





Organizations embrace the public cloud for the agility, scalability, and reliability it offers when running applications. But just as organizations need these capabilities to ensure their applications operate where needed and as needed, they also require their security does the same. Organizations may introduce multiple individual firewalls into their AWS infrastructure to produce this outcome. In theory, this may be a good decision, but in practice—this could lead to asymmetric routing issues. Complex SNAT configuration can mitigate asymmetric routing issues, but this isn’t practical for sustaining public cloud operations. Organizations are looking out for their long-term cloud strategies by ruling out SNAT and are calling for a more reliable and scalable solution for connecting their applications and security for always-on protection.
To solve these challenges, Cisco created stateful firewall clustering with Secure Firewall in AWS.
Firewall clustering for Secure Firewall Threat Defense Virtual provides a highly resilient and reliable architecture for securing your AWS cloud environment. This capability lets you group multiple Secure Firewall Threat Defense Virtual appliances together as a single logical device, known as a “cluster.”
A cluster provides all the conveniences of a single device (management and integration into a network) while taking advantage of the increased throughput and redundancy you would expect from deploying multiple devices individually. Cisco uses Cluster Control Link (CCL) for forwarding asymmetric traffic across devices in the cluster. Clusters can go up to 16 members, and we use VxLAN for CCL.
In this case, clustering has the following roles:

The above diagram explains traffic flow between the client and the server with the insertion of the firewall cluster in the network. Below defines the roles of clustering and how packet flow interacts at each step.
Owner: The Owner is the node in the cluster that initially receives the connection.
Backup Owner: The node that stores TCP/UDP state information received from the Owner so that the connection can be seamlessly transferred to a new owner in case of failure.
Director: The Director is the node in the cluster that handles owner lookup requests from the Forwarder(s).
Forwarder: The Forwarder is a node in the cluster that redirects packets to the Owner.
Fragment Owner: For fragmented packets, cluster nodes that receive a fragment determine a Fragment Owner using a hash of the fragment source IP address, destination IP address, and the packet ID. All fragments are then redirected to the Fragment Owner over Cluster Control Link.
Cisco brought support for AWS Gateway Load Balancer (Figure 2). This feature enables organizations to scale their firewall presence as needed to meet demand (see details here).

Building off the previous figure, organizations can take advantage of the AWS Gateway Load Balancer with Secure Firewall’s clustering capability to evenly distribute traffic at the Secure Firewall cluster. This enables organizations to maximize the benefits of clustering capabilities including increased throughput and redundancy. Figure 3 shows how positioning a Secure Firewall cluster behind the AWS Gateway Load Balancer creates a resilient architecture. Let’s take a closer look at what is going on in the diagram.

Figure 3 shows an Internet user looking to access a workload. Before the user can access the workload, the user’s traffic is routed to Firewall Node 2 for inspection. The traffic flow for this example includes:
User -> IGW -> GWLBe -> GWLB -> Secure Firewall (2) -> GLWB -> GWLBe -> Workload
In the event of failure, the AWS Gateway Load Balancer cuts off existing connections to the failed node, making the above solution non-stateful.
Recently, AWS announced a new feature for their load balancers known as Target Failover for Existing Flows. This feature enables forwarding of existing connections to another target in the event of failure.
Cisco is an early adaptor of this feature and has combined Target Failover for Existing Flows with Secure Firewall clustering capabilities to create the industry’s first stateful cluster in AWS.

Figure 4 shows a firewall failure event and how the AWS Gateway Load Balancer uses the Target Failover for Existing Flows feature to switch the traffic flow from Firewall Node 2 to Firewall Node 3. The traffic flow for this example includes:
User -> IGW -> GWLBe -> GWLB -> Secure Firewall (3) -> GLWB -> GWLBe -> Workload
Organizations need reliable and scalable security to protect always-on applications in their AWS cloud environment. With stateful firewall clustering capabilities from Cisco, organizations can protect their applications while maintaining cloud benefits such as agility, scalability, and reliability.
Cisco Secure Firewall Threat Defense Virtual is available in the AWS marketplace, providing features like firewalling, application visibility & control, IPS, URL filtering, and malware defense. Cisco offers flexible options for firewall licensing, such as pay-as-you-go (PAYG) and bring-your-own-license (BYOL). To learn more about how Cisco Secure Firewall clustering capabilities can help protect your AWS applications, see our additional resources, check out our 30-day free trial, or speak to your Cisco sales representative.
Cisco Secure Firewall Clustering in the Cloud
Introducing AWS Gateway Load Balancer Target Failover for Existing Flows
Secure Firewall for Public Cloud webpage
We’d love to hear what you think. Ask a Question, Comment Below, and Stay Connected with Cisco Secure on social!
Cisco Secure Social Channels
Lots of exciting things happening at Cisco, and for our customers, all to help them better prepare for what’s next. Case in point, we just returned from a very successful Cisco Partner Summit where the spotlight shined on cyber security. When our executives were on stage talking about solutions, the attendees heard a very catchy phrase; “if it’s connected, it’s protected.” A cool phrase, but there is more to that phrase and much more behind it.
To tie both connected and protected together, it’s good to note that Cisco is uniquely positioned as a security vendor with 80% of the worldwide internet traffic running through our network hardware and secured by our open platform, with hundreds of thousands of customers benefitting from automation, and from enriched and prioritized threat intel via our Extended Detection and Response (XDR) capabilities. That means a vast amount of unique insights for our customers to become more resilient, stay ahead of threats, be more confident, and benefit from less risk.
As examples of these questions above:
(1) what about proof points on the above?
(2) and do Cisco’s capabilities align with what customers want and need?
Let’s find out on the first by bringing the XDR aspect of security into the discussion, and the second by observing responses from a Forrester Total Economic Impact 
(TEI) study commissioned by Cisco, both points utilizing our Secure Endpoint solution.
First off, in simple terms, XDR provides the benefit of integrating threat intel from all control points of the security platform and combines that into actionable insights for better, faster, and where appropriate, prioritized remediation of the most critical threats, i.e. XDR helps security teams to identify the threats that can do the most damage and enables the workflows to neutralize those threats first.
And here is where the proof point comes in. One of the most critical components of XDR is endpoint security. And in the case of Cisco, it’s our Secure Endpoint solution. Cisco recently participated in the AV-Comparatives’ Endpoint Prevention and Response (EPR) Test. The AV-C test is described by that independent test organization as “… the most comprehensive test of EPR products ever performed.” Secure Endpoint was one of the 10 endpoint security products in the test that were subjected to 50 separate targeted attack scenarios, which used a variety of different techniques.
Here are the highlights of the AV-C EPR report where Cisco Secure Endpoint:
Stunning results and confidence building for our customers that Cisco is effective in endpoint security. Read the complete AV-C EPR Test Report here.
And then, what about the second proof point – is Cisco providing what customers want & need?
Cisco commissioned Forrester Consulting to perform an unbiased cost-benefit analysis of our Cisco Secure Endpoint product. The report yielded the highlights below, based upon a composite organization, and also includes 20+ outstanding customer quotes.
Here’s the Forrester TEI Study bottom line for the composite organization:
Very good results and again, confidence building for our customers that Cisco is effective in endpoint security. Read the Forrester “The Total Economic Impact Of Cisco Secure Endpoint” Study here.
Of Cisco Secure Endpoint” Study here.
One last thing, what about those customer quotes? Here are a couple of examples:
Director of IT security, logistics
Director of IT security, logistics
To find out more, read Forrester’s “The Total Economic Impact Of Cisco Secure Endpoint” Study here. And if you are not familiar with Secure Endpoint, or would like to sign up for a free trial, check it out here.
Of Cisco Secure Endpoint” Study here. And if you are not familiar with Secure Endpoint, or would like to sign up for a free trial, check it out here.
We’d love to hear what you think. Ask a Question, Comment Below, and Stay Connected with Cisco Secure on social!
Cisco Secure Social Channels

