







As millions of people around the world practice social distancing and work their office jobs from home, video conferencing has quickly become the new norm. Whether you’re attending regular work meetings, partaking in a virtual happy hour with friends, or catching up with extended family across the globe, video conferencing is a convenient alternative to many of the activities we can no longer do in real life. But as the rapid adoption of video conferencing tools and apps occurs, is security falling by the wayside?
One security vulnerability that has recently made headlines is the ability for uninvited attendees to bombard users’ virtual meetings. How? According to Forbes, many users have posted their meeting invite links on social media sites like Twitter. An attacker can simply click on one of these links and interrupt an important conference call or meeting with inappropriate content.
Online conferencing tools allow users to hold virtual meetings and share files via chat. But according to Security Boulevard, communicating confidential business information quickly and privately can be challenging with these tools. For example, users are not always immediately available, even when working from home. In fact, many parents are simultaneously doubling as working parents and teachers with the recent closure of schools and childcare providers. If a user needs to share private information with a coworker but they are unable to connect by video or phone, they might revert to using a messaging platform that lacks end-to-end encryption, a feature that prevents third-party recipients from seeing private messages. This could lead to leaks or unintended sharing of confidential data, whether personal or corporate. What’s more, the lack of using a secure messaging platform could present a hacker with an opportunity to breach a victim’s data or device. Depending on the severity of this type of breach, a victim could be at risk of identity theft.
With the recent surge of new video conferencing users, privacy policies have been placed under a microscope. According to WIRED, some online conferencing tools have had to update their policies to reflect the collection of user information and meeting content used for advertising or other marketing efforts. Another privacy concern was brought to light by a video conferencing tool’s attention-tracking feature. This alerts the virtual meeting host when an attendee hasn’t had the meeting window in their device foreground for 30 seconds, resulting in users feeling that their privacy has been compromised.
As users become accustomed to working from home, video conferencing tools will continue to become a necessary avenue for virtual communication. But how can users do so while putting their online security first? Follow these tips to help ensure that your virtual meetings are safeguarded:
There are plenty of video conferencing tools available online. Before downloading the first one you see, do your research and check for possible security vulnerabilities around the tools. Does the video conferencing tool you’re considering use end-to-end encryption? This ensures that only meeting participants have the ability to decrypt secure meeting content. Additionally, be sure to read the privacy policies listed by the video conferencing programs to find the one that is the most secure and fits your needs.
To ensure that only invited attendees can access your meeting, make sure they are password protected. For maximum safety, activate passwords for new meetings, instant meetings, personal meetings, and people joining by phone.
To keep users (either welcome or unwelcome) from taking control of your screen while you’re video conferencing, select the option to block everyone except the host (you) from screen sharing.
By turning on automatic updates, you are guaranteed to have all the latest security patches and enhancements for your video conferencing tool as soon as they become available.
The post How Secure Is Video Conferencing? appeared first on McAfee Blog.































By Oliver Devane
Update: In the past 24 hours (from time of publication) McAfee has identified 15 more scam sites bringing the total to 26. The combined value of the wallets shared on these sites is over $1,300,000 which is an increase of roughly $1,000,000 since this blog was last published. This highlights the scale of this current scam campaign. The table within this blog has been updated to include the new sites and crypto-wallets.
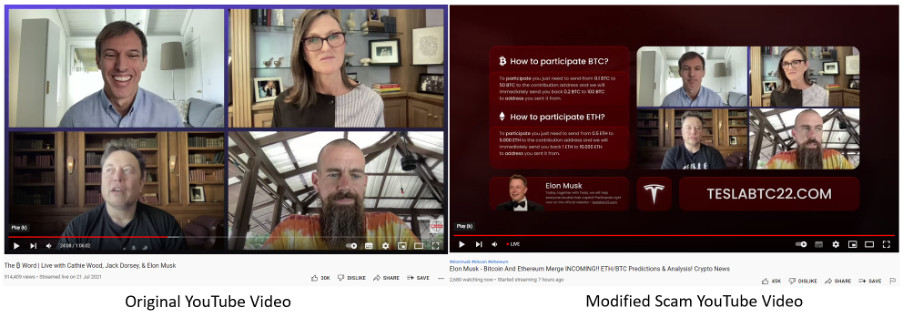
McAfee has identified several Youtube channels which were live-streaming a modified version of a live stream called ‘The B Word’ where Elon Musk, Cathie Wood, and Jack Dorsey discuss various aspects of cryptocurrency.
