
I'm going lead this post with where I finished the video because it brought the biggest smile to Charlotte's and my faces this week:
This. Is. Amazing 😍 pic.twitter.com/wOl4kpK841
— Troy Hunt (@troyhunt) March 3, 2023
When I talked about the McLaren in this week's video, Frits made the comment "the smile on your face says it all", which absolutely nailed it. But more than that, it brings a smile to the face of everyone who sees it (I suspect the colour helps), we're just loving seeing the excitement expressed by kids and adults alike. It's so much fun 😊
Less fun is dealing with Eye4Fraud. 24 hours on from recording this video, there's still zero visible progress and I lament that this one is just going to slip beneath the radar. If you're in the breach, do push for answers, it really shouldn't be this hard. All that and more in this week's video, enjoy!

Google is bidding adieu to an application that enabled Chrome users on Windows systems to get rid of unwanted software.…
Blackbaud has agreed to pay $3 million to settle charges that it made misleading disclosures about a 2020 ransomware infection in which crooks stole more than a million files on around 13,000 of the cloud software slinger's customers.…








According to the Monetary Authority of Singapore (MAS), trade barriers between US and China have resulted in geoeconomic fragmentation and will likely result in slower global growth and higher inflation.…
A request to move an online conversation to a supposedly more secure platform may not be as well-meaning as it sounds
The post APT hackers set a honeytrap to ensnare victims – Week in security with Tony Anscombe appeared first on WeLiveSecurity
Here's a roundup of some of the most common tricks that fraudsters use to dupe their victims on WhatsApp – and what you can do to protect yourself against them.
The post Common WhatsApp scams and how to avoid them appeared first on WeLiveSecurity
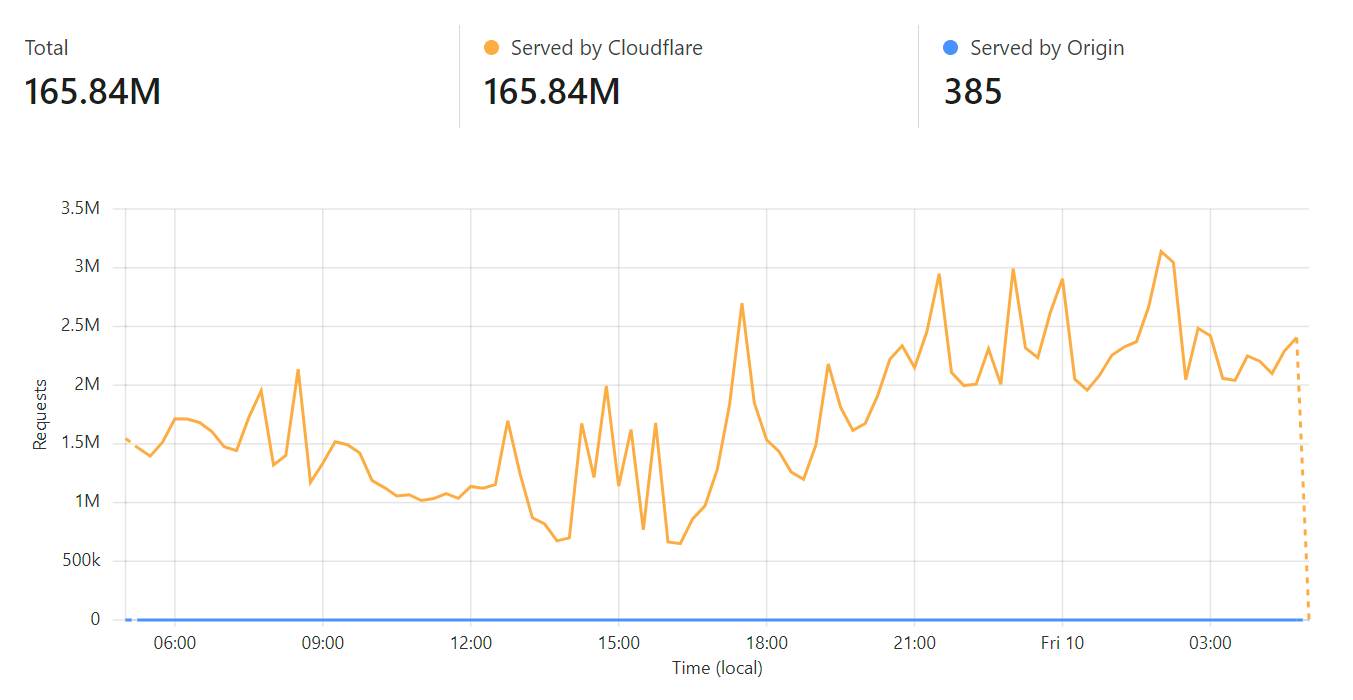
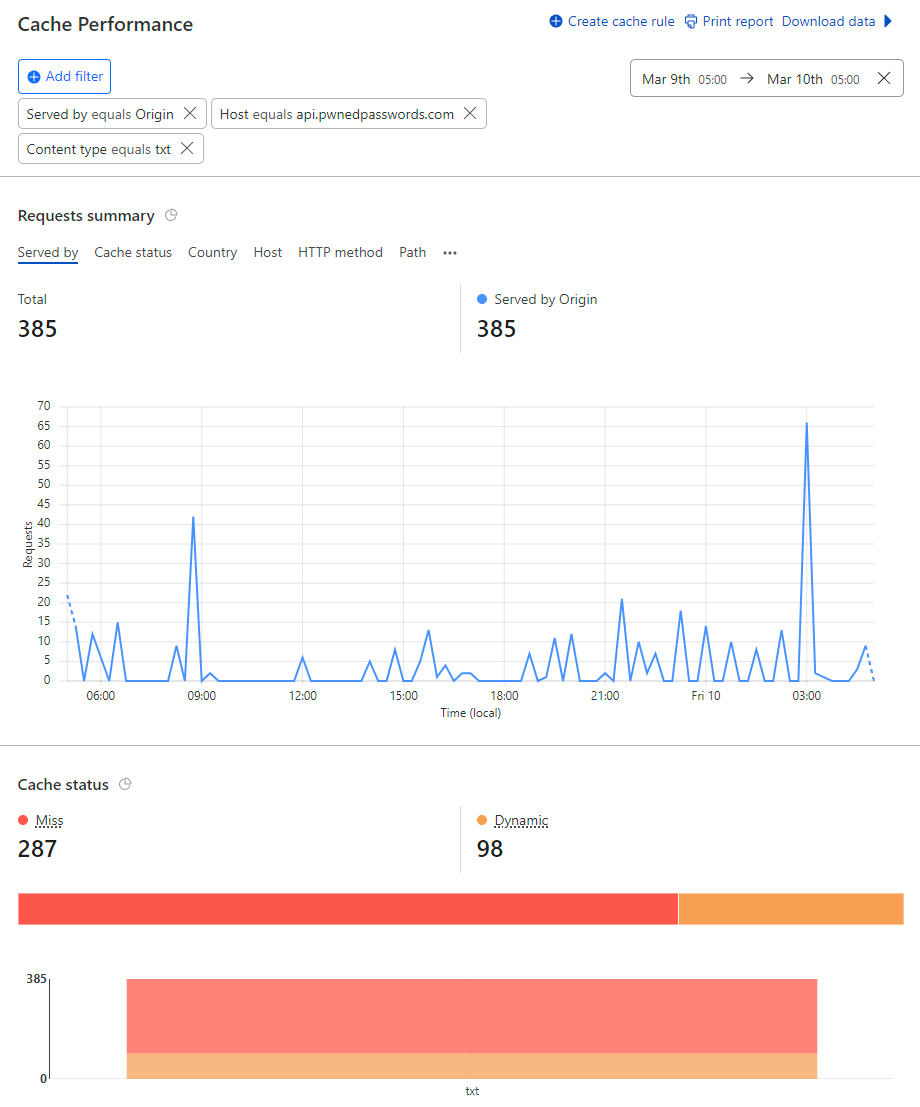
What if I told you... that you could run a website from behind Cloudflare and only have 385 daily requests miss their cache and go through to the origin service?