Authored by: Christy Crimmins and Oliver Devane
Football (or Soccer as we call it in the U.S.) is the most popular sport in the world, with over 3.5 billion fans across the globe. On November 20th, the men’s World Cup kicks off (pun intended) in Qatar. This event, a tournament played by 32 national teams every four years, determines the sport’s world champion. It will also be one of the most-watched sporting events of at least the last four years (since the previous World Cup).
An event with this level of popularity and interest also attracts fraudsters and cyber criminals looking to capitalize on fans’ excitement. Here’s how to spot these scams and stay penalty-free during this year’s tournament.
Phishing is a tool that cybercriminals have used for years now. Most of us are familiar with the telltale signs—misspelled words, poor grammar, and a sender email whose email address makes no sense or whose phone number is unknown. But excitement and anticipation can cloud our judgment. What football fan wouldn’t be tempted to win a free trip to see their home team participate in the ultimate tournament? Cybercriminals are betting that this excitement will cloud fans’ judgment, leading them to click on nefarious links that ultimately download malware or steal personal information.
It’s important to realize that these messages can come via a variety of channels, including email, text messages, (also known as smishing) and other messaging channels like WhatsApp and Telegram. No matter what the source is, it’s essential to remain vigilant and pause to think before clicking links or giving out personal or banking information.
For more information on phishing and how to spot a phisher, see McAfee’s “What is Phishing?” blog.
According to ActionFraud, the UK’s national reporting center for fraud and cybercrime, thousands of people were victims of ticket fraud in 2019—and that’s just in the UK. Ticket fraud is when someone advertises tickets for sale, usually through a website or message board, collects the payment and then disappears, without the buyer ever receiving the ticket.
The World Cup is a prime (and lucrative) target for this type of scam, with fans willing to pay thousands of dollars to see their teams compete. Chances are most people have their tickets firmly in hand (or digital wallet) by now, but if you’re planning to try a last-minute trip, beware of this scam and make sure that you’re using a legitimate, reputable ticket broker. To be perfectly safe, stick with well-known ticket brokers and those who offer consumer protection. Also beware of sites that don’t accept debit or credit cards and only accept payment in the form of bitcoin or wire transfers such as the one on the fake ticket site below:
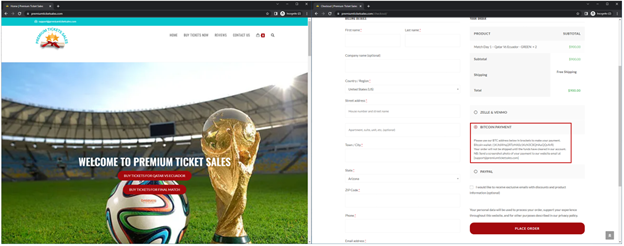
The red box on the right image shows that the ticket site accepts payment via Bitcoin.
Other red flags to look out for are websites that ask you to contact them to make payment and the only contact information is via WhatsApp.
Let’s be realistic—most of us are going to have to settle for watching the World Cup from the comfort of our own home, or the pub down the street. If you’re watching the tournament online, be sure that you’re using a legitimate streaming service. A quick Google of “FIFA World Cup 2022 Official Streaming” along with your country should get you the information you need to safely watch the event through official channels. The FIFA site itself is also a good source of information.
Illegal streaming sites usually contain deceptive ads and malware which can cause harm to your device.
In countries or regions where sports betting is legal, the 2022 World Cup is expected to drive an increase in activity. There’s no shortage of things to bet on, from a simple win/loss to the exact minute a goal will be scored by a particular player. Everything is subject to wager.
As with our previous examples, this increase in legitimate gambling brings with it an increase in deceptive activity. Online betting scams often start when users are directed to or search for gambling site and end up on a fraudulent one. After placing their bets and winning, users realize that while they may have “won” money, they are unable to withdraw it and are even sometimes asked to deposit even more money to make winnings available, and even then, they still won’t be. By the end of this process, the bettor has lost all their initial money (and then some, potentially) as well as any personal information they shared on the site.
Like other scams, users should be wary of sites that look hastily put together or are riddled with errors. Your best bet (yes, again, pun intended) is to look for an established online service that is approved by your government or region’s gaming commission. Finally, reading the fine print on incentives or bonuses is always a good idea. If something sounds too good to be true, it’s best to double-check.
For more on how you can bet online safely, and for details on how legalized online betting works in the U.S., check out our blog on the topic.
Using a free public Wi-Fi connection is risky. User data on these networks is unprotected, which makes it vulnerable to cyber criminals. Whether you’re traveling to Qatar for a match or watching the them with friends at your favorite pub, if you’re connecting to a public Wi-Fi connection, make sure you use a trusted VPN connection.
For more information on scams, visit our scam education page. Hopefully, with these tips, you’ll be able to enjoy and participate in some of the World Cup festivities, after all, fun is the goal!
The post Don’t Get Caught Offsides with These World Cup Scams appeared first on McAfee Blog.
Do you put yourself at greater risk for successful attacks by making one of these security mistakes?
The post 10 common security mistakes and how to avoid them appeared first on WeLiveSecurity



The word is out! Cisco Secure Endpoint’s effectiveness is off the charts in protecting your enterprise environment.
This is not just a baseless opinion; however, the facts are rooted in actual test results from the annual AV-Comparative EPR Test Report published in October 2022. Not only did Secure Endpoint knock it out of the park in enterprise protection; but Cisco Secure Endpoint obtained the lowest total cost of ownership (TCO) per agent at $587 over 5 years. No one else was remotely close in this area. More to come on that later.
If you are not familiar with the “AV-Comparatives Endpoint Prevention and Response Test is the most comprehensive test of EPR products ever performed. The 10 products in the test were subjected to 50 separate targeted attack scenarios, which used a variety of different techniques.”
These results are from an industry-respected third-party organization that assesses antivirus software and has just confirmed what we know and believe here at Cisco, which is our Secure Endpoint product is the industry’s best of the best.
Look for yourself at where we landed. That’s right, Cisco Secure Endpoint smashed this test, we are almost off the quadrant as one of the “Strategic Leaders”.

We ended up here for a combination of reasons, with the top being our efficacy in protecting our customers’ environments in this real-world test that emulates multi-stage attacks similar to MITRE’s ATT&CK evaluations which are conducted as part of this process (click here for an overview of MITRE ATT&CK techniques). Out of all the 50 scenarios tested, Secure Endpoint was the only product that STOPPED 100% of targeted threats toward enterprise users, which prevented further infiltration into the organization.
In addition, this test not only assesses the efficacy of endpoint security products but also analyzes their cost-effectiveness. Following up on my earlier remarks about achieving the lowest cost of ownership, the graph below displays how we stacked up against other industry players in this space including several well-known vendors that chose not to display their names due to poor results.

