


Webinar The cyber security of any organisation or enterprise relies on the integrity of its identity management structure. After all, there's no shortage of bad actors looking for a chink in the wall.…
In brief NATO officials are investigating after criminals put up some data for sale on dark forums that they claim is "classified" information stolen from European missile maker MBDA.…
Microsoft appears to have fixed a problem that saw its Defender antivirus program identify apps based on the Chromium browser engine and/or Electron JavaScript framework as malware, and suggest users remove them.…
China will conduct a three month blitz to cleanse the local internet of "rumors and false information".…
A 21-year-old New Jersey man has been arrested and charged with stalking in connection with a federal investigation into groups of cybercriminals who are settling scores by hiring people to carry out physical attacks on their rivals. Prosecutors say the defendant recently participated in several of these schemes — including firing a handgun into a Pennsylvania home and torching a residence in another part of the state with a Molotov Cocktail.
Patrick McGovern-Allen of Egg Harbor Township, N.J. was arrested on Aug. 12 on a warrant from the U.S. Federal Bureau of Investigation. An FBI complaint alleges McGovern-Allen was part of a group of co-conspirators who are at the forefront of a dangerous escalation in coercion and intimidation tactics increasingly used by competing cybercriminal groups.
Prosecutors say that around 2 a.m. on Jan 2, 2022, McGovern-Allen and an unidentified co-conspirator fired multiple handgun rounds into a residence in West Chester, Pa. Fortunately, none of the residents inside the home at the time were injured. But prosecutors say the assailants actually recorded video of the attack as “proof” that the shooting had been carried out.
A copy of that video was obtained by KrebsOnSecurity. According to investigators, McGovern-Allen was one of the shooters, who yelled “Justin Active was here” as they haphazardly fired at least eight rounds into the lower story of the West Chester residence.
On Dec. 18, 2021, police in Abington Township, Pa., responded to reports of a house fire from homeowners who said it sounded like something was thrown at their residence just prior to the fire.
Weeks later, on the day of the shooting in West Chester, a detective with the Westtown East Goshen Police Department contacted the Abington police and shared another video that was circulating on several online message boards that appeared to show two individuals setting fire to the Abington Township residence. The criminal complaint said the two police officers agreed the same suspect was present in both videos.
A copy of that video also was obtained by KrebsOnSecurity, and it shows at least two individuals smashing a window, then lighting a rag-soaked Mad Dog 20/20 grape wine bottle and hurling it at the side of the home [Update: My apologies for the file download link, but YouTube just deleted both of the videos included in this story — for allegedly violating their community standards].
“The Molotov cocktail caused the immediate surrounding area to ignite, including the siding of the house, grass, and the wooden chair,” the government’s complaint against McGovern-Allen states. “The two suspects then fled on foot toward the street and begin yelling something when the video stops.”
The government mentions the victims only by their initials — “K.M.” in the shooting and “A.R.” in the firebombing — but said both had been the target of previous harassment by rival cybercriminal groups that included swatting attacks, wherein the perpetrators spoof a distress call to the police about a hostage situation, suicide or bomb threat with the goal of sending a heavily-armed police response to a targeted address.
A number of previous swatting incidents have turned deadly. But these more “hands-on” and first person attacks are becoming increasingly common within certain cybercriminal communities, particularly those engaged in SIM swapping, a crime in which identity thieves hijack a target’s mobile phone number and use that to wrest control over the victim’s various online accounts and identities.
The complaint mentions a handle and user ID allegedly used by McGovern-Allen’s online persona “Tongue” on the Discord chat service, (user: “Tongue#0001”).
“In the chats, [Tongue] tells other Discord users that he was the person who shot K.M.’s house and that he was willing to commit firebombings using Molotov Cocktails,” the complaint alleges. “For example, in one Discord chat from March 2022, [the defendant] states ‘if you need anything done for $ lmk [“let me know”]/I did a shooting/Molotov/but I can also do things for ur entertainment.”
KrebsOnsecurity reviewed hundreds of chat records tied to this Tongue alias, and it appears both attacks were motivated by a desire to get back at a rival cybercriminal by attacking the female friends of that rival.
Recall that the shooters in the West Chester, Pa. incident shouted “Justin Active was here.” Justin Active is the nickname of an individual who is just as active in the same cybercriminal channels, but who has vehemently denied knowledge of or participation in the shooting. Justin Active said on Telegram that the person targeted in the shooting was his ex-girlfriend, and that the firebombing targeted another friend of his.
Justin Active has claimed for months that McGovern-Allen was responsible for both attacks, saying they were intended as an intimidation tactic against him. “DO THE PATRICK MCGOVERN ALLEN RAID DANCE!,” Justin Active’s alias “Nutcase68” shouted on Telegram on Aug. 12, the same day McGovern-Allen was arrested by authorities.
Justin Active’s version of events seems to be supported by a reference in the criminal complaint to an April 2, 2022 chat in which Tongue explained the reason for the shooting.
“The video/is [K]’s house/getting shit/shot/justin active/ was her current bf/ the reason it happened,” Tongue explained. “So that’s why Justin active was there.”
The Telegram chat channels that Justin Active and Tongue both frequented have hundreds to thousands of members each, and some of the more interesting solicitations on these communities are job offers for in-person assignments and tasks that can be found if one searches for posts titled, “If you live near,” or “IRL job” — short for “in real life” job.
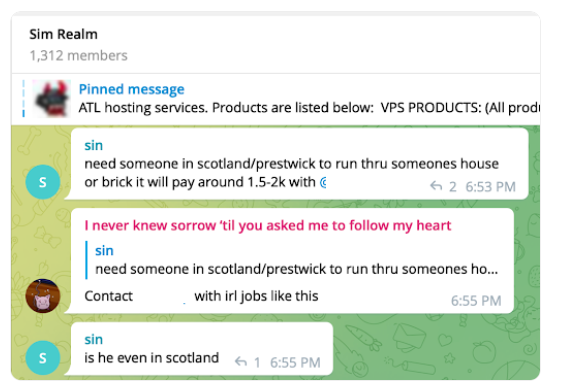
A number of these classified ads are in service of performing “brickings,” where someone is hired to visit a specific address and toss a brick through the target’s window.
“If you live near Edmonton Canada dm me need someone bricked,” reads on Telegram message on May 31, 2022.
“If you live near [address redacted] Lakewood, CA, dm [redacted] Paying 3k to slash the tires,” reads another help wanted ad in the same channel on Feb. 24, 2022. “If you live near here and can brick them, dm [address omitted] Richland, WA,” reads another from that same day.
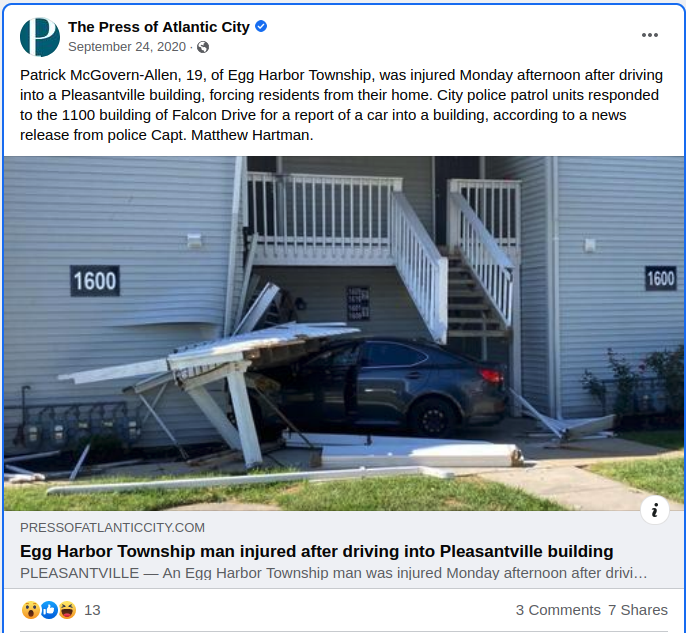
McGovern-Allen was in the news not long ago. According to a Sept. 2020 story from The Press of Atlantic City, a then 19-year-old Patrick McGovern Allen was injured after driving into a building and forcing residents from their home.
“Police found a 2007 Lexus, driven by Patrick McGovern-Allen, 19, that had lost control and left the road, crashing into the eastern end of the 1600 building,” the story recounted. “The car was driven through the steps that provide access to the second-floor apartments, destroying them, and also caused damage to the outer wall.”
A search on the Inmate Locator of the U.S. Bureau of Prisons website shows that McGovern-Allen remains in federal custody at a detention facility in Philadelphia. He’s currently represented by a public defender who has not responded to requests for comment.
A copy of the criminal complaint against McGovern-Allen is available here (PDF).
Many of the individuals involved in paying others to commit these physical attacks are also frequent participants in several Telegram channels focused singularly on SIM swapping activity. As a result, the vast majority of the people being targeted for brickings and other real-life physical assaults tend to be other cybercriminals involved in SIM swapping crimes (or individuals on the periphery of that scene).
There are dozens of SIM swappers who are now teenage or 20-something millionaires, by virtue of having stolen vast sums of cryptocurrencies from SIM swapping victims. And now many of these same individuals are finding that communities like Telegram can be leveraged to hire physical harassment and intimidation of their rivals and competitors.
The primary barrier to hiring someone to brick a home or slash some tires seems to be the costs involved: A number of solicitations for these services advertised payment of $3,000 or more upon proof of successful completion, which usually involves recording the attack and hiring a getaway driver in the town where the crime is to take place (calling a cab or hailing an Uber from the scene of a bricking isn’t the brightest idea).
My fear is these violence-as-a-service offerings will at some point migrate outside of the SIM swapping communities. This is precisely what happened with swatting, which for years was a crime perpetrated almost exclusively against online gamers and people streaming their games online. These days, swatting attacks are commonly used by SIM swapping groups as a way to harass and extort regular Internet users into giving up prized social media account names that can be resold for thousands of dollars.