No biggy, unless... that was out of a total of more than 166M requests in the same period:
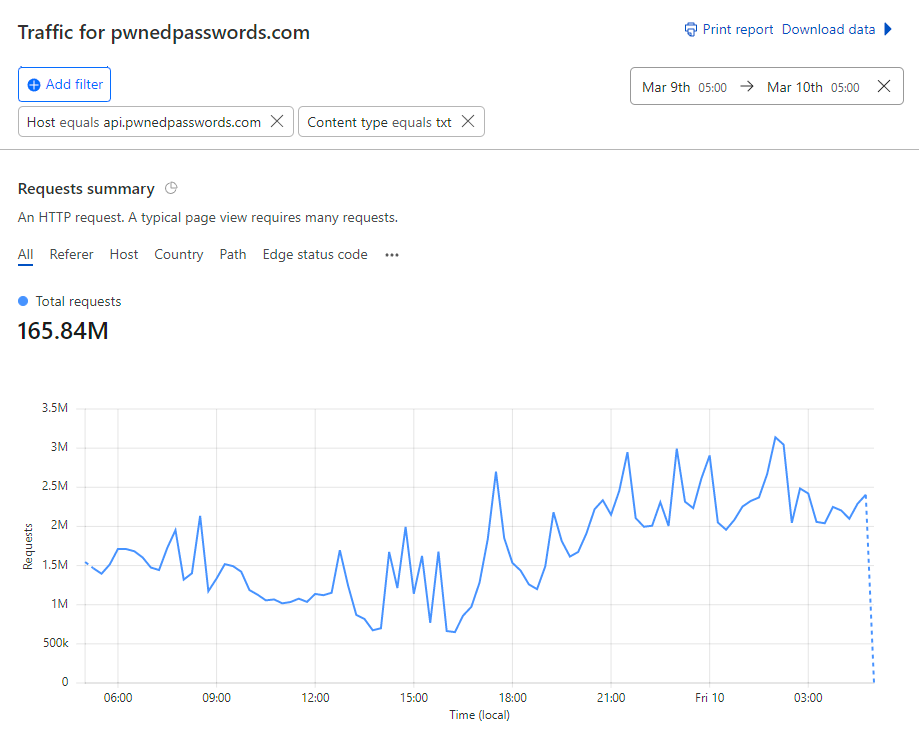
Yep, we just hit "five nines" of cache hit ratio on Pwned Passwords being 99.999%. Actually, it was 99.9998% but we're at the point now where that's just splitting hairs, let's talk about how we've managed to only have two requests in a million hit the origin, beginning with a bit of history:
Optimising Caching on Pwned Passwords (with Workers)- @troyhunt - https://t.co/KjBtCwmhmT pic.twitter.com/BSfJbWyxMy
— Cloudflare (@Cloudflare) August 9, 2018
Ah, memories 😊 Back then, Pwned Passwords was serving way fewer requests in a month than what we do in a day now and the cache hit ratio was somewhere around 92%. Put another way, instead of 2 in every million requests hitting the origin it was 85k. And we were happy with that! As the years progressed, the traffic grew and the caching model was optimised so our stats improved:
There it is - Pwned Passwords is now doing north of 2 *billion* requests a month, peaking at 91.59M in a day with a cache-hit ratio of 99.52%. All free, open source and out there for the community to do good with 😊 pic.twitter.com/DSJOjb2CxZ
— Troy Hunt (@troyhunt) May 24, 2022
And that's pretty much where we levelled out, at about the 99-and-a-bit percent mark. We were really happy with that as it was now only 5k requests per million hitting the origin. There was bound to be a number somewhere around that mark due to the transient nature of cache and eviction criteria inevitably meaning a Cloudflare edge node somewhere would need to reach back to the origin website and pull a new copy of the data. But what if Cloudflare never had to do that unless explicitly instructed to do so? I mean, what if it just stayed in their cache unless we actually changed the source file and told them to update their version? Welcome to Cloudflare Cache Reserve:
