US security technology provider L3Harris has courted controversial Israeli spyware firm NSO with an aim to buy it, according to reports.…
The UK's response to China's well-publicized efforts to use technology standards to shape the world in its image has been "incoherent and muted" according to report by the House of Commons Foreign Affairs Committee.…
Twice in the past month KrebsOnSecurity has heard from readers who had their accounts at big-three credit bureau Experian hacked and updated with a new email address that wasn’t theirs. In both cases the readers used password managers to select strong, unique passwords for their Experian accounts. Research suggests identity thieves were able to hijack the accounts simply by signing up for new accounts at Experian using the victim’s personal information and a different email address.

John Turner is a software engineer based in Salt Lake City. Turner said he created the account at Experian in 2020 to place a security freeze on his credit file, and that he used a password manager to select and store a strong, unique password for his Experian account.
Turner said that in early June 2022 he received an email from Experian saying the email address on his account had been changed. Experian’s password reset process was useless at that point because any password reset links would be sent to the new (impostor’s) email address.
An Experian support person Turner reached via phone after a lengthy hold time asked for his Social Security Number (SSN) and date of birth, as well as his account PIN and answers to his secret questions. But the PIN and secret questions had already been changed by whoever re-signed up as him at Experian.
“I was able to answer the credit report questions successfully, which authenticated me to their system,” Turner said. “At that point, the representative read me the current stored security questions and PIN, and they were definitely not things I would have used.”
Turner said he was able to regain control over his Experian account by creating a new account. But now he’s wondering what else he could do to prevent another account compromise.
“The most frustrating part of this whole thing is that I received multiple ‘here’s your login information’ emails later that I attributed to the original attackers coming back and attempting to use the ‘forgot email/username’ flow, likely using my SSN and DOB, but it didn’t go to their email that they were expecting,” Turner said. “Given that Experian doesn’t support two-factor authentication of any kind — and that I don’t know how they were able to get access to my account in the first place — I’ve felt very helpless ever since.”
Arthur Rishi is a musician and co-executive director of the Boston Landmarks Orchestra. Rishi said he recently discovered his Experian account had been hijacked after receiving an alert from his credit monitoring service (not Experian’s) that someone had tried to open an account in his name at JPMorgan Chase.
Rishi said the alert surprised him because his credit file at Experian was frozen at the time, and Experian did not notify him about any activity on his account. Rishi said Chase agreed to cancel the unauthorized account application, and even rescinded its credit inquiry (each credit pull can ding your credit score slightly).
But he never could get anyone from Experian’s support to answer the phone, despite spending what seemed like eternity trying to progress through the company’s phone-based system. That’s when Rishi decided to see if he could create a new account for himself at Experian.
“I was able to open a new account at Experian starting from scratch, using my SSN, date of birth and answering some really basic questions, like what kind of car did you take out a loan for, or what city did you used to live in,’ Rishi said.
Upon completing the sign-up, Rishi noticed that his credit was unfrozen.
Like Turner, Rishi is now worried that identity thieves will just hijack his Experian account once more, and that there is nothing he can do to prevent such a scenario. For now, Rishi has decided to pay Experian $25.99 a month to more closely monitor his account for suspicious activity. Even using the paid Experian service, there were no additional multi-factor authentication options available, although he said Experian did send a one-time code to his phone via SMS recently when he logged on.
“Experian now sometimes does require MFA for me if I use a new browser or have my VPN on,” Rishi said, but he’s not sure if Experian’s free service would have operated differently.
“I get so angry when I think about all this,” he said. “I have no confidence this won’t happen again.”
In a written statement, Experian suggested that what happened to Rishi and Turner was not a normal occurrence, and that its security and identity verification practices extend beyond what is visible to the user.
“We believe these are isolated incidents of fraud using stolen consumer information,” Experian’s statement reads. “Specific to your question, once an Experian account is created, if someone attempts to create a second Experian account, our systems will notify the original email on file.”
“We go beyond reliance on personally identifiable information (PII) or a consumer’s ability to answer knowledge-based authentication questions to access our systems,” the statement continues. “We do not disclose additional processes for obvious security reasons; however, our data and analytical capabilities verify identity elements across multiple data sources and are not visible to the consumer. This is designed to create a more positive experience for our consumers and to provide additional layers of protection. We take consumer privacy and security seriously, and we continually review our security processes to guard against constant and evolving threats posed by fraudsters.”
KrebsOnSecurity sought to replicate Turner and Rishi’s experience — to see if Experian would allow me to re-create my account using my personal information but a different email address. The experiment was done from a different computer and Internet address than the one that created the original account years ago.
