


The attack involved the first recorded abuse of a security vulnerability in a Dell driver that was patched in May 2021
The post ESET research into new attacks by Lazarus – Week in security with Tony Anscombe appeared first on WeLiveSecurity


ESET researchers have discovered Lazarus attacks against targets in the Netherlands and Belgium that use spearphishing emails connected to fake job offers
The post Amazon‑themed campaigns of Lazarus in the Netherlands and Belgium appeared first on WeLiveSecurity

How's this weeks video for a view?! It's a stunning location here in Bali and it's just been the absolute most perfect spot for a honeymoon, especially after weeks of guests and celebrations. But whoever hacked and ransom'd Optus didn't care about me taking time out and I've done more media in the last week than I have in a long time. I don't mind, it's a fascinating story the way this has unfolded and that's where most of the time in this week's video has gone, I hope you enjoy my analysis of what has become a pretty crazy story back home in Australia.

Microsoft has claimed a North Korean crew poses as LinkedIn recruiters to distribute poisoned versions of open source software packages.…
Updated Infosec experts have warned zero-day flaws in Microsoft’s Exchange server are being actively exploited.…
Two now-former eBay executives who pleaded guilty to cyberstalking charges this year have been sent down and fined tens of thousands of dollars.…


For almost a decade, the US Central Intelligence Agency communicated with informants abroad using a network of websites with hidden communications capabilities.…


Discovering and reporting critical security flaws that could allow foreign spies to steal sensitive US government data or launch cyberattacks via the Department of Defense's IT systems doesn't carry a high reward.…
Someone has recently created a large number of fake LinkedIn profiles for Chief Information Security Officer (CISO) roles at some of the world’s largest corporations. It’s not clear who’s behind this network of fake CISOs or what their intentions may be. But the fabricated LinkedIn identities are confusing search engine results for CISO roles at major companies, and they are being indexed as gospel by various downstream data-scraping sources.
If one searches LinkedIn for the CISO of the energy giant Chevron, one might find the profile for a Victor Sites, who says he’s from Westerville, Ohio and is a graduate of Texas A&M University.
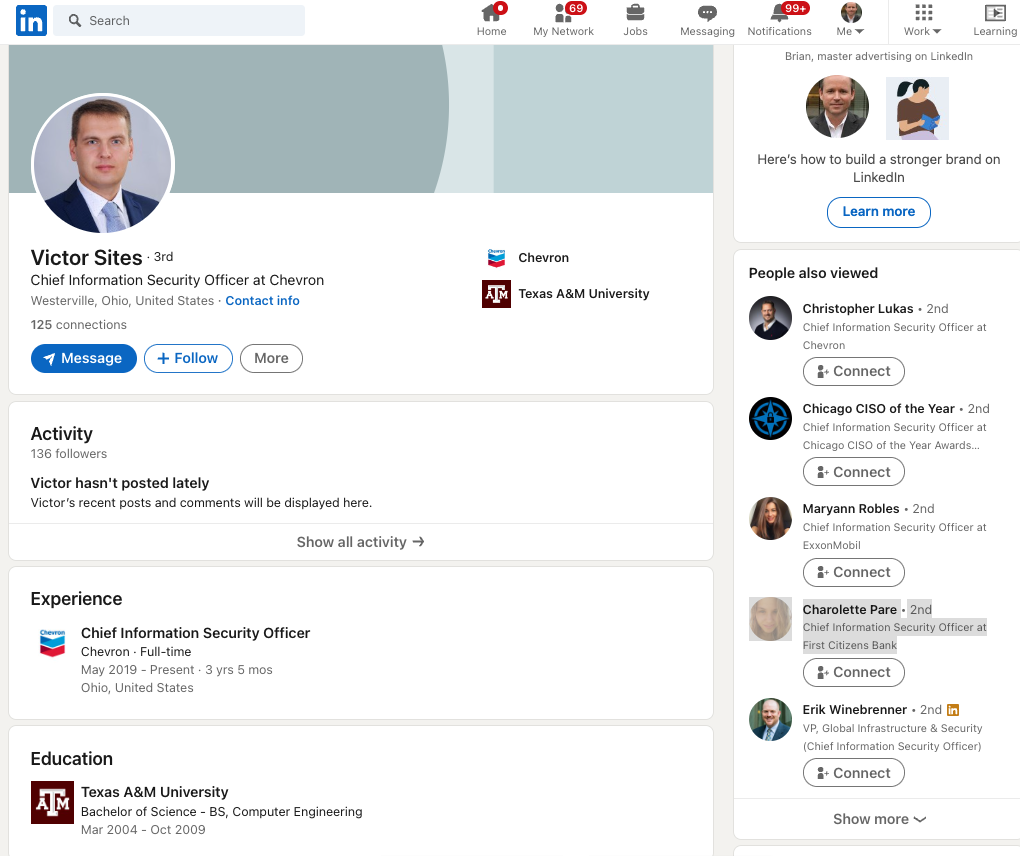
The LinkedIn profile for Victor Sites, who is most certainly NOT the CISO of Chevron.