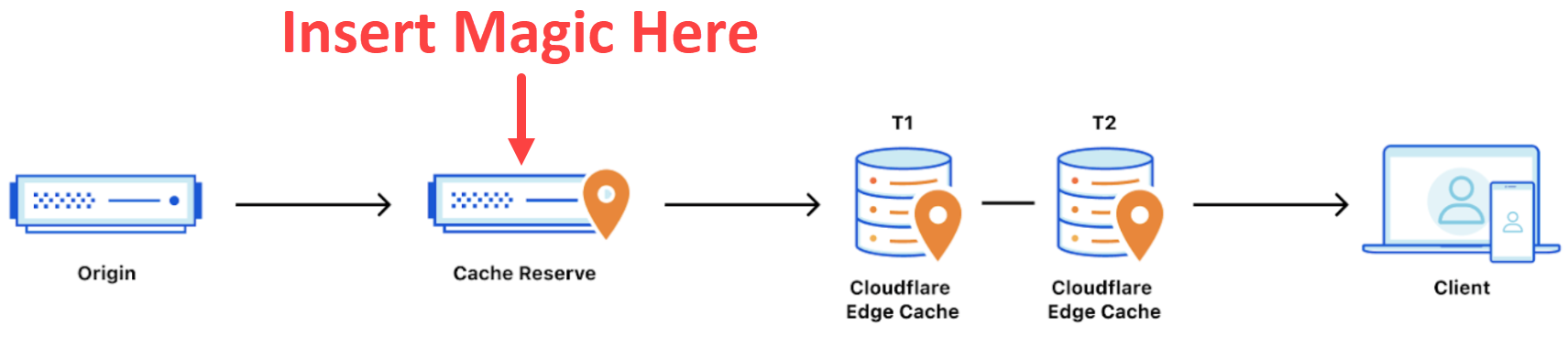
Ok, so I may have annotated the important bit but that's what it feels like - magic - because you just turn it on and... that's it. You still serve your content the same way, you still need the appropriate cache headers and you still have the same tiered caching as before, but now there's a "cache reserve" sitting between that and your origin. It's backed by R2 which is their persistent data store and you can keep your cached things there for as long as you want. However, per the earlier link, it's not free:
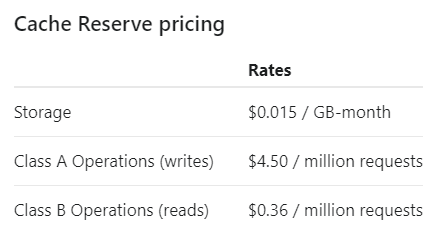
You pay based on how much you store for how long, how much you write and how much you read. Let's put that in real terms and just as a brief refresher (longer version here), remember that Pwned Passwords is essentially just 16^5 (just over 1 million) text files of about 30kb each for the SHA-1 hashes and a similar number for the NTLM ones (albeit slight smaller file sizes). Here are the Cache Reserve usage stats for the last 9 days:
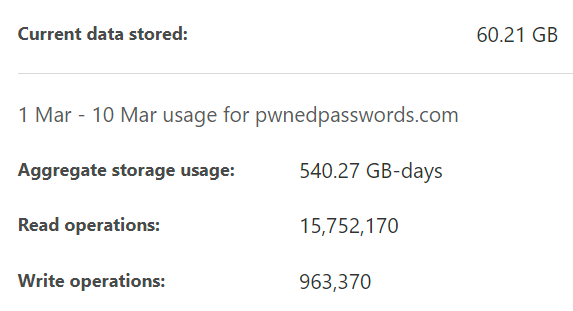
We can now do some pretty simple maths with that and working on the assumption of 9 days, here's what we get:
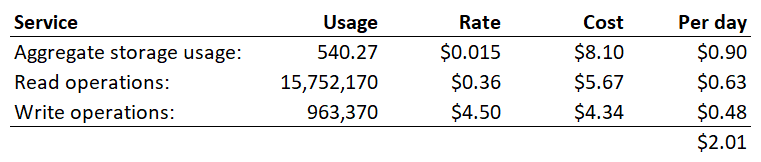
2 bucks a day 😲 But this has taken nearly 16M requests off my origin service over this period of time so I haven't paid for the Azure Function execution (which is cheap) nor the egress bandwidth (which is not cheap). But why are there only 16M read operations over 9 days when earlier we saw 167M requests to the API in a single day? Because if you scroll back up to the "insert magic here" diagram, Cache Reserve is only a fallback position and most requests (i.e. 99.52% of them) are still served from the edge caches.