The modified live streams make the original video smaller and put a frame around it advertising malicious sites that it claims will double the amount of cryptocurrency you send them. As the topic of the video is on cryptocurrency it adds some legitimacy to the websites being advertised.
The original video is shown below on the left and a modified one which includes a reference to a scam site is shown on the right.
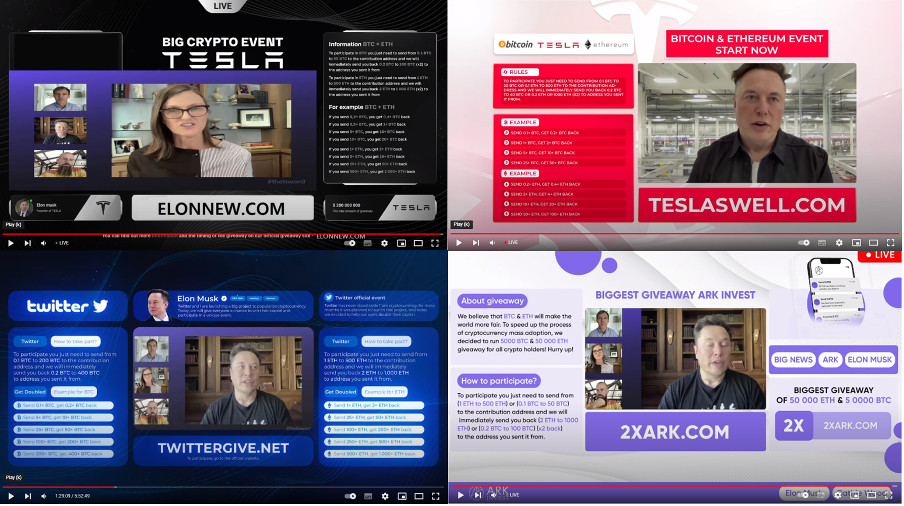
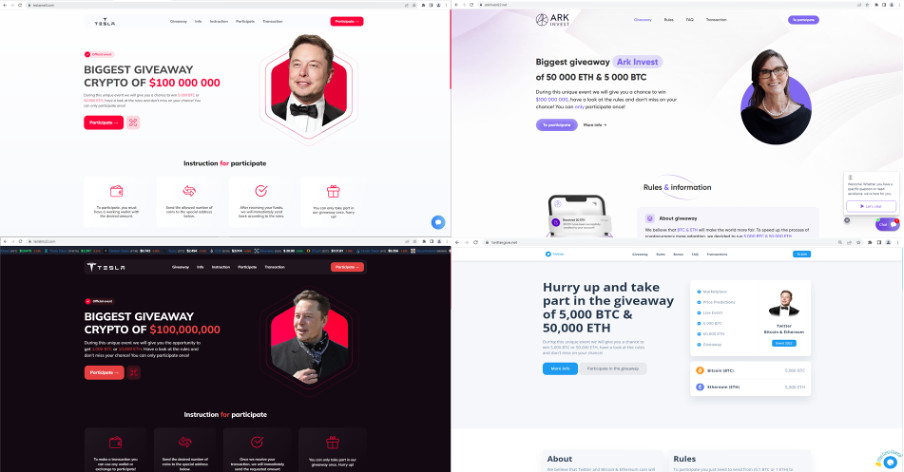
We identified several different streams occurring at a similar same time. The images of some are shown below:
The YouTube streams advertised several sites which shared a similar theme. They claim to send cryptocurrency worth double the value which they’ve received. For example, if you send 1BTC you will receive 2BTC in return. One of the site‘s frequently asked questions (FAQ) is shown below:
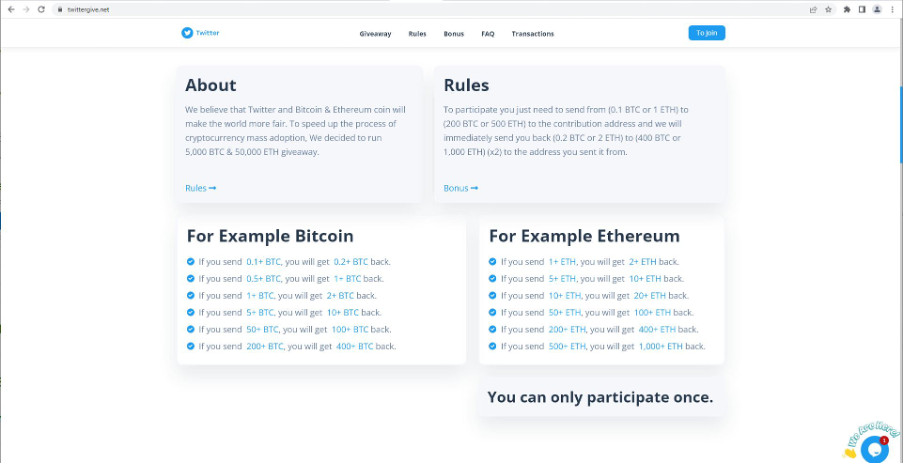
Here are some more examples of the scam sites we discovered:
The sites attempt to trick the visitors into thinking that others are sending cryptocurrency to it by showing a table with recent transactions. This is fake and is generated by JavaScript which creates random crypto wallets and amounts and then adds these to the table.