Of course, Sites is not the real CISO of Chevron. That role is currently occupied by Christopher Lukas of Danville, Calif. If you were confused at this point, you might ask Google who it thinks is the current Chief Information Security Officer of Chevron. When KrebsOnSecurity did that earlier this morning, the fake CISO profile was the very first search result returned (followed by the LinkedIn profile for the real Chevron CISO).
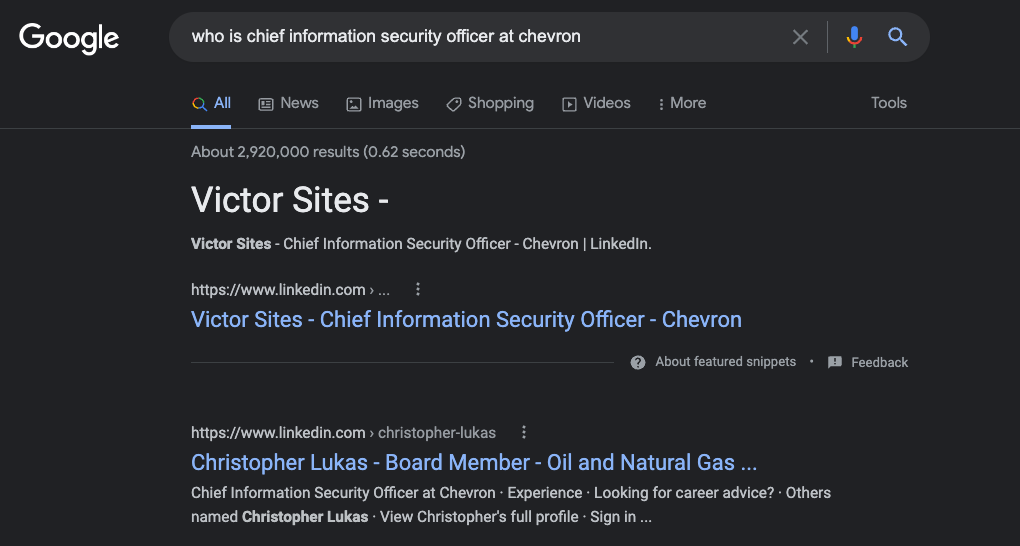
Helpfully, LinkedIn seems to be able to detect something in common about all these fake CISO profiles, because it suggested I view a number of them in the “People Also Viewed” column seen in the image above. There are two fake CISO profiles suggested there, including one for a Maryann Robles, who claims to be the CISO of another energy giant — ExxonMobil.
