As children’s safety and privacy online becomes a matter of increasing urgency, lawmakers around the world push ahead on new regulations in the digital realm
The post Online safety laws: What’s in store for children’s digital playgrounds? appeared first on WeLiveSecurity




“Where do we start?”
This is the question every CISO asks about every new program. In fact, I ask and answer that question many times a month. There’s a reason for this, of course. A strong start to any project builds momentum, reassures stakeholders, and sets the stage for what’s to come. Security resilience initiatives are no different. Security resilience is the ability to anticipate and respond to unpredictable threats or changes, and then emerge stronger. It’s hard to imagine a more vital undertaking for CISOs. And as with all initiatives, CISOs always want to know where to begin.
They’re likely to find some valuable starting points in the Security Outcomes Report, Volume 3: Achieving Security Resilience, the latest in a series of reports released by Cisco and reflecting the viewpoints of 4,700 IT and security professionals from 26 countries. The report identifies seven success factors CISOs can pursue to improve outcomes within their own enterprise security resilience programs, placing a high priority on security resilience. The seven success factors range in nature from the architectural—simplifying your hybrid IT environment, maximizing zero trust adoption—to more relationship-focused factors.
It’s the latter that caught my eye.
Seven success factors for resilience:
It shouldn’t surprise any CISO that the first two success factors are built around relationships. These factors zero in on relationships with company leadership (as measured by establishing executive support) and relationships with people across the organization (as measured by cultivating a culture of security). Experienced CISOs know that these factors can make or break security initiatives.
Given the objective of security resilience is to withstand threats and come back even stronger, it’s clear that resilience must exist before, during, and after a cybersecurity incident. This has repercussions on the executive level and throughout the business. Lack of executive support can lead to detection, response, and recovery capabilities that are chronically underfunded. This leaves CISOs at a disadvantage when security incidents do inevitably happen and panic strikes the C-suite. What’s more, CISOs who lack strong executive relationships may also find themselves struggling to oversee incident management and coordinate communications. And afterward? Remediating and improving the security posture, which often impacts multiple parts of the organization beyond IT and often requires significant investment, stalls without a necessary lift from leadership.
The security report, which scores resilience levels across a series of criteria, finds that organizations reporting a strong backing from leadership have resilience scores that are 39% higher when compared to organizations reporting weak support. “Bridges to the C-suite are built upon a solid understanding of how the business works and how security initiatives can make it work even better,” notes the report. “Support goes both ways in any relationship, after all.”

In addition to keeping the program aligned, CISOs must keep in communication with their peers and superiors. Those who share only transactional relationships within the C-Suite find their interactions limited to status updates and budget requests. Transformational relationships, however, involve more frequent and deeper communication and interactions, which cover a broader set of topics than submitting the latest budget ask. They are, in other words, more valuable.
Of course, executive support is just one crucial factor for success. Resilience programs need broad support from throughout the organization, not just at the top. Every time an employee picks up a mouse or accesses an app from their mobile phone, they make a choice to either strengthen or lessen the organization’s security posture. Every time an improvement is necessary following a security event, cultural buy-in determines whether this new request from security is implemented or circumvented.
According to the report, organizations that successfully foster a culture of security can see a 46% increase in resilience compared to those who lack such a culture. Much like aligning a program with the business direction furthers leadership buy-in, CISOs need to align security policy with the functional direction of the business—but in a way that helps employees see security measures as protecting not just corporate data and IT assets but also their own future. When employees aren’t on board or see security measures as IT concerns with no relation to them, resilience suffers. “Frequent security policy violations and workarounds,” notes the report, “are evidence of poor security culture.” By viewing policy exceptions as feedback, and investigating these from the perspective of identifying and correcting misalignment, security leaders can enroll employees as the willing participants in the solution—rather than contributors to the problem.
Security leaders know, by and large, what we need to do to secure our organizations. We have frameworks with pages of controls. We have risk registers with lists of action items. Where we often struggle is translating this knowledge into action. To do that, we must see our efforts within the strategic context of executive leaders and the tactical reality of the line managers in our organization. We must personalize and prioritize our efforts around what matters to the people we collaborate with. It is through engaging people that our security programs become human-centric and, in turn, become more resilient.
Where do we start? With relationships. Good relationships lead to good security programs, and good security programs lead to great relationships. And all of these contribute to security resilience.
