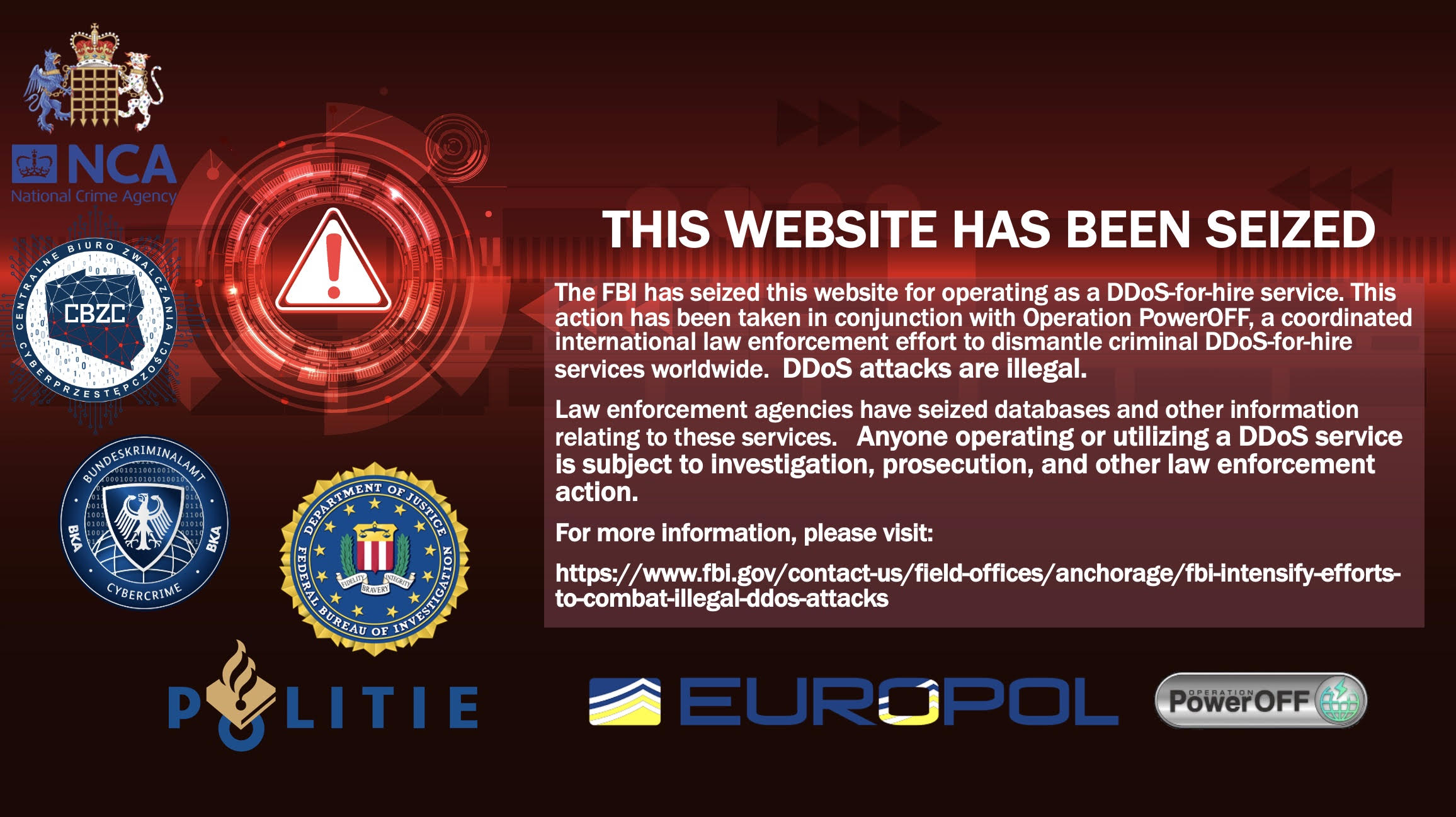
The FBI seizure notice that replaced the homepages of several booter services this week.
Dobbs is a computer science graduate student who for the past decade openly ran IPStresser[.]com, a popular and powerful attack-for-hire service that he registered with the state of Hawaii using his real name and address. Likewise, the domain was registered in Dobbs’s name and hometown in Pennsylvania. Prosecutors say Dobbs’ service attracted more than two million registered users, and was responsible for launching a staggering 30 million distinct DDoS attacks.
Many accused stresser site operators have pleaded guilty over the years after being hit with federal criminal charges. But the government’s core claim — that operating a booter site is a violation of U.S. computer crime laws — wasn’t properly tested in the courts until September 2021.
That was when a jury handed down a guilty verdict against Matthew Gatrel, a then 32-year-old St. Charles, Ill. man charged in the government’s first 2018 mass booter bust-up. Despite admitting to FBI agents that he ran two booter services (and turning over plenty of incriminating evidence in the process), Gatrel opted to take his case to trial, defended the entire time by court-appointed attorneys.
Gatrel was convicted on all three charges of violating the Computer Fraud and Abuse Act, including conspiracy to commit unauthorized impairment of a protected computer, conspiracy to commit wire fraud, and unauthorized impairment of a protected computer. He was sentenced to two years in prison.
A copy of the FBI’s booter seizure warrant is here (PDF). According to the DOJ, the defendants who pleaded guilty to operating booter sites include:
–Jeremiah Sam Evans Miller, aka “John The Dev,” 23, of San Antonio, Texas, who pleaded guilty on April 6 to conspiracy and violating the computer fraud and abuse act related to the operation of a booter service named RoyalStresser[.]com (formerly known as Supremesecurityteam[.]com);
–Angel Manuel Colon Jr., aka “Anonghost720” and “Anonghost1337,” 37, of Belleview, Florida, who pleaded guilty on February 13 to conspiracy and violating the computer fraud and abuse act related to the operation of a booter service named SecurityTeam[.]io;
–Shamar Shattock, 19, of Margate, Florida, who pleaded guilty on March 22 to conspiracy to violate the computer fraud and abuse act related to the operation of a booter service known as Astrostress[.]com;
–Cory Anthony Palmer, 23, of Lauderhill, Florida, who pleaded guilty on February 16 to conspiracy to violate the computer fraud and abuse act related to the operation of a booter service known as Booter[.]sx.
All four defendants are scheduled to be sentenced this summer.
The booter domains seized by the FBI this week include:
cyberstress[.]org
exoticbooter[.]com
layerstress[.]net
orbitalstress[.]xyz
redstresser[.]io
silentstress[.]wtf
sunstresser[.]net
silent[.]to
mythicalstress[.]net
dreams-stresser[.]org
stresserbest[.]io
stresserus[.]io
quantum-stress[.]org



A sprawling online company based in Georgia that has made tens of millions of dollars purporting to sell access to jobs at the United States Postal Service (USPS) has exposed its internal IT operations and database of nearly 900,000 customers. The leaked records indicate the network’s chief technology officer in Pakistan has been hacked for the past year, and that the entire operation was created by the principals of a Tennessee-based telemarketing firm that has promoted USPS employment websites since 2016.