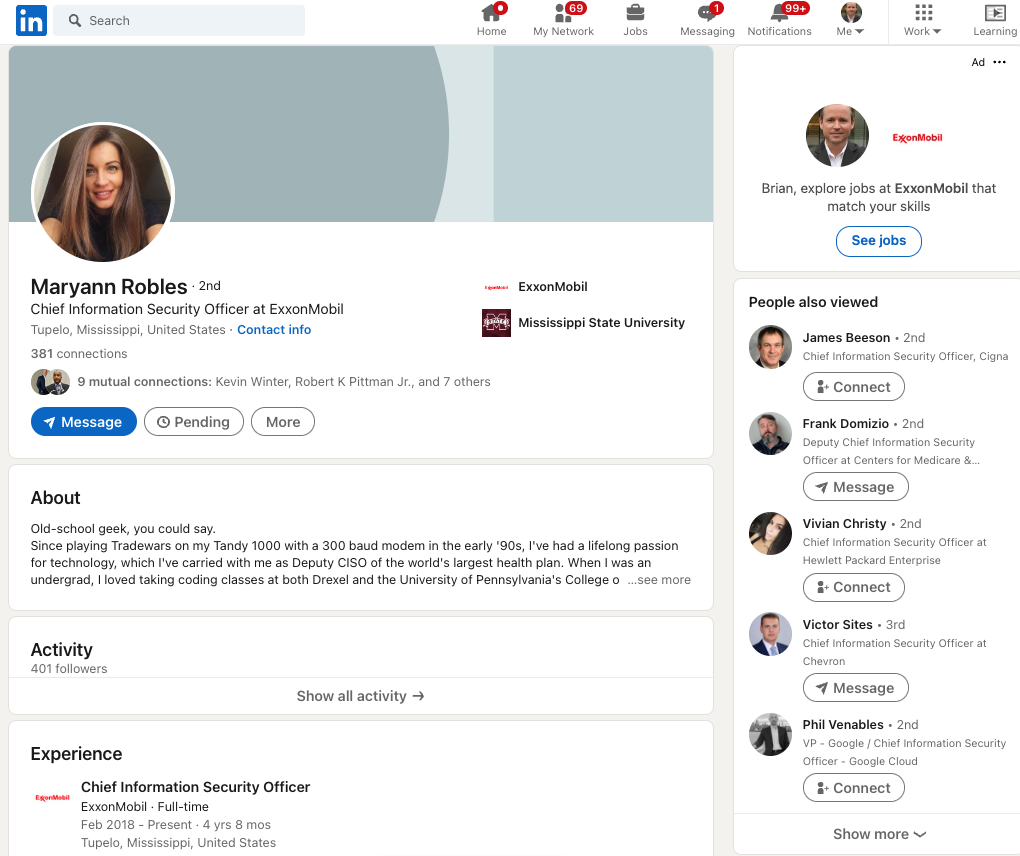
Maryann’s profile says she’s from Tupelo, Miss., and includes this detail about how she became a self-described “old-school geek.”
“Since playing Tradewars on my Tandy 1000 with a 300 baud modem in the early ’90s, I’ve had a lifelong passion for technology, which I’ve carried with me as Deputy CISO of the world’s largest health plan,” her profile reads.
However, this description appears to have been lifted from the profile for the real CISO at the Centers for Medicare & Medicaid Services in Baltimore, Md.