Well, after a crazy amount of work, a lot of edits, reflection, and feedback cycles, "Pwned" is almost here:
This better be a sizzling read @troyhunt or I'll be crashing the wedding in ways never done before.
— Mike Thompson (@AppSecBloke) August 30, 2022
Also, I thought they'd cancelled Neighbours? 😉❤️ pic.twitter.com/jrYIKtL0Uh
The preview cycle is in full swing with lots of feedback coming in and revisions being made before we push it live to the masses. This is really exciting and I can't wait to get the book out there in front of everyone, stay tuned 😊

Google and its YouTube subsidiary have joined other social media networks pledging to keep the 2022 US midterm elections safe and free from Russian trolls — and anyone else spewing democracy-damaging disinformation – by taking down such content.…
A US man has admitted he broke the law when he used 3D printers to make components converting semi-automatic guns to full auto.…





US mobile carriers know a lot about where their customers every move, and according to letters sent to the Federal Communications Commission (FCC), they routinely store such location data for years, willingly hand it over to law enforcement if served a proper subpoena, and say users can't opt out.…




A ruling handed down from the Delhi High Court this week declared that Telegram must hand over information such as IP addresses, mobile numbers, and devices used by channels on the platform involved in copyright infringement.…


What if your organization is hit by a cyberattack that is attributed to a nation state? Would your insurance cover the costs of the attack?
The post Will cyber‑insurance pay out? – Week in security with Tony Anscombe appeared first on WeLiveSecurity