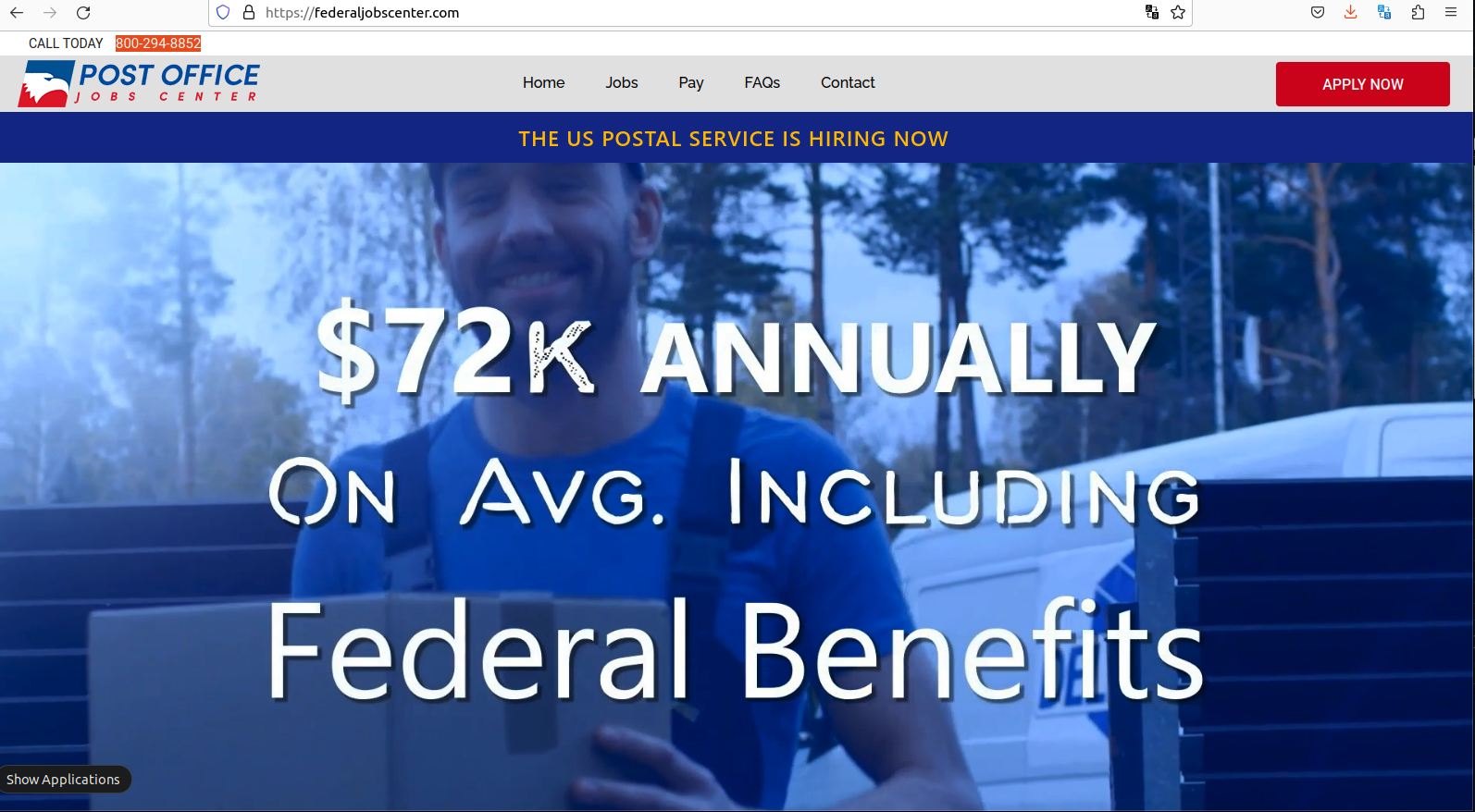
The website FederalJobsCenter promises to get you a job at the USPS in 30 days or your money back.
KrebsOnSecurity was recently contacted by a security researcher who said he found a huge tranche of full credit card records exposed online, and that at first glance the domain names involved appeared to be affiliated with the USPS.
Further investigation revealed a long-running international operation that has been emailing and text messaging people for years to sign up at a slew of websites that all promise they can help visitors secure employment at the USPS.
Sites like FederalJobsCenter[.]com also show up prominently in Google search results for USPS employment, and steer applicants toward making credit card “registration deposits” to ensure that one’s application for employment is reviewed. These sites also sell training, supposedly to help ace an interview with USPS human resources.
FederalJobsCenter’s website is full of content that makes it appear the site is affiliated with the USPS, although its “terms and conditions” state that it is not. Rather, the terms state that FederalJobsCenter is affiliated with an entity called US Job Services, which says it is based in Lawrenceville, Ga.
“US Job Services provides guidance, coaching, and live assistance to postal job candidates to help them perform better in each of the steps,” the website explains.
The site says applicants need to make a credit card deposit to register, and that this amount is refundable if the applicant is not offered a USPS job within 30 days after the interview process.