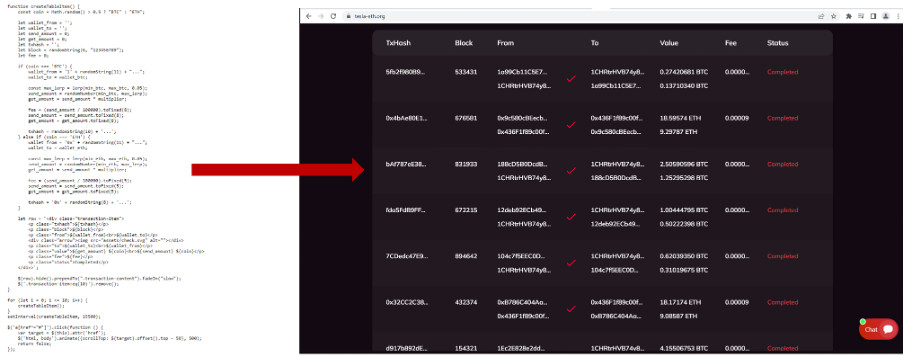
The wallets associated with the malicious sites have received a large number of transactions with a combined value of $280,000 as of 5 PM UTC on the 5th of May 2022
| Scam Site | Crypto Type | Wallet | Value as on 5PM UTC 5th May 2022 |
| 22ark-invest[.]org | ETH | 0x820a78D8e0518fcE090A9D16297924dB7941FD4f | $25,726.46 |
| 22ark-invest[.]org | BTC | 1Q3r1TzwCwQbd1dZzVM9mdFKPALFNmt2WE | $29,863.78 |
| 2xEther[.]com | ETH | 0x5081d1eC9a1624711061C75dB9438f207823E694 | $2,748.50 |
| 2x-musk[.]net | ETH | 0x18E860308309f2Ab23b5ab861087cBd0b65d250A | $10,409.13 |
| 2x-musk[.]net | BTC | 17XfgcHCfpyYMFdtAWYX2QcksA77GnbHN9 | $4,779.47 |
| arkinvest22[.]net | ETH | 0x2605dF183743587594A3DBC5D99F12BB4F19ac74 | $11,810.57 |
| arkinvest22[.]net | BTC | 1GLRZZHK2fRrywVUEF83UkqafNV3GnBLha | $5,976.80 |
| doublecrypto22[.]com | ETH | 0x12357A8e2e6B36dd6D98A2aed874D39c960eC174 | $0.00 |
| doublecrypto22[.]com | BTC | 1NKajgogVrRYQjJEQY2BcvZmGn4bXyEqdY | $0.00 |
| elonnew[.]com | ETH | 0xAC9275b867DAb0650432429c73509A9d156922Dd | $0.00 |
| elonnew[.]com | BTC | 1DU2H3dWXbUA9mKWuZjbqqHuGfed7JyqXu | $0.00 |
| elontoday[.]org | ETH | 0xBD73d147970BcbccdDe3Dd9340827b679e70d9d4 | $18,442.96 |
| elontoday[.]org | BTC | bc1qas66cgckep3lrkdrav7gy8xvn7cg4fh4d7gmw5 | $0.00 |
| Teslabtc22[.]com | ETH | 0x9B857C44C500eAf7fAfE9ed1af31523d84CB5bB0 | $27,386.69 |
| Teslabtc22[.]com | BTC | 18wJeJiu4MxDT2Ts8XJS665vsstiSv6CNK | $17,609.62 |
| tesla-eth[.]org | ETH | 0x436F1f89c00f546bFEf42F8C8d964f1206140c64 | $5,841.84 |
| tesla-eth[.]org | BTC | 1CHRtrHVB74y8Za39X16qxPGZQ12JHG6TW | $132.22 |
| teslaswell[.]com | ETH | 0x7007Fa3e7dB99686D337C87982a07Baf165a3C1D | $9.43 |
| teslaswell[.]com | BTC | bc1qdjma5kjqlf7l6fcug097s9mgukelmtdf6nm20v | $0.00 |
| twittergive[.]net | ETH | 0xB8e257C18BbEC93A596438171e7E1E77d18671E5 | $25,918.90 |
| twittergive[.]net | BTC | 1EX3dG9GUNVxoz6yiPqqoYMQw6SwQUpa4T | $99,123.42 |
Scammers have been using social media sites such as Twitter and Youtube to attempt to trick users into parting ways with their cryptocurrency for the past few years. McAfee urges its customers to be vigilant and if something sounds too good to be true then it is most likely not legitimate.