After providing my Social Security Number (SSN), date of birth, and answering several multiple choice questions whose answers are derived almost entirely from public records, Experian promptly changed the email address associated with my credit file. It did so without first confirming that new email address could respond to messages, or that the previous email address approved the change.
Experian’s system then sent an automated message to the original email address on file, saying the account’s email address had been changed. The only recourse Experian offered in the alert was to sign in, or send an email to an Experian inbox that replies with the message, “this email address is no longer monitored.”
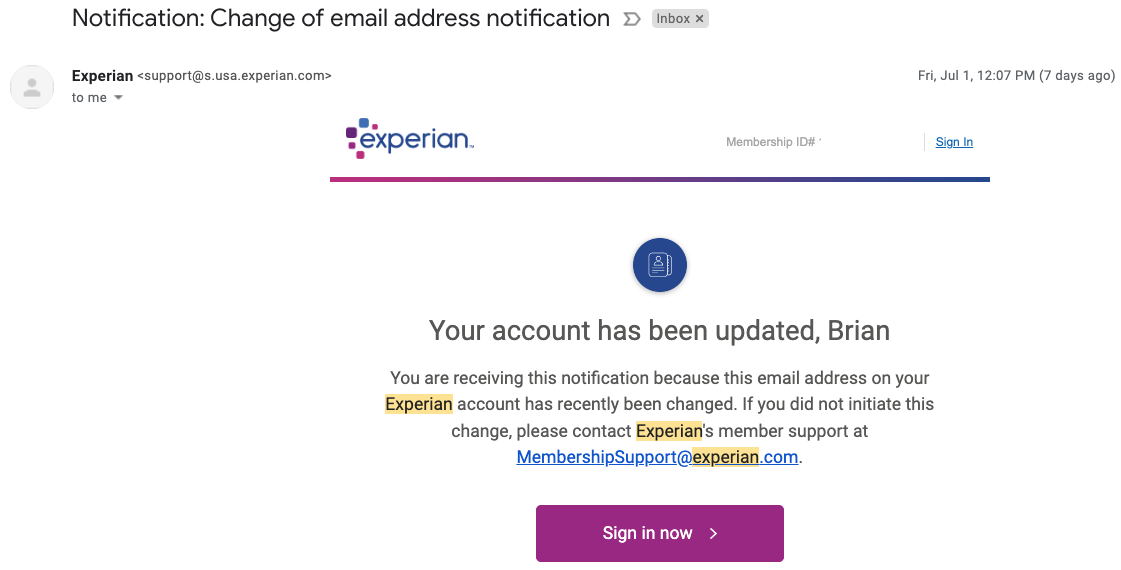
After that, Experian prompted me to select new secret questions and answers, as well as a new account PIN — effectively erasing the account’s previously chosen PIN and recovery questions. Once I’d changed the PIN and security questions, Experian’s site helpfully reminded me that I have a security freeze on file, and would I like to remove or temporarily lift the security freeze?
To be clear, Experian does have a business unit that sells one-time password services to businesses. While Experian’s system did ask for a mobile number when I signed up a second time, at no time did that number receive a notification from Experian. Also, I could see no option in my account to enable multi-factor authentication for all logins.
How does Experian differ from the practices of Equifax and TransUnion, the other two big consumer credit reporting bureaus? When KrebsOnSecurity tried to re-create an existing account at TransUnion using my Social Security number, TransUnion rejected the application, noting that I already had an account and prompting me to proceed through its lost password flow. The company also appears to send an email to the address on file asking to validate account changes.
Likewise, trying to recreate an existing account at Equifax using personal information tied to my existing account prompts Equifax’s systems to report that I already have an account, and to use their password reset process (which involves sending a verification email to the address on file).
KrebsOnSecurity has long urged readers in the United States to place a security freeze on their files with the three major credit bureaus. With a freeze in place, potential creditors can’t pull your credit file, which makes it very unlikely anyone will be granted new lines of credit in your name. I’ve also advised readers to plant their flag at the three major bureaus, to prevent identity thieves from creating an account for you and assuming control over your identity.
The experiences of Rishi, Turner and this author suggest Experian’s practices currently undermine both of those proactive security measures. Even so, having an active account at Experian may be the only way you find out when crooks have assumed your identity. Because at least then you should receive an email from Experian saying they gave your identity to someone else.
In April 2021, KrebsOnSecurity revealed how identity thieves were exploiting lax authentication on Experian’s PIN retrieval page to unfreeze consumer credit files. In those cases, Experian failed to send any notice via email when a freeze PIN was retrieved, nor did it require the PIN to be sent to an email address already associated with the consumer’s account.
A few days after that April 2021 story, KrebsOnSecurity broke the news that an Experian API was exposing the credit scores of most Americans.
Emory Roan, policy counsel for the Privacy Rights Clearinghouse, said Experian not offering multi-factor authentication for consumer accounts is inexcusable in 2022.
“They compound the problem by gating the recovery process with information that’s likely available or inferable from third party data brokers, or that could have been exposed in previous data breaches,” Roan said. “Experian is one of the largest Consumer Reporting Agencies in the country, trusted as one of the few essential players in a credit system Americans are forced to be part of. For them to not offer consumers some form of (free) MFA is baffling and reflects extremely poorly on Experian.”
Nicholas Weaver, a researcher for the International Computer Science Institute at University of California, Berkeley, said Experian has no real incentive to do things right on the consumer side of its business. That is, he said, unless Experian’s customers — banks and other lenders — choose to vote with their feet because too many people with frozen credit files are having to deal with unauthorized applications for new credit.
“The actual customers of the credit service don’t realize how much worse Experian is, and this isn’t the first time Experian has screwed up horribly,” Weaver said. “Experian is part of a triopoly, and I’m sure this is costing their actual customers money, because if you have a credit freeze that gets lifted and somebody loans against it, it’s the lender who eats that fraud cost.”
And unlike consumers, he said, lenders do have a choice in which of the triopoly handles their credit checks.
“I do think it’s important to point out that their real customers do have a choice, and they should switch to TransUnion and Equifax,” he added.
More greatest hits from Experian:
2017: Experian Site Can Give Anyone Your Credit Freeze PIN
2015: Experian Breach Affects 15 Million Customers
2015: Experian Breach Tied to NY-NJ ID Theft Ring
2015: At Experian, Security Attrition Amid Acquisitions
2015: Experian Hit With Class Action Over ID Theft Service
2014: Experian Lapse Allowed ID Theft Service Access to 200 Million Consumer Records
2013: Experian Sold Consumer Data to ID Theft Service
Update, 10:32 a.m.: Updated the story to clarify that while Experian does sometimes ask users to enter a one-time code sent via SMS to the number on file, there does not appear to be any option to enable this on all logins.
Details have emerged on how more than a billion personal records were stolen in China and put up for sale on the dark web, and it all boils down to a unprotected online dashboard that left the data open to anyone who could find it.…