Note also that there are nearly 1M write operations and there are 2 reasons for this:
An untold number of businesses rely on Pwned Passwords as an integral part of their registration, login and password reset flows. Seriously, the number is "untold" because we have no idea who's actually using it, we just know the service got hit three and a quarter billion times in the last 30 days:
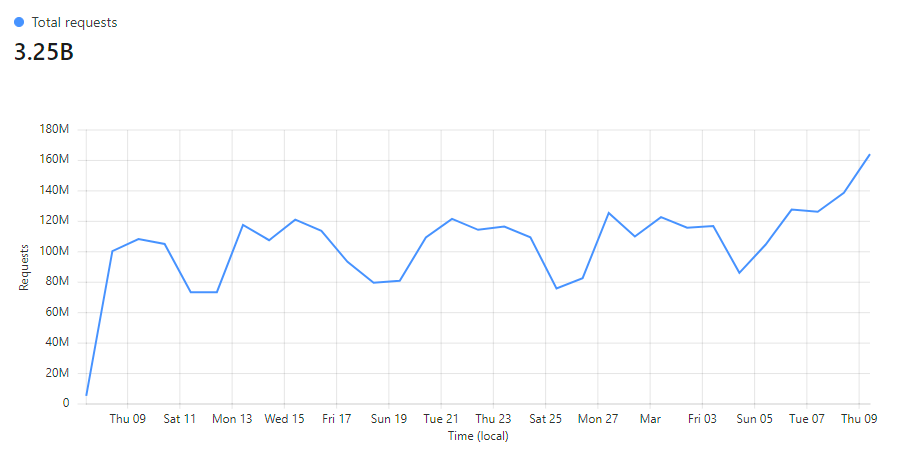
Giving consumers of the service confidence that not only is it highly resilient, but also massively fast is essential to adoption. In turn, more adoption helps drive better password practices, less account takeovers and more smiles all round 😊
As those remaining hash prefixes populate Cache Reserve, keep an eye on the "cf-cache-status" response header. If you ever see a value of "MISS" then congratulations, you're literally one in a million!
Full disclosure: Cloudflare provides services to HIBP for free and they helped in getting Cache Reserve up and running. However, they had no idea I was writing this blog post and reading it live in its entirety is the first anyone there has seen it. Surprise! 👋

The CISO of Acronis has downplayed what appeared to be an intrusion into its systems, insisting only one customer was affected, using stolen credentials, and that all other data remains safe.…
A Catholic clergy conformance organization has reportedly been buying up tracking data from mobile apps to identify gay priests, and providing that information to bishops around America.…
International law enforcement agencies have claimed another victory over cyber criminals, after seizing the website, and taking down the infrastructure operated by crims linked to the NetWire remote access trojan (RAT).…
AT&T has confirmed that miscreants had access to nine million of its wireless customers' account details after a vendor's network was broken into in January.…
Health data and other personal information of members of Congress and staff were stolen during a breach of servers run by DC Health Care Link and are now up for sale on the dark web.…

Today, we released the latest issue of The Domain Name Industry Brief, which shows that the fourth quarter of 2022 closed with 350.4 million domain name registrations across all top-level domains (TLDs), an increase of 0.5 million domain name registrations, or 0.1%, compared to the third quarter of 2022.1,2 Domain name registrations have increased by 8.7 million, or 2.6%, year over year.1,2

Check out the latest issue of The Domain Name Industry Brief to see domain name stats from the fourth quarter of 2022, including:
• Top 10 Largest TLDs by Number of Reported Domain Names
• Top 10 Largest ccTLDs by Number of Reported Domain Names
• ngTLDs as Percentage of Total TLDs
• Geographical ngTLDs as Percentage of Total Corresponding Geographical TLDs
To see past issues of The Domain Name Industry Brief, please visit https://verisign.com/dnibarchives.