These results provide a meaningful proof point that Cisco Secure Endpoint is perfectly positioned to secure the enterprise as well as secure the future of hybrid workers.
Enriched with built-in Extended Detection and Response (XDR) capabilities, Cisco Secure Endpoint has allowed our customers to maintain resiliency when faced with outside threats.
As we embark on securing “what’s next” by staying ahead of unforeseen cyber threats of tomorrow, Cisco Secure Endpoint integration with the complete Cisco Secure Solutions portfolio allows you to move forward with the peace of mind that if it’s connected, we can and will protect it.
Now that you have seen how effective Secure Endpoint is with live real-world testing, try it for yourself with one of our live instant demos. Click here to access instructions on how to download and install your demo account for a test drive.
Click here to see what analysts, customers, and third-party testing organizations have to say about Cisco Secure Endpoint Security efficacy, easy implementation and overall low total cost of ownership for their organization —and stay ahead of threats.
We’d love to hear what you think. Ask a Question, Comment Below, and Stay Connected with Cisco Secure on social!
Cisco Secure Social Channels
Responding to a recent surge in AI-generated bot accounts, LinkedIn is rolling out new features that it hopes will help users make more informed decisions about with whom they choose to connect. Many LinkedIn profiles now display a creation date, and the company is expanding its domain validation offering, which allows users to publicly confirm that they can reply to emails at the domain of their stated current employer.
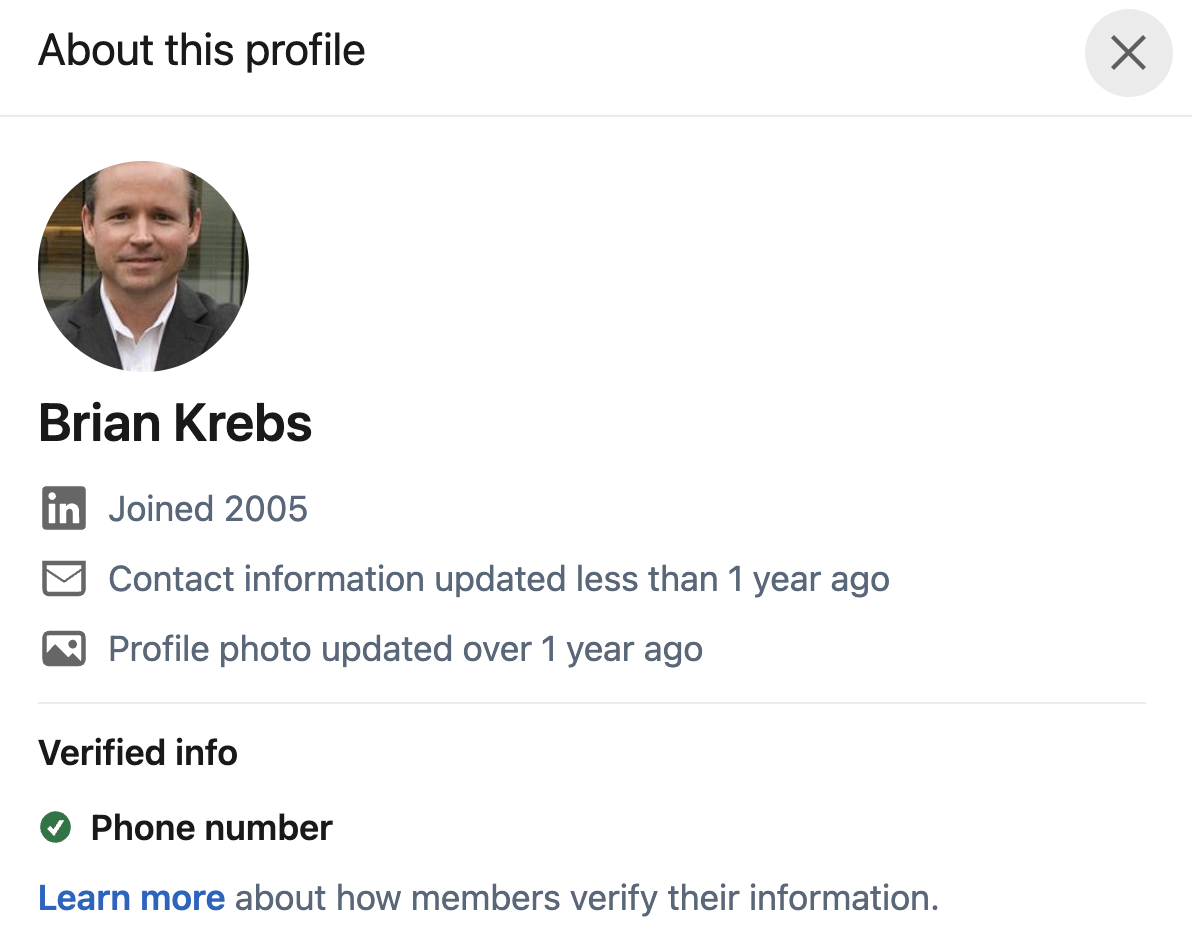
LinkedIn’s new “About This Profile” section — which is visible by clicking the “More” button at the top of a profile — includes the year the account was created, the last time the profile information was updated, and an indication of how and whether an account has been verified.
LinkedIn also said it is adding a warning to some LinkedIn messages that include high-risk content, or that try to entice the user into taking the conversation to another platform (like WeChat).
“We may warn you about messages that ask you to take the conversation to another platform because that can be a sign of a scam,” the company said in a blog post. “These warnings will also give you the choice to report the content without letting the sender know.”
In late September 2022, KrebsOnSecurity warned about the proliferation of fake LinkedIn profiles for Chief Information Security Officer (CISO) roles at some of the world’s largest corporations. A follow-up story on Oct. 5 showed how the phony profile problem has affected virtually all executive roles at corporations, and how these fake profiles are creating an identity crisis for the businesses networking site and the companies that rely on it to hire and screen prospective employees.
Reporting here last month also tracked a massive drop in profiles claiming to work at several major technology companies, as LinkedIn apparently took action against hundreds of thousands of inauthentic accounts that falsely claimed roles at these companies.
For example, on October 10, 2022, there were 576,562 LinkedIn accounts that listed their current employer as Apple Inc. The next day, half of those profiles no longer existed. At around the same time, the number of LinkedIn profiles claiming current roles at Amazon fell from roughly 1.25 million to 838,601 in just one day, a 33 percent drop.
For whatever reason, the majority of the phony LinkedIn profiles reviewed by this author were young women with profile photos that appear to have been generated by artificial intelligence (AI) tools.
“We’re seeing rapid advances in AI-based synthetic image generation technology and we’ve created a deep learning model to better catch profiles made with this technology,” LinkedIn’s Oscar Rodriguez wrote. “AI-based image generators can create an unlimited number of unique, high-quality profile photos that do not correspond to real people.”
It remains unclear who or what is behind the recent proliferation of fake executive profiles on LinkedIn, but likely they are from a combination of scams. Cybersecurity firm Mandiant (recently acquired by Google) told Bloomberg that hackers working for the North Korean government have been copying resumes and profiles from leading job listing platforms LinkedIn and Indeed, as part of an elaborate scheme to land jobs at cryptocurrency firms.
Identity thieves have been known to masquerade on LinkedIn as job recruiters, collecting personal and financial information from people who fall for employment scams.
Also, fake profiles also may be tied to so-called “pig butchering” scams, wherein people are lured by flirtatious strangers online into investing in cryptocurrency trading platforms that eventually seize any funds when victims try to cash out.
Welcome back! Previously in our Go Dox Yourself series, we walked through reviewing what information is available about you online, prioritizing those accounts that are most important or still active, and then restricting how much we share through those accounts and who gets to see it. That’s two out of our three steps — maybe good enough for Meatloaf, but not for us! You’re in the home stretch now, and this is the most straightforward-if-slow portion of the process — so let’s dive right in.
In the review step , along with the top accounts that you wrote out in your initial brain dump, we used some email search tricks and the free services NameCheckup.com and NameChk.com to dig up any unused, forgotten, or now obsolete accounts you might have previously registered under your email address or favorite username (or, as us ʼ80s kids used to say, your “handle.”)

We set those old accounts to the side to focus on your active and sensitive data first, but now it’s time to make Marie Kondo proud and clean out the junk drawers of our online life – if it doesn’t still serve you or spark joy, let’s kiss it goodbye!
In a perfect world, this would be as simple as logging in, going to your account settings and clicking a big ol’ “Cancel My Account” button. However, many sites opt to bury the cancelation settings behind a series of smokescreen menus, sometimes even including a half dozen unskippable “are you SURE you want to leave?” and “but we’ll give you a super good deal to stay!” surveys to click through first.
If you find yourself thwarted and your first search of “[Unwanted Service] cancel” doesn’t take you where you need to go, try checking out AccountKiller. This collaborative resource takes submissions of step-by-step deletion instructions and direct links to cancel for a tremendous number of sites, and even includes phone tree options and direct support numbers for canceling offline accounts as well.
The first pass of your delete list might well be longer than a CVS receipt, because these days the average person has 100 password-protected accounts to manage, but don’t worry! You don’t have to sprint to the finish line, and slow progress checking off a few accounts in short sessions over a few weeks will serve you better than a several-hour slog of trying to clear them all at once and burning out.
An important lesson in security is that operating at max capacity isn’t sustainable all the time, and planning for rest and overflow in our personal security planning is no different. Remember that the work you’re doing is cumulative, each small step is one more forward, and every account you clear now is one less that you’ll need to revisit later.
You might notice that we’ve checked off most of the information from our initial brainstorm: emails, usernames, phone numbers, profile pictures… but so far, we haven’t done much with your location history: the cities you lived in and live now, the cities where you worked or went to school, and the city of your birth. Now that we’re going to see how much information on you is available through data brokers and public record sites, these details will be important to have handy.
For the unfamiliar, data brokers are companies which collect and bundle personal information for everything from ad customization to individual investigation. Brokers collect their data through a wide variety of methods, including:
These metrics and details are bundled and sold, either directly through lookup sites like we’ll review in just a moment, or in demographic bundles (for example, “Resilient Renters” or “Living on Loans: Young Urban Single Parents”). If you’ve ever walked through a car dealership window-shopping and suddenly found sponsored content for that car company in your feed, data brokers are the most likely reason.
For this step you should reference the previously-mentioned Personal Data Removal Workbook provided by Michael Bazzell through his company, IntelTechniques. Bazzell has maintained and updated this workbook for many years now, and it is by far the most comprehensive resource for keeping a handle on who is buying and selling your data.
One of the first things you’ll notice on opening the workbook is the sheer volume of businesses out there buying and selling your data: at time of writing, the current edition includes 220 separate brokers. But much like your initial account inventory likely included a select set of important accounts and a longer list of less-relevant ones, there are less than a dozen brokers who dominate most of the market and should be at the top of your list – and fortunately, they’re also at the top of the workbook! These sites are:
Aside from covering most of the market for data and analytics intelligence, these primary sites often act as “feeders” for smaller providers that are either directly affiliated or collect information for their own databases from the largest providers. Which means that as you remove your data from these sites, you’ll not only check off another box on your list, but you may also reduce the number of hits you find for your information on smaller sites as you work your way down.
Congratulations: if you’ve been following along, you’ve just made it through your self-doxxing! Hopefully you’re feeling much better informed and aware of what tracks you’ve left online, and addressed who you do and do not want to have your… addresses. Join us soon for our wrap-up post where we’ll recap with takeaway lessons, as well as good habits and check-ins to keep you safe going forward.
Care about keeping people and their data safe online? Check out our open roles.
We’d love to hear what you think. Ask a Question, Comment Below, and Stay Connected with Cisco Secure on social!
Cisco Secure Social Channels
As we wrapped up October, we also put the final touches on a flurry of activities to celebrate Cyber Security Awareness Month. The tradition of October as National Cybersecurity Awareness Month goes back to 2004 when Congress and the White House tasked the Cybersecurity and Infrastructure Security Agency (CISA) and the National Cybersecurity Alliance (NCA) to join forces to help individuals protect themselves online as threats to technology and confidential data became more commonplace. There is no question that the scale and severity of threats have only increased exponentially in the nearly two decades we have been actively participating in cybersecurity awareness.
This year’s theme was “See Yourself in Cyber” to reinforce the fact that that while cybersecurity is technology-driven, ultimately, it’s really all about people that makes it real. So, this month is all about sharing information across the cybersecurity industry with individuals and companies around the world so we can all be more effective together. That gives me a great opportunity to discuss a related issue that profoundly impacts professionals who work in cybersecurity every single day: mental health.
Working in cybersecurity can be a stressful endeavor, which is why I’m so proud to be part of this global network of professionals who have dedicated our work lives to this important mission. We must be ever vigilant and on guard against threats and bad actors, both known and unknown. It is this ever-changing world of cybersecurity work that only compounds the stress level. The possibilities of work-related depression and burnout are real and becoming more common. According to this Forbes column, more than half of cybersecurity professionals in the US and Europe are on medication to help improve work-related mental health.
I wrote extensively about ways we can help our colleagues and employees work through mental health issues in this blog last May commemorating the official Mental Health Awareness Month. The key takeaways I closed with are worth repeating.
From a technology point of view, we at Cisco Secure are committed to the goal of helping organizations become more security resilient. We know that unpredictability is the nature of working in cybersecurity. But by being more resilient I firmly believe that we can help organizations to be able to withstand the ever-changing threat landscape and ultimately emerge stronger.
Naturally, our goal is to extend the benefits of resilience downstream to the cybersecurity pros who are on the frontlines of battling threats and bad actors. To that end, there are a couple of resources I’d like to point to. One, the American Psychological Association offers a few very helpful ways people can develop more resilience with regards to mental health. Two, Cisco offers great resources to help you either enter the cybersecurity field or enhance your career through advanced training education. Additionally, Cisco has made a commitment to the White House as part of the Cyber Workforce and Education Summit to train more than 200,000 students to join the cybersecurity field over the next three years.
November 16 happens to be the UN International Day for Tolerance. Like the word resilience, tolerance can take on several different meanings. But I want to take the opportunity to apply it to another critical issue impacting the cybersecurity industry: the need for a more diverse and inclusive workforce. I covered some of these themes in one of the earliest blogs I posted after joining Cisco. I look forward to providing additional perspectives with some of the latest trends and stats we are seeing within Cisco Secure.