Download the Security Outcomes Report, Vol. 3: Achieving Security Resilience today.
Explore more original research and blogs like this:
We’d love to hear what you think. Ask a Question, Comment Below, and Stay Connected with Cisco Secure on social!
Cisco Secure Social Channels
The use of unmanaged and IoT devices in enterprises is growing exponentially, and will account for 55.7 billion connected devices by the end of 2025. A critical concern is deploying IoT devices without requisite security controls.
While these numbers are numbing, their reality is undeniable. 90% of customers believe digitization has accelerated the importance placed upon security. The World Economic Forum now lists cybersecurity failure as a critical threat, and estimates a gap of more than 3 million security experts worldwide, hindering secure deployments at scale. Furthermore, 83% of IoT-based transactions happen over plaintext channels and not SSL, making them especially risky.
Securing an IoT device can be achieved either through securing the IoT device itself, or hardening the network it accesses. Securing devices can be cumbersome, requiring complex manufacturing partnerships and increasing unit prices, thereby reducing adoption. On the other hand, securing the network is always desirable as it helps secure access, encrypt traffic, and ease management.
Being a leader in both security and networking, Cisco continues to bring security closer to networking, providing the network with built-in security, and enabling the network to act both as sensor and as an enforcer. The convergence of security and networking leverages the network’s intelligence and visibility to enable more-informed decisions on policy and threats.
Cisco uniquely integrates security and networking, for instance we recently integrated Cisco Secure Firewall to operate on Cisco Catalyst 9000 Series switches. Additionally, Secure Firewall can be deployed in a containerized form, on-premises and in clouds. Cisco Secure Firewall classifies traffic and protects applications while stopping exploitation of vulnerable systems. Additionally, we offer Identity Services Engine with AI Endpoint Analytics to passively identify IoT devices and apply segmentation policies. Furthermore, Cisco offers management flexibility by integrating with Cisco Defense Orchestrator and DNA Center and with existing customer tools like SIEMs and XDRs.
Let’s look at three use cases where the addition of Secure Firewall capability on Catalyst 9000 Series switches solves real world problems:
Use case 1: Securing the Smart Building: This solution is ideal to secure smart buildings, converging various IoT systems into a single IT-managed network infrastructure. Smart buildings lower the operational and energy costs. Smarter building systems, however, pose serious security risks as these include so many unmanaged devices such as window shades, lighting, tailored HVAC, and more. One of the methods to secure smart buildings is to control access to avoid manipulation of sensors. Such control is attained with a networking switch with enhanced firewall capability. The firewall ensures granular segmentation, directing policies for traffic generated out of IoT devices, providing access to the right users. This integration also brings security closer to endpoints, making policy orchestration simpler.
Use Case 2: Centrally manage isolated IoT network clusters: IoT devices which communicate with each other in the same subnet typically cannot be routed, which is a challenge. By default, most IoT networks are configured in the same subnet, making it difficult to manage them centrally. Administrators are forced to physically connect to the IoT network to manage and collect telemetry. Furthermore, IoT vendors often charge hefty amounts to update IP addresses of devices. Cisco Secure Firewall, hosted on the Catalyst switch, solves this problem and not only inspects traffic from the IoT network but also translates duplicate IoT IP addresses to unique global IP addresses using NAT for centralized management of isolated IoT networks.
Use Case 3: Securely encrypt IoT traffic passing through a shared IT network: At airports, for example, multiple vendors manage unique systems such as baggage, air quality, biometric access control, etc, which share a common network. IoT traffic is usually in plain text, making it susceptible to packet sniffing, eavesdropping, man-in-the-middle attacks, and other such exploits. The IPSec capability on Cisco Secure Firewall encrypts IoT traffic, securing data transfer and reducing risk.
Cisco’s IoT initiatives join the once disconnected worlds of IT and IoT, unifying networking and security. For further details refer to the At-A Glance and see how and an Australian oil company, Ampol, fortified its retail IoT with Cisco Secure!
We’d love to hear what you think. Ask a Question, Comment Below, and Stay Connected with Cisco Secure on social!