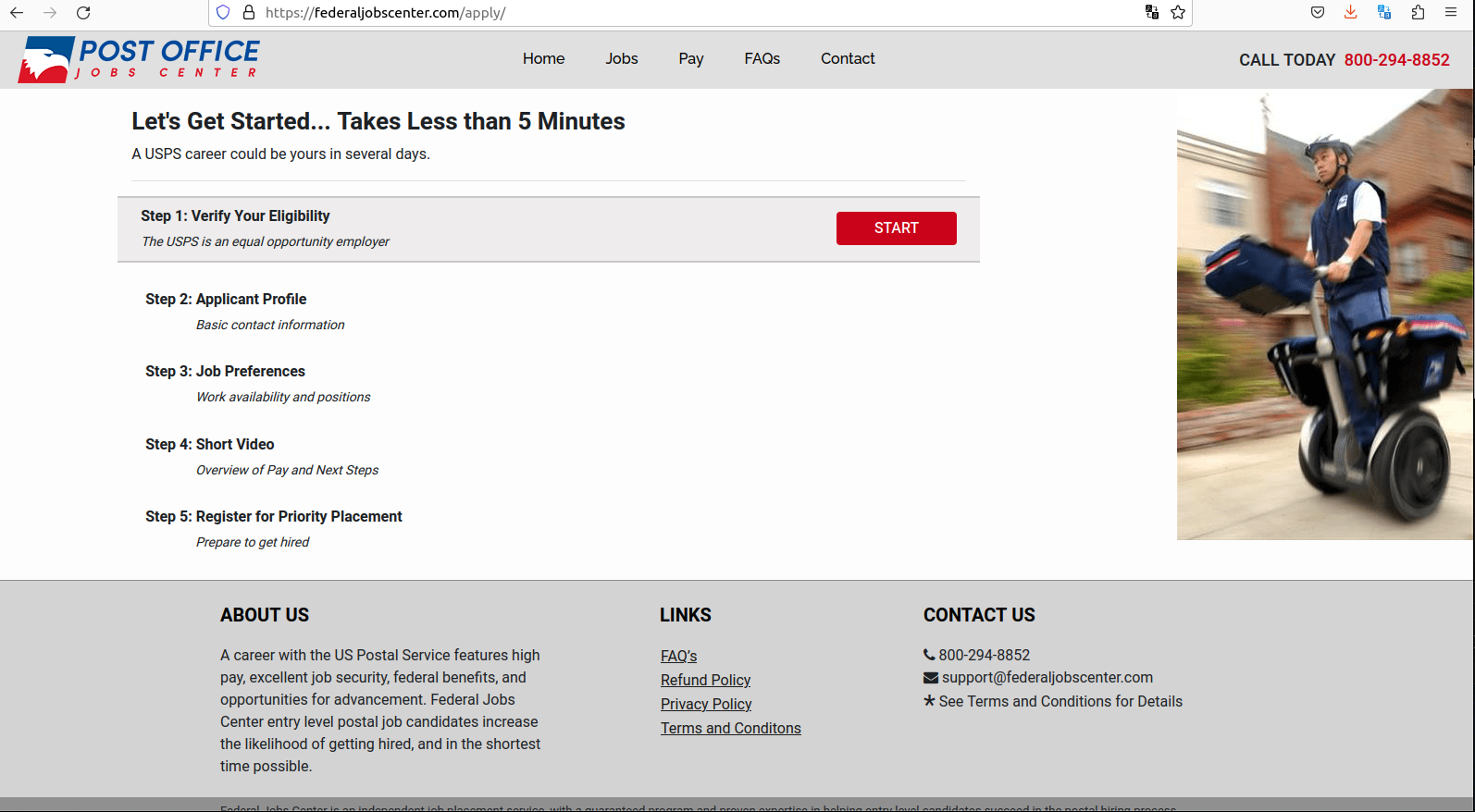
But a review of the public feedback on US Job Services and dozens of similar names connected to this entity over the years shows a pattern of activity: Applicants pay between $39.99 and $100 for USPS job coaching services, and receive little if anything in return. Some reported being charged the same amount monthly.
The U.S. Federal Trade Commission (FTC) has sued several times over the years to disrupt various schemes offering to help people get jobs at the Postal Service. Way back in 1998, the FTC and the USPS took action against several organizations that were selling test or interview preparation services for potential USPS employees.
“Companies promising jobs with the U.S. Postal Service are breaking federal law,” the joint USPS-FTC statement said.
In that 1998 case, the defendants behind the scheme were taking out classified ads in newspapers. Ditto for a case the FTC brought in 2005. By 2008, the USPS job exam preppers had shifted to advertising their schemes mostly online. And in 2013, the FTC won a nearly $5 million judgment against a Kentucky company purporting to offer such services.
Tim McKinlay authored a report last year at Affiliateunguru.com on whether the US Job Services website job-postal[.]com was legitimate or a scam. He concluded it was a scam based on several factors, including that the website listed multiple other names (suggesting it had recently switched names), and that he got nothing from the transaction with the job site.
“They openly admit they’re not affiliated with the US Postal Service, but claim to be experts in the field, and that, just by following the steps on their site, you easily pass the postal exams and get a job in no time,” McKinlay wrote. “But it’s really just a smoke and mirrors game. The site’s true purpose is to collect $46.95 from as many people as possible. And considering how popular this job is, they’re probably making a killing.”
KrebsOnSecurity was alerted to the data exposure by Patrick Barry, chief information officer at Charlotte, NC based Rebyc Security. Barry said he found that not only was US Job Services leaking its customer payment records in real-time and going back to 2016, but its website also leaked a log file from 2019 containing the site administrator’s contact information and credentials to the site’s back-end database.
Barry shared screenshots of that back-end database, which show the email address for the administrator of US Job Services is tab.webcoder@gmail.com. According to cyber intelligence platform Constella Intelligence, that email address is tied to the LinkedIn profile for a developer in Karachi, Pakistan named Muhammed Tabish Mirza.
A search on tab.webcoder@gmail.com at DomainTools.com reveals that email address was used to register several USPS-themed domains, including postal2017[.]com, postaljobscenter[.]com and usps-jobs[.]com.
Mr. Mirza declined to respond to questions, but the exposed database information was removed from the Internet almost immediately after KrebsOnSecurity shared the offending links.
A “Campaigns” tab on that web panel listed several advertising initiatives tied to US Job Services websites, with names like “walmart drip campaign,” “hiring activity due to virus,” “opt-in job alert SMS,” and “postal job opening.”
Another page on the US Job Services panel included a script for upselling people who call in response to email and text message solicitations, with an add-on program that normally sells for $1,200 but is being “practically given away” for a limited time, for just $49.
“There’s something else we have you can take advantage of that can help you make more money,” the script volunteers. “It’s an easy to use 12-month career development plan and program to follow that will result in you getting any job you want, not just at the post office….anywhere…and then getting promoted rapidly.”
It’s bad enough that US Job Services was leaking customer data: Constella Intelligence says the email address tied to Mr. Mirza shows up in more than a year’s worth of “bot logs” created by a malware infection from the Redline infostealer.
Constella reports that for roughly a year between 2021 and 2022, a Microsoft Windows device regularly used by Mr. Mirza and his colleagues was actively uploading all of the device’s usernames, passwords and authentication cookies to cybercriminals based in Russia.
The web-based backend for US Job Services lists more than 160 people under its “Users & Teams” tab. This page indicates that access to the consumer and payment data collected by US Job Services is currently granted to several other coders who work with Mr. Mirza in Pakistan, and to multiple executives, contractors and employees working for a call center in Murfreesboro, Tennessee.
The call center — which operates as Nextlevelsupportcenters[.]com and thenextlevelsupport[.]com — curiously has several key associates with a history of registering USPS jobs-related domain names.