Interestingly, Maryann’s LinkedIn profile was accepted as truth by Cybercrime Magazine’s CISO 500 listing, which claims to maintain a list of the current CISOs at America’s largest companies:
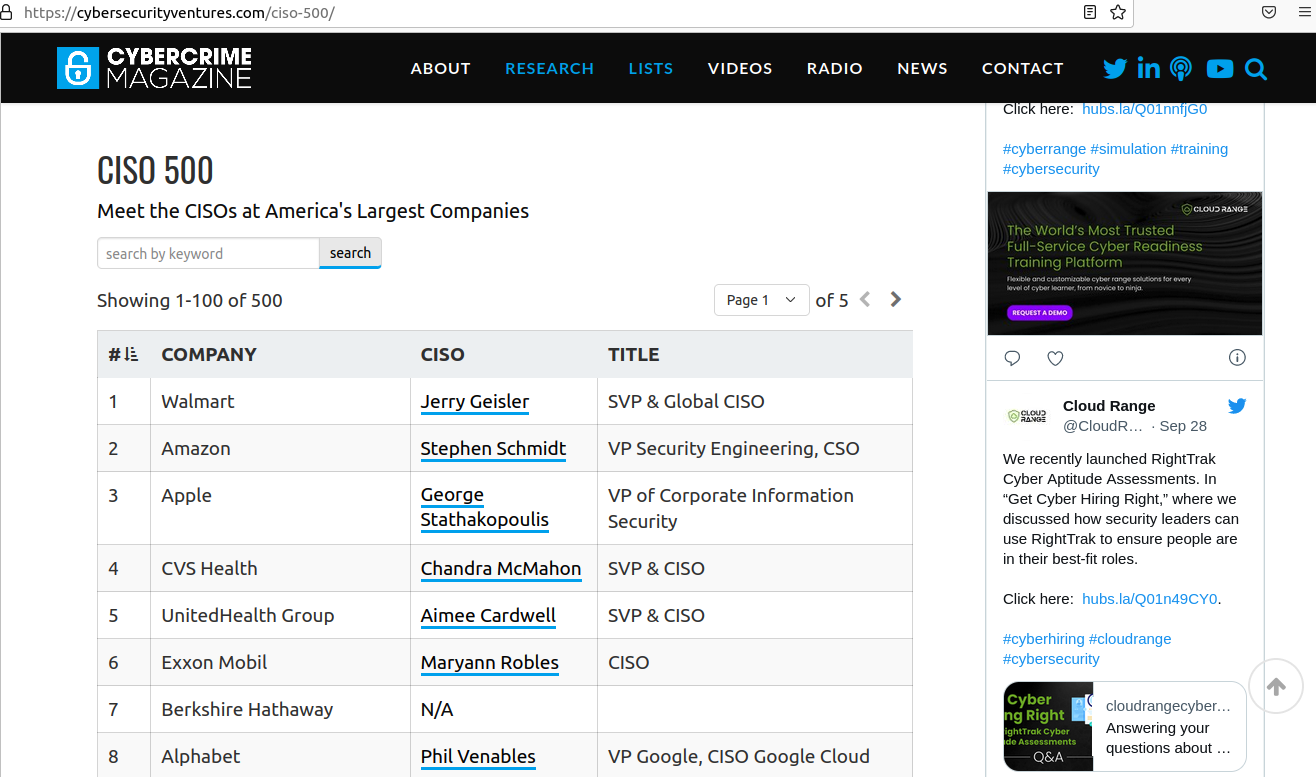
The fake CISO for ExxOnMobil was indexed in Cybercrime Magazine’s CISO 500.
Rich Mason, the former CISO at Fortune 500 firm Honeywell, began warning his colleagues on LinkedIn about the phony profiles earlier this week.
“It’s interesting the downstream sources that repeat LinkedIn bogus content as truth,” Mason said. “This is dangerous, Apollo.io, Signalhire, and Cybersecurity Ventures.”
Google wasn’t fooled by the phony LinkedIn profile for Jennie Biller, who claims to be CISO at biotechnology giant Biogen (the real Biogen CISO is Russell Koste). But Biller’s profile is worth mentioning because it shows how some of these phony profiles appear to be quite hastily assembled. Case in point: Biller’s name and profile photo suggest she is female, however the “About” description of her accomplishments uses male pronouns. Also, it might help that Jennie only has 18 connections on LinkedIn.