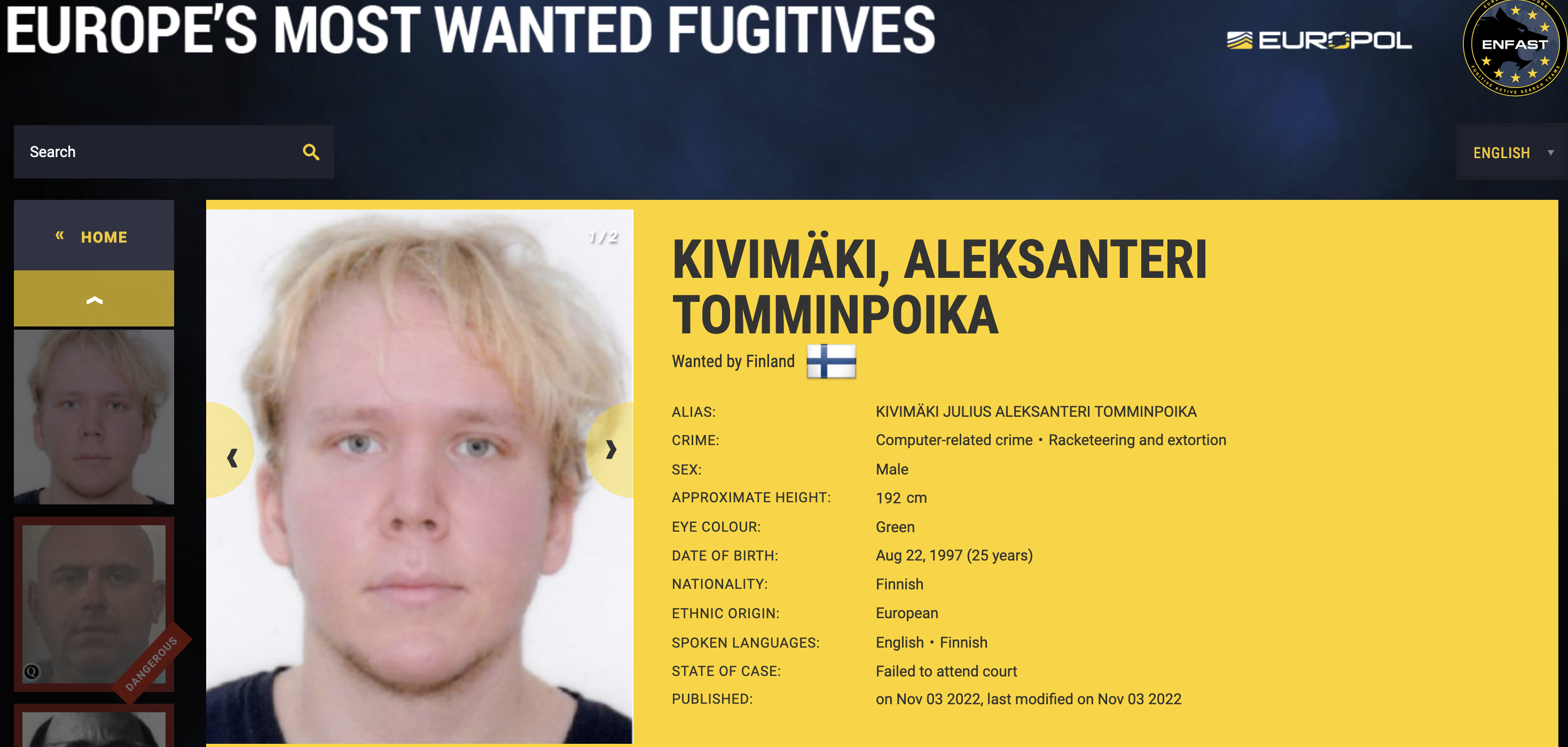
A 25-year-old Finnish man has been charged with extorting a once popular and now-bankrupt online psychotherapy company and its patients. Finnish authorities rarely name suspects in an investigation, but they were willing to make an exception for Julius “Zeekill” Kivimaki, a notorious hacker who — at the tender age of 17 — had been convicted of more than 50,000 cybercrimes, including data breaches, payment fraud, operating botnets, and calling in bomb threats.
In late October 2022, Kivimaki was charged (and arrested in absentia, according to the Finns) with attempting to extort money from the Vastaamo Psychotherapy Center. On October 21, 2020, Vastaamo became the target of blackmail when a tormentor identified as “ransom_man” demanded payment of 40 bitcoins (~450,000 euros at the time) in return for a promise not to publish highly sensitive therapy session notes Vastaamo had exposed online.
In a series of posts over the ensuing days on a Finnish-language dark net discussion board, ransom_man said Vastaamo appeared unwilling to negotiate a payment, and that he would start publishing 100 patient profiles every 24 hours “to provide further incentive for the company to continue communicating with us.”
“We’re not asking for much, approximately 450,000 euros which is less than 10 euros per patient and only a small fraction of the around 20 million yearly revenues of this company,” ransom_man wrote.
When Vastaamo declined to pay, ransom_man shifted to extorting individual patients. According to Finnish police, some 22,000 victims reported extortion attempts targeting them personally, targeted emails that threatened to publish their therapy notes online unless paid a 500 euro ransom.
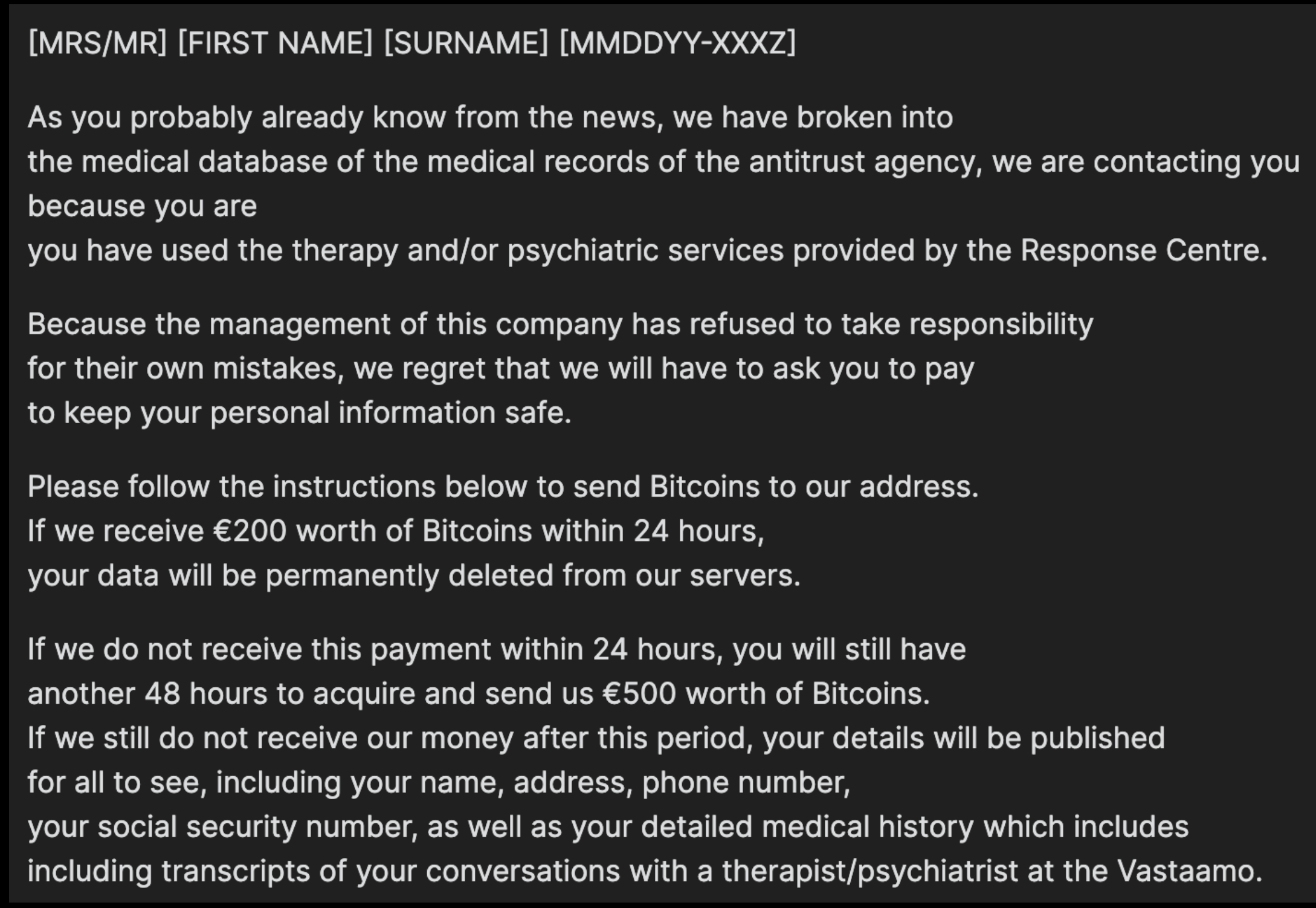
The extortion message targeted Vastaamo patients.
On Oct. 23, 2020, ransom_man uploaded to the dark web a large compressed file that included all of the stolen Vastaamo patient records. But investigators found the file also contained an entire copy of ransom_man’s home folder, a likely mistake that exposed a number of clues that they say point to Kivimaki.
Ransom_man quickly deleted the large file (accompanied by a “whoops” notation), but not before it had been downloaded a number of times. The entire archive has since been made into a searchable website on the Dark Web.
Among those who grabbed a copy of the database was Antti Kurittu, a team lead at Nixu Corporation and a former criminal investigator. In 2013, Kurittu worked on investigation involving Kivimaki’s use of the Zbot botnet, among other activities Kivimaki engaged in as a member of the hacker group Hack the Planet.
“It was a huge opsec [operational security] fail, because they had a lot of stuff in there — including the user’s private SSH folder, and a lot of known hosts that we could take a very good look at,” Kurittu told KrebsOnSecurity, declining to discuss specifics of the evidence investigators seized. “There were also other projects and databases.”
Kurittu said he and others he and others who were familiar with illegal activities attributed to Kivimäki couldn’t shake suspicion that the infamous cybercriminal was also behind the Vastaamo extortion.
“I couldn’t find anything that would link that data directly to one individual, but there were enough indicators in there that put the name in my head and I couldn’t shake it,” Kurittu said. “When they named him as the prime suspect I was not surprised.”
A handful of individually extorted victims paid a ransom, but when news broke that the entire Vastaamo database had been leaked online, the extortion threats no longer held their sting. However, someone would soon set up a site on the dark web where anyone could search this sensitive data.
Kivimaki stopped using his middle name Julius in favor of his given first name Aleksanteri when he moved abroad several years ago. A Twitter account by that name was verified by Kivimaki’s attorney as his, and through that account he denied being involved in the Vastaamo extortion.
“I believe [the Finnish authorities] brought this to the public in order to influence the decision-making of my old case from my teenage years, which was just processed in the Court of Appeal, both cases are investigated by the same persons,” Kivimaki tweeted on Oct. 28.
Kivimaki is appealing a 2020 district court decision sentencing him to “one year of conditional imprisonment for two counts of fraud committed as a young person, and one of gross fraud, interference with telecommunications as a young person, aggravated data breach as a young person and incitement to fraud as a young person,” according to the Finnish tabloid Ilta-Sanomat.
“Now in the Court of Appeal, the prosecutor is demanding a harsher punishment for the man, i.e. unconditional imprisonment,” reads the Ilta-Sanomat story. “The prosecutor notes in his complaint that the young man has been committing cybercrimes from Espoo since he was 15 years old, and the actions have had to be painstakingly investigated through international legal aid.”
As described in this Wired story last year, Vastaamo filled an urgent demand for psychological counseling, and it won accolades from Finnish health authorities and others for its services.
“Vastaamo was a private company, but it seemed to operate in the same spirit of tech-enabled ease and accessibility: You booked a therapist with a few clicks, wait times were tolerable, and Finland’s Social Insurance Institution reimbursed a big chunk of the session fee (provided you had a diagnosed mental disorder),” William Ralston wrote for Wired. “The company was run by Ville Tapio, a 39-year-old coder and entrepreneur with sharp eyebrows, slicked-back brown hair, and a heavy jawline. He’d cofounded the company with his parents. They pitched Vastaamo as a humble family-run enterprise committed to improving the mental health of all Finns.”
But for all the good it brought, the healthcare records management system that Vastaamo used relied on little more than a MySQL database that was left dangerously exposed to the web for 16 months, guarded by nothing more than an administrator account with a blank password.
The Finnish daily Iltalehti said Tapio was relieved of his duties as CEO of Vastaamo in October 2020, and that in September, prosecutors brought charges against Tapio for a data protection offense in connection with Vastaamo’s information leak.
“According to Vastaamo, the data breach in Vastaamo’s customer databases took place in November 2018,” Iltalehti reported last month. “According to Vastaamo, Tapio concealed information about the data breach for more than a year and a half.”
NetWitness and Cisco released the third annual Findings Report from the RSA Conference® 2022 Security Operations Center (SOC).
The RSA Conference® SOC analyzes the Moscone Center wireless traffic, which is an open network during the week of the Conference.
The role of the SOC at RSA Conference is an educational exhibit sponsored by NetWitness and Cisco. It has elements of a SOC like you would create to protect an organization. The RSAC SOC coordinated with the Moscone Center Network Operation Center for a SPAN of the network traffic from the Moscone Center wireless network. In the SOC, NetWitness had real time visibility of the traffic traversing the wireless network. Cisco provided automated malware analysis, threat intelligence, DNS visibility and Intrusion Detection; brought together with SecureX.