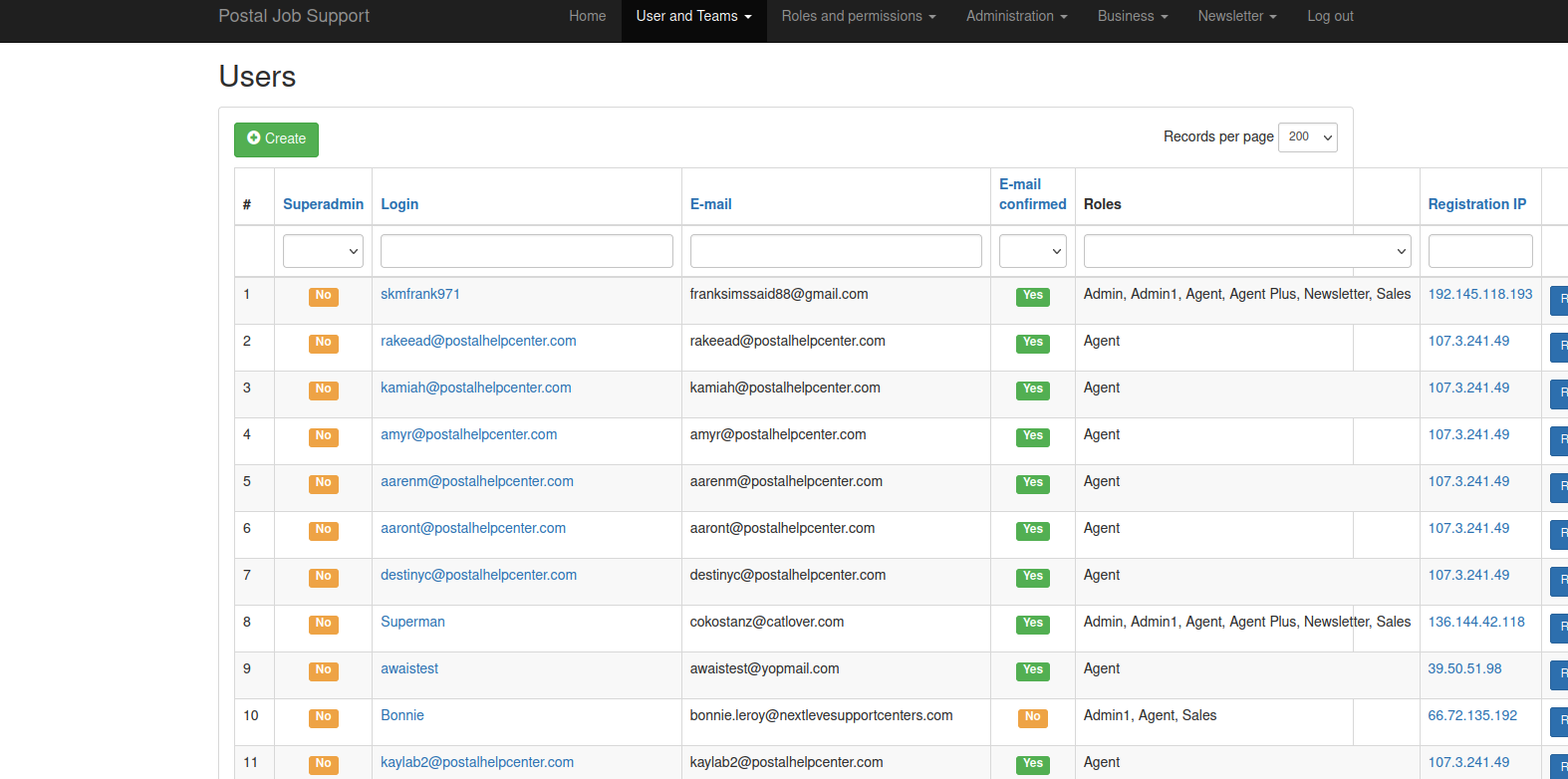
The US Job Services website has more than 160 users, including most of the employees at Next Level Support.
The website for NextLevelSupport says it was founded in 2017 by a Gary Plott, whose LinkedIn profile describes him as a seasoned telecommunications industry expert. The leaked backend database for US Job Services says Plott is a current administrator on the system, along with several other Nextlevel founders listed on the company’s site.
Reached via telephone, Plott initially said his company was merely a “white label” call center that multiple clients use to interact with customers, and that the content their call center is responsible for selling on behalf of US Job Services was not produced by NextLevelSupport.
“A few years ago, we started providing support for this postal product,” Plott said. “We didn’t develop the content but agreed we would support it.”
Interestingly, DomainTools says the Gmail address used by Plott in the US Jobs system was also used to register multiple USPS job-related domains, including postaljobssite[.]com, postalwebsite[.]com, usps-nlf[.]com, usps-nla[.]com.
Asked to reconcile this with his previous statement, Plott said he never did anything with those sites but acknowledged that his company did decide to focus on the US Postal jobs market from the very beginning.
Plott said his company never refuses to issue a money-back request from a customer, because doing so would result in costly chargebacks for NextLevel (and presumably for the many credit card merchant accounts apparently set up by Mr. Mirza).
“We’ve never been deceptive,” Plott said, noting that customers of the US Job Services product receive a digital download with tips on how to handle a USPS interview, as well as unlimited free telephone support if they need it.
“We’ve never told anyone we were the US Postal Service,” Plott continued. “We make sure people fully understand that they are not required to buy this product, but we think we can help you and we have testimonials from people we have helped. But ultimately you as the customer make that decision.”
An email address in the US Job Services teams page for another user — Stephanie Dayton — was used to register the domains postalhiringreview[.]com, and postalhiringreviewboard[.]org back in 2014. Reached for comment, Ms. Dayton said she has provided assistance to Next Level Support Centers with their training and advertising, but never in the capacity as an employee.
Perhaps the most central NextLevel associate who had access to US Job Services was Russell Ramage, a telemarketer from Warner Robins, Georgia. Ramage is listed in South Carolina incorporation records as the owner of a now-defunct call center service called Smart Logistics, a company whose name appears in the website registration records for several early and long-running US Job Services sites.

According to the state of Georgia, Russell Ramage was the registered agent of several USPS job-themed companies.
The leaked records show the email address used by Ramage also registered multiple USPS jobs-related domains, including postalhiringcenter[.]com, postalhiringreviews[.]com, postaljobs-email[.]com, and postaljobssupport1[.]com.
A review of business incorporation records in Georgia indicate Ramage was the registered agent for at least three USPS-related companies over the years, including Postal Career Placement LLC, Postal Job Services Inc., and Postal Operations Inc. All three companies were founded in 2015, and are now dissolved.
An obituary dated February 2023 says Russell Ramage recently passed away at the age of 41. No cause of death was stated, but the obituary goes on to say that Russ “Rusty” Ramage was “preceded in death by his mother, Anita Lord Ramage, pets, Raine and Nola and close friends, Nicole Reeves and Ryan Rawls.”
In 2014, then 33-year-old Ryan “Jootgater” Rawls of Alpharetta, Georgia pleaded guilty to conspiring to distribute controlled substances. Rawls also grew up in Warner Robins, and was one of eight suspects charged with operating a secret darknet narcotics ring called the Farmer’s Market, which federal prosecutors said trafficked in millions of dollars worth of controlled substances.
Reuters reported that an eighth suspect in that case had died by the time of Rawls’ 2014 guilty plea, although prosecutors declined to offer further details about that. According to his obituary, Ryan Christopher Rawls died at the age of 38 on Jan. 28, 2019.