Cisco Secure Social Channels




Opinion The tech sector is failing at cybersecurity. Global spending on the stuff is at $190 billion a year, a quarter of the US defense budget. That hasn't stemmed an estimated $7 trillion in annual cybercriminal damages. People are fond of saying that the Wild West days of the internet are over, but on those numbers an 1875 Dodge City bank vault looks like Fort Knox.…
When a Texas school district sold some old laptops at auction last year, it probably didn't expect to end up in a public legal fight with a local computer repair shop – but a debate over what to do with district data found on the liquidated machines has led to precisely that.…
France's Computer Emergency Response Team has issued a Bulletin D'Alerte regarding a campaign to infect VMware’s ESXI hypervisor with ransomware.…
Julius “Zeekill” Kivimäki, a 25-year-old Finnish man charged with extorting a local online psychotherapy practice and leaking therapy notes for more than 22,000 patients online, was arrested this week in France. A notorious hacker convicted of perpetrating tens of thousands of cybercrimes, Kivimäki had been in hiding since October 2022, when he failed to show up in court and Finland issued an international warrant for his arrest.
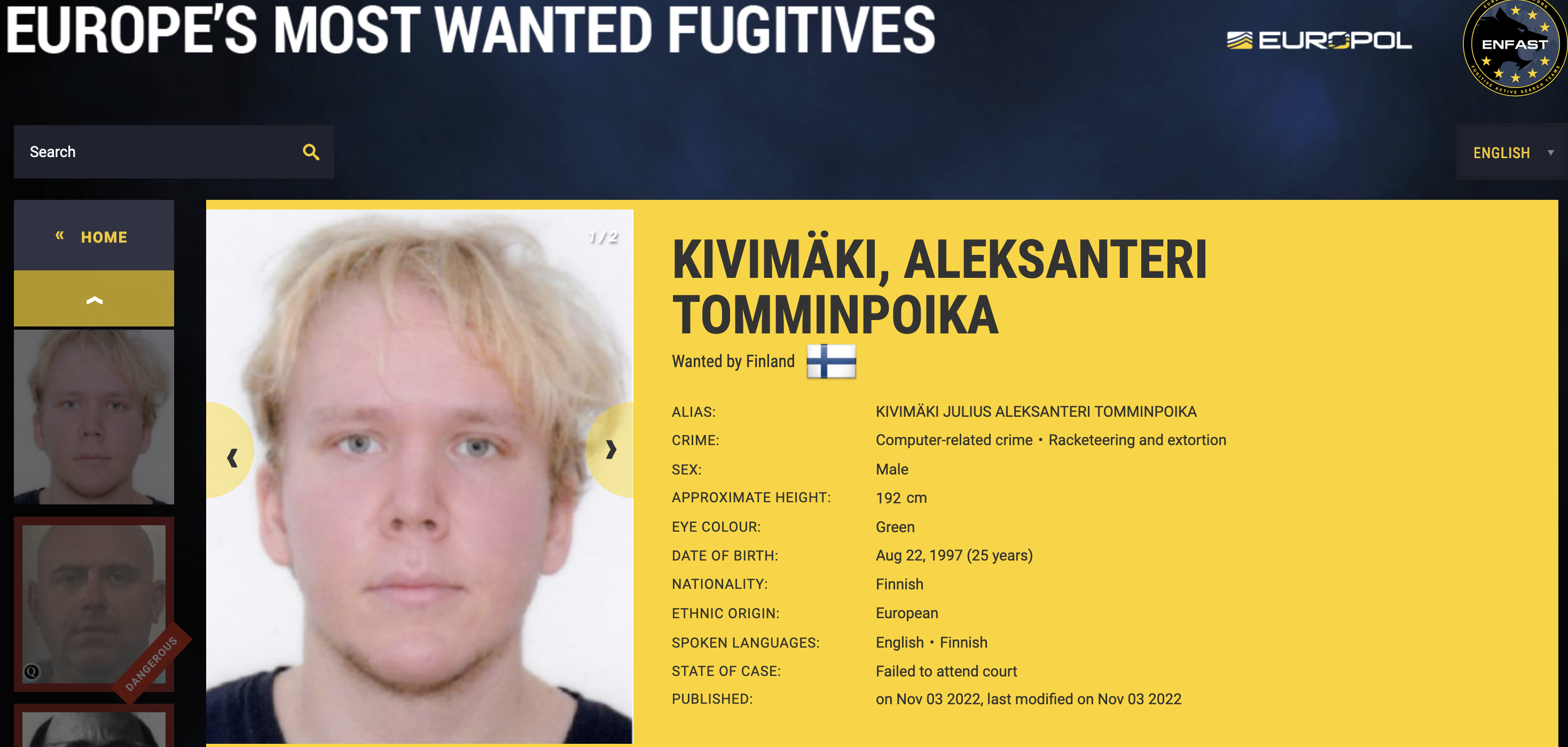
In late October 2022, Kivimäki was charged (and “arrested in absentia,” according to the Finns) with attempting to extort money from the Vastaamo Psychotherapy Center. In that breach, which occurred in October 2020, a hacker using the handle “Ransom Man” threatened to publish patient psychotherapy notes if Vastaamo did not pay a six-figure ransom demand.