The goal of the RSAC SOC is to use technology to educate conference attendees about what happens on a typical wireless network. The education comes in the form of daily SOC tours and an RSA Conference® session. You can watch the replay of the ‘EXPOSURE: The 3rd Annual RSAC SOC Report’ session here.
The findings report addresses several security topics, including:

Look forward to seeing you in 2023!
Download the RSA Conference® 2022 Security Operations Center Findings Report here.
Acknowledgements: Our appreciation to those who made the RSAC SOC possible.
Percy Tucker
Steve Fink
Bart Stump
Dave Glover
Jessica Bair Oppenheimer – Cisco SOC Manager
Ian Redden – Team Lead & Integrations
Aditya Sankar / Ben Greenbaum – SecureX & Malware Analytics
Alejo Calaoagan / Christian Clasen – Cisco Umbrella
Dinkar Sharma / Seyed Khadem-Djahaghi – Cisco Secure Firewall
Matt Vander Horst – SecureX Orchestration
Doug Hurd – Partnerships
Eric Kostlan
Navin Sinha
Zohreh Khezri
Eric Goodwin
Gabe Gilligan and the amazing staff at XPO Digital!
We’d love to hear what you think. Ask a Question, Comment Below, and Stay Connected with Cisco Secure on social!
Cisco Secure Social Channels
To mark Antimalware Day, we’ve rounded up some of the most pressing issues for cybersecurity now and in the future
The post The future starts now: 10 major challenges facing cybersecurity appeared first on WeLiveSecurity