In a comment on Ramage’s memorial wall, Stephanie Dayton said she began working with Ramage in 2006.
“Our friendship far surpassed a working one, we had a very close bond and became like brother and sister,” Dayton wrote. “I loved Russ deeply and he was like family. He was truly one of the best human beings I have ever known. He was kind and sweet and truly cared about others. Never met anyone like him. He will be truly missed. RIP brother.”
The FTC and USPS note that while applicants for many entry-level postal jobs are required to take a free postal exam, the tests are usually offered only every few years in any particular district, and there are no job placement guarantees based on score.
“If applicants pass the test by scoring at least 70 out of 100, they are placed on a register, ranked by their score,” the FTC explained. “When a position becomes open, the local post office looks to the applicable register for that geographic location and calls the top three applicants. The score is only one of many criteria taken into account for employment. The exams test general aptitude, something that cannot necessarily be increased by studying.”
The FTC says anyone interested in a job at the USPS should inquire at their local postal office, where applicants generally receive a free packet of information about required exams. More information about job opportunities at the postal service is available at the USPS’s careers website.
Michael Martel, spokesperson for the United States Postal Inspection Service, said in a written statement that the USPS has no affiliation with the websites or companies named in this story.
“To learn more about employment with USPS, visit USPS.com/careers,” Martel wrote. “If you are the victim of a crime online report it to the FBI’s Internet Crime Complaint Center (IC3) at www.ic3.gov. To report fraud committed through or toward the USPS, its employees, or customers, report it to the United States Postal Inspection Service (USPIS) at www.uspis.gov/report.”
According to the leaked back-end server for US Job Services, here is a list of the current sites selling this product:
usjobshelpcenter[.]com
usjobhelpcenter[.]com
job-postal[.]com
localpostalhiring[.]com
uspostalrecruitment[.]com
postalworkerjob[.]com
next-level-now[.]com
postalhiringcenters[.]com
postofficehiring[.]com
postaljobsplacement[.]com
postal-placement[.]com
postofficejobopenings[.]com
postalexamprep[.]com
postaljobssite[.]com
postalwebsite[.]com
postalcareerscenters[.]com
postal-hiring[.]com
postal-careers[.]com
postal-guide[.]com
postal-hiring-guide[.]com
postal-openings[.]com
postal-placement[.]com
postofficeplacements[.]com
postalplacementservices[.]com
postaljobs20[.]com
postal-jobs-placement[.]com
postaljobopenings[.]com
postalemployment[.]com
postaljobcenters[.]com
postalmilitarycareers[.]com
epostaljobs[.]com
postal-job-center[.]com
postalcareercenter[.]com
postalhiringcenters[.]com
postal-job-center[.]com
postalcareercenter[.]com
postalexamprep[.]com
postalplacementcenters[.]com
postalplacementservice[.]com
postalemploymentservices[.]com
uspostalhiring[.]com






A shocking number of organizations — including banks and healthcare providers — are leaking private and sensitive information from their public Salesforce Community websites, KrebsOnSecurity has learned. The data exposures all stem from a misconfiguration in Salesforce Community that allows an unauthenticated user to access records that should only be available after logging in.
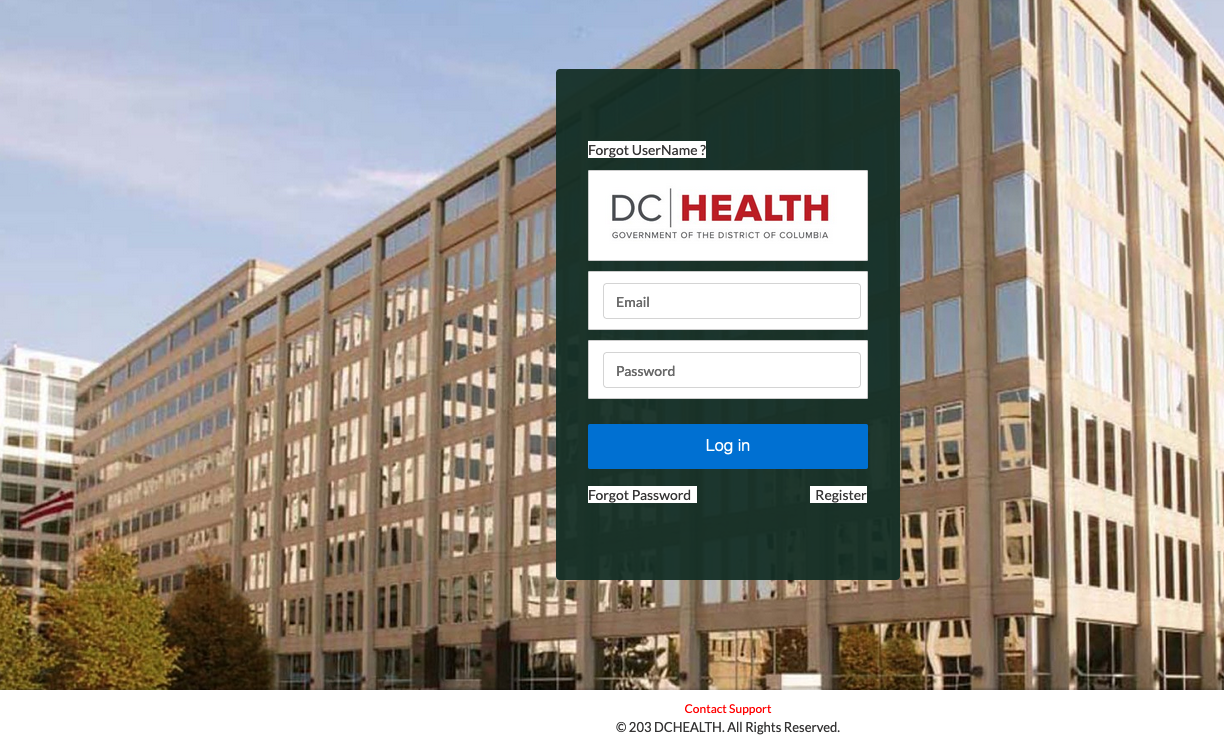
A researcher found DC Health had five Salesforce Community sites exposing data.
Salesforce Community is a widely-used cloud-based software product that makes it easy for organizations to quickly create websites. Customers can access a Salesforce Community website in two ways: Authenticated access (requiring login), and guest user access (no login required). The guest access feature allows unauthenticated users to view specific content and resources without needing to log in.
However, sometimes Salesforce administrators mistakenly grant guest users access to internal resources, which can cause unauthorized users to access an organization’s private information and lead to potential data leaks.
Until being contacted by this reporter on Monday, the state of Vermont had at least five separate Salesforce Community sites that allowed guest access to sensitive data, including a Pandemic Unemployment Assistance program that exposed the applicant’s full name, Social Security number, address, phone number, email, and bank account number.