Our customers are protected against the malicious sites detailed in this blog as they are blocked with McAfee Web Advisor
| Type | Value | Product | Blocked |
| URL – Crypto Scam | twittergive[.]net | McAfee WebAdvisor | YES |
| URL – Crypto Scam | tesla-eth[.]org | McAfee WebAdvisor | YES |
| URL – Crypto Scam | 22ark-invest[.]org | McAfee WebAdvisor | YES |
| URL – Crypto Scam | 2xEther[.]com | McAfee WebAdvisor | YES |
| URL – Crypto Scam | Teslabtc22[.]com | McAfee WebAdvisor | YES |
| URL – Crypto Scam | elontoday[.]org | McAfee WebAdvisor | YES |
| URL – Crypto Scam | elonnew[.]com | McAfee WebAdvisor | YES |
| URL – Crypto Scam | teslaswell[.]com | McAfee WebAdvisor | YES |
| URL – Crypto Scam | 2x-musk[.]net | McAfee WebAdvisor | YES |
| URL – Crypto Scam | doublecrypto22[.]com | McAfee WebAdvisor | YES |
| URL – Crypto Scam | arkinvest22[.]net | McAfee WebAdvisor | YES |
The post Crypto Scammers Exploit: Elon Musk Speaks on Cryptocurrency appeared first on McAfee Blog.







On the internet, the Domain Name System (DNS) is the way regular people access websites such as ESPN.com or BBC.com. However, the internet uses a unique series of Internet Protocol (IP) addresses to access websites which are tricky for humans to remember. Web browsers typically interact with websites through IP addresses, and DNS translates websites into IP addresses so browsers can access Internet resources. Historically, this has been done in the form of unencrypted clear text that ISPs and security providers such as McAfee can read and act upon to sort through risky websites or to improve network performance and intelligence.
However, this also opens up vulnerabilities of security and privacy. As an industry, (Apple, Microsoft, Google, and others) participants are moving toward encrypting this traffic to and from DNS servers with protocols such as DNS over TLS (DoT) and DNS over HTTPS (DoH). Unless the ISP offers DoT/DoH decryption (translation) capabilities, traffic could go directly to outside DNS providers such as Google DNS and Cloudflare who do. Without this visibility, unsafe websites cannot be seen and blocked using DNS filtering technology. Customers can visit sites created by criminals that can trick them to steal their account credentials, download ransomware, or show inappropriate content to their kids.
We’re advancing our Secure Home Platform (SHP) technology to future proof the ability for our partners to protect their customers, their families, and their connected home devices. McAfee is the first in the market to build and introduce this technology. McAfee and OpenXchange have partnered to provide an integration of a forwarder/translator (PowerDNS) with the home router-based SHP product that will make it possible to keep the traffic within the ISP network, as shown in the diagram below – allowing DNS filtering even in encrypted DNS environments.
The ISP can continue to read the traffic and stands to benefit in several ways:
Consumers in turn benefit from these additional capabilities that ISPs can provide in security, privacy, and performance.
If you are interested in McAfee’s exciting new DoT-DoH technology for the Secure Home Platform, please contact your McAfee Account Representative for further details.
The post Advancing our Secure Home Platform with DNS over HTTPS appeared first on McAfee Blog.










































eleceye-1200