The post Verisign Domain Name Industry Brief: 350.4 Million Domain Name Registrations in the Fourth Quarter of 2022 appeared first on Verisign Blog.



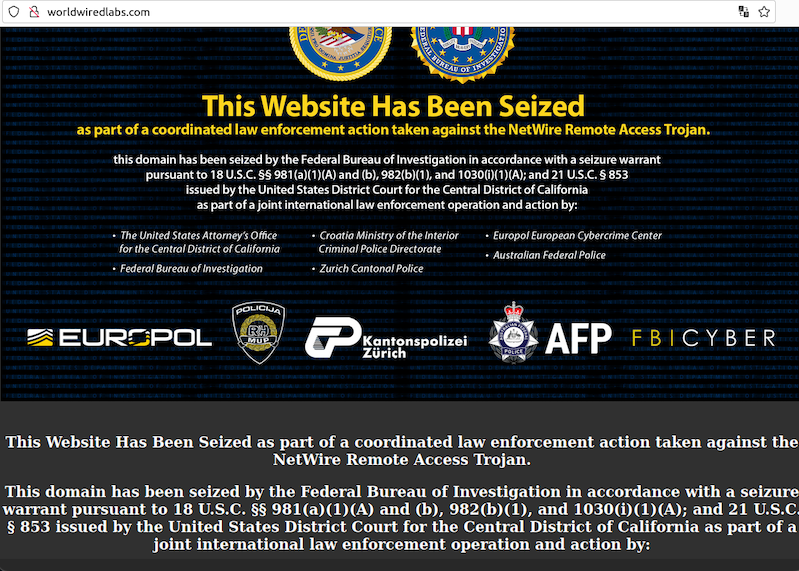
A Croatian national has been arrested for allegedly operating NetWire, a Remote Access Trojan (RAT) marketed on cybercrime forums since 2012 as a stealthy way to spy on infected systems and siphon passwords. The arrest coincided with a seizure of the NetWire sales website by the U.S. Federal Bureau of Investigation (FBI). While the defendant in this case hasn’t yet been named publicly, the NetWire website has been leaking information about the likely true identity and location of its owner for the past 11 years.
Typically installed by booby-trapped Microsoft Office documents and distributed via email, NetWire is a multi-platform threat that is capable of targeting not only Microsoft Windows machines but also Android, Linux and Mac systems.
NetWire’s reliability and relatively low cost ($80-$140 depending on features) has made it an extremely popular RAT on the cybercrime forums for years, and NetWire infections consistently rank among the top 10 most active RATs in use.
NetWire has been sold openly on the same website since 2012: worldwiredlabs[.]com. That website now features a seizure notice from the U.S. Department of Justice (DOJ), which says the domain was taken as part of “a coordinated law enforcement action taken against the NetWire Remote Access Trojan.”
“As part of this week’s law enforcement action, authorities in Croatia on Tuesday arrested a Croatian national who allegedly was the administrator of the website,” reads a statement by the DOJ today. “This defendant will be prosecuted by Croatian authorities. Additionally, law enforcement in Switzerland on Tuesday seized the computer server hosting the NetWire RAT infrastructure.”
Neither the DOJ’s statement nor a press release on the operation published by Croatian authorities mentioned the name of the accused. But it’s fairly remarkable that it has taken so long for authorities in the United States and elsewhere to move against NetWire and its alleged proprietor, given that the RAT’s author apparently did very little to hide his real-life identity.
The WorldWiredLabs website first came online in February 2012 using a dedicated host with no other domains. The site’s true WHOIS registration records have always been hidden by privacy protection services, but there are plenty of clues in historical Domain Name System (DNS) records for WorldWiredLabs that point in the same direction.
In October 2012, the WorldWiredLabs domain moved to another dedicated server at the Internet address 198.91.90.7, which was home to just one other domain: printschoolmedia[.]org, also registered in 2012.
According to DomainTools.com, printschoolmedia[.]org was registered to a Mario Zanko in Zapresic, Croatia, and to the email address zankomario@gmail.com. DomainTools further shows this email address was used to register one other domain in 2012: wwlabshosting[.]com, also registered to Mario Zanko from Croatia.