What you paid for your home, who lives there with you, your age, your children, your driving record, education, occupation, estimated income, purchasing habits, and any political affiliations you may have—all pretty personal information, right? Well, there’s a good chance that anyone can find it online. All it takes is your name and address.
Thankfully, there’s something you can do about it.
But first, go ahead and give it a try. Type your name and address in a search bar and see what comes up. If you’re like most people, your search results turned up dozens of sites with your information on them. Some sites offer bits of it for free. Other sites offer far more detailed information, for a price.
Who’s behind all this? Data brokers. All part of a global data economy estimated at $200 billion U.S. dollars a year fueled by thousands of data points on billions of people scraped from public records, social media, third-party sources, and sometimes other data broker sites as well.
The result? A chillingly accurate picture of you.
So accurate, that reporters and law enforcement will often use profiles from data broker sites to dig up a person’s background. And so could scammers and thieves.
Ever wonder how you end up with all those spam calls and texts? Look no further than the data brokers. They help scammers compile the calling and texting lists they use. Yet spammy calls and texts are just part of the problem with these sites. They can give thieves the tools they need to steal your identity.
How? Visualize your identity as a jigsaw puzzle. Every bit of personal information makes up a piece, and if you cobble enough pieces together, a scammer or thief could have enough information to steal your identity. And data brokers compile all those pieces in one place and offer up them up in droves.
If you’re wondering if this activity is legal or at least regulated in some way, it largely isn’t. For example, the U.S. has no federal laws that require data brokers to remove personal information from their sites if requested to do so. On the state level, Nevada, Vermont, and California have legislation in place aimed at protecting consumers from having their data disclosed on these sites. Other legislation is being considered, yet as of this writing there’s very little on the books right now.
With next to no oversight, data brokers continue to collect personal information, which may or may not be accurate. It may be out of date or flat out wrong. Likewise, as it is with any large data store, data brokers are subject to hacks and attacks, which may lead to breaches that release detailed personal information onto the dark web and into the hands of bad actors.
Put plainly, data brokers collect, buy, and sell high volumes of personal information, often in ways that leave no trace that it’s happening to you—or that the information is correct in any way.
All this can feel like it’s out of your control. And maybe the search you did on yourself made you a little uneasy. (Understandable!) Yet you have plenty of ways you can curb this activity and even remove your information from some of the riskiest data broker sites as well.
It starts by finding out which sites have information on you, followed by filing requests to have it removed. Yet with dozens and dozens of these sites proliferating online, this can be a time-consuming process. Not to mention a frustrating one. We created McAfee+ so people can not only be safe but feel safe online, particularly in a time when there’s so much concern about identity theft and invasion of our online privacy. McAfee+ contains a comprehensive set of tools, such as Personal Data Cleanup which are designed to help protect your online privacy.
Personal Data Cleanup scans some of the riskiest data broker sites and shows you which ones are selling your personal info. It also provides guidance on how you can remove your data from those sites and can even manage the removal for you depending on your plan.
And because getting your info removed once isn’t a guarantee that a data broker won’t collect and post it again, Personal Data Cleanup can continually monitor those sites. So should your info get posted again, you can request its removal again as well.
The other way you can thwart data brokers involves cleaning up your tracks when you go online, essentially leaving a smaller amount of data in your wake that they can collect and resell.
Searching for your name and address can turn up some surprises and introduce you to the world of data brokers, the dozens and dozens of companies that collect, buy, and sell your personal information. While data brokers sell this information to companies for advertising and marketing purposes, they will also sell that information to hackers, scammers, and thieves. Simply put, they don’t discriminate when selling your personal info. That puts more than just your privacy at risk, it can put your identity at risk as well. By selling your personal information, it can give bad actors the info they need to commit identity fraud and theft.
While cleaning up personal information from these sites is often a difficult and time-consuming task, tools like our Personal Data Cleanup can now dig out the sites where your personal info is posted and can help you remove it. Moreover, you now have several tricks and tactics you can use to reduce the amount of personal data these sites can collect. In all, you now have far more control over what data brokers can collect, buy, and sell than you had before. And now is most certainly a time to take that control given all the time we spend online and the many ways we rely on it to help us work, play, and simply get things done.
The post How much of your personal info is available online? A simple search could show you plenty. appeared first on McAfee Blog.


ossl-code-1200



Cisconians delight in contributing to their communities in a variety of ways including at the local theatre, farm and library. Cisco’s paid Time2Give benefit encourages team members to volunteer at the places where their passions thrive.
How should you decide where to get involved? Customer Success Program Manager Kate Pydyn advises: “Find something that speaks to your passion while giving back. There are so many opportunities that involve being outdoors, crafting, teaching skills you’ve developed, telling stories or providing comfort.”
With ten paid days a year to give, these Cisconians demonstrate that building relationships with people, the arts and the earth can increase fulfillment, connection and community.
Urban farming is an issue very close to the heart of Petra Hammerl, a senior enterprise customer success manager who works on Duo Security. Hammerl frequently volunteers at Farm City Detroit, part of Detroit Blight Busters. Using Time2Give, Hammerl has shared the experience by “bringing a crew of awesome co-workers which has been amazing and a lot of fun,” she said.

“It felt great to take action! There are so many problems in the world, and I often feel powerless to make a difference. What I did was small, but with all of the volunteers together, the work that was done makes a real difference in the lives of my neighbors.” – Kate Pydyn
Pydyn and Emily Gennrich, a manager of operations for security customer success at Cisco Secure, joined in on the fun by contributing to multiple facets of gardening from weeding to harvesting food. “It felt great to take action! There are so many problems in the world, and I often feel powerless to make a difference. What I did was small, but with all of the volunteers together, the work that was done makes a real difference in the lives of my neighbors,” Pydyn said.
Senior Communications Manager, Brand Strategy & Design at Cisco Secure Chrysta Cherrie spent her Time2Give as a sighted assistant at the VISIONS vendor fair, hosted at the Ann Arbor District Library Downtown. “I was really happy to take some time to volunteer at the VISIONS vendor fair for people who are blind, visually impaired or physically disabled,” Cherrie said.

Learning how to be a sighted assistant was “a reminder that we can do more when we can rely on each other. Taking the time to better understand how someone makes their way through life gives you a chance to build empathy,” Cherrie said. She escorted attendees around the event where exhibitors offered products and services like electronic readers, leader dogs and transportation. There were also talks throughout the day and Cherrie helped attendees navigate between the presentation and vendor areas.
Meeting attendees of the VISIONS vendor fair and experiencing how meaningful the event is also moved Cherrie. The fair “brings out folks throughout southeast Michigan, so there’s a good chance that the person you’re assisting will run into some friends, and getting to see people connect like that can’t help but make you feel good,” Cherrie said.
Jenny Callans, a senior design researcher who works on Duo Security, serves as the chair of the Friends of the Detroit Film Theatre’s Auxiliary, a part of the Detroit Institute of Arts. “We support the mission of the Friends of the Detroit Film Theatre to make great niche films accessible to audiences,” she said. To do that, the organization is responsible for building a community of film fans and overseeing how donations are spent.