Sponsored Post If you do any sort of business via the web, the damage caused by a distributed denial of service (DDoS) attack could be catastrophic for your bottom line.…








Vacations are a great time to unwind, but if you're not careful, you may face a digital disaster. Here's how to keep your devices and data secure while you're on the move
The post Avoid travel digital disasters – Week in security with Tony Anscombe appeared first on WeLiveSecurity
Scammers don't take the summer off – be on your guard when buying your Crit'Air sticker
The post Driving to France this summer? Watch out for scam websites before you go appeared first on WeLiveSecurity








![]()








It’s a question we get a lot from parents: “How can I keep my kids safe when they are constantly hopping between so many different apps?” We get it, there’s a lot to stay on top and all of it changes constantly. Unfortunately, that question doesn’t have a simple answer. But there are some baseline actions every parent can take to boost their child’s safety on popular apps like TikTok, Snapchat, and Instagram.
The safety equation is threefold, with every piece as important to your child’s overall safety as the next.
A report released in 2021 by Common Sense Media found that teenagers (ages 13-18) use an average of nine hours of entertainment media per day and that tweens (ages 8-12) use an average of six hours a day, not including time spent using media for school or homework. The report also found that boys spend more time on gaming devices while girls spend more time on social media and that mobile devices now account for 41% of all screen time among tweens and 46% among teens.
With those numbers increasing each year, it’s even more important to understand the different ways parents can help kids stay safe. Let’s break down a few safety basics on each app that are easy to access and use.
TikTok has some impressive safety guidelines broken down into topics parents could easily use as a springboard for some great family discussions. The guidelines and the Safety Center cover issues such as dangerous TikTok challenges and how to deal with other digital threats such as bullying, sexual content, fake news, and hateful behavior. You can increase safeguards using TikTok’s:
Every app functions differently and thus, offers different ways to boost security. Snapchat provides a helpful guide for parents and educators, including safety tips and conversation starters. You can increase safeguards using Snapchat’s:
Instagram offers parents and minor users a library of safety and mental health resources accessible via the app’s Community Tab at the bottom of its home page. You can increase safeguards using Instagram’s:
One of the most powerful safety features is you—a child’s mom, dad, or guardian. Your face-to-face, heart-to-heart connection will speak loudest in your child’s life. If you haven’t lately, ask your child what’s going on in their digital life, who their friends are, what they’ve created to share, and what’s new, hilarious, or trending. You may get some resistance now and then but don’t let that discourage you from pressing in and doing all the things that help keep them as safe as possible online.
The post Setting Up Parental Controls in TikTok, Instagram & Snapchat appeared first on McAfee Blog.