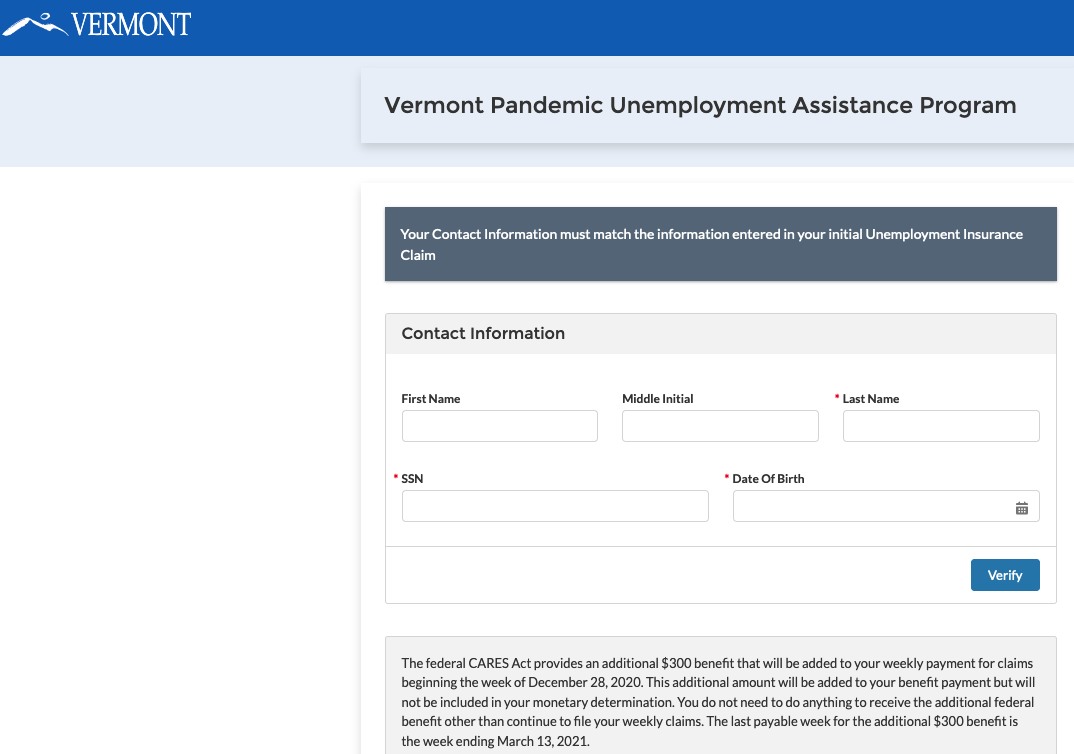
This misconfigured Salesforce Community site from the state of Vermont was leaking pandemic assistance loan application data, including names, SSNs, email address and bank account information.
Vermont’s Chief Information Security Officer Scott Carbee said his security teams have been conducting a full review of their Salesforce Community sites, and already found one additional Salesforce site operated by the state that was also misconfigured to allow guest access to sensitive information.
“My team is frustrated by the permissive nature of the platform,” Carbee said.
Carbee said the vulnerable sites were all created rapidly in response to the Coronavirus pandemic, and were not subjected to their normal security review process.
“During the pandemic, we were largely standing up tons of applications, and let’s just say a lot of them didn’t have the full benefit of our dev/ops process,” Carbee said. “In our case, we didn’t have any native Salesforce developers when we had to suddenly stand up all these sites.”
Earlier this week, KrebsOnSecurity notified Columbus, Ohio-based Huntington Bank that its recently acquired TCF Bank had a Salesforce Community website that was leaking documents related to commercial loans. The data fields in those loan applications included name, address, full Social Security number, title, federal ID, IP address, average monthly payroll, and loan amount.
Huntington Bank has disabled the leaky TCF Bank Salesforce website. Matthew Jennings, deputy chief information security officer at Huntington, said the company was still investigating how the misconfiguration occurred, how long it lasted, and how many records may have been exposed.
KrebsOnSecurity learned of the leaks from security researcher Charan Akiri, who said he wrote a program that identified hundreds of other organizations running misconfigured Salesforce pages. But Akiri said he’s been wary of probing too far, and has had difficulty getting responses from most of the organizations he has notified to date.
“In January and February 2023, I contacted government organizations and several companies, but I did not receive any response from these organizations,” Akiri said. “To address the issue further, I reached out to several CISOs on LinkedIn and Twitter. As a result, five companies eventually fixed the problem. Unfortunately, I did not receive any responses from government organizations.”
The problem Akiri has been trying to raise awareness about came to the fore in August 2021, when security researcher Aaron Costello published a blog post explaining how misconfigurations in Salesforce Community sites could be exploited to reveal sensitive data (Costello subsequently published a follow-up post detailing how to lock down Salesforce Community sites).
On Monday, KrebsOnSecurity used Akiri’s findings to notify Washington D.C. city administrators that at least five different public DC Health websites were leaking sensitive information. One DC Health Salesforce Community website designed for health professionals seeking to renew licenses with the city leaked documents that included the applicant’s full name, address, Social Security number, date of birth, license number and expiration, and more.
Akiri said he notified the Washington D.C. government in February about his findings, but received no response. Reached by KrebsOnSecurity, interim Chief Information Security Officer Mike Rupert initially said the District had hired a third party to investigate, and that the third party confirmed the District’s IT systems were not vulnerable to data loss from the reported Salesforce configuration issue.
But after being presented with a document including the Social Security number of a health professional in D.C. that was downloaded in real-time from the DC Health public Salesforce website, Rupert acknowledged his team had overlooked some configuration settings.
Washington, D.C. health administrators are still smarting from a data breach earlier this year at the health insurance exchange DC Health Link, which exposed personal information for more than 56,000 users, including many members of Congress.
That data later wound up for sale on a top cybercrime forum. The Associated Press reports that the DC Health Link breach was likewise the result of human error, and said an investigation revealed the cause was a DC Health Link server that was “misconfigured to allow access to the reports on the server without proper authentication.”
Salesforce says the data exposures are not the result of a vulnerability inherent to the Salesforce platform, but they can occur when customers’ access control permissions are misconfigured.
“As previously communicated to all Experience Site and Sites customers, we recommend utilizing the Guest User Access Report Package to assist in reviewing access control permissions for unauthenticated users,” reads a Salesforce advisory from Sept. 2022. “Additionally, we suggest reviewing the following Help article, Best Practices and Considerations When Configuring the Guest User Profile.”