For Callans, the most meaningful part of using Time2Give to support the FDFT and the DIA is sharing her love of film with others. Time2Give supports her duties as FDFT chair, and gives her a sense of connection when she’s visiting the DFT to take in a movie. “Sitting in a theatre next to my young adult son, but surrounded by strangers watching a film that is unusual or unexpected but which moves me and challenges me to think is the best part hands-down,” Callans said.
From supporting youth to volunteering at community hubs, Time2Give “is a fantastic opportunity to have a long-lasting, meaningful relationship with your community by volunteering as a board or committee member! Having a long-term presence with an org is amazingly impactful, for you and for the organization,” Callans said.
Time2Give is one of Cherrie’s favorite things about working at Cisco. She says, “Take advantage of the opportunity! Time2Give is a great way to give back to your community and the people and causes that you care about.”
Stay tuned for more posts celebrating the community engagement Time2Give fosters and check out our open roles to join in on giving back.
We’d love to hear what you think. Ask a Question, Comment Below, and Stay Connected with Cisco Secure on social!
Cisco Secure Social Channels
Going beyond the hype, passwordless authentication is now a reality. Cisco Duo’s passwordless authentication is now generally available across all Duo Editions.
“Cisco Duo simplifies the passwordless journey for organizations that want to implement phishing-resistant authentication and adopt a zero trust security strategy.”
—Jack Poller, Senior Analyst, ESG
We received tremendous participation and feedback during our public preview, and we are now excited to bring this capability to our customers and prospects.
“Over the last few years, we have increased our password complexities and required 2FA wherever possible. With this approach, employees had more password lock outs, password fatigue, and forgetting their longer passwords due to password rotations. With Duo Passwordless, we are excited to introduce this feature to our employees to keep our password complexities in place and leverage different Biometric options whether that is using their mobile device, Windows Hello, or a provided FIDO security key.
The Duo Push for passwordless authentication feature is simple and easy and introduces a more pleasant experience overall. Using Duo’s device insight and application policies, we are able to leverage and verify the security of the mobile devices before the device is allowed to be used. To top it off, Duo is connected to our SIEM and our InfoSec team is able to review detailed logs and setup alerts to be able to keep everything secure.”
—Vice President of IT, Banking and Financial Services Customer
As with any new technology, getting to a completely passwordless state will be a journey for many organizations. We see customers typically starting their passwordless journey with web-based applications that support modern authentication. To that effect, Duo’s passwordless authentication is enabled through Duo Single Sign-On (SSO) for federated applications. Customers can choose to integrate their existing SAML Identity provider such as Microsoft (ADFS, Azure), Okta or Ping Identity; or choose to use Duo SSO (Available across all Duo editions).
“Password management is a challenging proposition for many enterprises, especially in light of BYOD and ever increasing sophistication of phishing schemes. Cisco aims to simplify the process with its Duo passwordless authentication that offers out-of-box integrations with popular single sign-on solutions.”
—Will Townsend, Vice President & Principal Analyst, Networking & Security, Moor Insights & Strategy
Duo offers a flexible choice of passwordless authentication options to meet the needs of businesses and their use cases. This includes:
No matter which authentication option you choose, it is secure and inherently multi-factor authentication. We are eliminating the need for the weak knowledge factor (something you know – passwords) which are shared during authentication and can be easily compromised. Instead, we are relying on stronger factors, which are the inherence factor (something you are – biometrics) and possession factor (something you have – a registered device). A user completes this authentication in a single gesture without having to remember a complex string of characters. This significantly improves the user experience and mitigates the risk of stolen credentials and man-in-the-middle (MiTM) attacks.
FIDO2 authentication is regarded as phishing-resistant authentication because it:
Using Duo with FIDO2 authenticators enables organizations to enforce phishing-resistant MFA in their environment. It also complies with the Office of Management and Budget (OMB) guidance issued earlier this year in a memo titled “Moving the U.S. Government Towards Zero Trust Cybersecurity Principles”. The memo specifically requires agencies to use phishing-resistant authentication method.
We understand that getting the IT infrastructure ready to support FIDO2 can be expensive and is typically a long-term project for organizations. In addition, deploying and managing 3rd party security keys creates IT overhead that some organizations are not able to undertake immediately.
Alternatively, using Duo Push for passwordless authentication is an easy, cost effective to get started on a passwordless journey for many organizations, without compromising on security.
We have incorporated security into the login workflow to bind the browser session and the device being used. So, organizations get the same benefits of eliminating use of stolen credentials and mitigation of phishing attacks. To learn more about passwordless authentication with Duo Push, check out our post: Available Now! Passwordless Authentication Is Just a Tap Away.
In addition to going passwordless, many organizations are looking to implement zero trust access in their IT environment. This environment typically is a mix of modern and legacy applications, meaning passwordless cannot be universally adopted. At least not until all applications can support modern authentication.
Additionally, organizations need to support a broad range of use cases to allow access from both managed and unmanaged (personal or 3rd party contractor) devices. And IT security teams need visibility into these devices and the ability to enforce compliance to meet the organization’s security policies such as ensuring that the operating system (OS) and web browser versions are up to date. The importance of verifying device posture at the time of authentication is emphasized in the guidance provided by OMB’s zero trust memorandum – “authorization systems should work to incorporate at least one device-level signal alongside identity information about the authenticated user.”
Duo can help organizations adopt a zero trust security model by enforcing strong user authentication across the board either through passwordless authentication where applicable or thought password + MFA where necessary, while providing a consistent user experience. Further, with capabilities such as device trust and granular adaptive policies, and with our vision for Continuous Trusted Access, organizations get a trusted security partner they can rely on for implementing zero trust access in their environment.
To learn more, check out the eBook – Passwordless: The Future of Authentication, which outlines a 5-step path to get started. And watch the passwordless product demo in this on-demand webinar .
Many of our customers have already begun their passwordless journey. If you are looking to get started as well, sign-up for a free trial and reach out to our amazing representatives.
We’d love to hear what you think. Ask a Question, Comment Below, and Stay Connected with Cisco Secure on social!
Cisco Secure Social Channels






It’s Partner Summit week and, for me, it’s an important reminder that no one company, not even Cisco, can do it alone. Our partners provide diverse perspectives, expertise, and solutions offerings. Each partner plays a key part in delivering the outcomes and experiences our customers need, want, and expect. So, when we say, “Let’s Own It”, it’s a rally cry for Cisco and our partners alike to do our parts to seize the massive opportunity that we have in front of us and turn it into mutual success.
Together, I know we can achieve amazing things. Foremost on my mind right now is both the opportunity and necessity to empower customers with security resilience. Resilience means customers can protect the integrity of every aspect of their business so that they can withstand unpredictable threats or changes and emerge stronger. It’s about providing controlled, trusted access to applications and services, at any time, from any place.
Resilience can also help customers deal with issues the moment they arise. If changes are needed, they will have the visibility to determine priorities, thanks to actionable intelligence and insight in the face of some major security realities that they are dealing with every day.
One, businesses are more interconnected, meaning that a breach on anyone in the value chain has dramatic ripple effects on the others.
Two, security attacks are becoming more personalized. Individuals remain one of the easiest targets for cybercriminals and their attacks are becoming more sophisticated and customized for the individual.
Three, hybrid work is here to stay. People around the world will continue to work from anywhere, on managed and unmanaged devices, over secured and unsecured networks, to applications spread across multiple clouds and data centers.
Our vision for enabling a more resilient organization is the Cisco Security Cloud. It’s an open, integrated security platform that will protect the integrity of entire IT ecosystems by safeguarding users, devices and applications across public clouds and private data centers, without public cloud lock-in. Delivering on the Security Cloud is part of our long-term product strategy; but the innovations we are announcing at Partner Summit this week are foundational elements that execute on this vision.
Specifically, we are announcing new solutions and technologies across our portfolio in Secure Connectivity, Network Security, and Zero Trust. I encourage all partners to drill down on each announcement in the accompanying blogs and news announcements. But here are the highlights of the announcements.
Helping increase resistance to phishing attacks and improve user experience through frictionless access using Duo Passwordless, which is now generally available with support for Duo Mobile as a passwordless authenticator.
Expanding the Cisco Secure Firewall 3100 series, the first firewall purpose-built for hybrid work, with the Secure Firewall 3105, ideal for branch office and similar use cases focused on performance at a competitive price point.
Strengthening Umbrella’s data loss prevention (DLP) capabilities by adding API-based enforcement and unified reporting to protect sensitive data, e.g., intellectual property and financial and healthcare information. This complements Umbrella’s current inline-DLP functionality and collectively forms multi-mode DLP.
New Secure Workload capabilities delivering policy-as-code workload security for cloud-native and public-cloud application development. Common use cases for policy-as-code include access control to infrastructure and simplifying enterprise compliance and controls.
Our strategy and our innovation roadmap are all designed to set you up, our partners, for long-term success. In addition, we are committed to several partner enablement programs to help you deliver more value to customers and to help you become more profitable. Examples include:
Partner Summit is for you. So, my call-to-action is for you to maximize the value you get out of this week by attending as many of the informative, high-impact security sessions many teams worked hard to create. I am really looking forward to meeting as many of you as possible – on the expo floor, at the sessions, or in our 1-on-1 meetings.
Security has never been more critical and the need for resiliency is a requirement for virtually every business. The time for us to own it and innovate to win this future together has never been better.
We’d love to hear what you think. Ask a Question, Comment Below, and Stay Connected with Cisco Secure on social!
Cisco Secure Social Channels