A review of DNS records for both printschoolmedia[.]org and wwlabshosting[.]com shows that while these domains were online they both used the DNS name server ns1.worldwiredlabs[.]com. No other domains have been recorded using that same name server.

The WorldWiredLabs website, in 2013. Source: Archive.org.
DNS records for worldwiredlabs[.]com also show the site forwarded incoming email to the address tommaloney@ruggedinbox.com. Constella Intelligence, a service that indexes information exposed by public database leaks, shows this email address was used to register an account at the clothing retailer romwe.com, using the password “123456xx.”
Running a reverse search on this password in Constella Intelligence shows there are more than 450 email addresses known to have used this credential, and two of those are zankomario@gmail.com and zankomario@yahoo.com.
A search on zankomario@gmail.com in Skype returns three results, including the account name “Netwire” and the username “Dugidox,” and another for a Mario Zanko (username zanko.mario).
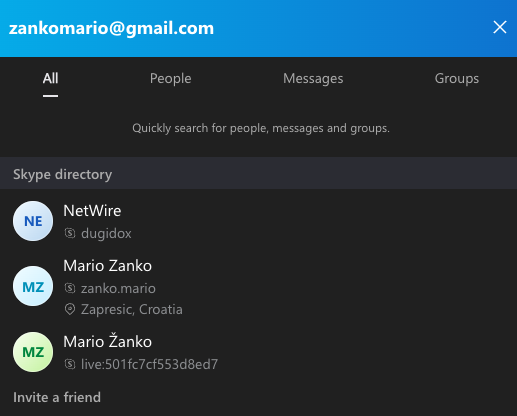 Dugidox corresponds to the hacker handle most frequently associated with NetWire sales and support discussion threads on multiple cybercrime forums over the years.
Dugidox corresponds to the hacker handle most frequently associated with NetWire sales and support discussion threads on multiple cybercrime forums over the years.
Constella ties dugidox@gmail.com to a number of website registrations, including the Dugidox handle on BlackHatWorld and HackForums, and to IP addresses in Croatia for both. Constella also shows the email address zankomario@gmail.com used the password “dugidox2407.”
In 2010, someone using the email address dugidox@gmail.com registered the domain dugidox[.]com. The WHOIS registration records for that domain list a “Senela Eanko” as the registrant, but the address used was the same street address in Zapresic that appears in the WHOIS records for printschoolmedia[.]org, which is registered in Mr. Zanco’s name.
Prior to the demise of Google+, the email address dugidox@gmail.com mapped to an account with the nickname “Netwire wwl.” The dugidox email also was tied to a Facebook account (mario.zanko3), which featured check-ins and photos from various places in Croatia.
That Facebook profile is no longer active, but back in January 2017, the administrator of WorldWiredLabs posted that he was considering adding certain Android mobile functionality to his service. Three days after that, the Mario.Zank3 profile posted a photo saying he was selected for an Android instruction course — with his dugidox email in the photo, naturally.
Incorporation records from the U.K.’s Companies House show that in 2017 Mr. Zanko became an officer in a company called Godbex Solutions LTD. A Youtube video invoking this corporate name describes Godbex as a “next generation platform” for exchanging gold and cryptocurrencies.
The U.K. Companies House records show Godbex was dissolved in 2020. It also says Mr. Zanko was born in July 1983, and lists his occupation as “electrical engineer.”
Mr. Zanko did not respond to multiple requests for comment.
A statement from the Croatian police about the NetWire takedown is here.
Emotet is back. After another months-long lull since a spate of attacks in November 2022, the notorious malware operation that has already survived a law enforcement takedown and various periods of inactivity began sending out malicious emails on Tuesday morning.…
Suspected Chinese cyber criminals have zeroed in on unpatched SonicWall gateways and are infecting the devices with credential-stealing malware that persists through firmware upgrades, according to Mandiant.…
On Tuesday a bipartisan group of a dozen US senators introduced a bill to authorize the Commerce Department to ban information and communications technology products and services deemed threats to national security.…