In a written statement, Salesforce said it is actively focused on data security for organizations with guest users, and that it continues to release “robust tools and guidance for our customers,” including:
Control Which Users Experience Cloud Site Users Can See
Best Practices and Considerations When Configuring the Guest User Profile
“We’ve also continued to update our Guest User security policies, beginning with our Spring ‘21 release with more to come in Summer ‘23,” the statement reads. “Lastly, we continue to proactively communicate with customers to help them understand the capabilities available to them, and how they can best secure their instance of Salesforce to meet their security, contractual, and regulatory obligations.”











The legislation aims to bolster the Union’s cyber-resilience and enhance its capabilities to prepare for, detect and respond to incidents
The post The EU’s Cyber Solidarity Act: Security Operations Centers to the rescue! appeared first on WeLiveSecurity

KrebsOnSecurity received a nice bump in traffic this week thanks to tweets from the Federal Bureau of Investigation (FBI) and the Federal Communications Commission (FCC) about “juice jacking,” a term first coined here in 2011 to describe a potential threat of data theft when one plugs their mobile device into a public charging kiosk. It remains unclear what may have prompted the alerts, but the good news is that there are some fairly basic things you can do to avoid having to worry about juice jacking.
On April 6, 2023, the FBI’s Denver office issued a warning about juice jacking in a tweet.
“Avoid using free charging stations in airports, hotels or shopping centers,” the FBI’s Denver office warned. “Bad actors have figured out ways to use public USB ports to introduce malware and monitoring software onto devices. Carry your own charger and USB cord and use an electrical outlet instead.”
Five days later, the Federal Communications Commission (FCC) issued a similar warning. “Think twice before using public charging stations,” the FCC tweeted. “Hackers could be waiting to gain access to your personal information by installing malware and monitoring software to your devices. This scam is referred to as juice jacking.”
The FCC tweet also provided a link to the agency’s awareness page on juice jacking, which was originally published in advance of the Thanksgiving Holiday in 2019 but was updated in 2021 and then again shortly after the FBI’s tweet was picked up by the news media. The alerts were so broadly and breathlessly covered in the press that a mention of juice jacking even made it into this week’s Late Late Show with James Corden.
The term juice jacking crept into the collective paranoia of gadget geeks in the summer of 2011, thanks to the headline for a story here about researchers at the DEFCON hacker convention in Vegas who’d set up a mobile charging station designed to educate the unwary to the reality that many mobile devices connected to a computer would sync their data by default.
Since then, Apple, Google and other mobile device makers have changed the way their hardware and software works so that their devices no longer automatically sync data when one plugs them into a computer with a USB charging cable. Instead, users are presented with a prompt asking if they wish to trust a connected computer before any data transfer can take place.
On the other hand, the technology needed to conduct a sneaky juice jacking attack has become far more miniaturized, accessible and cheap. And there are now several products anyone can buy that are custom-built to enable juice jacking attacks.
Probably the best known example is the OMG cable, a $180 hacking device made for professional penetration testers that looks more or less like an Apple or generic USB charging cable. But inside the OMG cable is a tiny memory chip and a Wi-Fi transmitter that creates a Wi-Fi hotspot, to which the attacker can remotely connect using a smartphone app and run commands on the device.

The $180 “OMG cable.” Image: hak5.org.
Brian Markus is co-founder of Aries Security, and one of the researchers who originally showcased the threat from juice jacking at the 2011 DEFCON. Markus said he isn’t aware of any public accounts of juice jacking kiosks being found in the wild, and said he’s unsure what prompted the recent FBI alert.
But Markus said juice jacking is still a risk because it is far easier and cheaper these days for would-be attackers to source and build the necessary equipment.
“Since then, the technology and components have become much smaller and very easy to build, which puts this in the hands of less sophisticated threat actors,” Markus said. “Also, you can now buy all this stuff over the counter. I think the risk is possibly higher now than it was a decade ago, because a much larger population of people can now pull this off easily.”
How seriously should we take the recent FBI warning? An investigation by the myth-busting site Snopes suggests the FBI tweet was just a public service announcement based on a dated advisory. Snopes reached out to both the FBI and the FCC to request data about how widespread the threat of juice jacking is in 2023.
“The FBI replied that its tweet was a ‘standard PSA-type post’ that stemmed from the FCC warning,” Snopes reported. “An FCC spokesperson told Snopes that the commission wanted to make sure that their advisory on “juice-jacking,” first issued in 2019 and later updated in 2021, was up-to-date so as to ensure ‘the consumers have the most up-to-date information.’ The official, who requested anonymity, added that they had not seen any rise in instances of consumer complaints about juice-jacking.”
What can you do to avoid juice jacking? Bring your own gear. A general rule of thumb in security is that if an adversary has physical access to your device, you can no longer trust the security or integrity of that device. This also goes for things that plug into your devices.
Juice jacking isn’t possible if a device is charged via a trusted AC adapter, battery backup device, or through a USB cable with only power wires and no data wires present. If you lack these things in a bind and still need to use a public charging kiosk or random computer, at least power your device off before plugging it in.













John Clifton Davies, a 60-year-old con man from the United Kingdom who fled the country in 2015 before being sentenced to 12 years in prison for fraud, has enjoyed a successful life abroad swindling technology startups by pretending to be a billionaire investor. Davies’ newest invention appears to be “CodesToYou,” which purports to be a “full cycle software development company” based in the U.K.
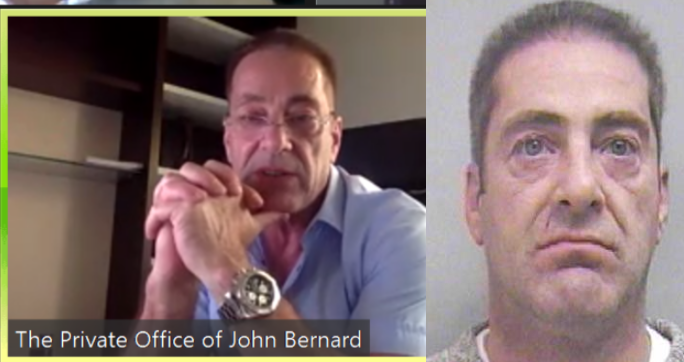
The scam artist John Bernard a.k.a. Alan John Mykailov (left) in a recent Zoom call, and a mugshot of John Clifton Davies from nearly a decade earlier.
Several articles here have delved into the history of John Bernard, the pseudonym used by a fake billionaire technology investor who tricked dozens of startups into giving him tens of millions of dollars.
John Bernard’s real name is John Clifton Davies, a convicted fraudster from the United Kingdom who is currently a fugitive from justice. For several years until reinventing himself again quite recently, Bernard pretended to be a billionaire Swiss investor who made his fortunes in the dot-com boom 20 years ago.
“The Private Office of John Bernard” let it be known to investment brokers that he had tens of millions of dollars to invest in tech startups, and he attracted a stream of new victims by offering extraordinarily generous finder’s fees to brokers who helped him secure new clients. But those brokers would eventually get stiffed because Bernard’s company would never consummate a deal.