Vastaamo refused, so Ransom Man shifted to extorting individual patients — sending them targeted emails threatening to publish their therapy notes unless paid a 500-euro ransom.
When Ransom Man found little success extorting patients directly, they uploaded to the dark web a large compressed file containing all of the stolen Vastaamo patient records.
But as documented by KrebsOnSecurity in November 2022, security experts soon discovered Ransom Man had mistakenly included an entire copy of their home folder, where investigators found many clues pointing to Kivimäki’s involvement. From that story:
“Among those who grabbed a copy of the database was Antti Kurittu, a team lead at Nixu Corporation and a former criminal investigator. In 2013, Kurittu worked on an investigation involving Kivimäki’s use of the Zbot botnet, among other activities Kivimäki engaged in as a member of the hacker group Hack the Planet (HTP).”
“It was a huge opsec [operational security] fail, because they had a lot of stuff in there — including the user’s private SSH folder, and a lot of known hosts that we could take a very good look at,” Kurittu told KrebsOnSecurity, declining to discuss specifics of the evidence investigators seized. “There were also other projects and databases.”
According to the French news site actu.fr, Kivimäki was arrested around 7 a.m. on Feb. 3, after authorities in Courbevoie responded to a domestic violence report. Kivimäki had been out earlier with a woman at a local nightclub, and later the two returned to her home but reportedly got into a heated argument.
Police responding to the scene were admitted by another woman — possibly a roommate — and found the man inside still sleeping off a long night. When they roused him and asked for identification, the 6′ 3″ blonde, green-eyed man presented an ID that stated he was of Romanian nationality.
The French police were doubtful. After consulting records on most-wanted criminals, they quickly identified the man as Kivimäki and took him into custody.
Kivimäki initially gained notoriety as a self-professed member of the Lizard Squad, a mainly low-skilled hacker group that specialized in DDoS attacks. But American and Finnish investigators say Kivimäki’s involvement in cybercrime dates back to at least 2008, when he was introduced to a founding member of what would soon become HTP.
Finnish police said Kivimäki also used the nicknames “Ryan”, “RyanC” and “Ryan Cleary” (Ryan Cleary was actually a member of a rival hacker group — LulzSec — who was sentenced to prison for hacking).
Kivimaki and other HTP members were involved in mass-compromising web servers using known vulnerabilities, and by 2012 Kivimäki’s alias Ryan Cleary was selling access to those servers in the form of a DDoS-for-hire service. Kivimäki was 15 years old at the time.
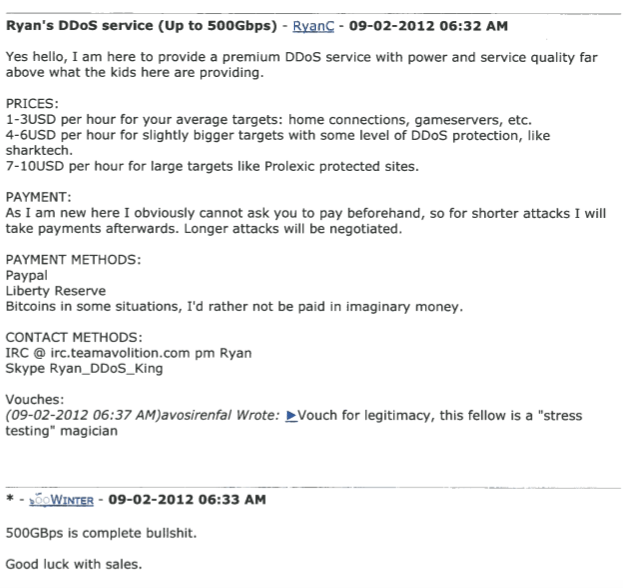
The DDoS-for-hire service allegedly operated by Kivimäki in 2012.
In 2013, investigators going through devices seized from Kivimäki found computer code that had been used to crack more than 60,000 web servers using a previously unknown vulnerability in Adobe’s ColdFusion software.