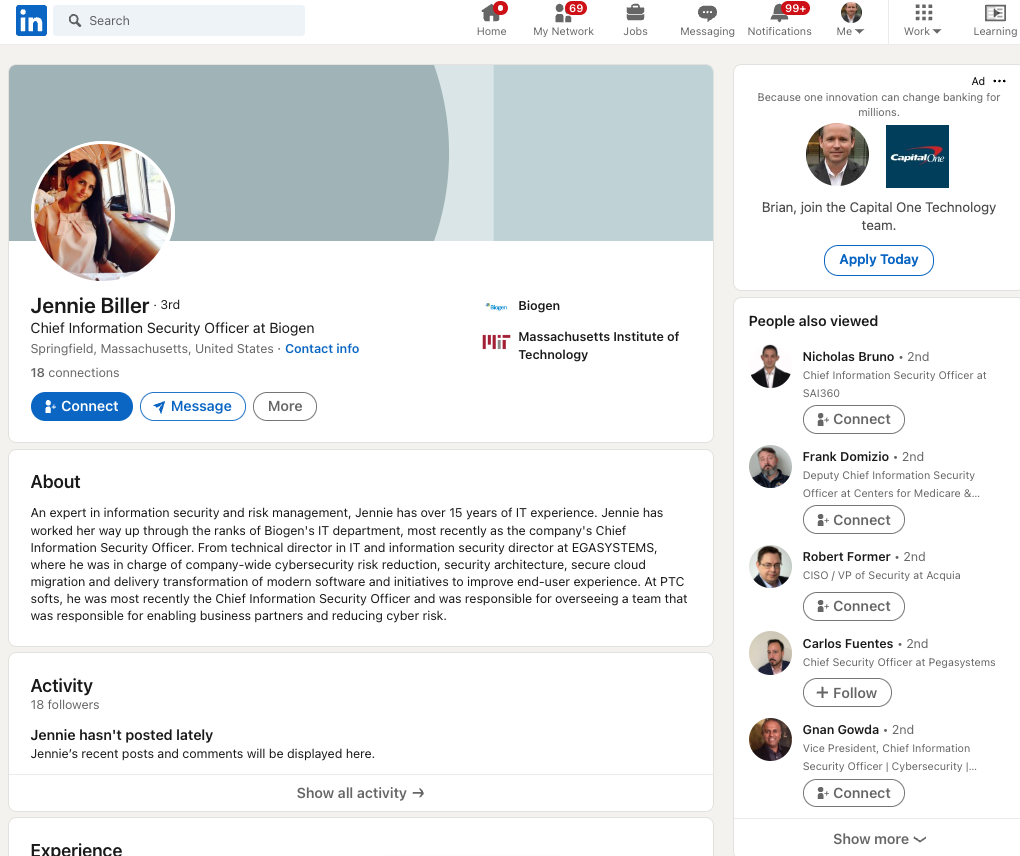
Again, we don’t know much about who or what is behind these profiles, but in August the security firm Mandiant (recently acquired by Google) told Bloomberg that hackers working for the North Korean government have been copying resumes and profiles from leading job listing platforms LinkedIn and Indeed, as part of an elaborate scheme to land jobs at cryptocurrency firms.
None of the profiles listed here responded to requests for comment (or to become a connection).
In a statement provided to KrebsOnSecurity, LinkedIn said its teams were actively working to take these fake accounts down.
“We do have strong human and automated systems in place, and we’re continually improving, as fake account activity becomes more sophisticated,” the statement reads. “In our transparency report we share how our teams plus automated systems are stopping the vast majority of fraudulent activity we detect in our community – around 96% of fake accounts and around 99.1% of spam and scam.”
LinkedIn could take one simple step that would make it far easier for people to make informed decisions about whether to trust a given profile: Add a “created on” date for every profile. Twitter does this, and it’s enormously helpful for filtering out a great deal of noise and unwanted communications.
The former CISO Mason said LinkedIn also could experiment with offering something akin to Twitter’s verified mark to users who chose to validate that they can respond to email at the domain associated with their stated current employer.
“If I saw that a LinkedIn profile had been domain-validated, then my confidence in that profile would go way up,” Mason said, noting that many of the fake profiles had hundreds of followers, including dozens of real CISOs. Maryann’s profile grew by a hundred connections in just the past few days, he said.
“If we have CISOs that are falling for this, what hopes do the masses have?” Mason said.
Mason said LinkedIn also needs a more streamlined process for allowing employers to remove phony employee accounts. He recently tried to get a phony profile removed from LinkedIn for someone who falsely claimed to have worked for his company.
“I shot a note to LinkedIn and said please remove this, and they said, well, we have to contact that person and arbitrate this,” he said. “They gave the guy two weeks and he didn’t respond, so they took it down. But that doesn’t scale, and there needs to be a mechanism where an employer can contact LinkedIn and have these fake profiles taken down in less than two weeks.”