John Bernard’s former website, where he pretended to be a billionaire tech investor.
Bernard would promise to invest millions in tech startups, and then insist that companies pay tens of thousands of dollars worth of due diligence fees up front. However, the due diligence company he insisted on using — another Swiss firm called The Inside Knowledge GmbH — also was secretly owned by Bernard, who would invariably pull out of the deal after receiving the due diligence money.
A variety of clues suggest Davies has recently adopted at least one other identity — Alan John Mykhailov — who is listed as chairman of a British concern called CodesToYou LTD, incorporated in May 2022. The CodesToYou website says the company employs talented coders in several countries, and that its programmers offer “your ultimate balance between speed, cost and quality.”

The team from CodesToYou.
In response to questions from KrebsOnSecurity, CodesToYou’s marketing manager — who gave their name only as “Zhena” — said the company was not affiliated with any John Bernard or John Clifton Davies, and maintained that CodesToYou is a legitimate enterprise.
But publicly available information about this company and its leadership suggests otherwise. Official incorporation documents from the U.K.’s Companies House represent that CodesToYou is headed by an Alan John Mykhailov, a British citizen born in March 1958.
Companies House says Mykhailov is an officer in three other companies, including one called Blackstone Corporate Alliance Ltd. According to the Swiss business tracking service business-monitor.ch, Blackstone Corporate Alliance Ltd. is currently the entity holding a decision-making role in John Bernard’s fake due diligence company — The Inside Knowledge GmbH — which is now in liquidation.
A screen shot of the stock photos and corporate-speak on John Bernard’s old website. Image: Archive.org
Also listed as a partner in Blackstone Corporate Alliance Limited is Igor Hubskyi (a.k.a. Igor Gubskyi), a Ukrainian man who was previously president of The Inside Knowledge GmbH.
The CodesToYou website says the company’s marketing team lead is Maria Yakovleva, and the photo of this employee matches the profile for the LinkedIn account name “Maria Y.” That same LinkedIn profile and photo previously listed Maria by a different first and last name — Mariya Kulikova; back then, Ms. Kulikova’s LinkedIn profile said she was an executive assistant in The Private Office of Mr. John Bernard.
Companies House lists Alan John Mykhailov as a current officer in two other companies, including Frisor Limited, and Ardelis Solutions Limited. A cached copy of the now-defunct Ardelis Solutions website says it was a private equity firm.
CodesToYou’s Maria also included Ardelis Solutions in the work history section of her LinkedIn resume. That is, until being contacted by this author on LinkedIn, after which Maria’s profile picture and any mention of Ardelis Solutions were deleted.
Listed as head of business development at CodesToYou is David Bruno, a Canadian man whose LinkedIn profile says he is founder of an organization called “World Privacy Resource.” As KrebsOnSecurity reported in 2020, Bruno was at the time promoting himself as the co-CEO of a company called SafeSwiss Secure Communication AG, and the founder of another tech startup called Secure Swiss Data.
Secure Swiss Data’s domain — secureswissdata.com — is a Swiss concern that sells encrypted email and data services. According to DomainTools.com, that website name was registered in 2015 by The Inside Knowledge GmbH. In February 2020, a press release announced that Secure Swiss Data was purchased in an “undisclosed multimillion buyout” by SafeSwiss Secure Communication AG.
A cached copy of the Ardelis Solutions website, which said it was a private equity firm and included similar stock images as John Bernard’s investment website.
When reached in 2020 and asked about his relationship to Mr. Bernard, Mr. Bruno said the two were business partners and that he couldn’t imagine that Mr. Bernard would be involved in anything improper. To this day Mr. Bruno is the only person I’ve spoken to who has had anything positive to say about Mr. Bernard.
Mr. Bruno did not respond to requests for comment this time around, but his LinkedIn profile no longer makes any mention of Secure Swiss Data or SafeSwiss — both companies he claimed to run for many years. Nor does it mention CodesToYou. However, Mr. Bruno’s former company SafeSwiss is listed as one of the six “portfolio” companies whose services are promoted on the CodesToYou website.
In mid-2021, Bruno announced he was running for public office in Ontario.
“The Kenora resident is no stranger to the government as he contributed to Canada’s new Digital Charter, Bill C-11, which is a new Cyber Security policy,” reported Drydennow.com, a news website that covers Northwestern Ontario. Drydennow says the next federal election is expected to be held on or before Oct. 16, 2023.
John Clifton Davies was convicted in 2015 of swindling businesses throughout the U.K. that were struggling financially and seeking to restructure their debt. For roughly six years, Davies ran a series of firms that pretended to offer insolvency services, but instead simply siphoned what little remaining money these companies had.
The very first entity mentioned in the technology portfolio advertised on the CodesToYou website is called “MySolve,” and it purports to offer a “multi-feature platform for insolvency practitioners.”
Mr. Davies’ fourth wife, Iryna Davies, is listed as a director of one of the insolvency consulting businesses in the U.K. that was part of John Davies’ 2015 fraud conviction. Prior to his trial for fraud, Davies served 16 months in jail before being cleared of murdering his third wife on their honeymoon in India: Colette Davies, 39, died after falling 80 feet from a viewing point at a steep gorge in the Himachal Pradesh region of India.
Mr. Davies was charged with murder and fraud after he attempted to collect GBP 132,000 in her life insurance payout, but British prosecutors ultimately conceded they did not have enough evidence to convict him.
The scams favored by Davies and his alter egos are smart because he never approaches investors directly; rather, investors are incentivized to put his portfolio in front of tech firms seeking financial backing. And all the best cons begin as an idea or possibility planted in the target’s mind.
It’s also a reliable scam because companies bilked by small-time investment schemes rarely pursue legal action, mainly because the legal fees involved can quickly surpass the losses. On top of that, many victims will likely be too ashamed to admit their duping. Victims who do press their case in court and win then face the daunting challenge of collecting damages from a slew of ephemeral shell corporations.
The latest Bernard victim to speak publicly — a Norwegian company hoping to build a fleet of environmentally friendly shipping vessels — is now embroiled in a lawsuit over a deal gone bad. As part of that scam, Bernard falsely claimed to have secured $100 million from six other wealthy investors, including the founder of Uber and the artist Abel Makkonen Tesfaye, better known as The Weeknd.
If you liked this story, check out my previous reporting on John Bernard/Davies:
Due Diligence That Money Can’t Buy
Who is Tech Investor John Bernard?
Promising Infusions of Cash, Fake Investor John Bernard Walked Away With $30 Million
Investment Scammer John Davies Reinvents Himself?
Fake Investor John Bernard Sinks Norwegian Green Shipping Dreams



How fraudsters groom their marks and move in for the kill using tricks from the playbooks of romance and investment scammers
The post Pig butchering scams: The anatomy of a fast‑growing threat appeared first on WeLiveSecurity