KrebsOnSecurity detailed the work of HTP in September 2013, after the group compromised servers inside data brokers LexisNexis, Kroll, and Dun & Bradstreet.
The group used the same ColdFusion flaws to break into the National White Collar Crime Center (NWC3), a non-profit that provides research and investigative support to the U.S. Federal Bureau of Investigation (FBI).
As KrebsOnSecurity reported at the time, this small ColdFusion botnet of data broker servers was being controlled by the same cybercriminals who’d assumed control over ssndob[.]ms, which operated one of the underground’s most reliable services for obtaining Social Security Number, dates of birth and credit file information on U.S. residents.
Multiple law enforcement sources told KrebsOnSecurity that Kivimäki was responsible for making an August 2014 bomb threat against former Sony Online Entertainment President John Smedley that grounded an American Airlines plane. That incident was widely reported to have started with a tweet from the Lizard Squad, but Smedley and others said it started with a call from Kivimäki.
Kivimäki also was involved in calling in multiple fake bomb threats and “swatting” incidents — reporting fake hostage situations at an address to prompt a heavily armed police response to that location.
Kivimäki’s apparent indifference to hiding his tracks drew the interest of Finnish and American cybercrime investigators, and soon Finnish prosecutors charged him with an array of cybercrime violations. At trial, prosecutors presented evidence showing he’d used stolen credit cards to buy luxury goods and shop vouchers, and participated in a money laundering scheme that he used to fund a trip to Mexico.
Kivimäki was ultimately convicted of orchestrating more than 50,000 cybercrimes. But largely because he was still a minor at the time (17) , he was given a 2-year suspended sentence and ordered to forfeit EUR 6,558.
As I wrote in 2015 following Kivimäki’s trial:
“The danger in such a decision is that it emboldens young malicious hackers by reinforcing the already popular notion that there are no consequences for cybercrimes committed by individuals under the age of 18.
Kivimäki is now crowing about the sentence; He’s changed the description on his Twitter profile to “Untouchable hacker god.” The Twitter account for the Lizard Squad tweeted the news of Kivimäki’s non-sentencing triumphantly: “All the people that said we would rot in prison don’t want to comprehend what we’ve been saying since the beginning, we have free passes.”
Something tells me Kivimäki won’t get off so easily this time, assuming he is successfully extradited back to Finland. A statement by the Finnish police says they are seeking Kivimäki’s extradition and that they expect the process to go smoothly.
Kivimäki could not be reached for comment. But he has been discussing his case on Reddit using his legal first name — Aleksanteri (he stopped using his middle name Julius when he moved abroad several years ago). In a post dated Jan. 31, 2022, Kivimäki responded to another Finnish-speaking Reddit user who said they were a fugitive from justice.
“Same thing,” Kivimäki replied. “Shall we start some kind of club? A support organization for wanted persons?”
The hack of SolarWinds' software more than two years ago pushed the threat of software supply chain attacks to the front of security conversations, but is anything being done?.…
Microsoft believes the gang who boasted it had stolen and leaked more than 200,000 Charlie Hebdo subscribers' personal information is none other than a Tehran-backed criminal group.…
A sneaky botnet dubbed HeadCrab that uses bespoke malware to mine for Monero has infected at least 1,200 Redis servers in the last 18 months.…




The reasons businesses and consumers like contactless payment transactions – high security and speed – are what make those systems bad for cybercriminals.…
The man accused of bringing down decentralized crypto exchange Mango Markets through market manipulation has made his first appearance in court in connection with the theft of millions in cryptocurrency.…





![]()

As our latest APT Activity Report makes abundantly clear, the threat of cyberespionage and stealthy attacks remains very real
The post Key takeaways from ESET’s new APT Activity Report – Week in security with Tony Anscombe appeared first on WeLiveSecurity
A former employee of RAC, one of Britain's major roadside recovery service operators, has pleaded guilty to data theft after he stored traffic accident information on his personal device that was passed onto claims companies.…
Updated A Chinese high-altitude spy balloon, spotted drifting over America, has caused concern about national security – though the US Department of Defense says it will not be shot down by F22s at this time.…


UK regulators are investigating a cyberattack against financial technology firm ION, while the LockBit ransomware gang has threatened to publish the stolen data on February 4 if the software provider doesn't pay up.…