On Black Friday and Cyber Monday, the deals roll out. So do some of the worst Black Friday and Cyber Monday scams.
Hackers, scammers, and thieves look to cash in this time of year by blending in with the holiday rush, spinning up their own fake shipping notices, phony deals, and even bogus charities that look legitimate at first glance, yet are anything but. Instead, they may be loaded with malware, point you to phishing sites that steal your personal info, or they may simply rip you off.
Classically, many online scams play on emotions by creating a sense of urgency or even fear. And for the holidays, you can throw stress into that mix as well—the stress of time, money, or even the pressure of finding that hard-to-get gift that seems to be out of stock everywhere. The bad actors out there will tailor their attacks around these feelings, hoping that they’ll catch you with your guard down during this busy time of year.
So while knowing how to spot a great gift at a great price is solid skill to have this time of year, so is the ability to spot a scam. Let’s look at some of the worst ones out there, along with what you can do to steer clear of them.
Come this time of year, keeping tabs on all the packages you have in transit can get tricky. You may have an armload of them enroute at any given time, and scammers will look to slip into this mix with phony order confirmations sent to your mailbox or your phone by text. Packed with either an email attachment or a link to a bogus website, they’ll try to get you to download malware or visit a site that attempts to steal your identity.
These messages can look quite legit, so the best way to keep track of your orders is on the sites where you purchased them. Go directly to those sites rather than clicking on any links or attachments you get.
This scam plays out much like the fake order scam, yet in this case the crooks will send a phony package tracking notification, again either as a link or as an attachment. For starters, legitimate retailers won’t send tracking numbers in an attached file. If you see anything like that, it’s surely a scam designed to inject malware onto your device. In the case of a link, the scammers aim to send you to a site that will steal your personal info, just like in the case above.
Once again, the best way to track your packages is to go to the source. Visit the online store where you made your purchase, open your current orders, and get your package tracking information from there.
A classic scammer move is to “typosquat” phony email addresses and URLs that look awfully close to legitimate addresses of legitimate companies and retailers. So close that you may overlook them. They often appear in phishing emails and instead of leading you to a great deal, these can in fact link you to scam sites that can then lift your login credentials, payment info, or even funds should you try to place an order through them.
You can avoid these sites by going to the retailer’s site directly. Be skeptical of any links you receive by email, text, or direct message—it’s best to go to the site yourself by manually typing in the legitimate address yourself and look for the deal there.
At the heart of holiday shopping is scarcity. And scarcity is something scammers love. There’s always some super-popular holiday item that’s tough to find, and scammers will spin up phony websites and offers around those items to lure you in. They may use the typosquatting technique mentioned above to pose as a legitimate retailer, or they may set up a site with their own branding to look legitimate on their own (or at least try). Either way, these scams can hurt you in a couple of ways—one, you’ll pay for the goods and never receive them; and two, the scammers will now have your payment info and address, which they can use to commit further fraud.
If the pricing, availability, or delivery time all look too good to be true for the item in question, it may be a scam designed to harvest your personal info and accounts. Use caution here before you click. If you’re unsure about a product or retailer, read reviews from trusted websites to help see if it’s legitimate. (The Better Business Bureau is a great place to start—more on that in moment.)
In the season of giving, donating to charities in your name or in the name of others makes for a popular holiday gesture. Scammers know this too and will set up phony charities to cash in. Some indications that a phony charity has reached you include an urgent pitch that asks you to “act now.” A proper charity will certainly make their case for a donation, yet they won’t pressure you into it. Moreover, phony charities will outright ask for payment in the form of gift cards, wire transfers (like Western Union), money orders, or even cryptocurrency—because once those funds are sent, they’re nearly impossible to reclaim when you find out you’ve been scammed.
There are plenty of ways to make donations to legitimate charities, and the U.S. Federal Trade Commission (FTC) has a site full of resources so that you can make your donation truly count.
Some of it takes an eagle eye that can spot these scams as they pop up in your inbox, texts, social media feed, and so on. Yet you have further ways you can keep safe while shopping on Black Friday, Cyber Monday, and any time.
This is a great one to start with. Directly typing in the correct address for online stores and retailers is a prime way to avoid scammers online. In the case of retailers that you don’t know much about, the U.S. Better Business Bureau (BBB) asks shoppers to do their research and make sure that retailer has a good reputation. The BBB makes that easier with a listing of retailers you can search simply by typing in their name.
Secure websites begin their address with “https,” not just “http.” That extra “s” in stands for “secure,” which means that it uses a secure protocol for transmitting sensitive info like passwords, credit card numbers, and the like over the internet. It often appears as a little padlock icon in the address bar of your browser, so double-check for that. If you don’t see that it’s secure, it’s best to avoid making purchases on that website.
In the U.S., the Fair Credit Billing Act offers the public protection against fraudulent charges on credit cards, where citizens can dispute charges over $50 for goods and services that were never delivered or otherwise billed incorrectly. Note that many credit card companies have their own policies that improve upon the Fair Credit Billing Act as well. However, debit cards aren’t afforded the same protection under the Act. Avoid using a debit card while shopping online and use your credit card instead.
Two-factor authentication is an extra layer of defense on top of your username and password. It adds in the use of a special one-time-use code to access your account, usually sent to you via email or to your phone by text or a phone call. In all, it combines something you know, like your password, with something you have, like your smartphone. Together, that makes it tougher for a crook to hack your account. If any of your accounts support two-factor authentication, the few extra seconds it takes to set up is more than worth the big boost in protection you’ll get.
Public Wi-Fi in coffee shops and other public locations can expose your private surfing to prying eyes because those networks are open to all. Using a virtual private network (VPN) encrypts your browsing, shopping, and other internet traffic, thus making it secure from attempts at intercepting your data on public Wi-Fi, such as your passwords and credit card numbers.
What’s more, a VPN masks your whereabouts and your IP address, plus uses encryption that helps keep your activities private. As a result, companies and data brokers can potentially learn far less about you, your shopping, your travels, your habits, and any other information that they could possibly collect and otherwise profit from.
Yes, it’s true. Your information gets collected, bought, and solid online. In fact, personal information fuels a global data trading economy estimated at $200 billion U.S. dollars a year. Run by data brokers that keep hundreds and even thousands of data points on billions of people, these sites gather, analyze, buy, and sell this information to other companies as well as to advertisers. Likewise, these data brokers may sell this information to bad actors, such as hackers, spammers, and identity thieves who would twist this information for their own purposes.
Getting your info removed from these sites can seem like a daunting task. (Where do I start, and just how many of these sites are out there?) Our Personal Data Cleanup can help by regularly scanning these high-risk data broker sites for info like your home address, date of birth, and names of relatives. It identifies which sites are selling your data, and depending on your plan, automatically requests removal.
Another place where personal information is bought and sold, stored, and exchanged is the dark web. The problem is that it’s particularly difficult for you to determine what, if any, of your info is on the dark web, stashed away in places where hackers and thieves can get their hands on it. Identity monitoring can help. McAfee’s identity monitoring helps you keep your personal info safe by alerting you if your data is found on the dark web, an average of 10 months before our competitors.
Monitored info can range anywhere from bank account and credit card numbers to your email addresses and government ID number, depending on your location. If your information gets spotted, you’ll get an alert, along with steps you can take to minimize or even prevent damage if the information hasn’t already been put to illegal use.
Identity protection through McAfee takes identity monitoring a step further by offering, depending on your location and plan, identity theft coverage for financial losses and expenses due to identity theft, in addition to hands-on help from a recovery professional to help restore your identity—all in addition to the identity monitoring called out above, again depending on your location and plan.
Keeping an eye on your bills and statements as they come in can help you spot unusual activity on your accounts. A credit monitoring service can do that one better by keeping daily tabs on your credit report. While you can do this manually, there are limitations. First, it involves logging into each bureau and doing some digging of your own. Second, there are limitations as to how many free credit reports you can pull each year. A service does that for you and without impacting your credit score.
Depending on your location and plan, McAfee’s credit monitoring allows you to look after your credit score and the accounts within it to see fluctuations and help you identify unusual activity, all in one place, checking daily for signs of identity theft.
A complete suite of online protection software like McAfee+ can offer layers of extra security while you shop. In addition to the VPN, identity, credit monitoring, and other features mentioned above, it includes web browser protection that can block malicious and suspicious links that could lead you down the road to malware or a phishing scam—along with a password manager that can create strong, unique passwords and store them securely as well. Taken together, McAfee+ offers all-in-one online protection for your identity, privacy, and security that can keep you far safer when you shop online—and as you spend your time online in general.
Even if you take the proper precautions the unexpected can happen. Whether it’s a scam, an identity crime, or flat-out theft, there are steps you can take right away to help minimize the damage.
The first bit of advice is to take a deep breath and get right to work on recovery. From there, you can take the following steps:
Whether you spot a curious charge on your bank statement, discover potentially a fraudulent account when you check credit report, or when you get an alert from your monitoring service, let the bank or organization involved know you suspect fraud or theft. With a visit to their website, you can track down the appropriate number to call and get the investigation process started.
Some businesses will require you to file a local police report and acquire a case number to complete your claim. Beyond that, filing a report is a good idea in itself. Identity theft is still theft and reporting it provides an official record of the incident. Should your case of identity theft lead to someone impersonating you or committing a crime in your name, filing a police report right away can help clear your name down the road. Be sure to save any evidence you have, like statements or documents that are associated with the theft. They can help clean up your record as well.
In the U.S., the identity theft website from the Federal Trade Commission (FTC) is a fantastic resource should you find yourself in need. In addition to keeping records of the theft, the FTC can provide you with a step-by-step recovery plan—and even walk you through the process if you create an account with them. Additionally, reporting theft to the FTC can prove helpful if debtors come knocking to collect on any bogus charges in your name. With a copy of your report, you can ask debtors to stop.
An instance of identity fraud or theft, suspected or otherwise, is a good time to review your options for a credit freeze or lock. As mentioned earlier, see what the credit bureaus in your region offer, along with the terms and conditions of each. With the right decision, a freeze or lock can help minimize and prevent further harm.
Strongly consider using a monitoring service like the one we described earlier to help you continue to keep tabs on your identity. The unfortunate fact of identity theft and fraud is that it can mark the start of a long, drawn-out affair. One instance of theft can possibly lead to another, so even what may appear to be an isolated bad charge on your credit card calls for keeping an eye on your identity all around. Many of the tools you would use up to this point still apply, such as checking up on your credit reports, maintaining fraud alerts as needed, and reviewing your accounts closely—along with utilizing an identity monitoring service.
A recovery service can help you clean up your credit in the wake of fraud or theft, all by working on your behalf. Given the time, money, and stress that can come along with setting your financial record straight, leaning on the expertise of a professional can provide you with much-needed relief on several counts.
Just as it’s always been, hackers, scammers, and thieves want to ruin a good thing. In this case, it’s your spirit of giving and sharing in the holiday season. Yet with this list of top scams and ways you can avoid them, you can keep bad actors like them at bay. Remember, they’re counting on you to be in a hurry this time of year, and maybe a bit stressed and a little disorganized to boot. Take your time while shopping out there and keep an eye out for their tricks. That extra moment can save you far more time and money than you may think.
The post The Worst Black Friday and Cyber Monday Scams – And How to Avoid Them appeared first on McAfee Blog.